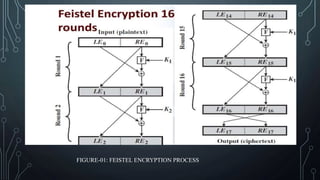
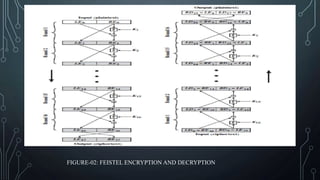
This presentation introduces Feistel encryption and decryption. It discusses the Feistel cipher structure which partitions the input block into two halves and processes them through multiple rounds of substitution and permutation. It shows diagrams of the Feistel encryption and decryption processes. It also covers the design features of Feistel networks such as block size, key size, number of rounds, and sub-key generation. Finally, it provides an example of the round function that performs a bitwise XOR of the left half and output of a function applied to the right half and sub-key.