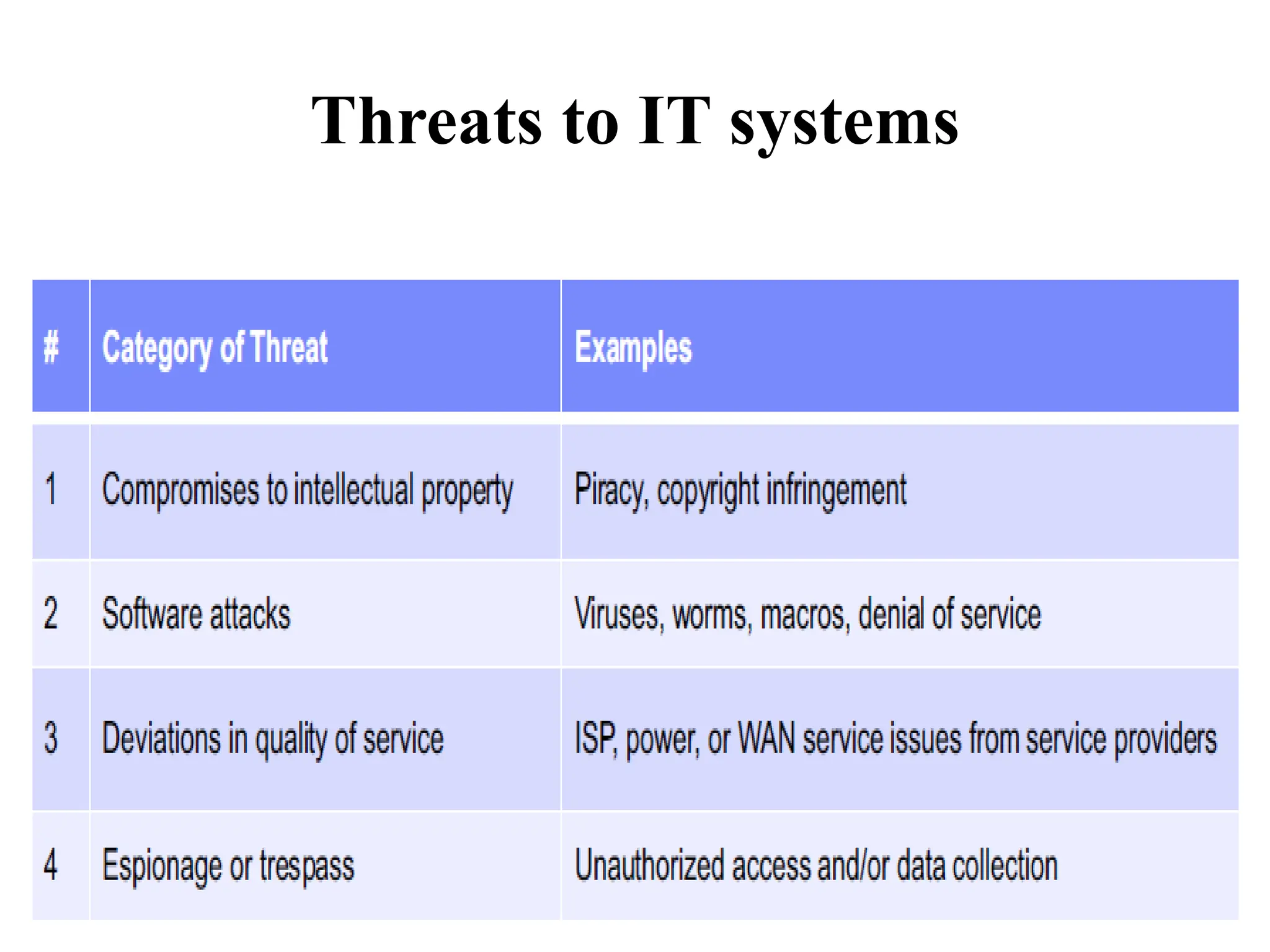
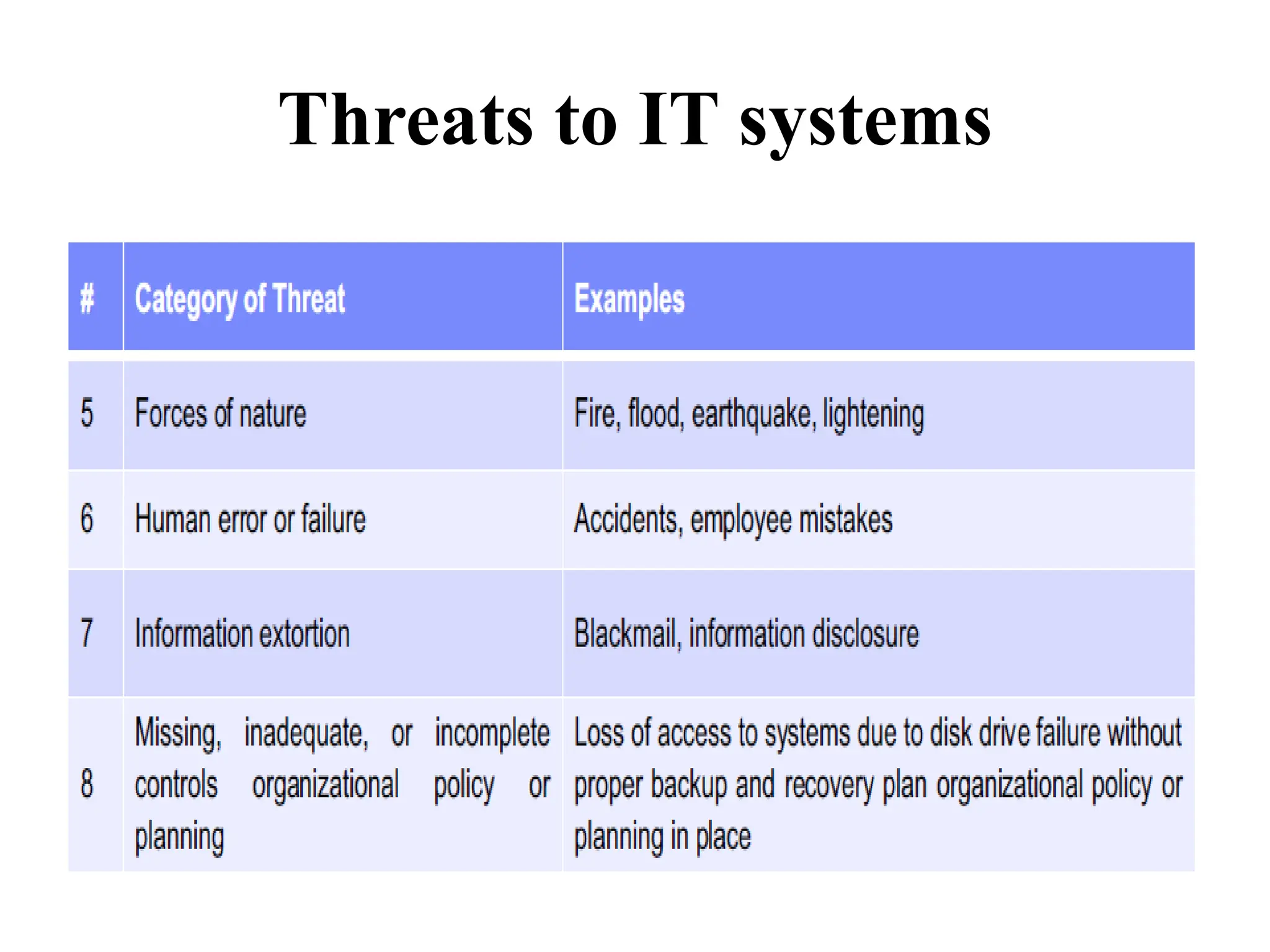
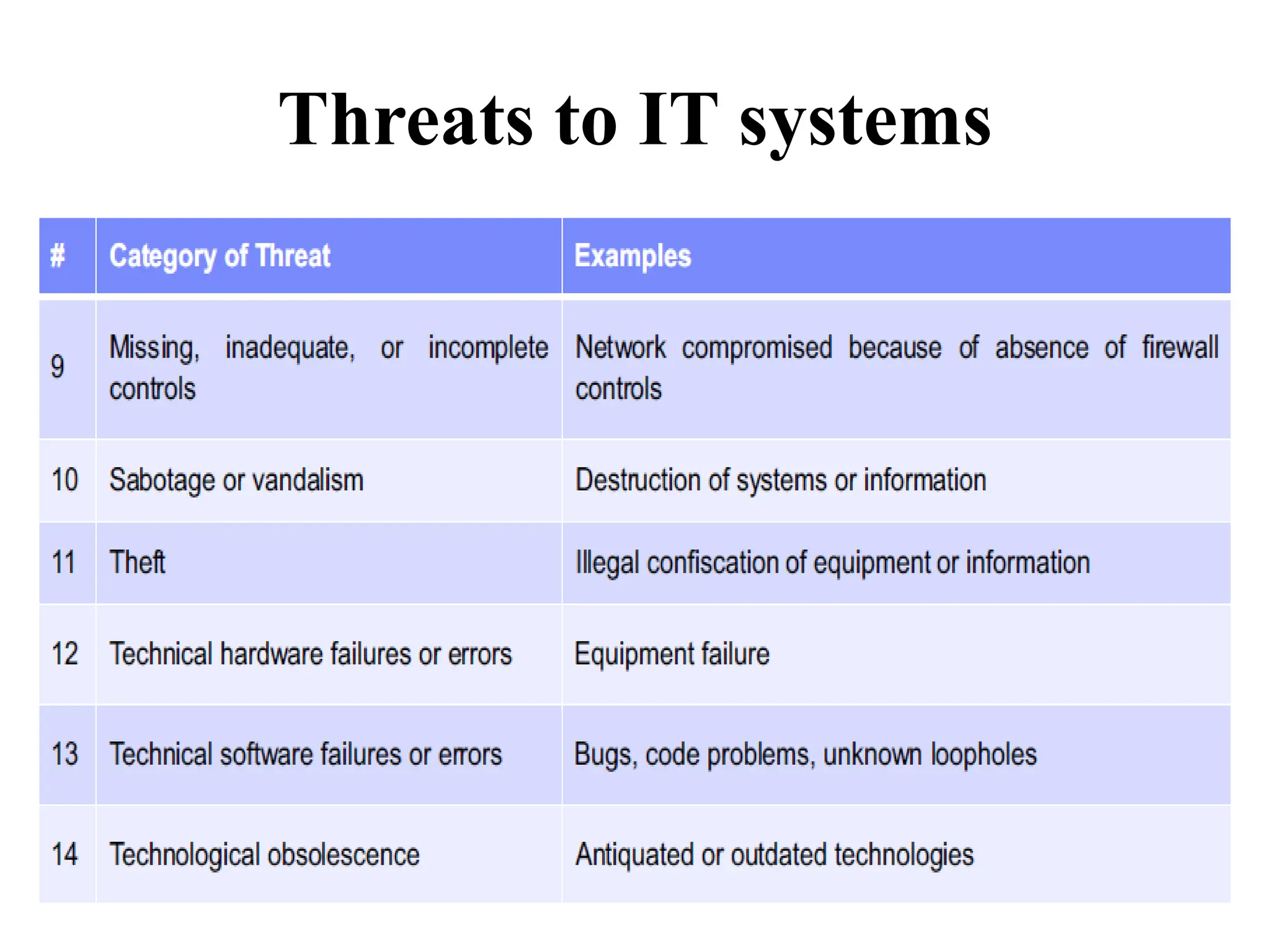
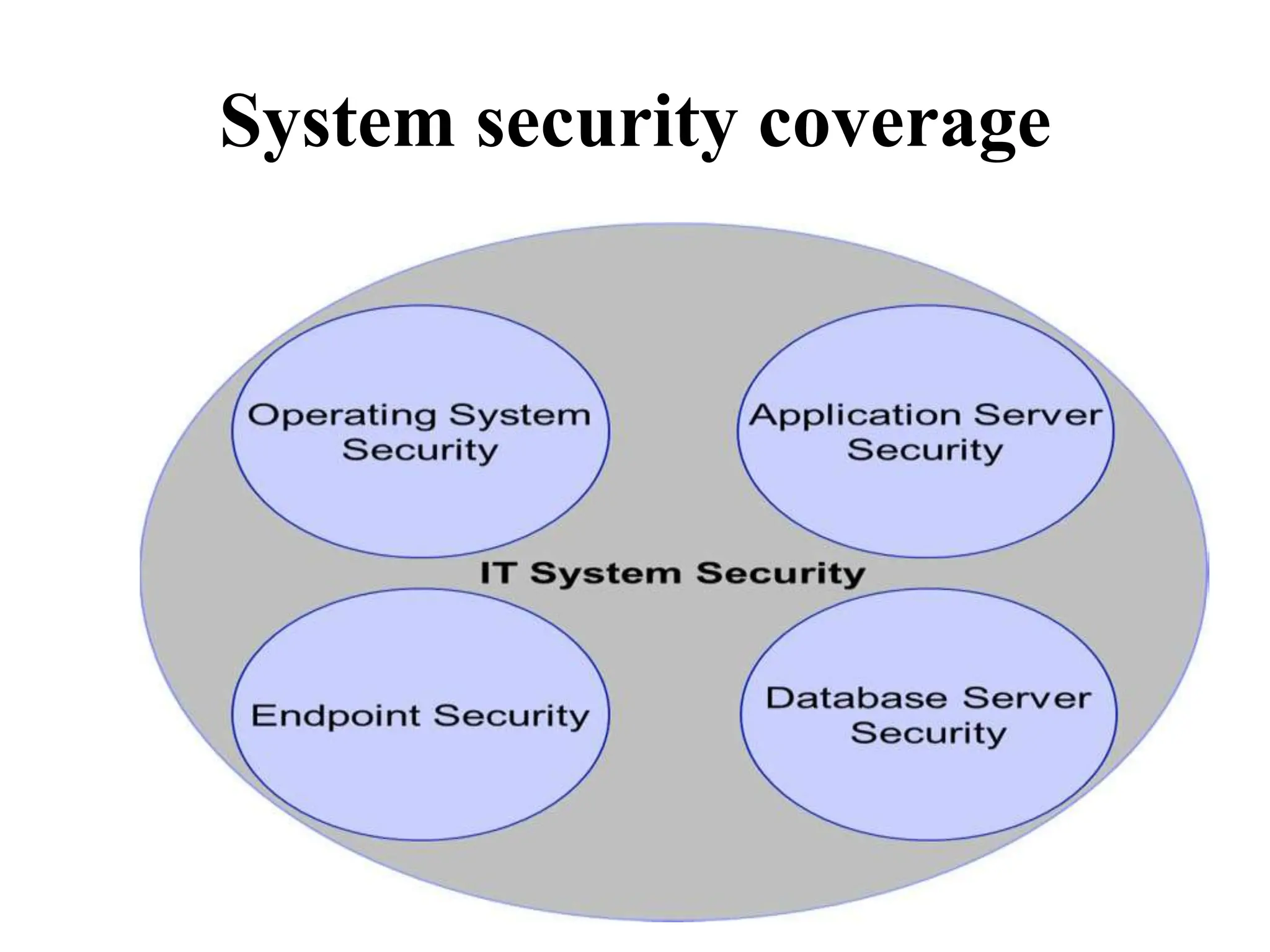
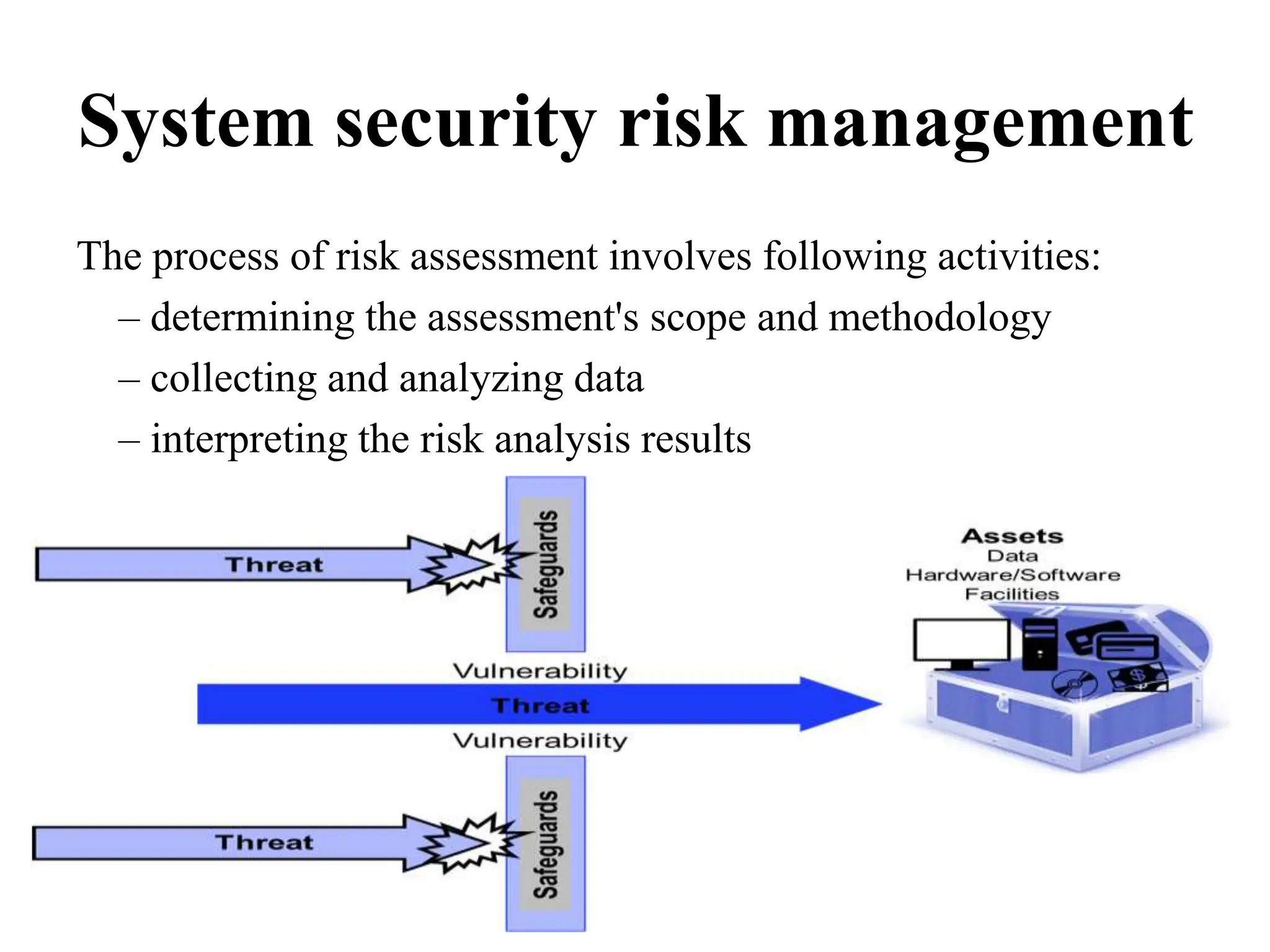
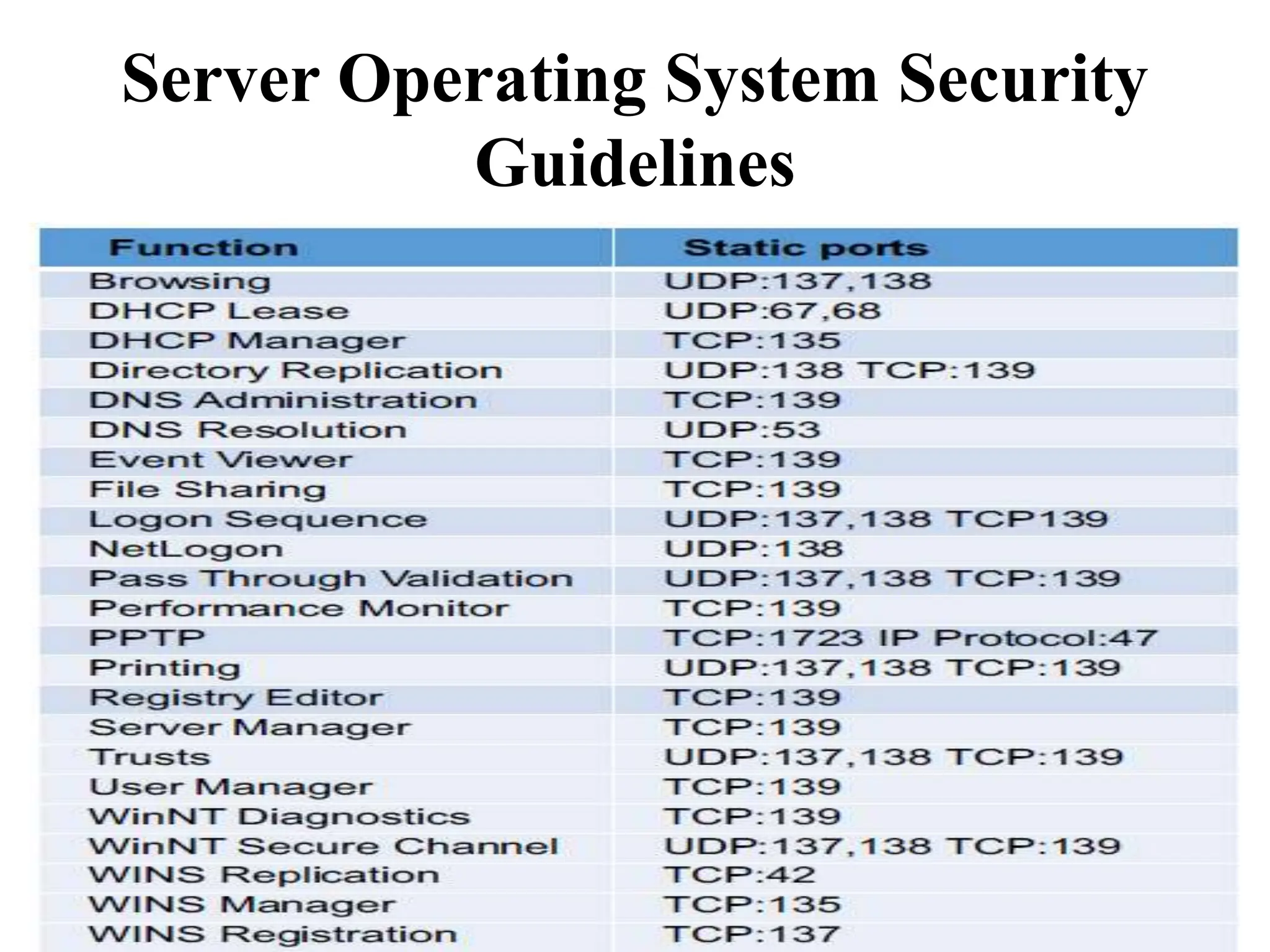
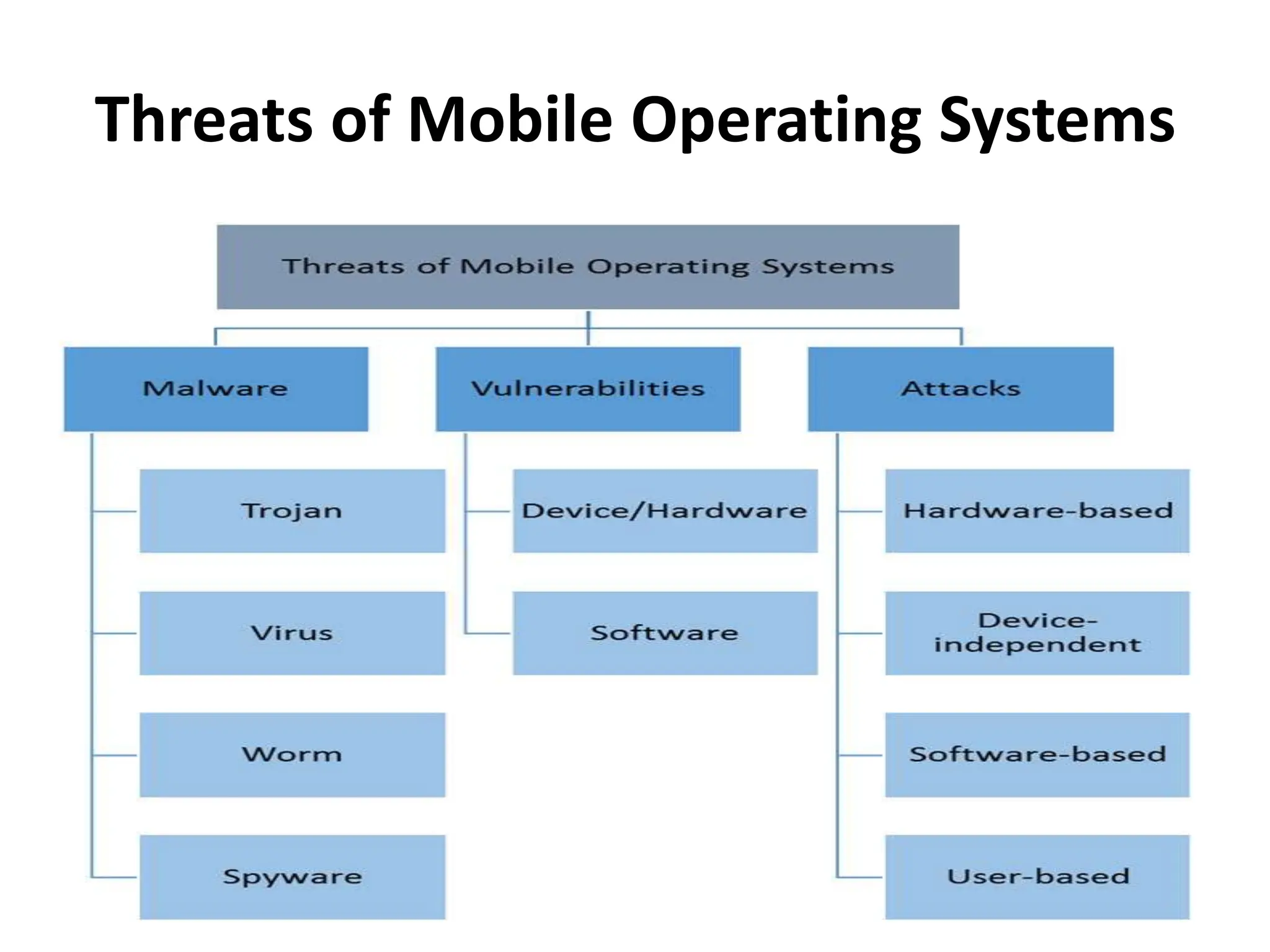
