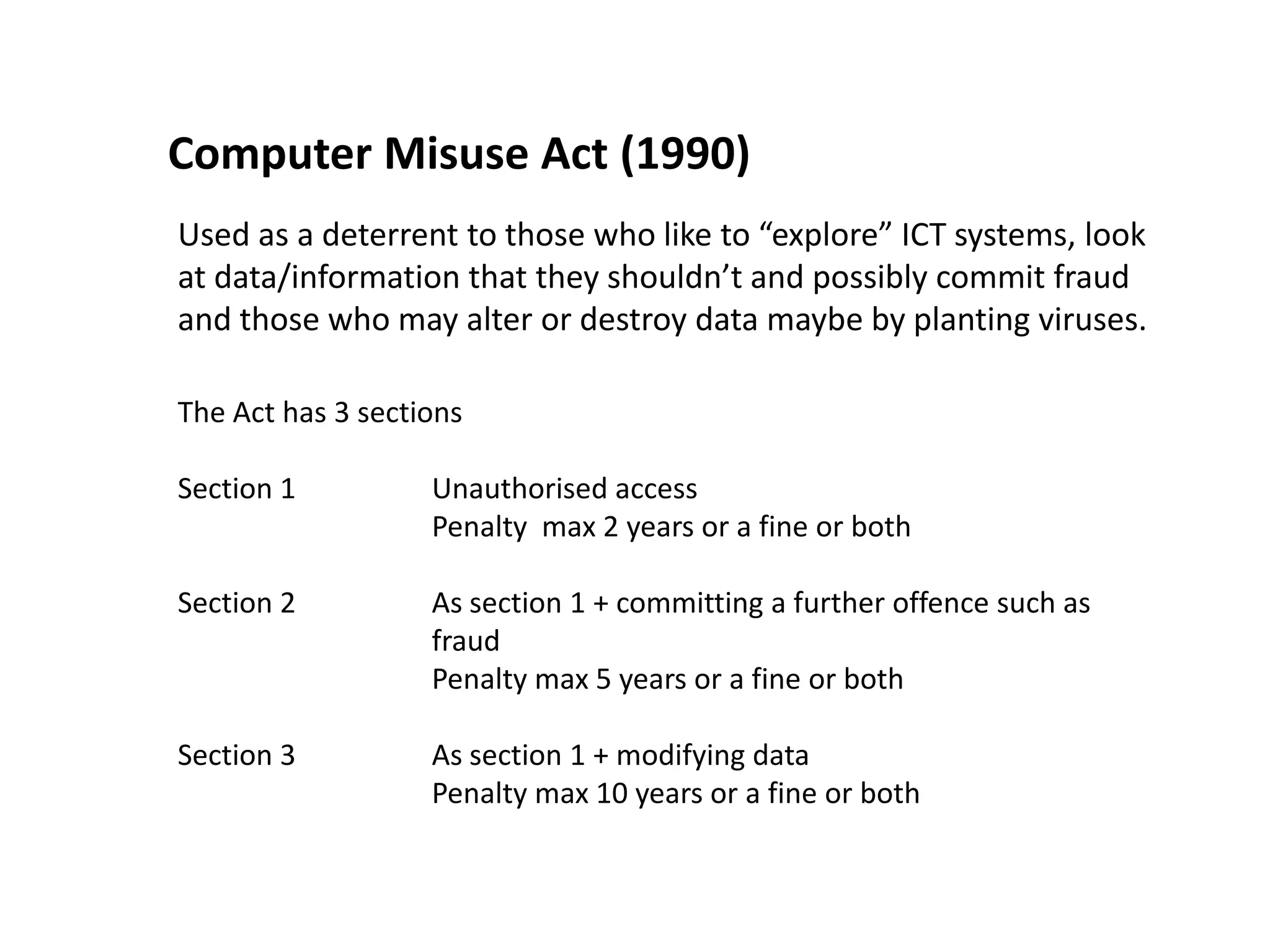
The document summarizes key information about protecting data and systems on ICT networks. It discusses reasons for protecting data including privacy, identity theft, and threats to systems. Common threats are identified as viruses, hacking, fire or power loss. Systems can be protected through measures like access controls, encryption, firewalls, and regular software updates. Relevant legislation is outlined, including the Computer Misuse Act which prohibits unauthorized access or data modification, and the Data Protection Act which protects personal information.