Embed presentation
Downloaded 38 times






![[1]William Stallings, “Cryptography and
Network Security Principles and Practices”,
Fourth Edition
Created by Sumita Das](https://image.slidesharecdn.com/trustedsystems1-160914013934/85/Trusted-systems1-12-320.jpg)

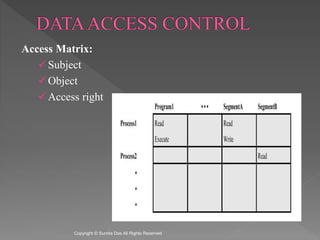
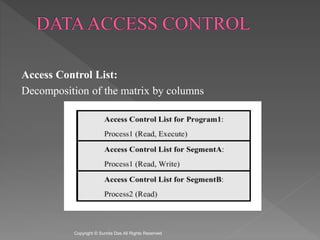
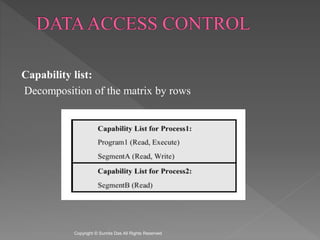
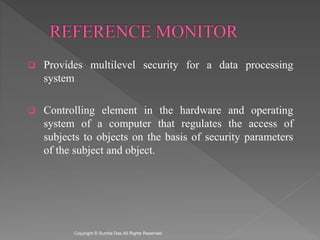
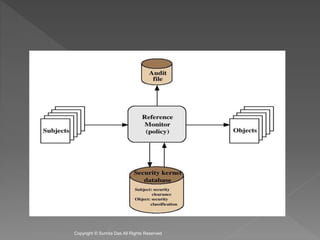
The document discusses network security and cryptography. It covers access matrices and lists, multilevel security models, security levels, trusted systems, and complete mediation, isolation, and verifiability as methods for enhancing system defenses against intruders and malicious programs. The document is authored by Sumita Das and references William Stallings' book on cryptography and network security principles and practices.











![[1]William Stallings, “Cryptography and
Network Security Principles and Practices”,
Fourth Edition
Created by Sumita Das](https://image.slidesharecdn.com/trustedsystems1-160914013934/85/Trusted-systems1-12-320.jpg)