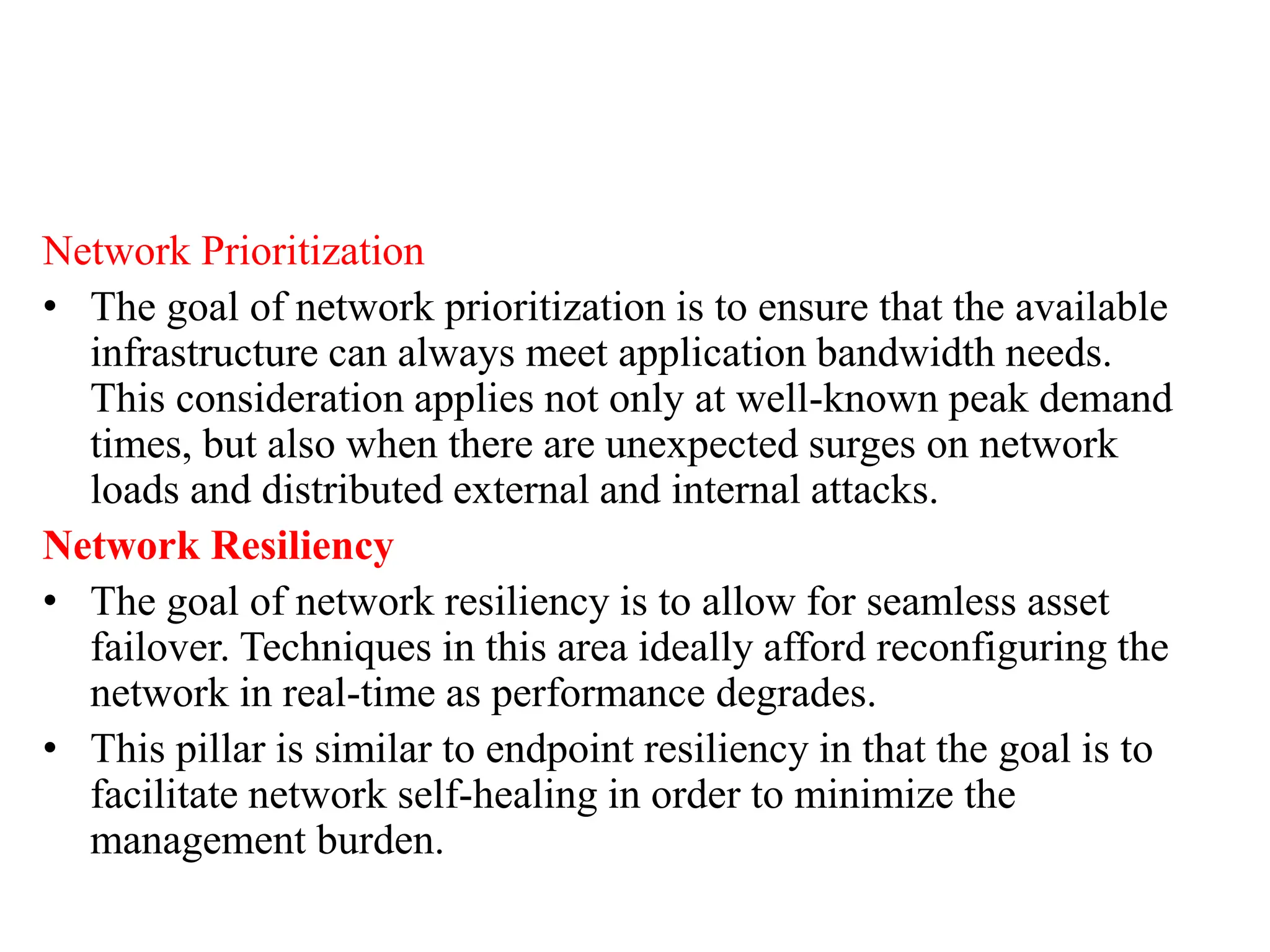
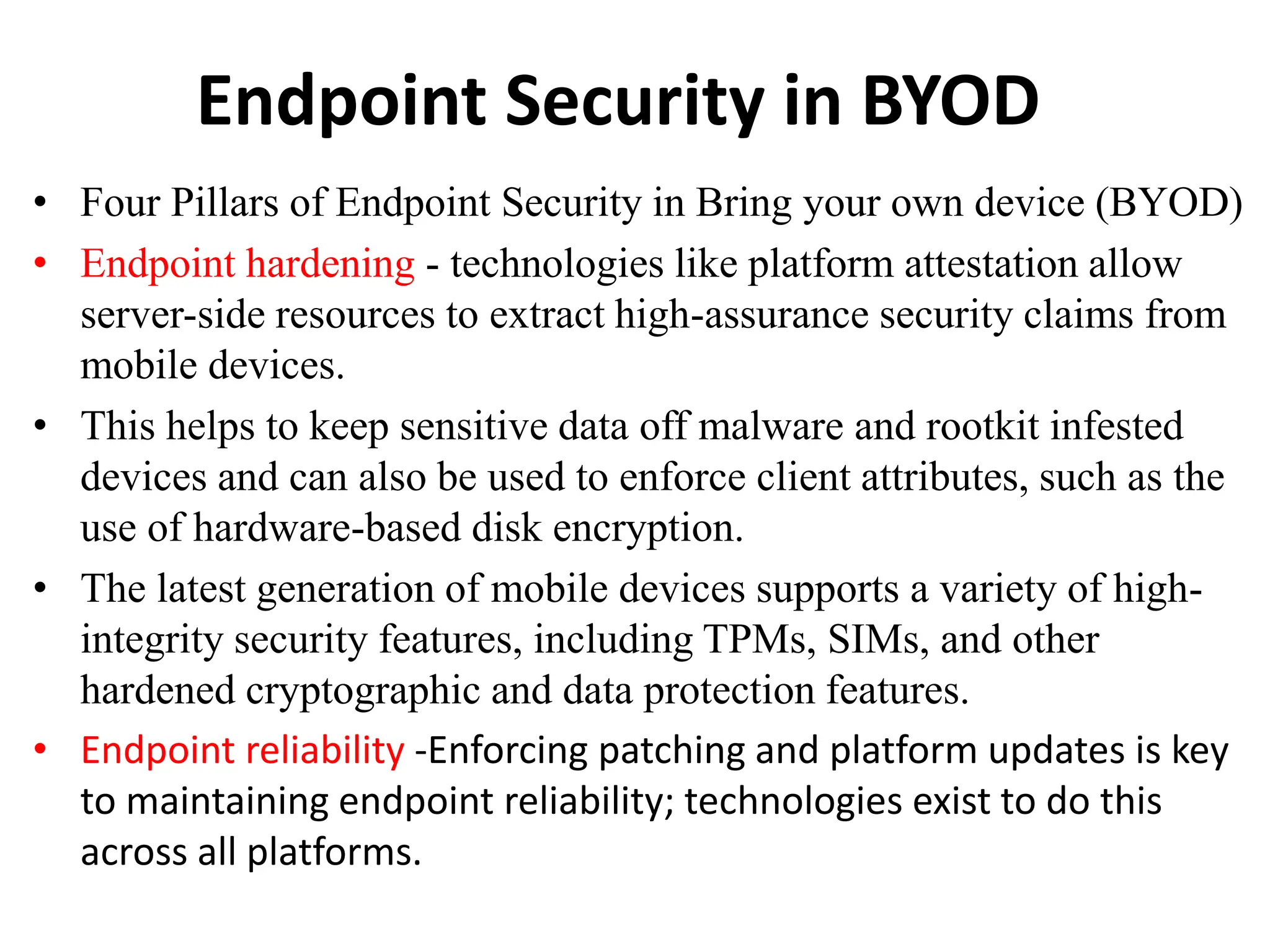
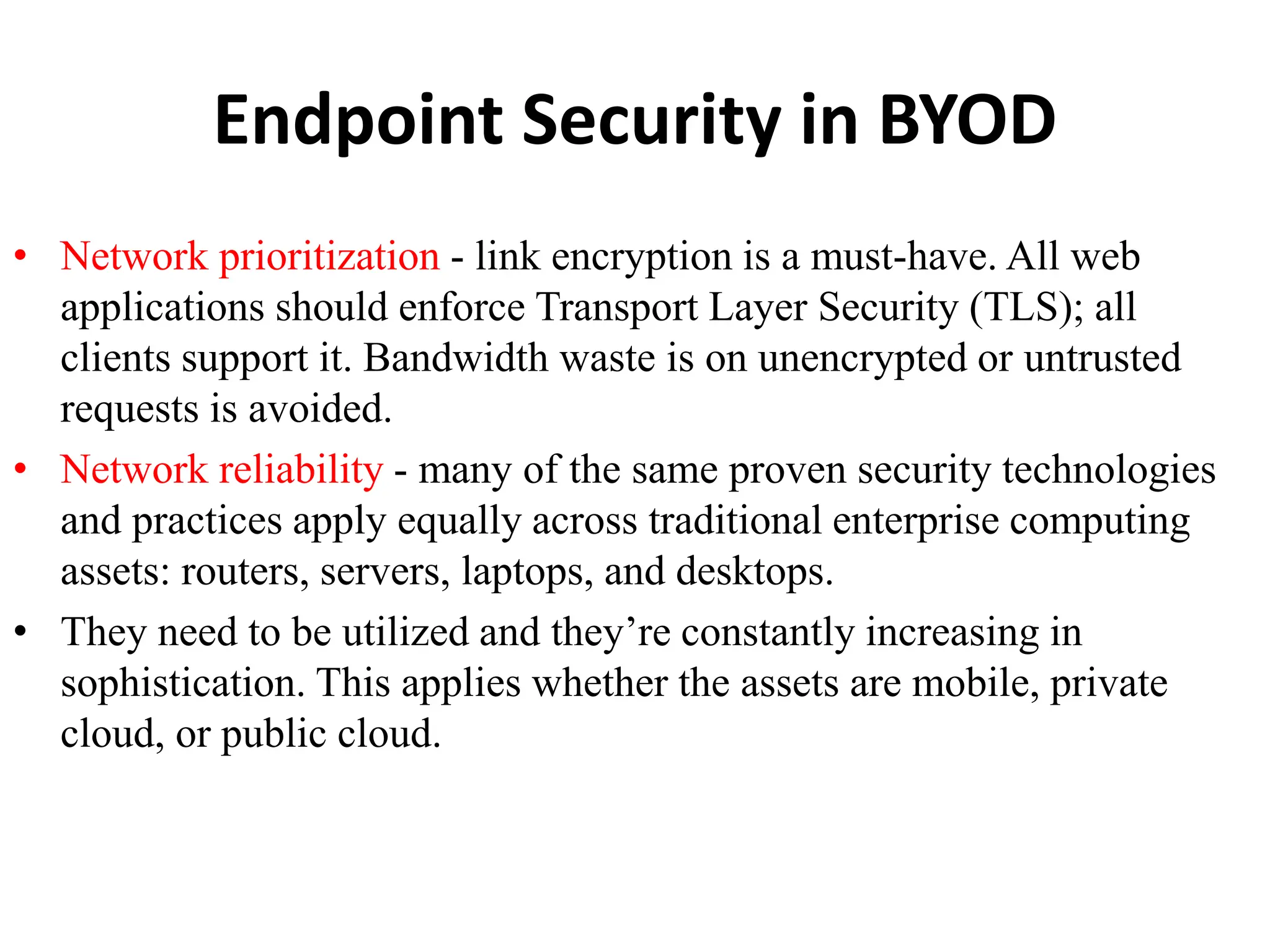
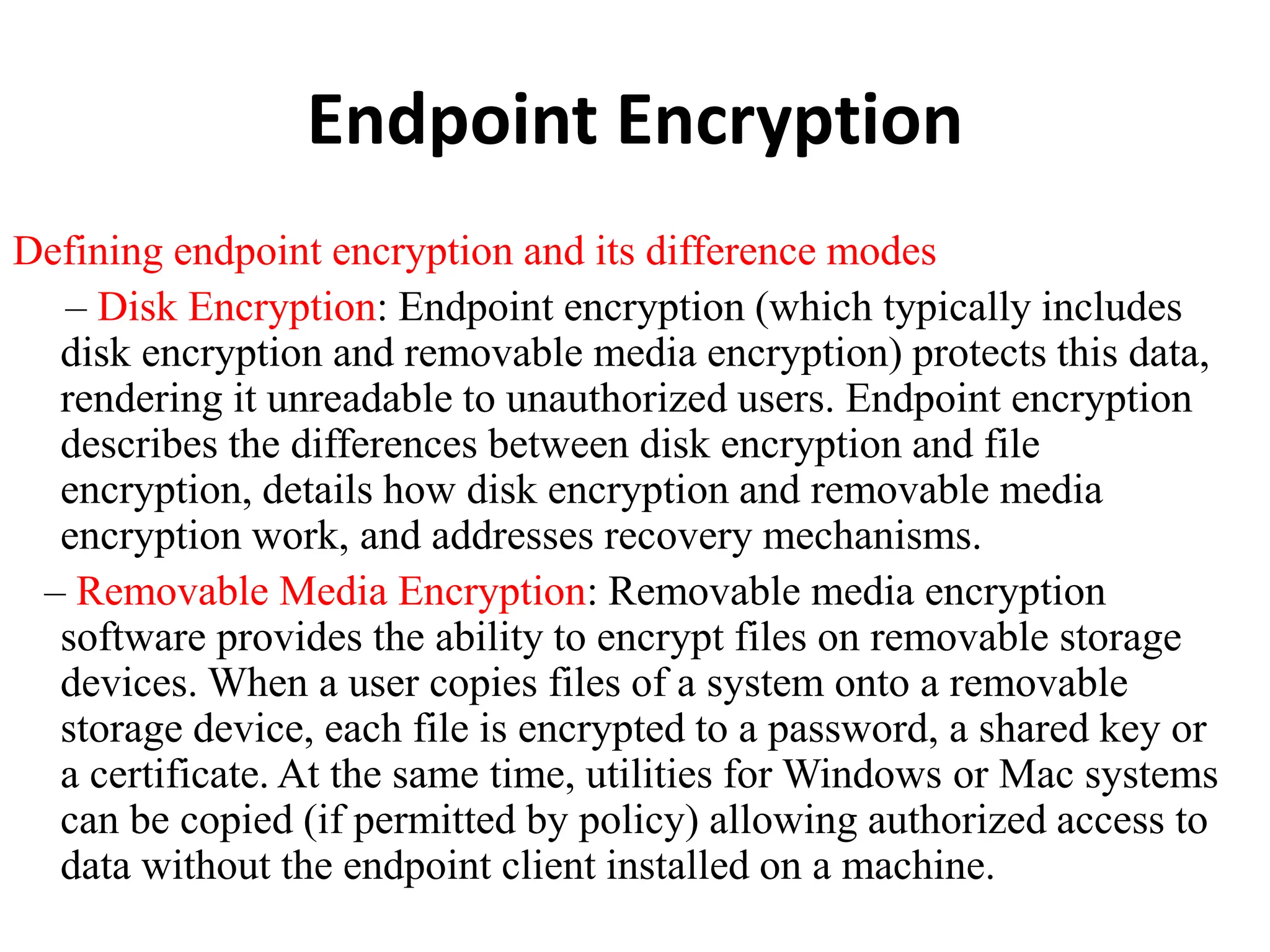
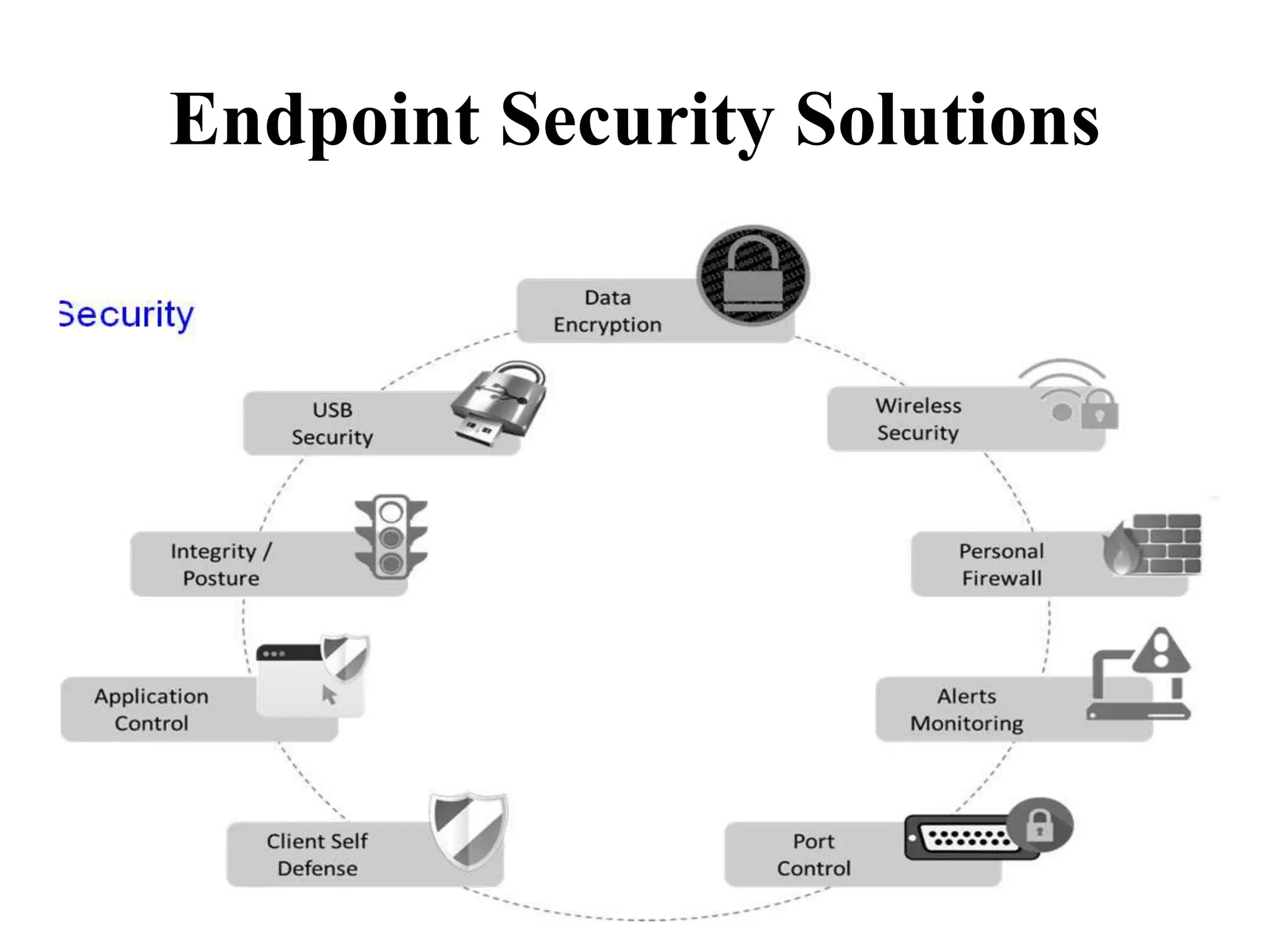
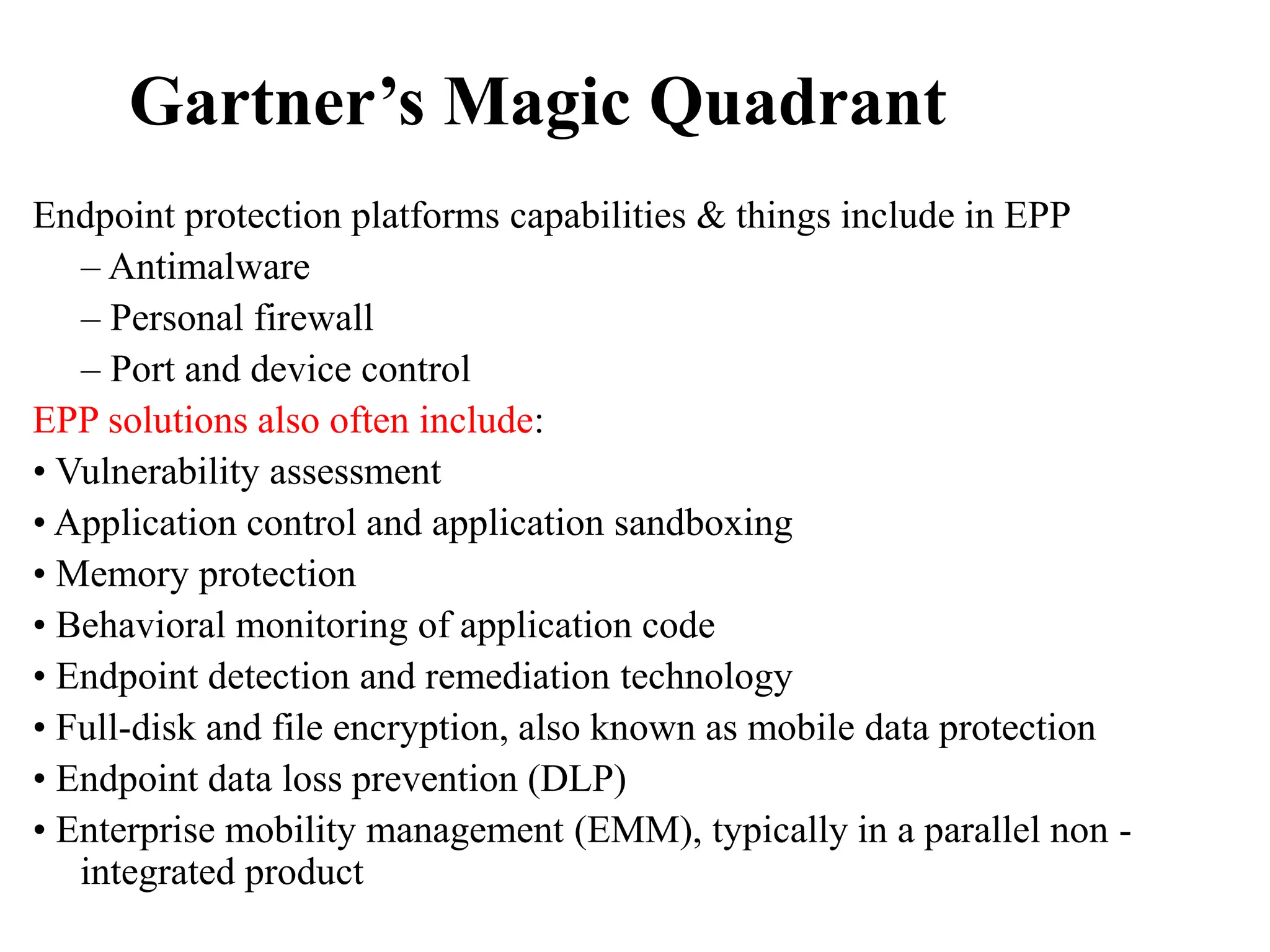
