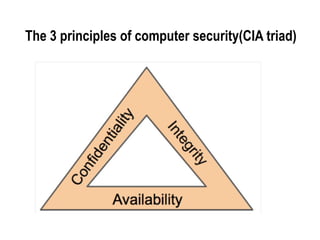
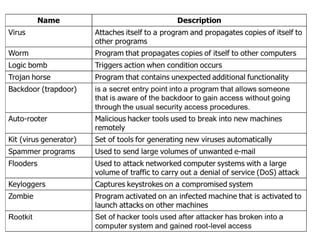
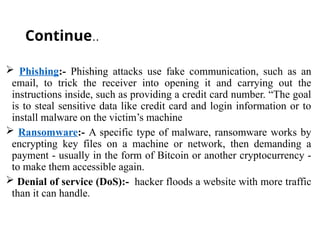
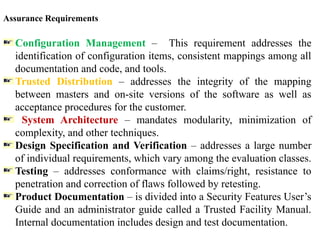
The document provides an outline for an exit exam tutor session at Injibara University, focusing on key concepts of computer security, including vulnerabilities, security requirements for trusted operating systems, and techniques for database integrity and protection. It discusses the CIA triad of computer security—confidentiality, integrity, and availability—and outlines common threats like phishing and ransomware, as well as the importance of independent evaluation for security systems. Additionally, it emphasizes the need for database security practices to safeguard data management systems from cyberattacks and ensure reliability.