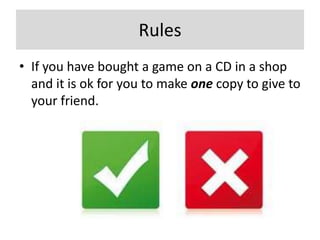
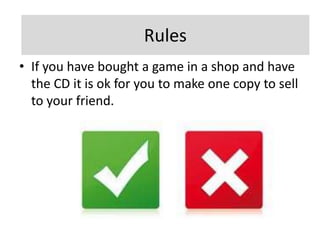
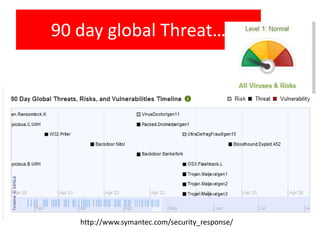
The document discusses various topics related to the effects of using information and communication technologies (ICT), including software copyright issues, computer viruses and hacking, the impact of ICT on employment and online shopping/banking, internet security threats, and potential health and safety risks of ICT use. It provides information on software piracy prevention methods and explains concepts like encryption, phishing, and cookies.




















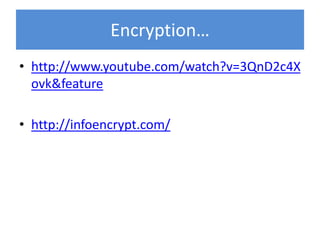
![encryption
• is the process of transforming information
(referred to as plaintext) using an algorithm
(called a cipher) to make it unreadable to anyone
except those possessing special
knowledge, usually referred to as a key. The result
of the process is encrypted information (in
cryptography, referred to as ciphertext). The
reverse process, i.e., to make the encrypted
information readable again, is referred to as
decryption (i.e., to make it unencrypted).[citation
needed]](https://image.slidesharecdn.com/unit6effectsofusingict-120519041711-phpapp01/85/iGCSE-Theory-Unit-6-Effects-of-Using-ICT-28-320.jpg)







![Pharming
• Pharming[p] is a hacker's attack intended to redirect a
website's traffic to another, bogus site. Pharming can
be conducted either by changing the hosts file on a
victim's computer or by exploitation of a vulnerability
in DNS server software. DNS servers are computers
responsible for resolving Internet names into their real
IP addresses. Compromised DNS servers are sometimes
referred to as "poisoned". Pharming requires
unprotected access to target a computer, such as
altering a customer's home computer, rather than a
corporate business server.](https://image.slidesharecdn.com/unit6effectsofusingict-120519041711-phpapp01/85/iGCSE-Theory-Unit-6-Effects-of-Using-ICT-40-320.jpg)
![Spam
• Spam (its name a portmanteau of
the words "Spiced" and "Ham")[1]
is a canned precooked meat
product made by the Hormel
Foods Corporation, first
introduced in 1937. The labelled
ingredients in the classic variety
of Spam are chopped pork
shoulder meat, with ham meat
added, salt, water, modified
potato starch as a binder, and
sodium nitrite as a preservative.](https://image.slidesharecdn.com/unit6effectsofusingict-120519041711-phpapp01/85/iGCSE-Theory-Unit-6-Effects-of-Using-ICT-41-320.jpg)