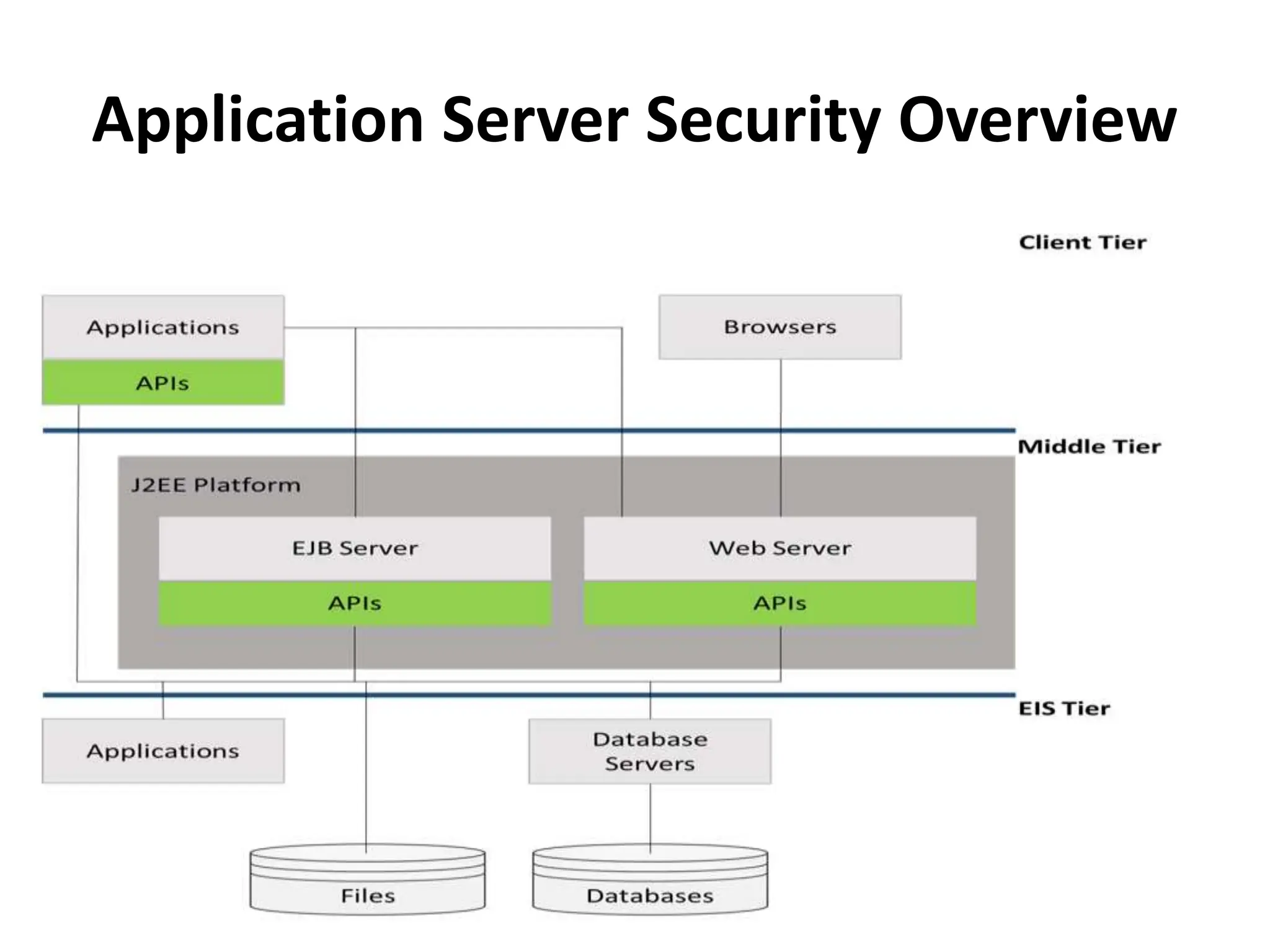
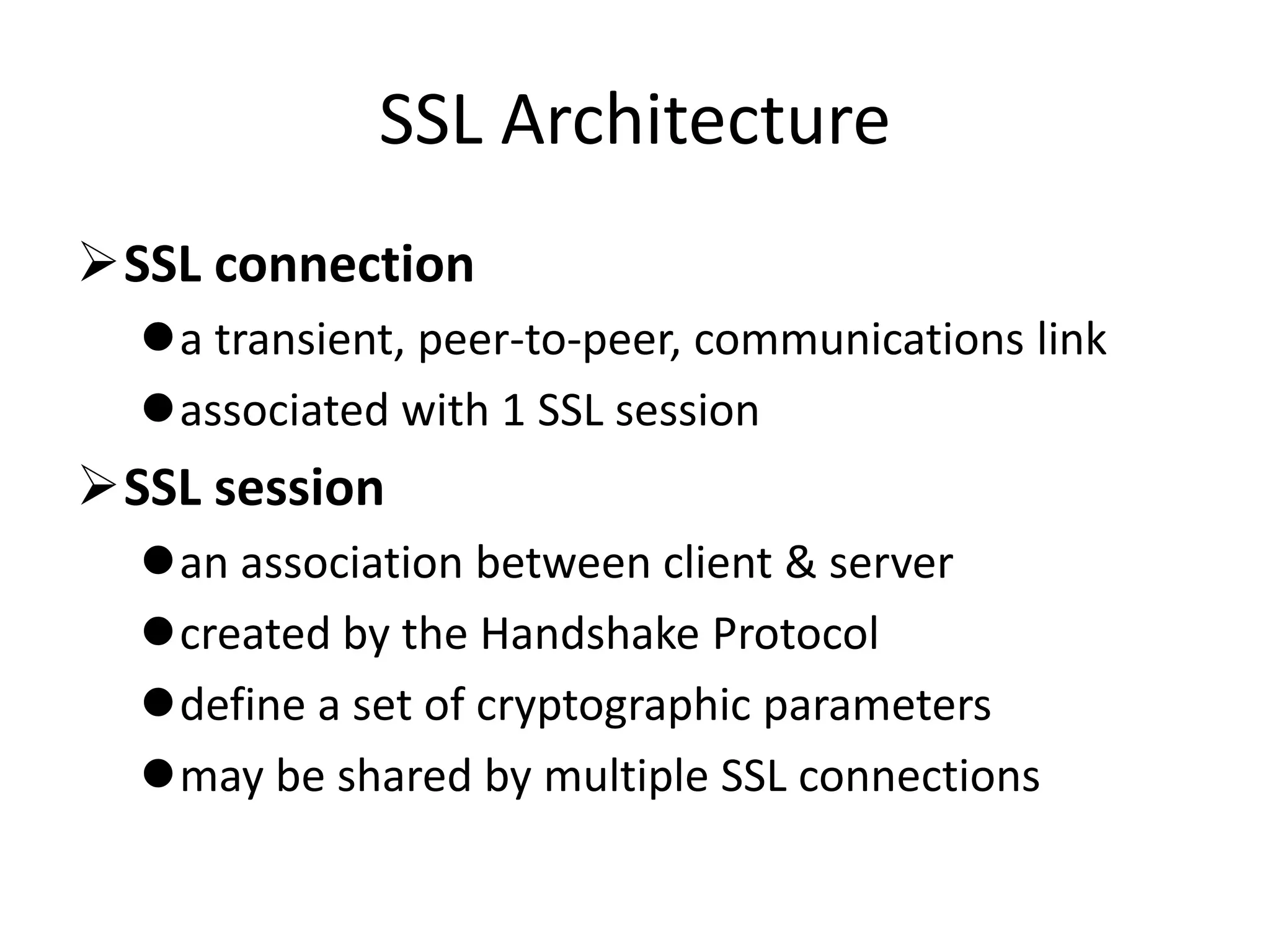
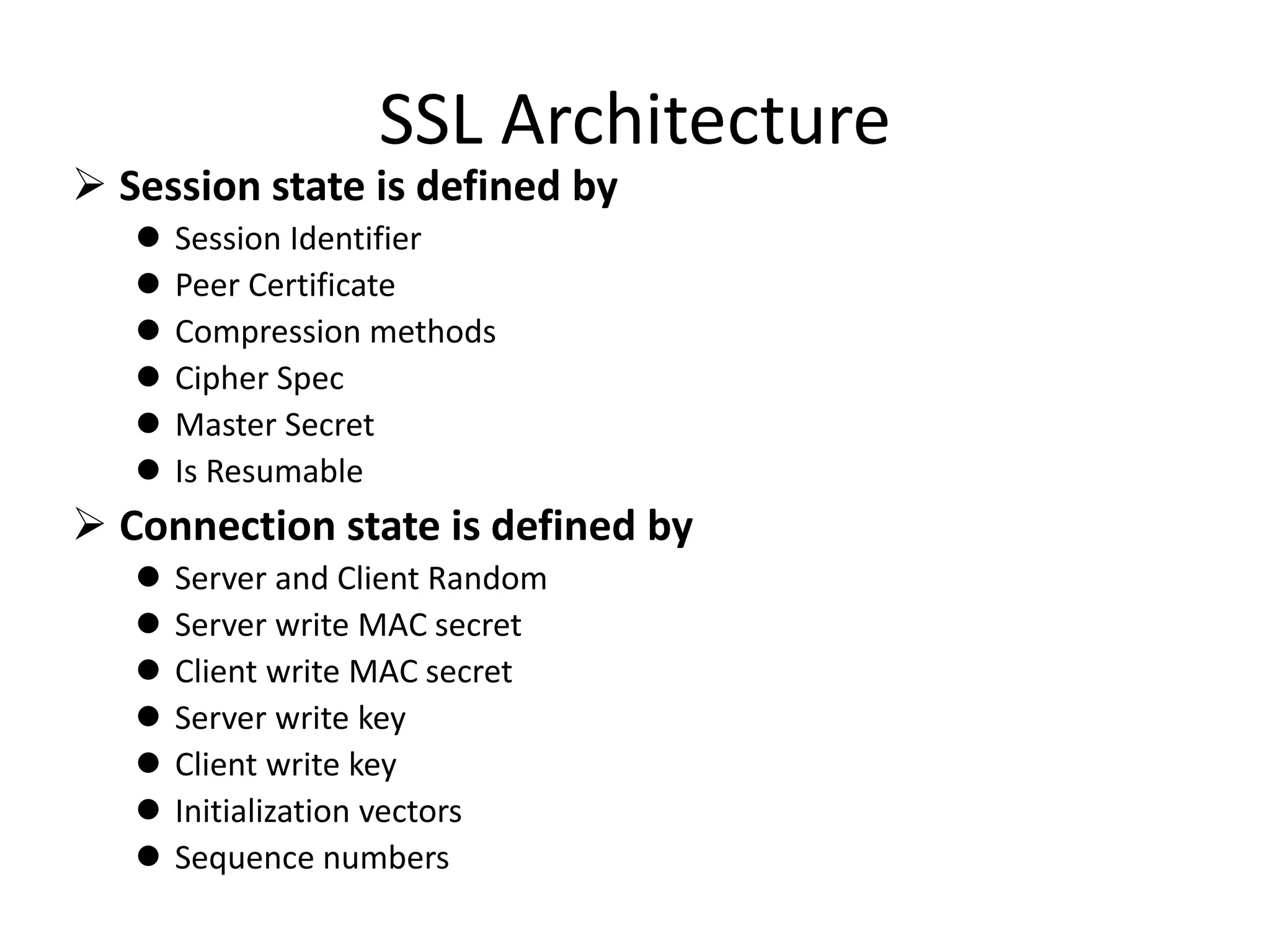
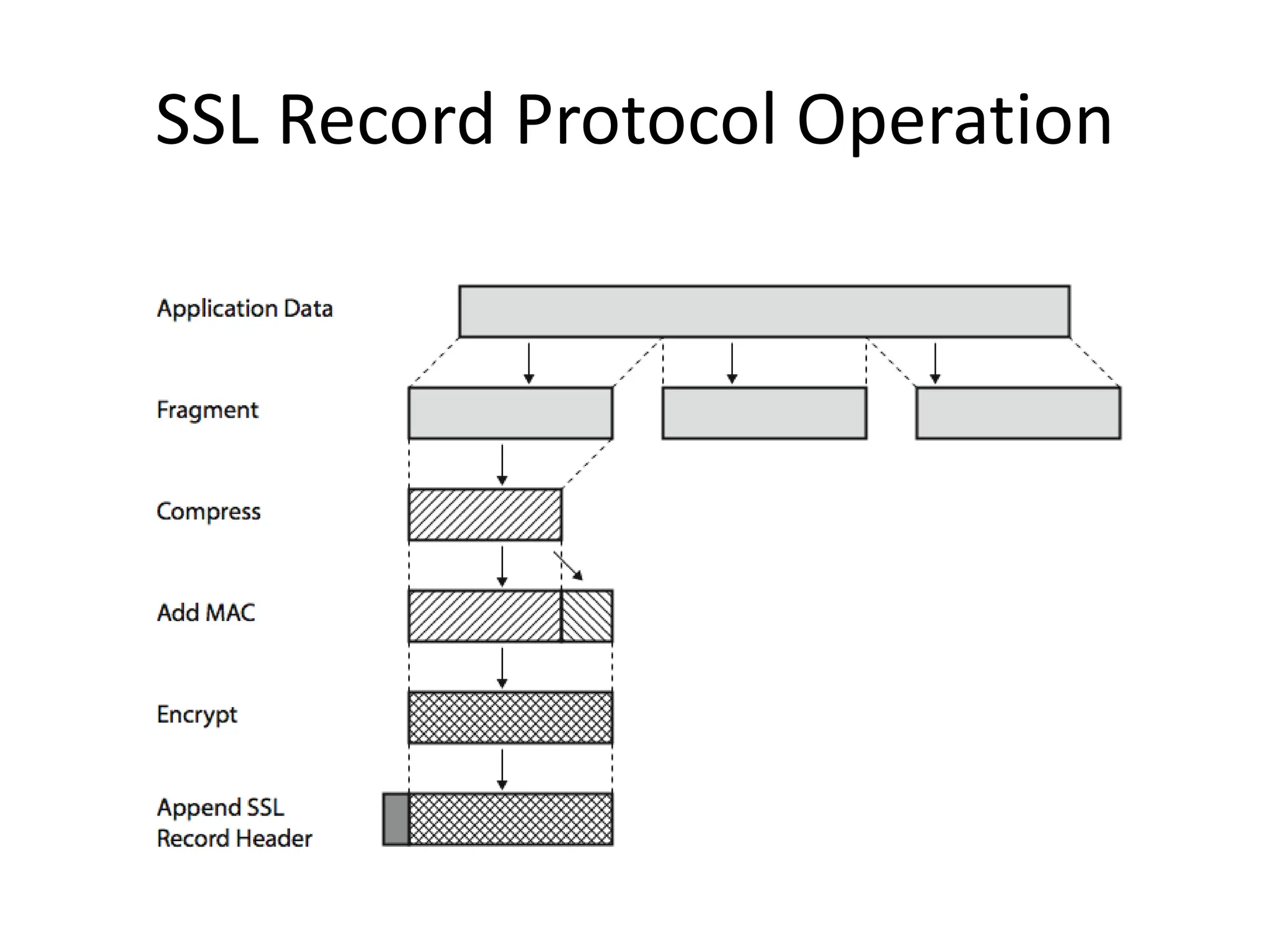
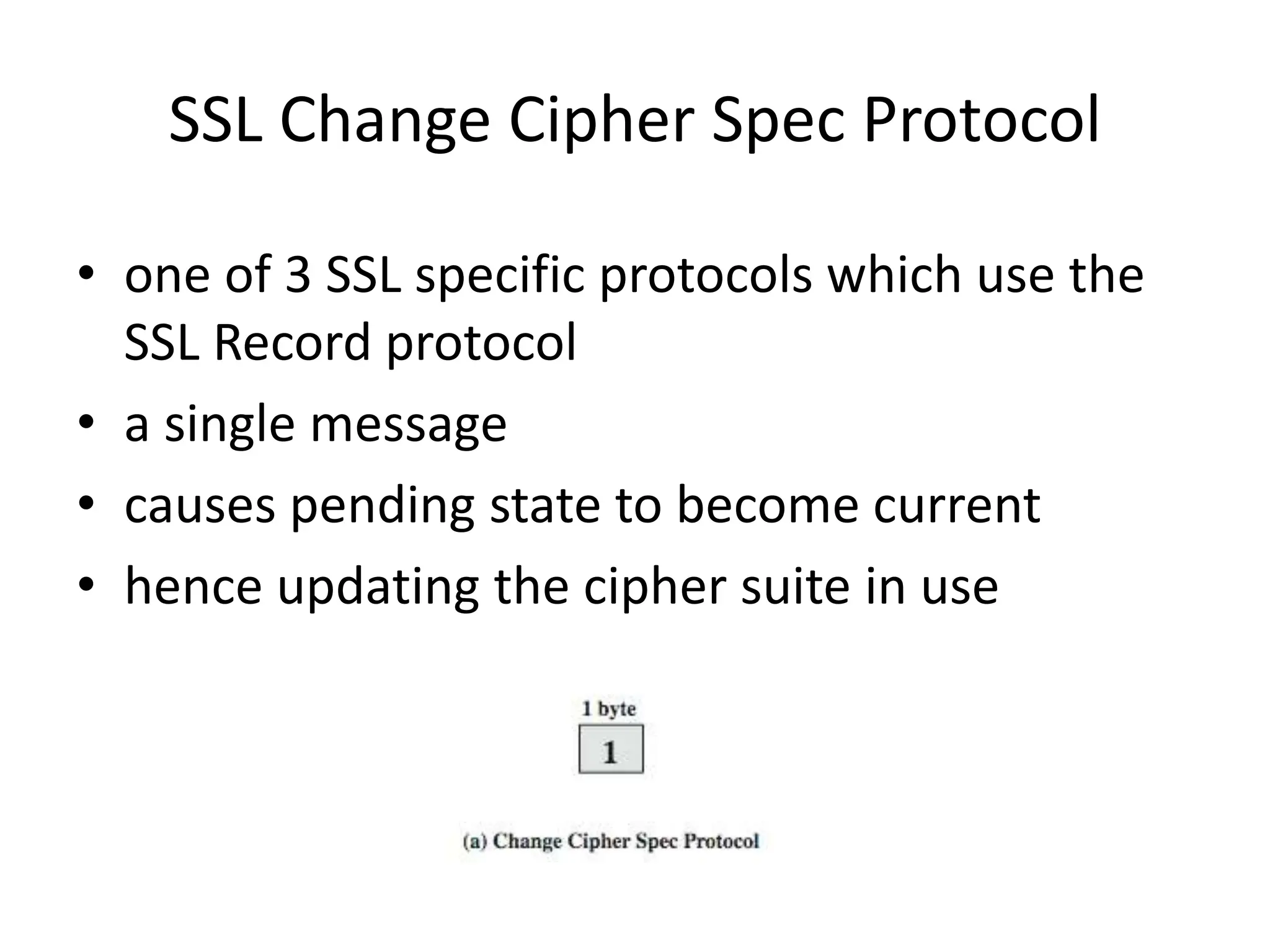
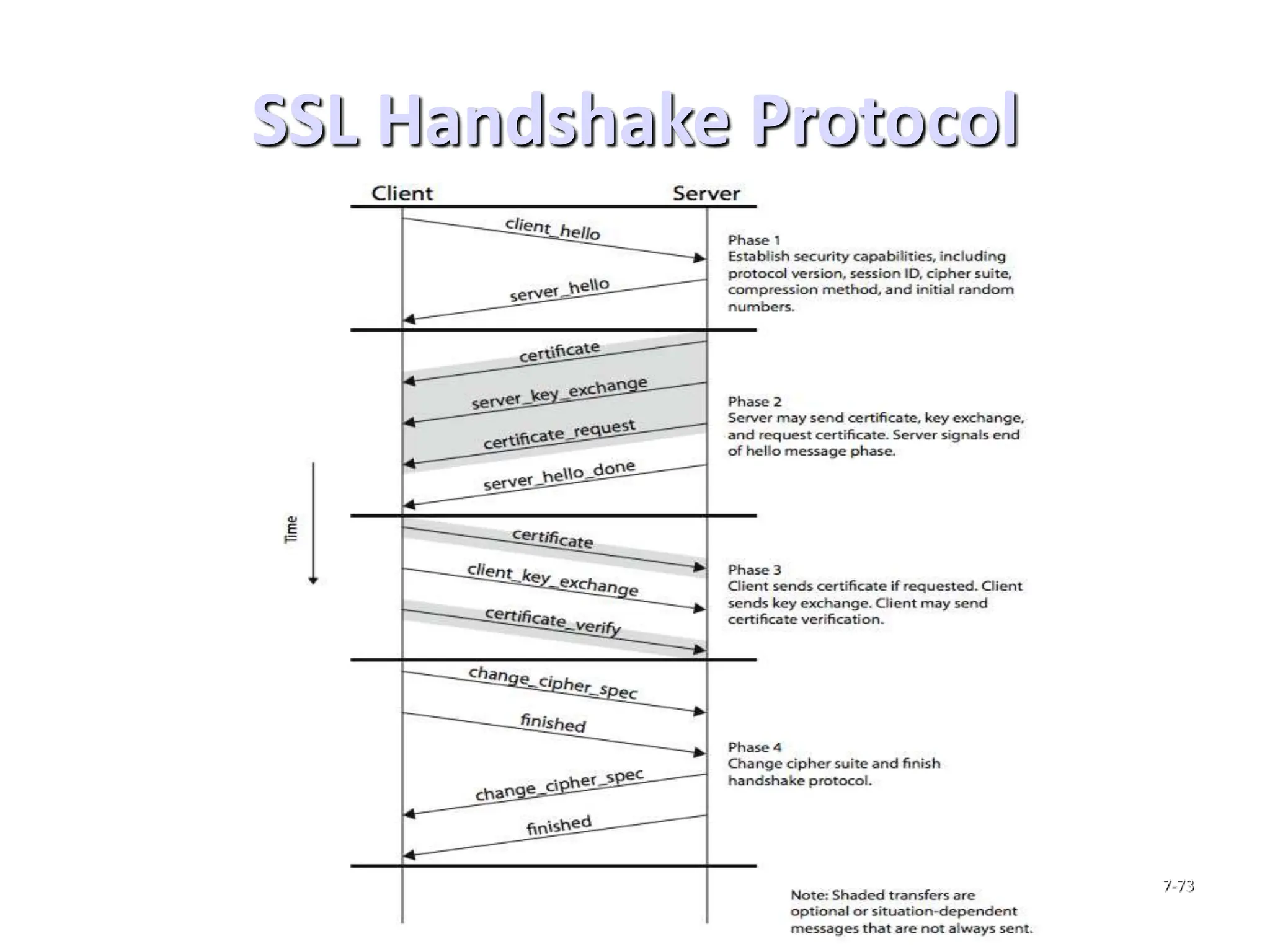
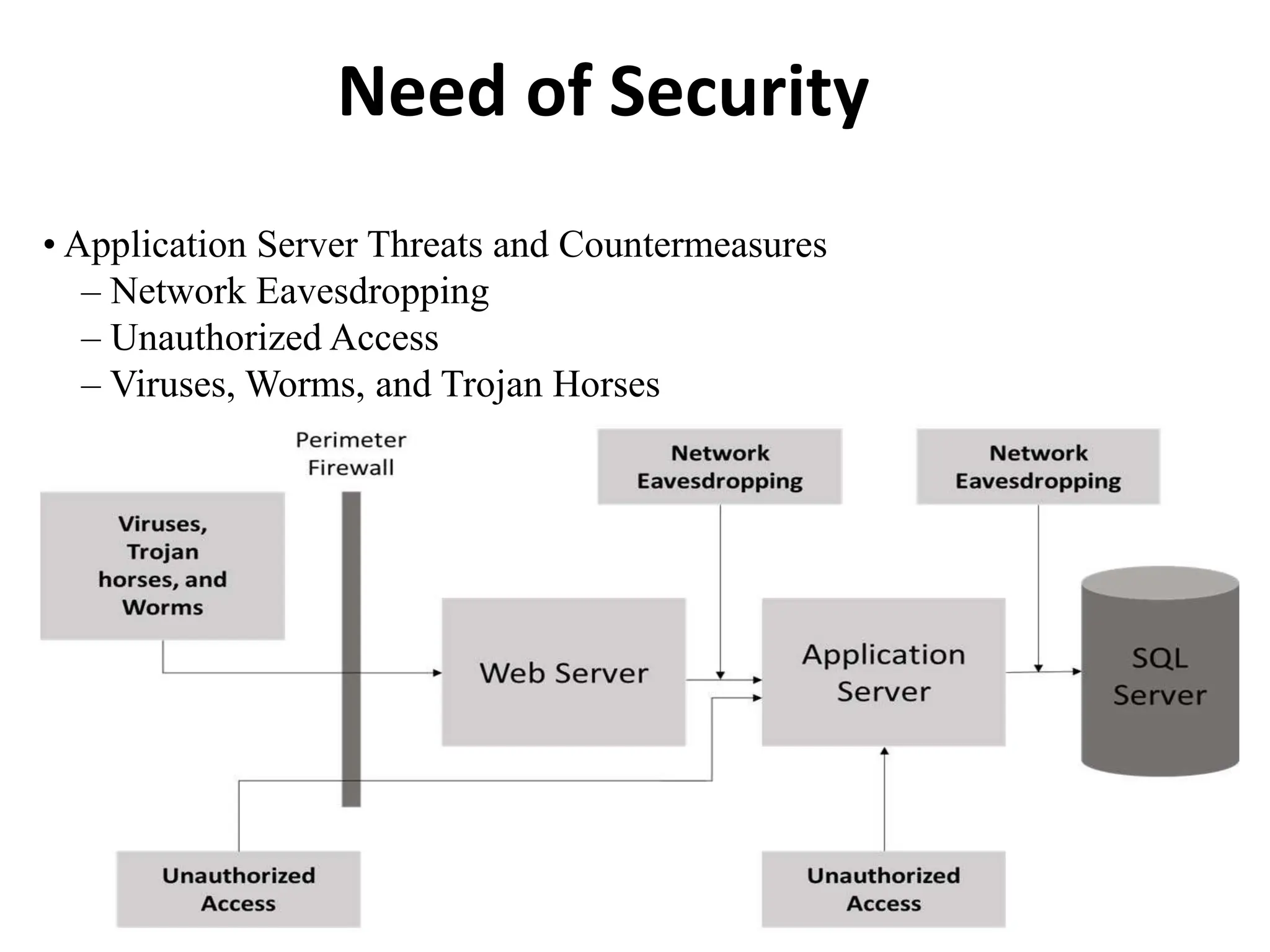
