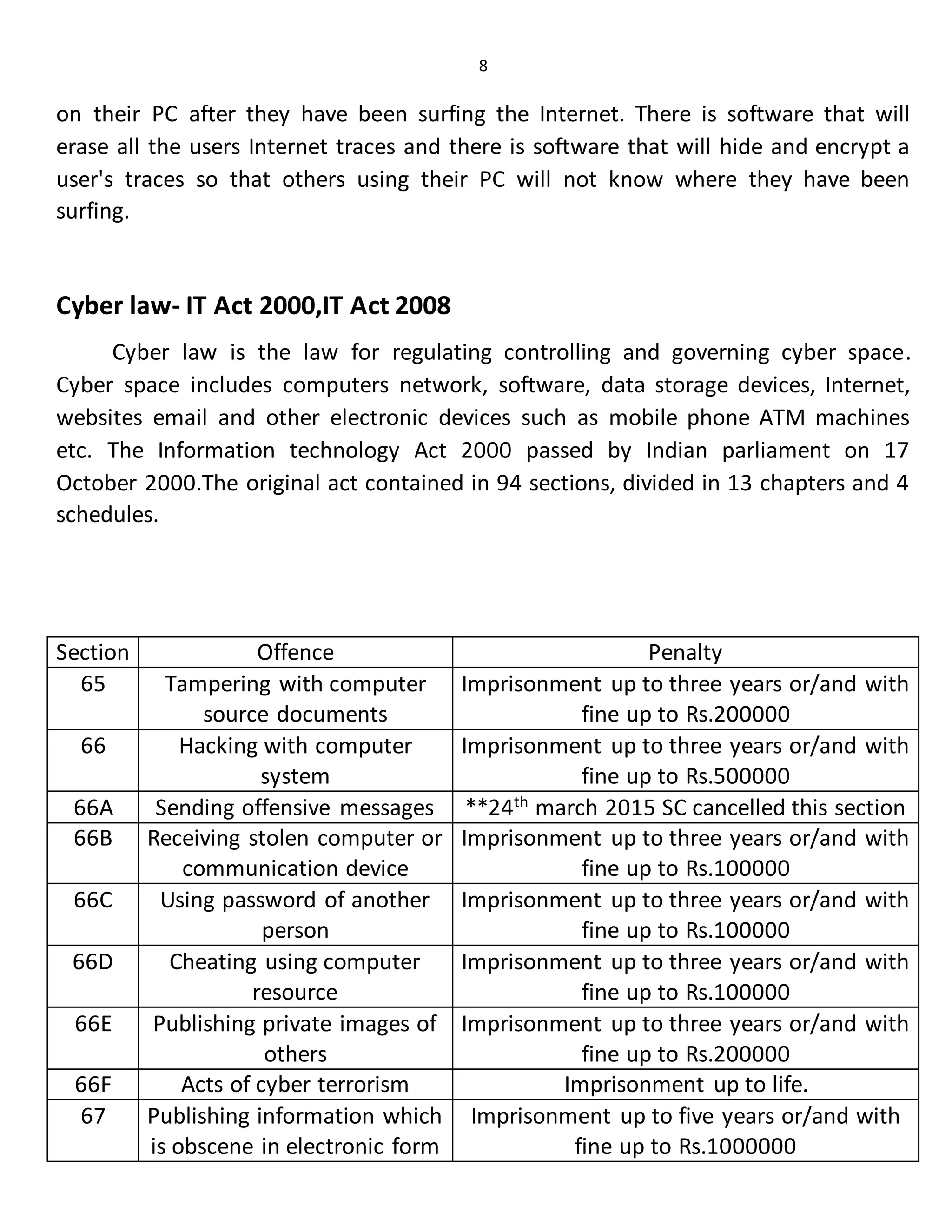
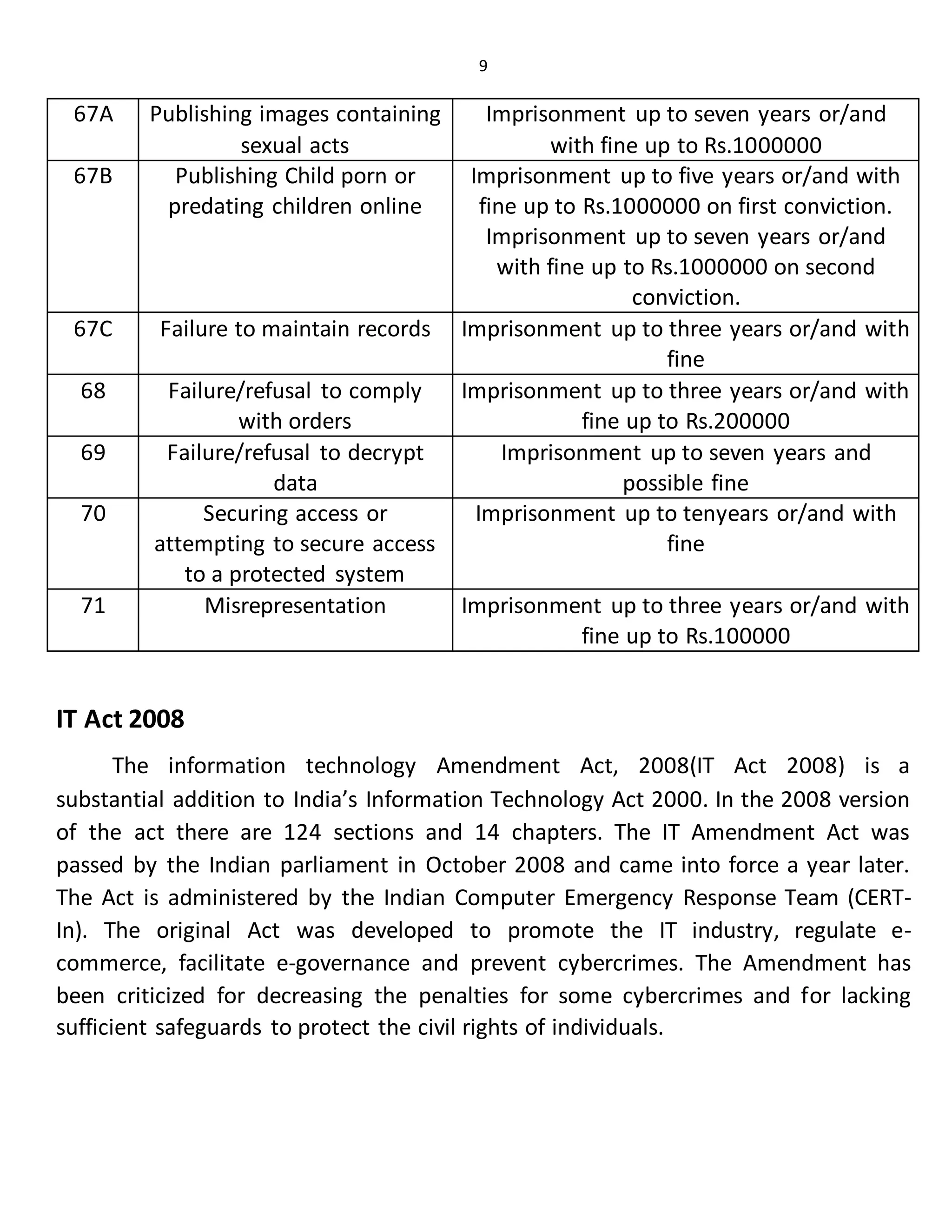
Computer viruses, malware, spyware, and Trojan horses are types of malicious software that can harm computers. Viruses spread by infecting files or programs and getting copied to other computers. Malware performs unwanted tasks like displaying ads or stealing data. Spyware monitors users' online activities without consent. Trojan horses deliver malware hidden within seemingly harmless programs or files. Antivirus software and firewalls help prevent infection by viruses, malware, and other cyber threats.