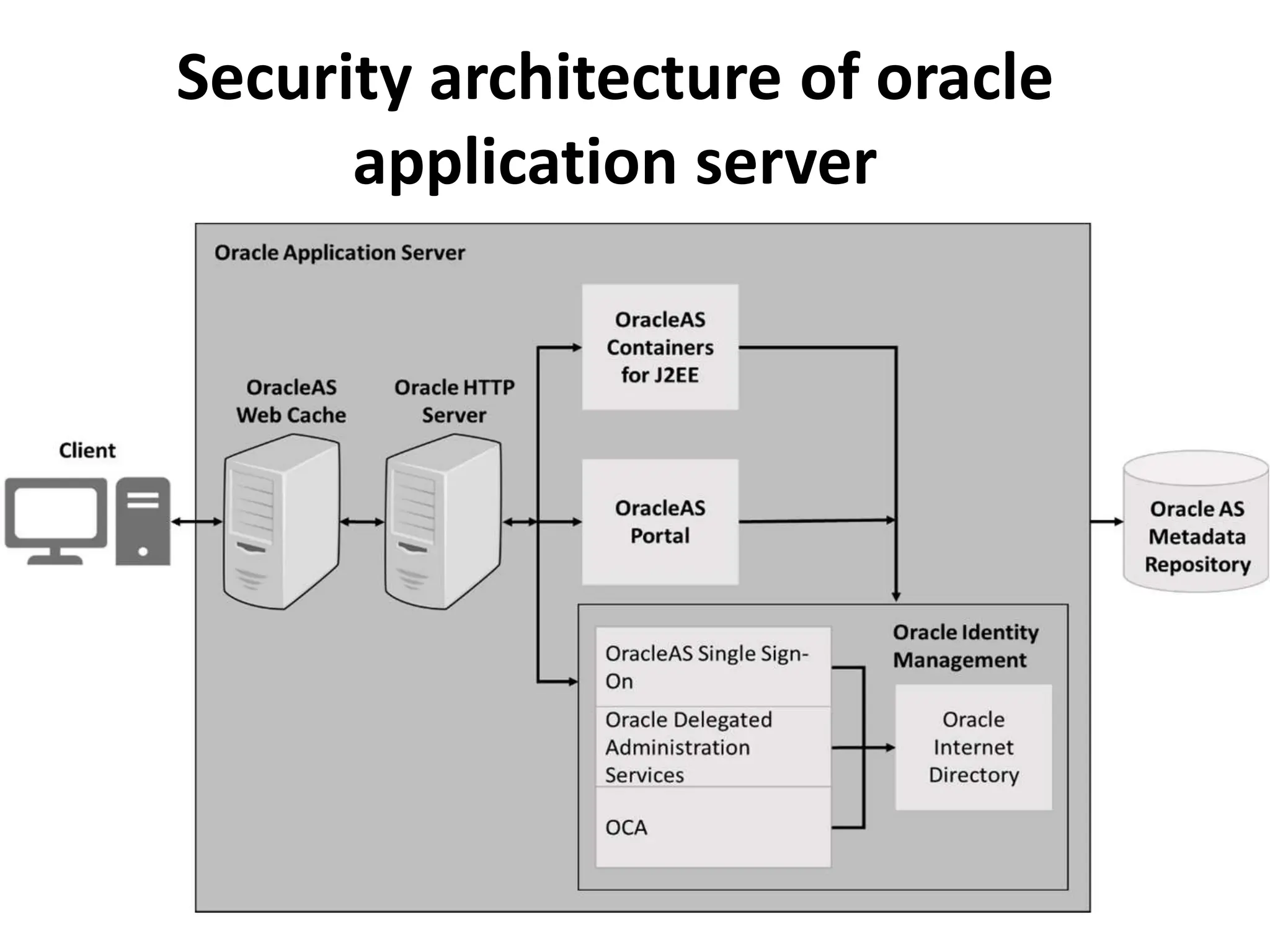
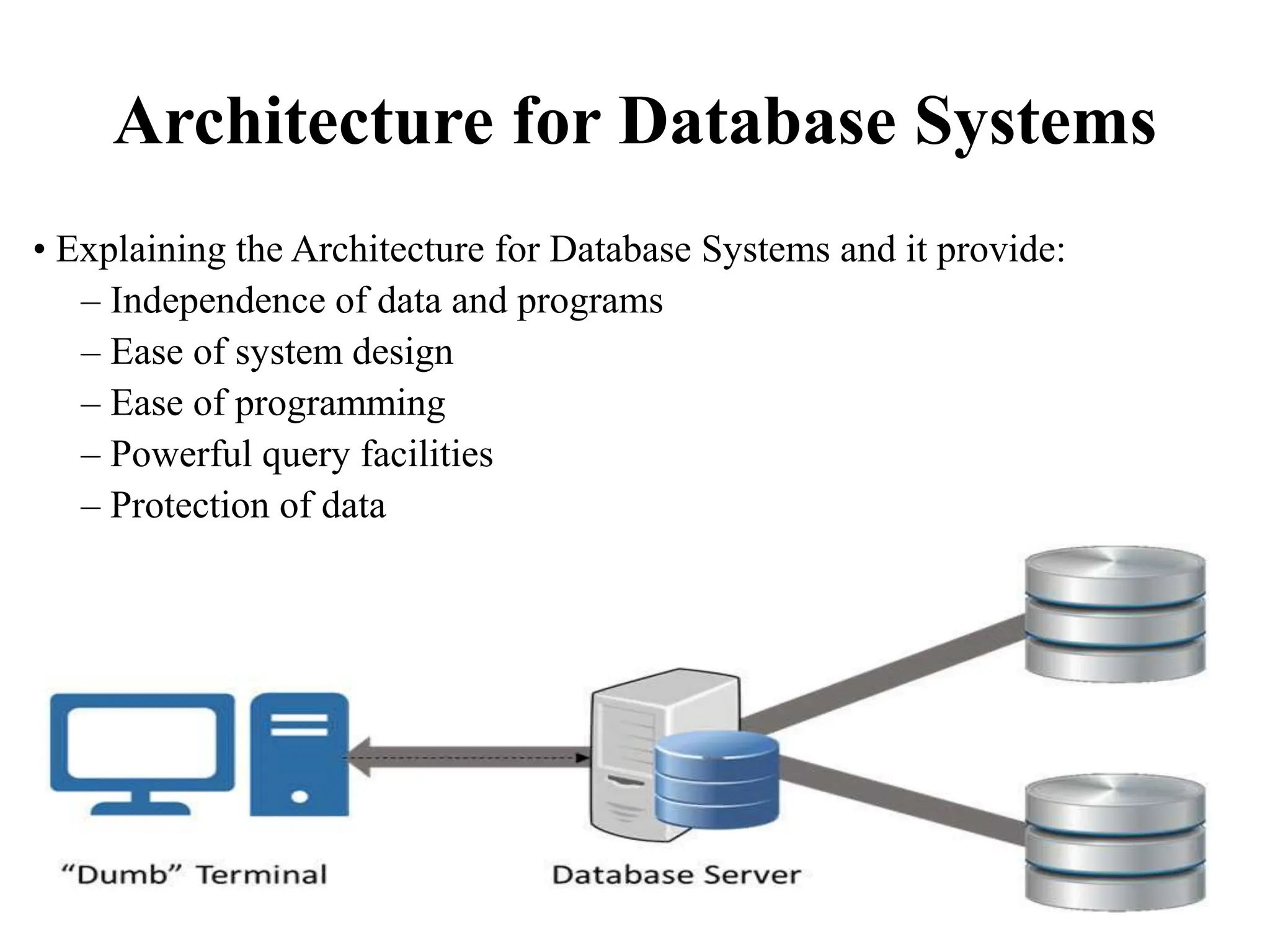
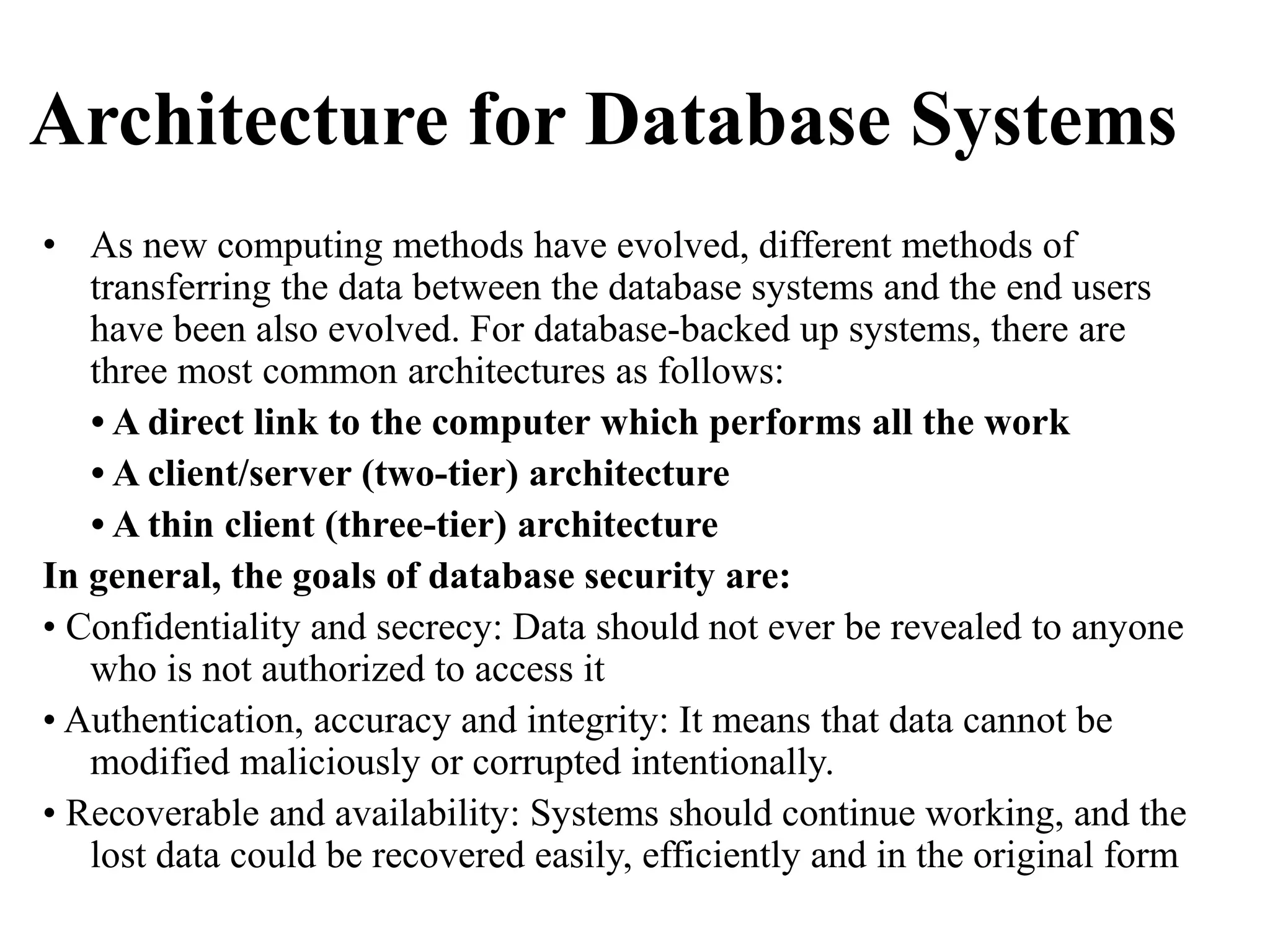
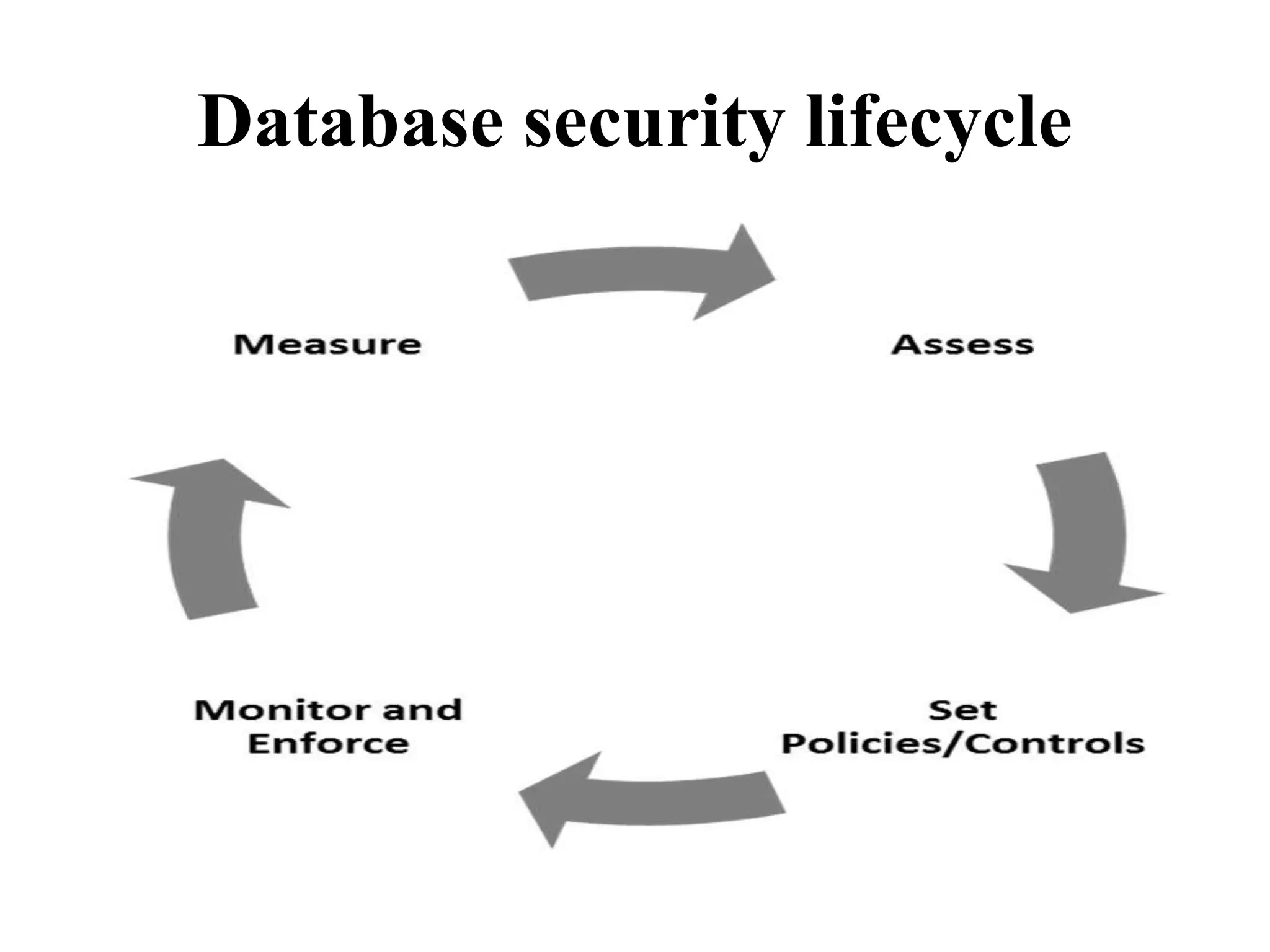
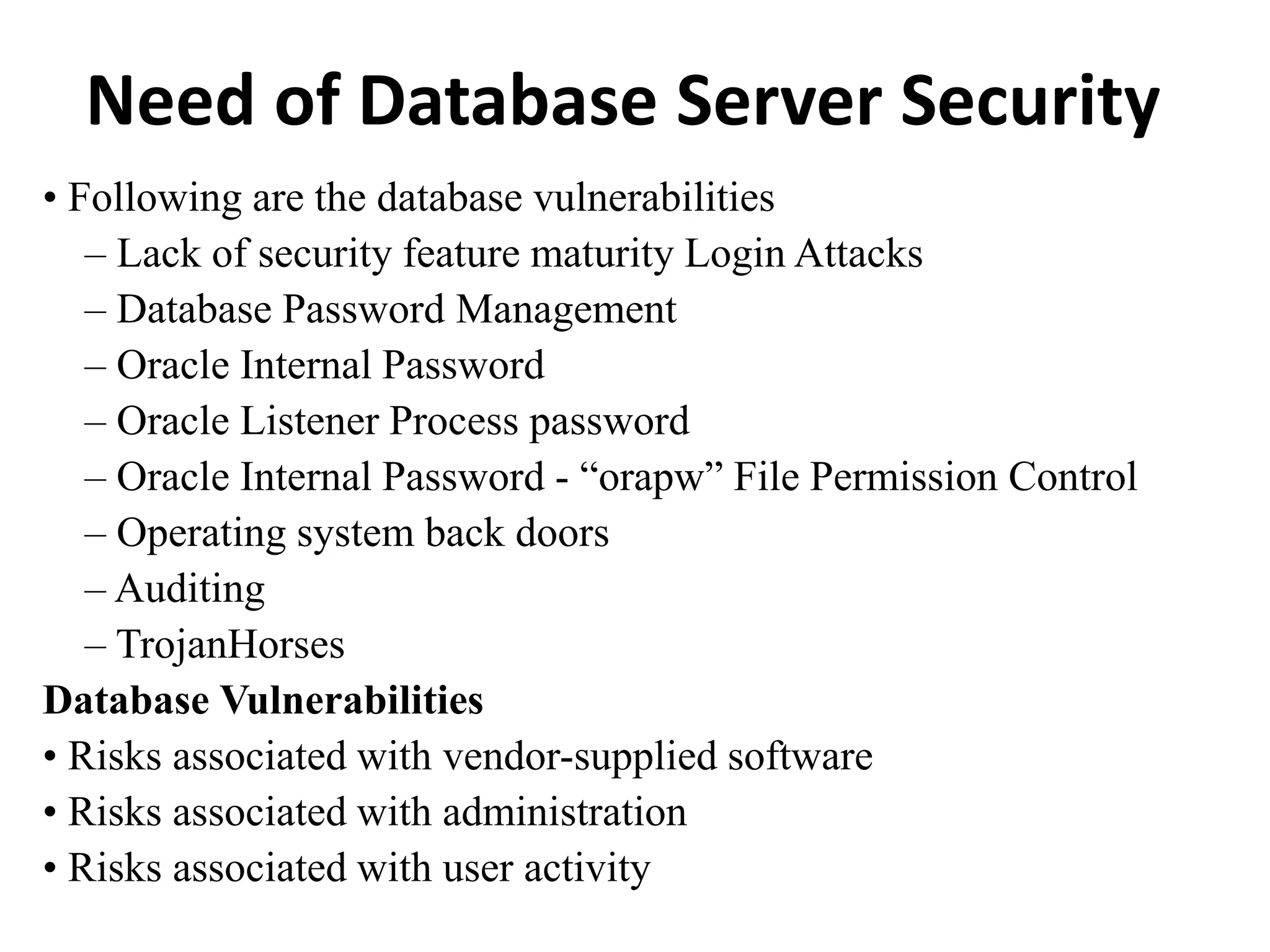
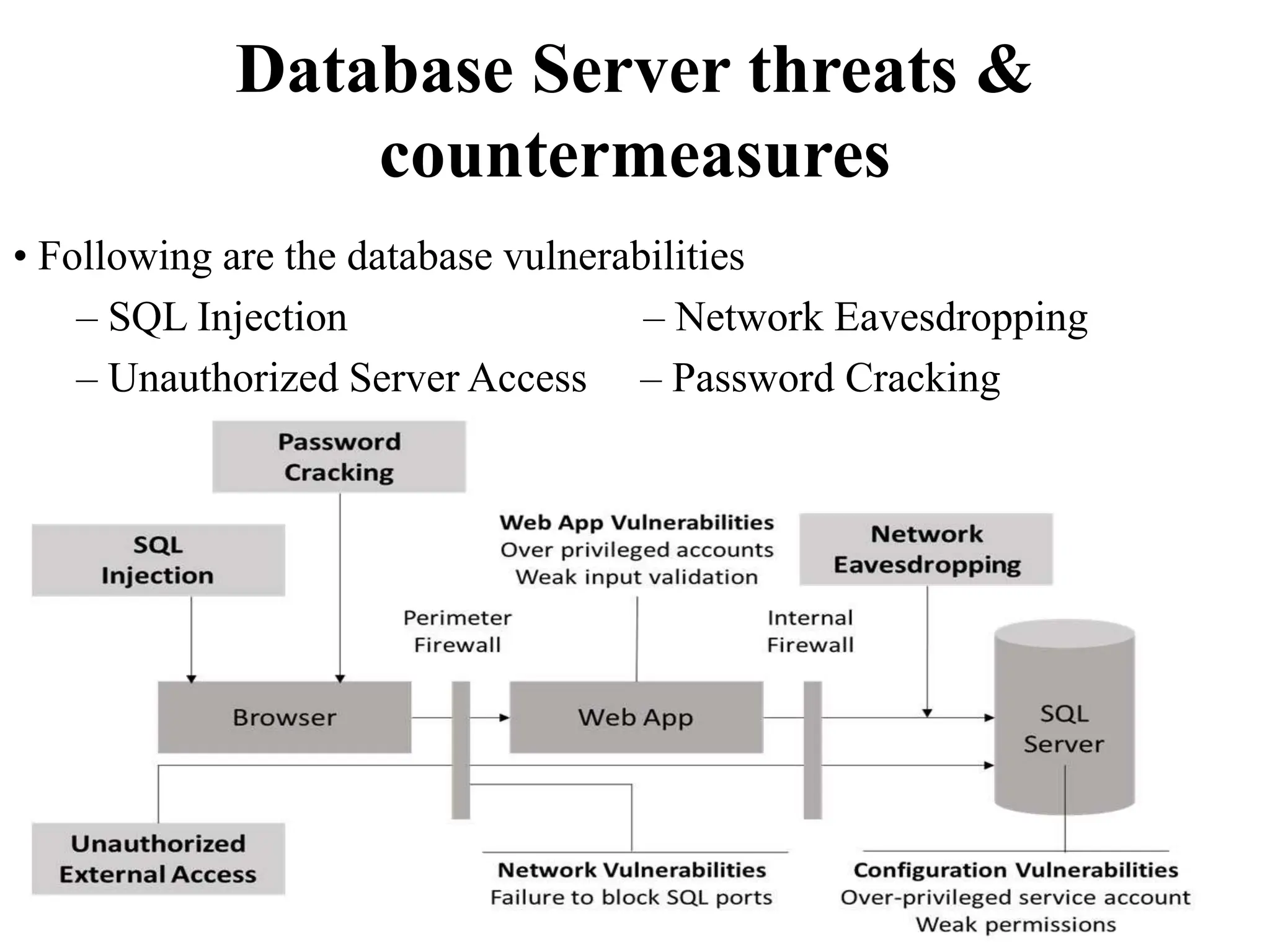
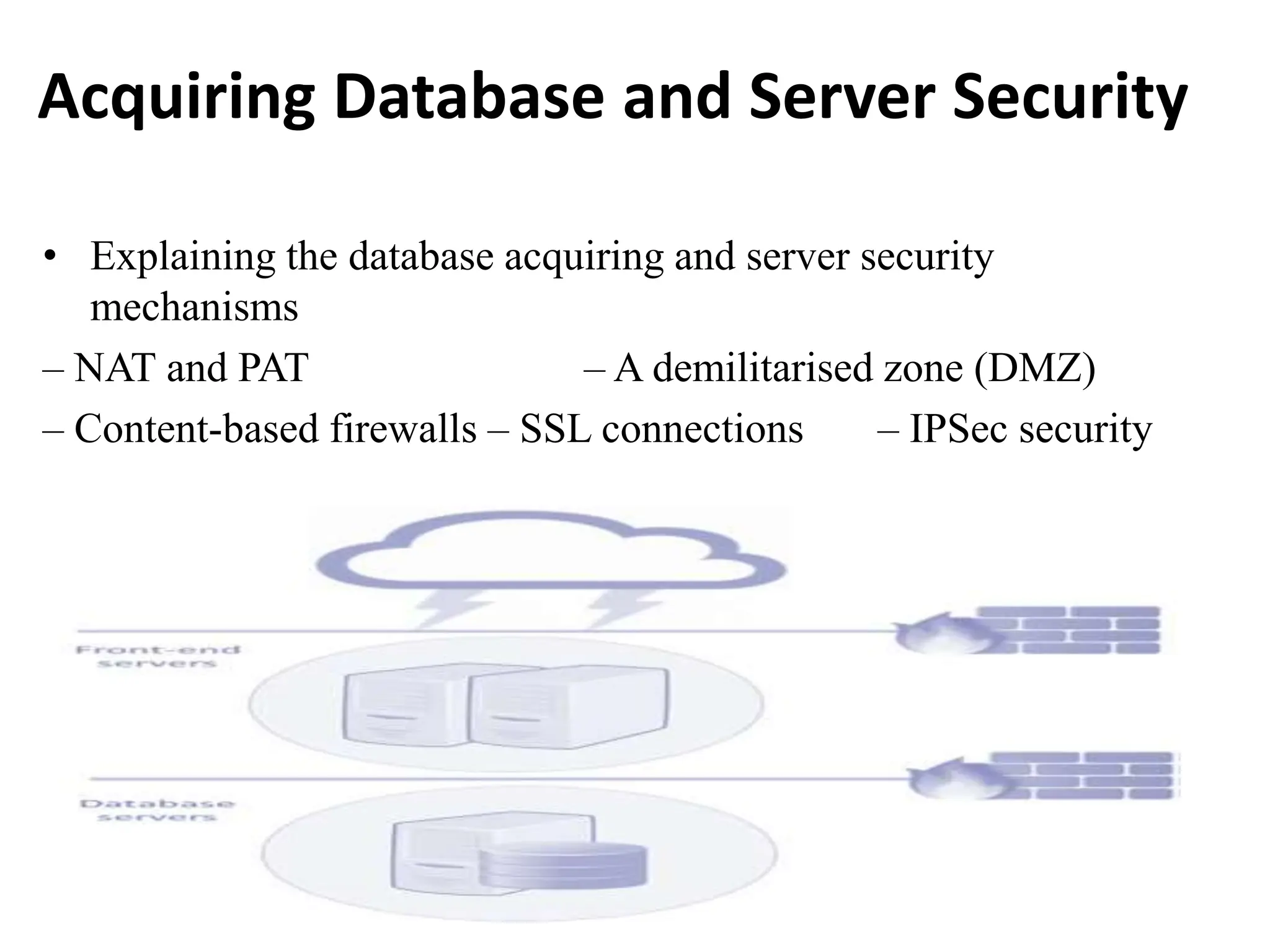
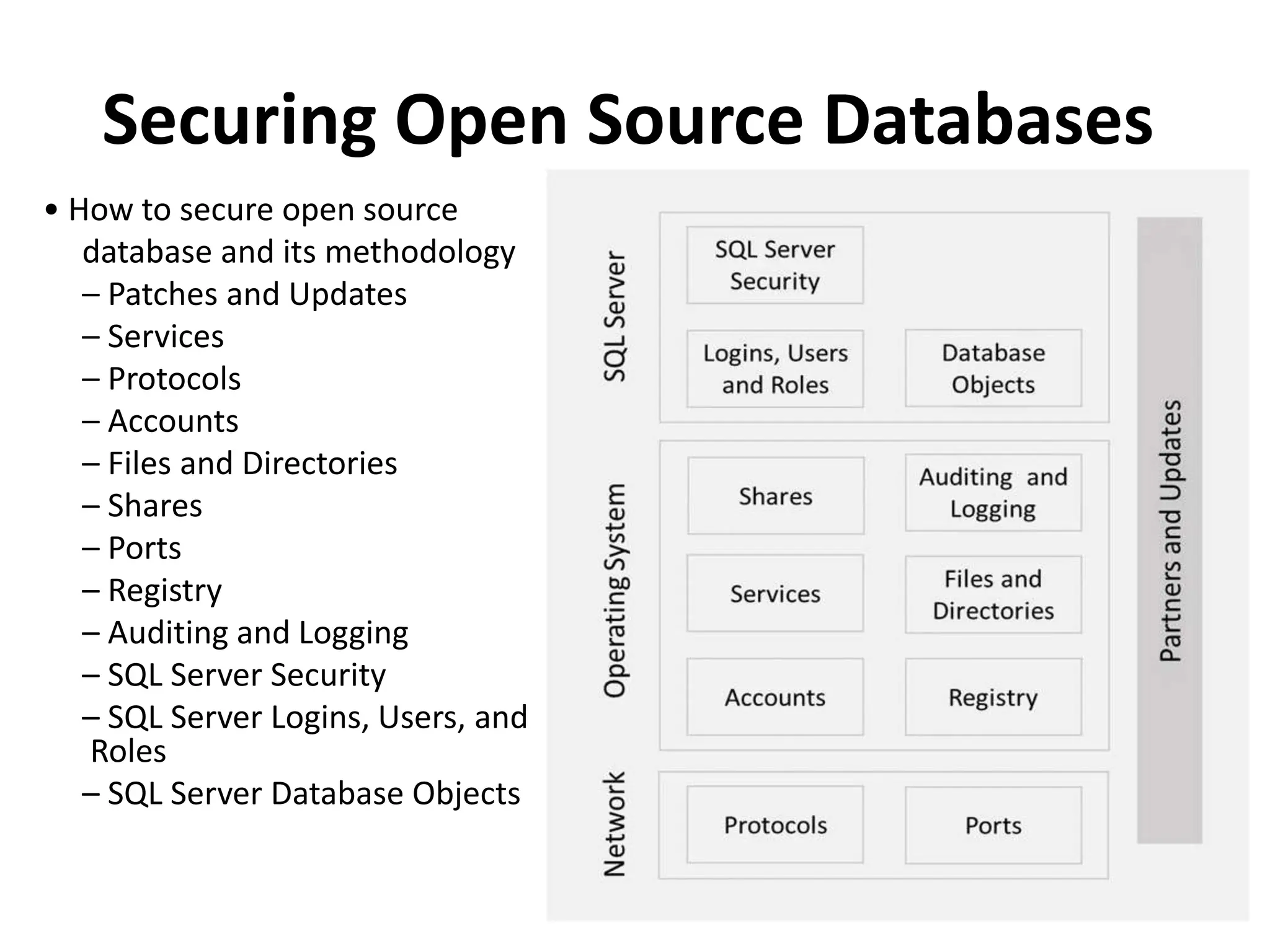
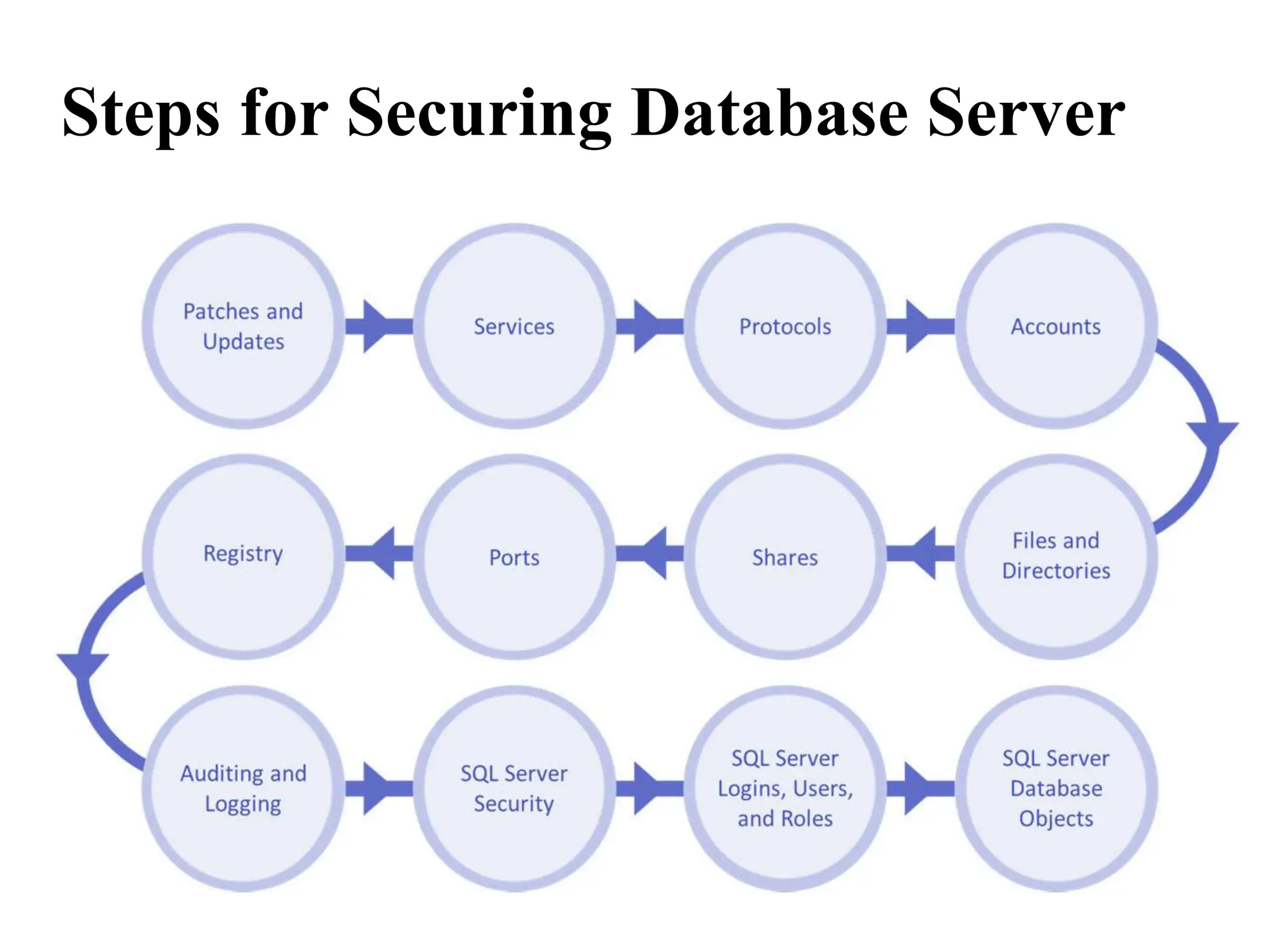
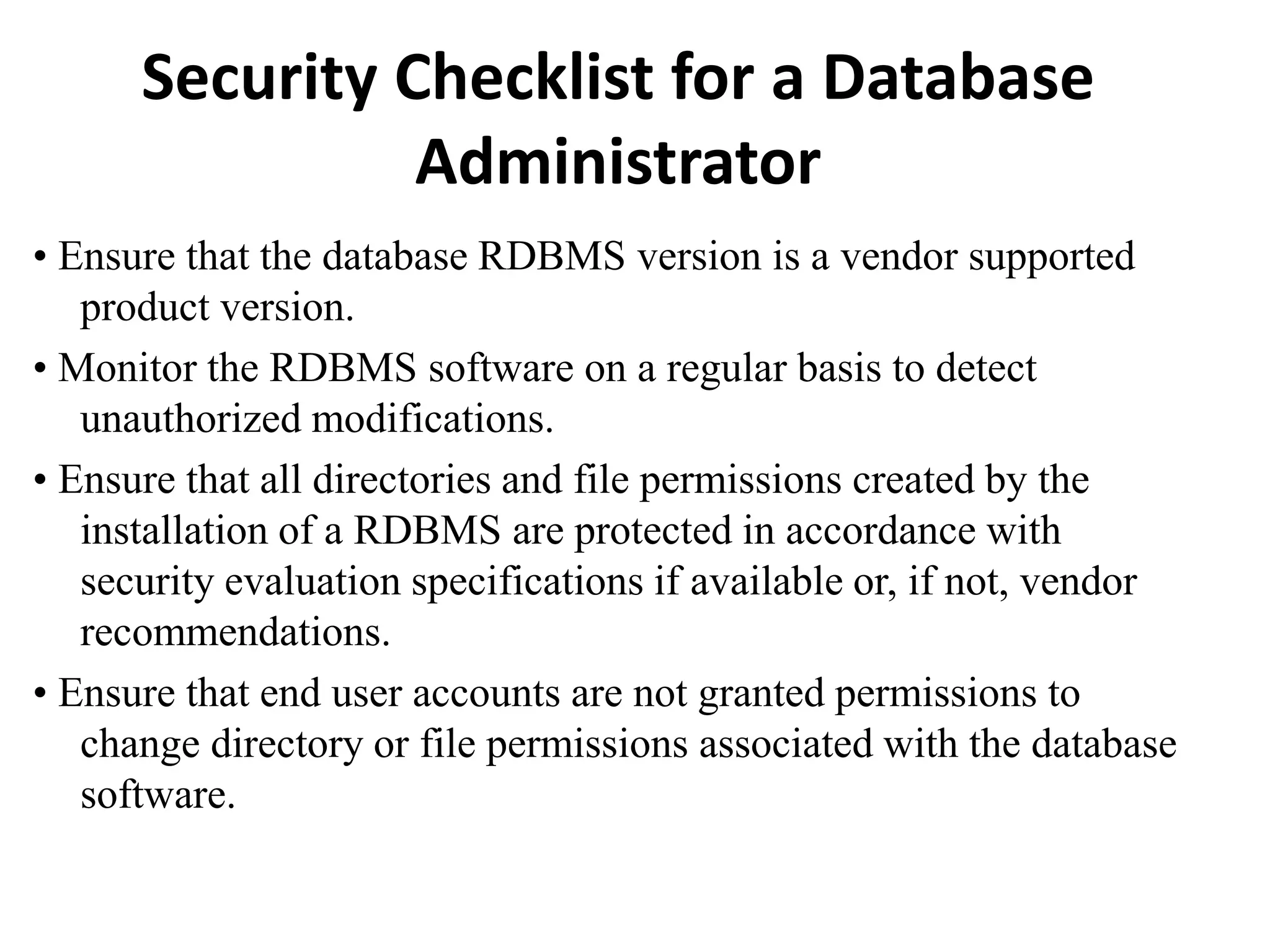
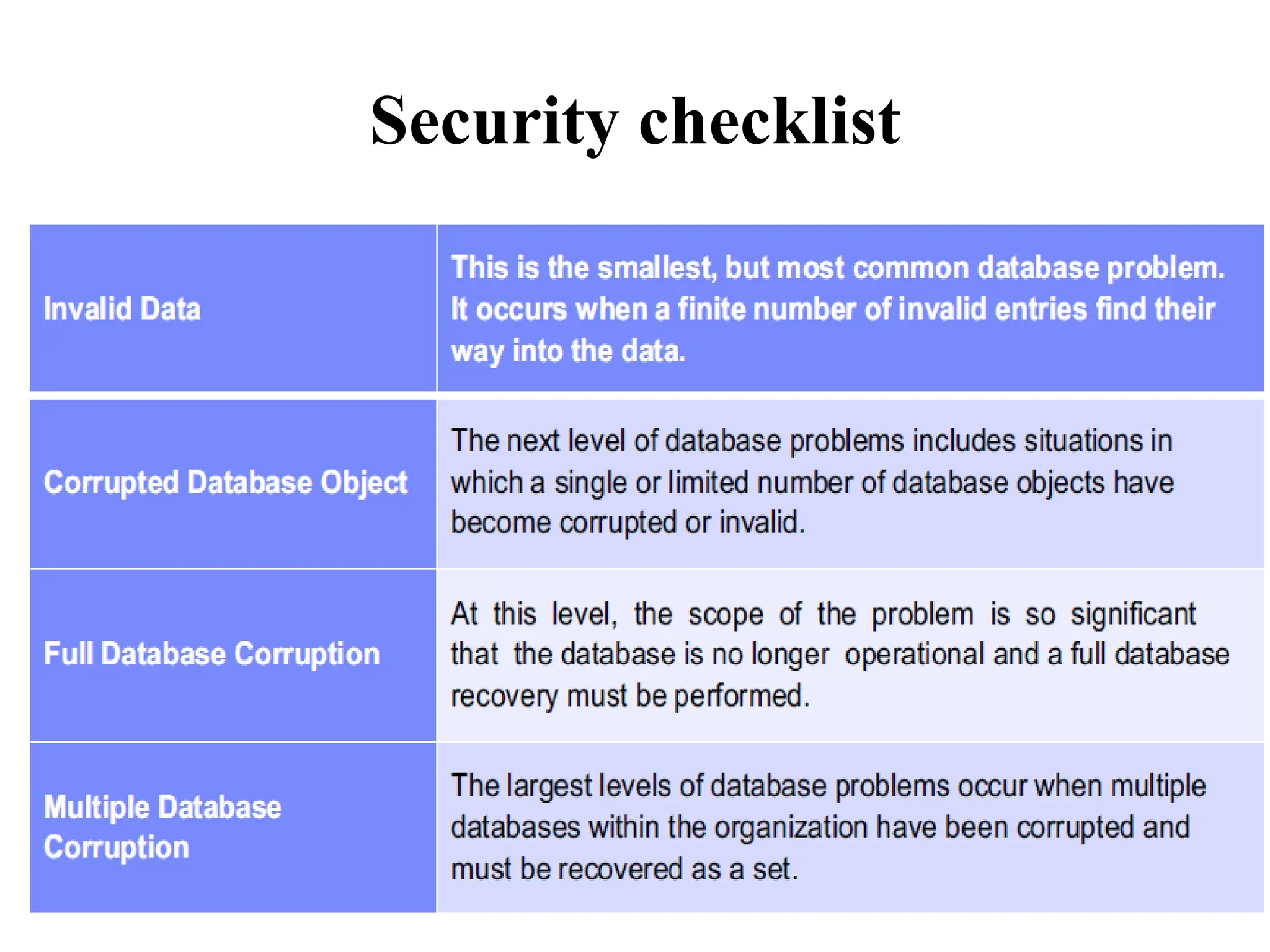
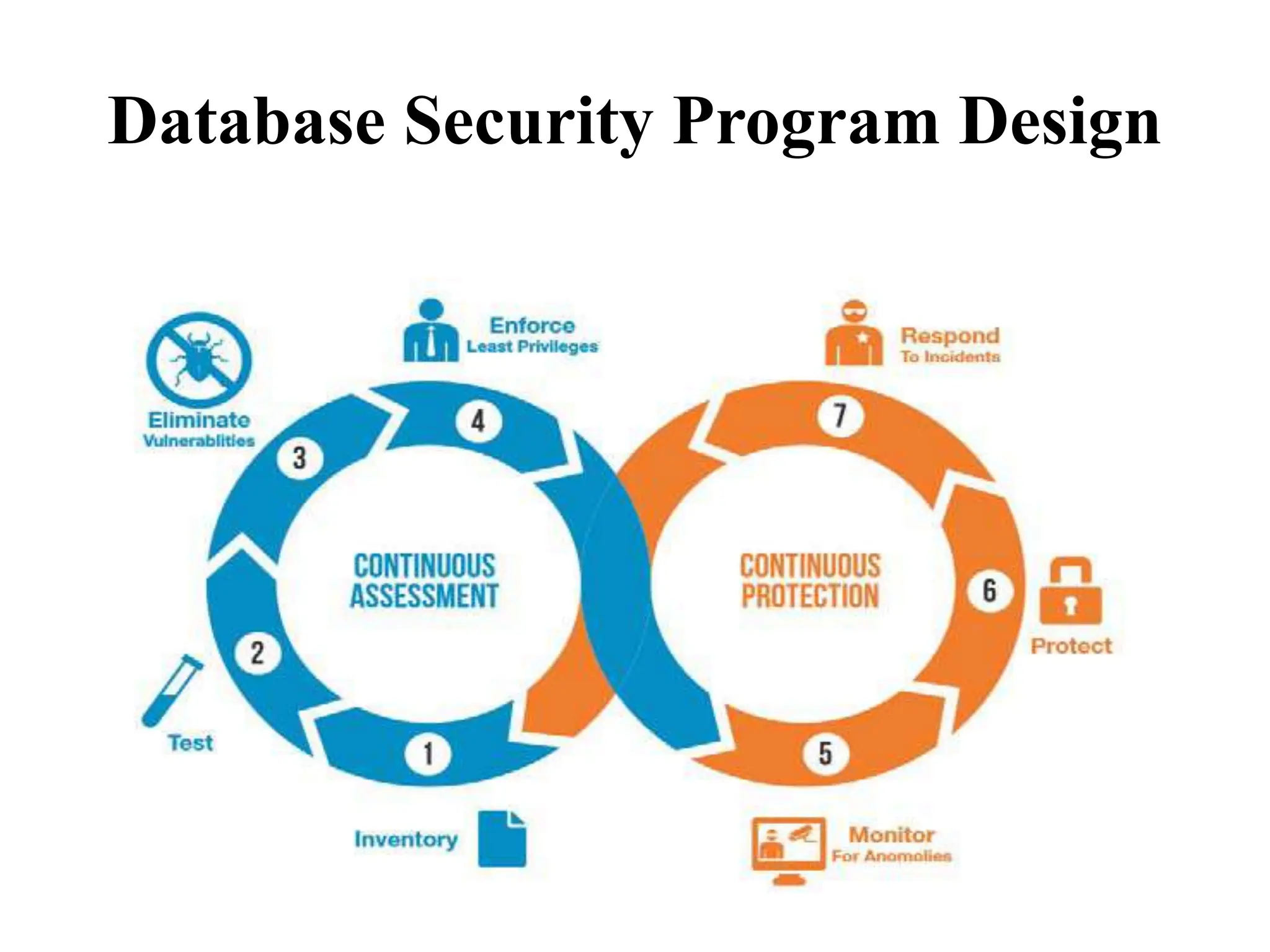
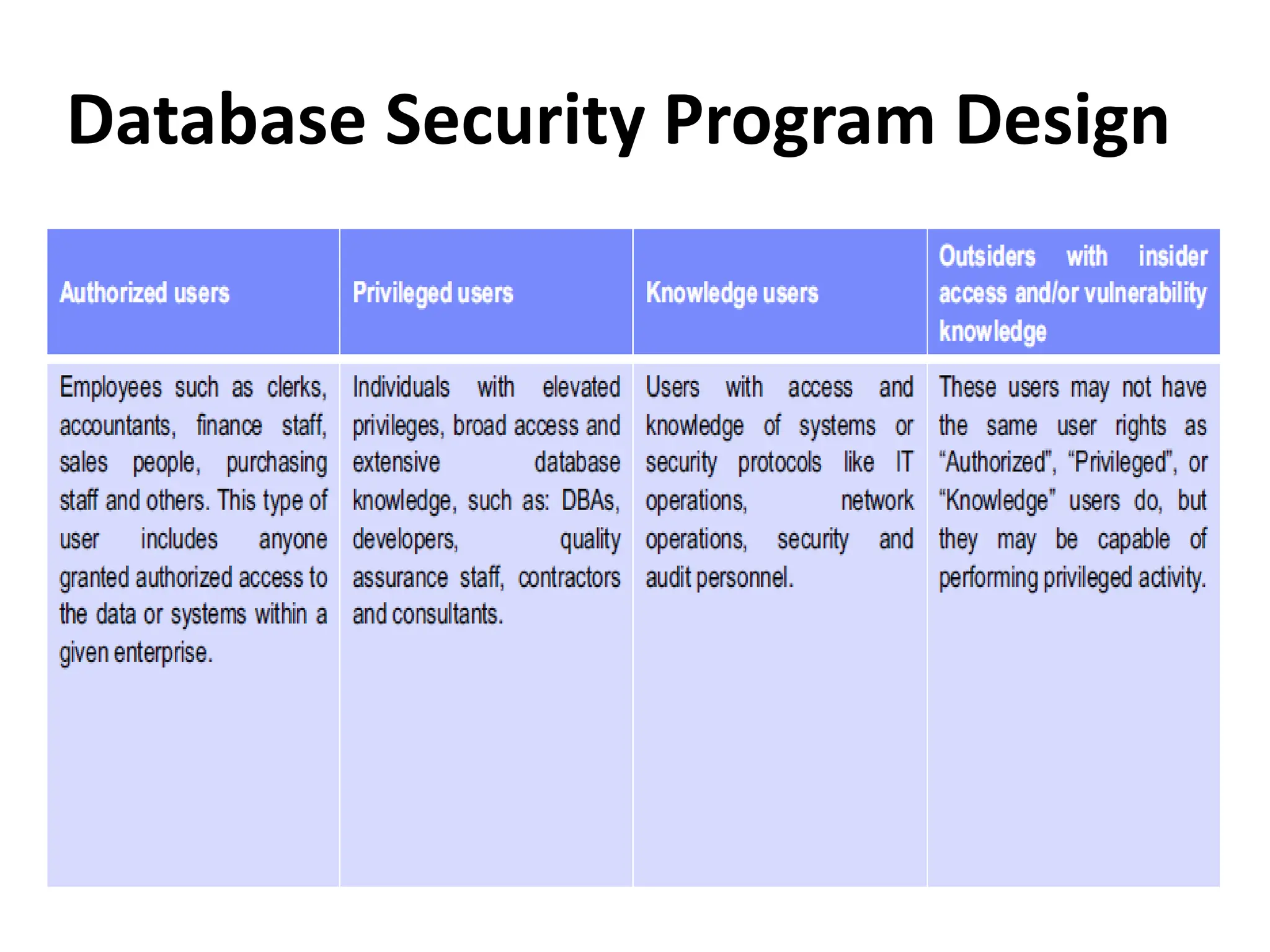
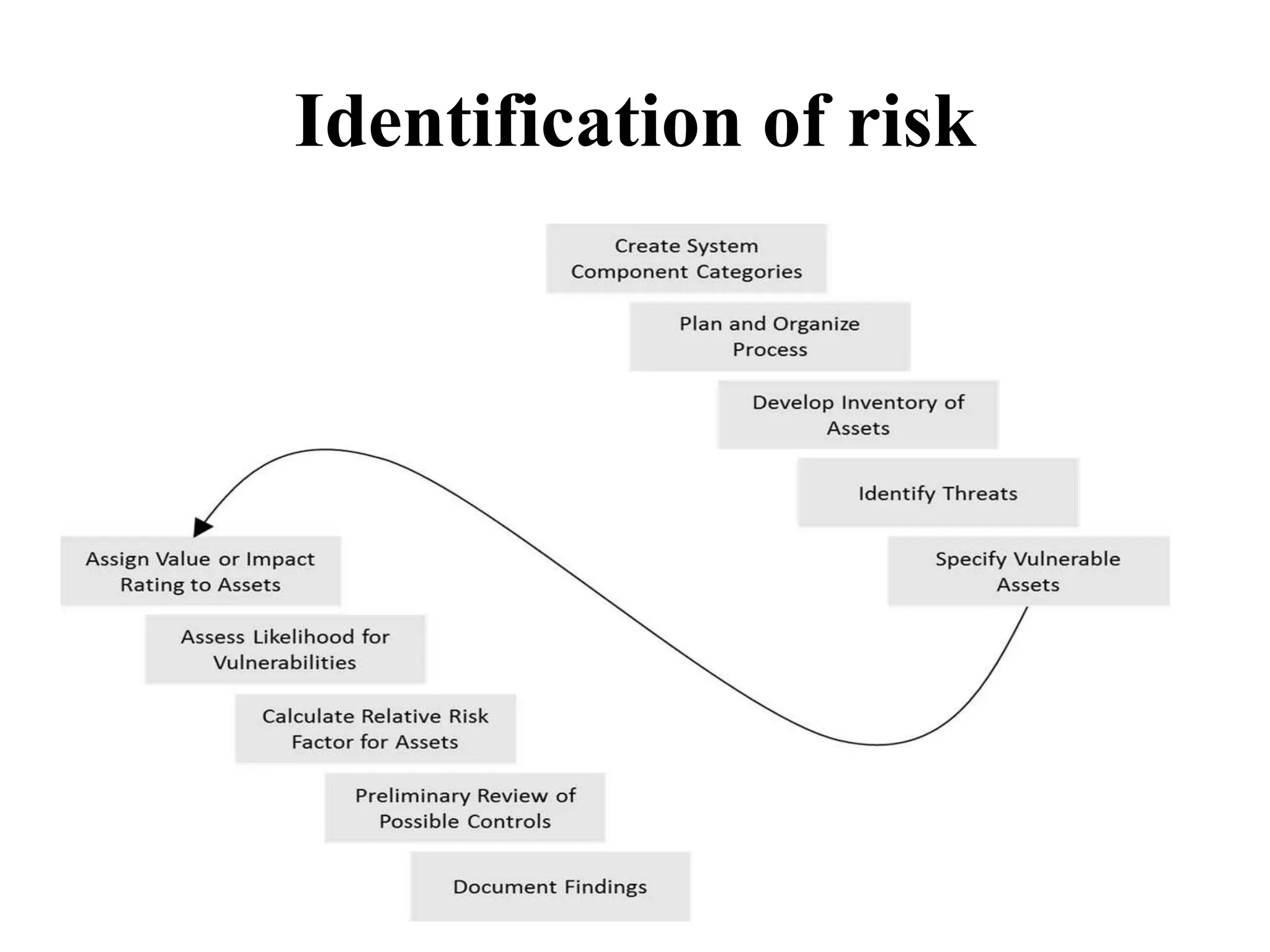
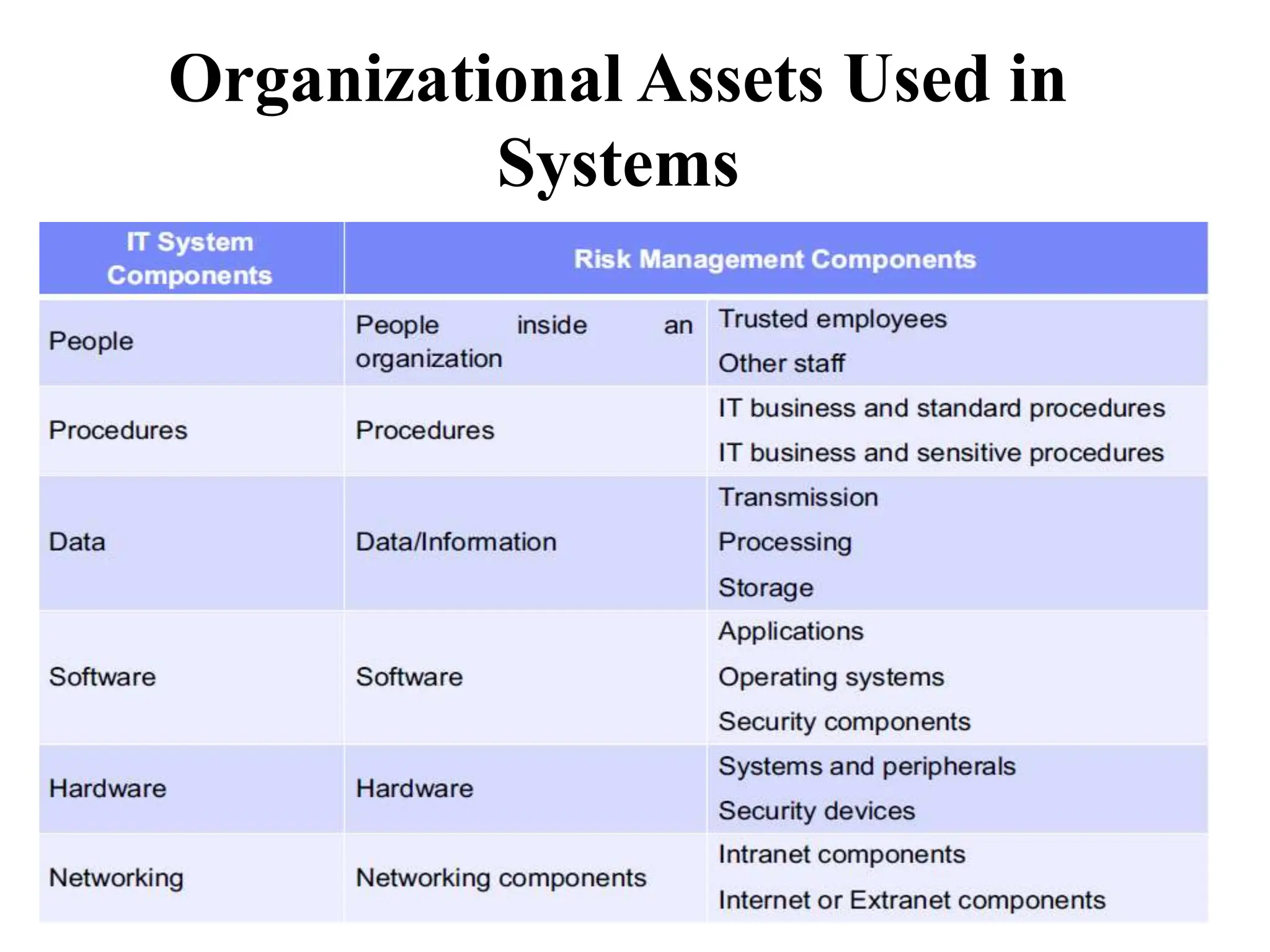
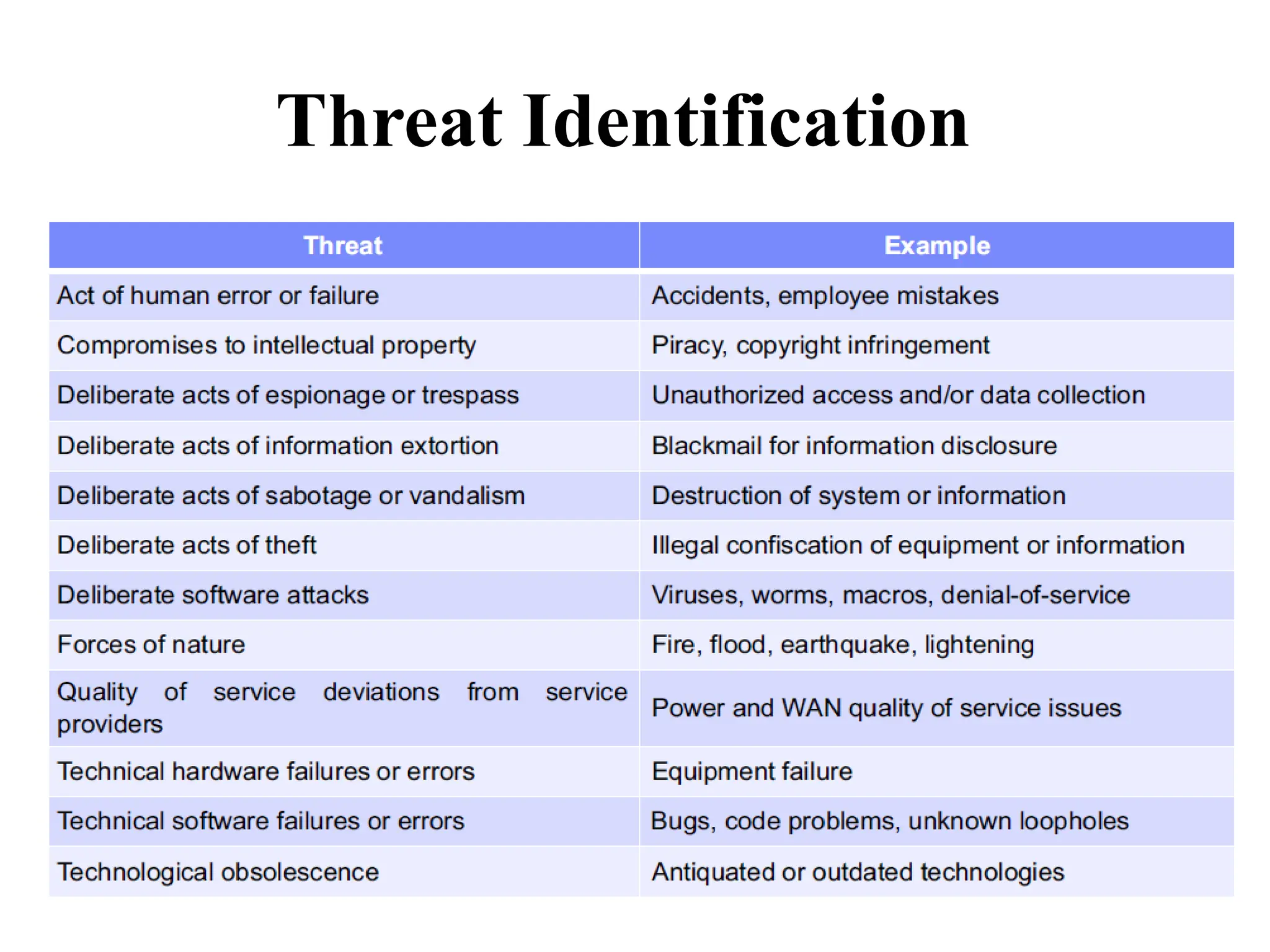
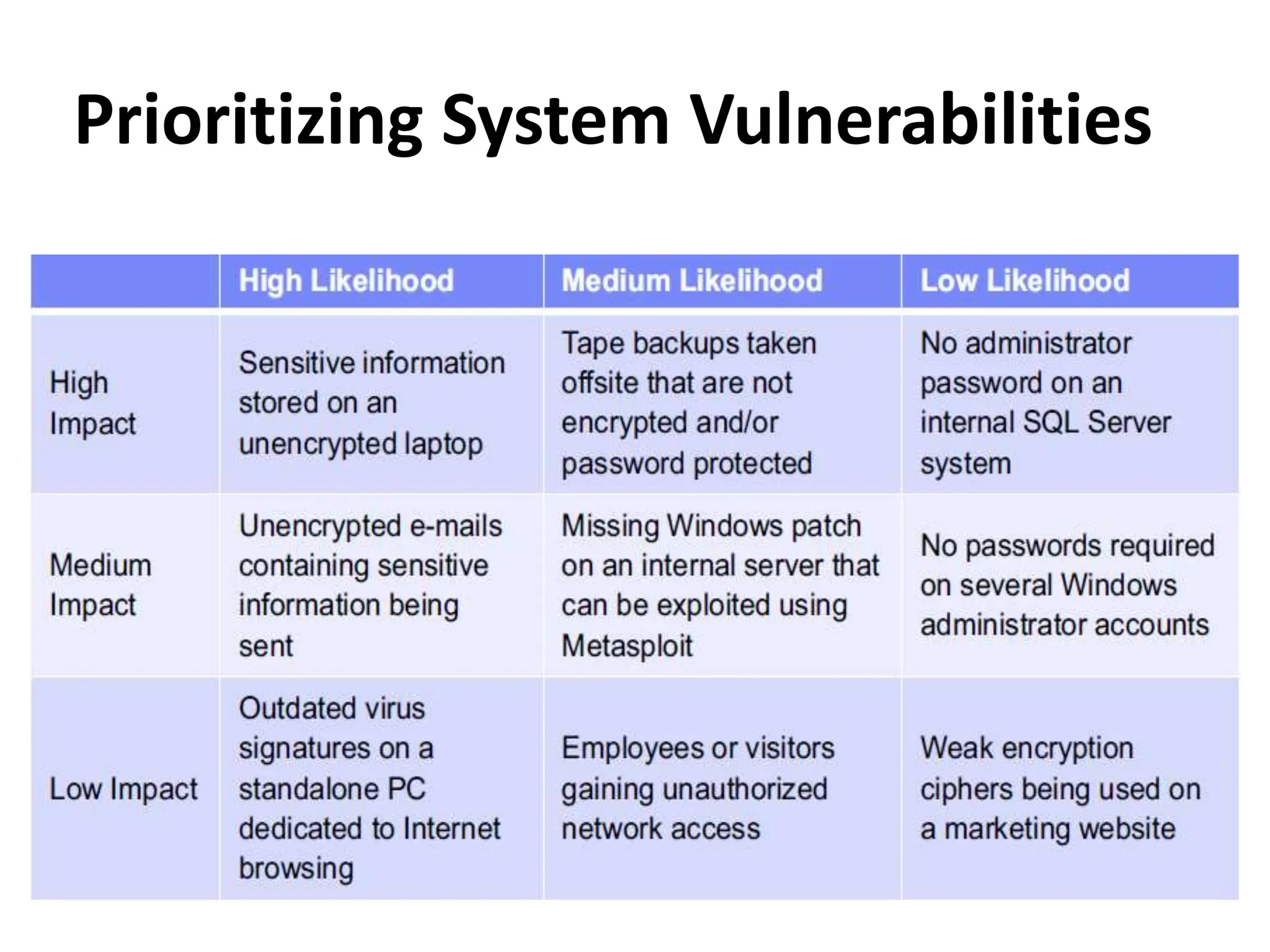
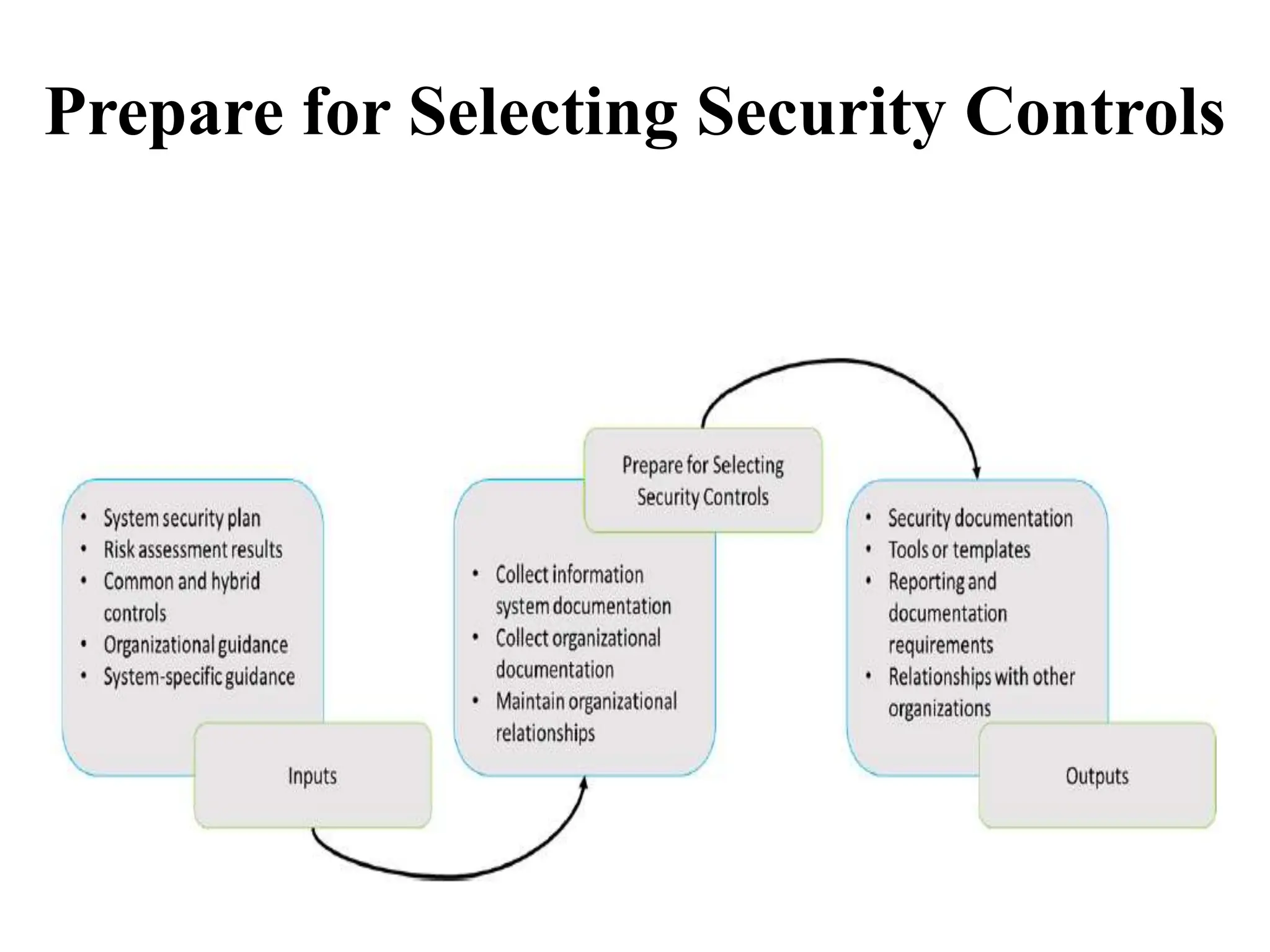
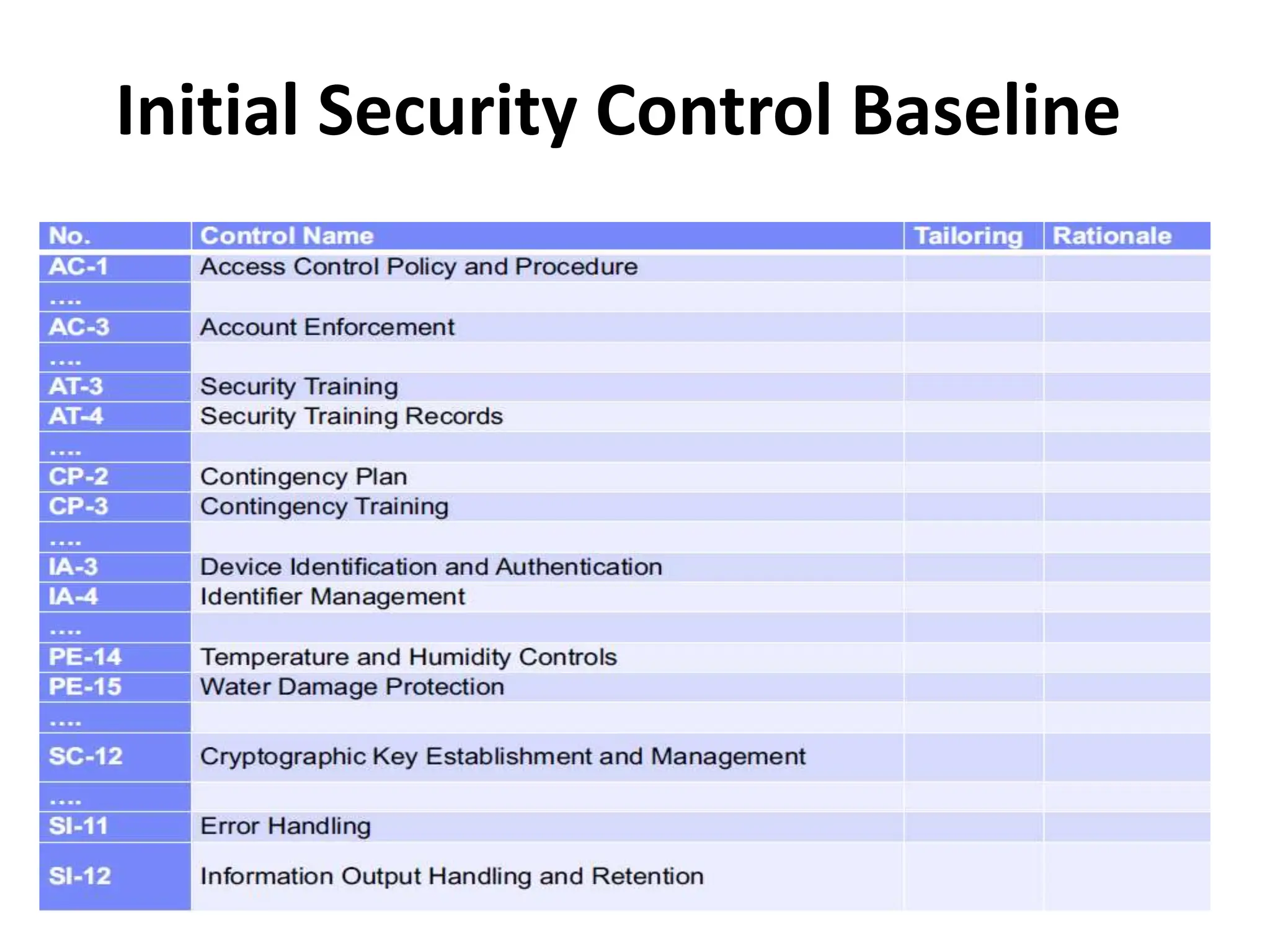
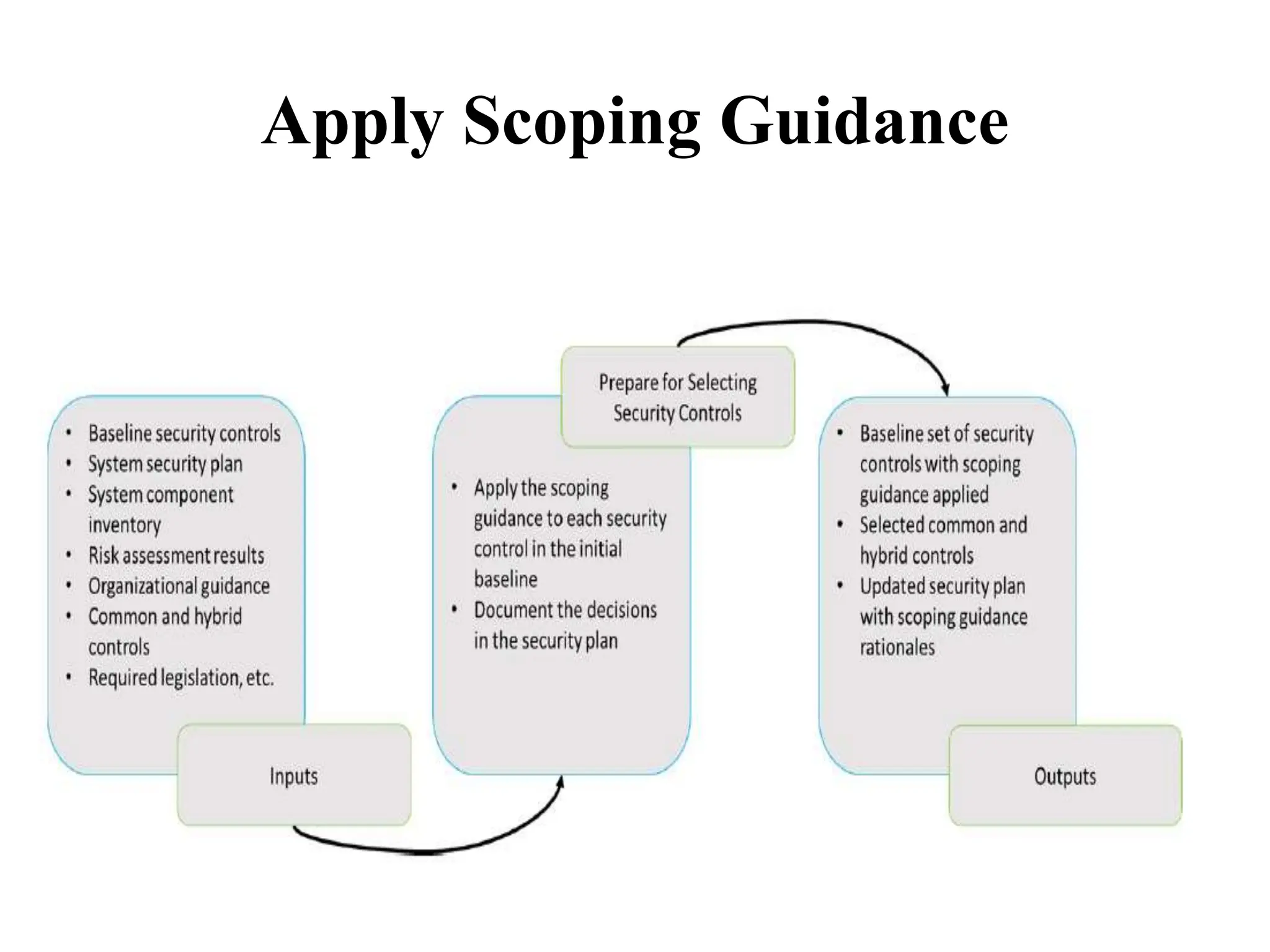
This document discusses security elements and goals in IT systems, including integrity, confidentiality, availability, non-repudiation, and authentication. It also covers threats to IT systems and technical controls like vulnerability management. Operating system security is then discussed, including changing threats, why OS's are hard to secure, trust models, threat models, and key security features like access control and network protection. Application security topics like malware protection, application verification, sandboxing, and execution are also summarized.