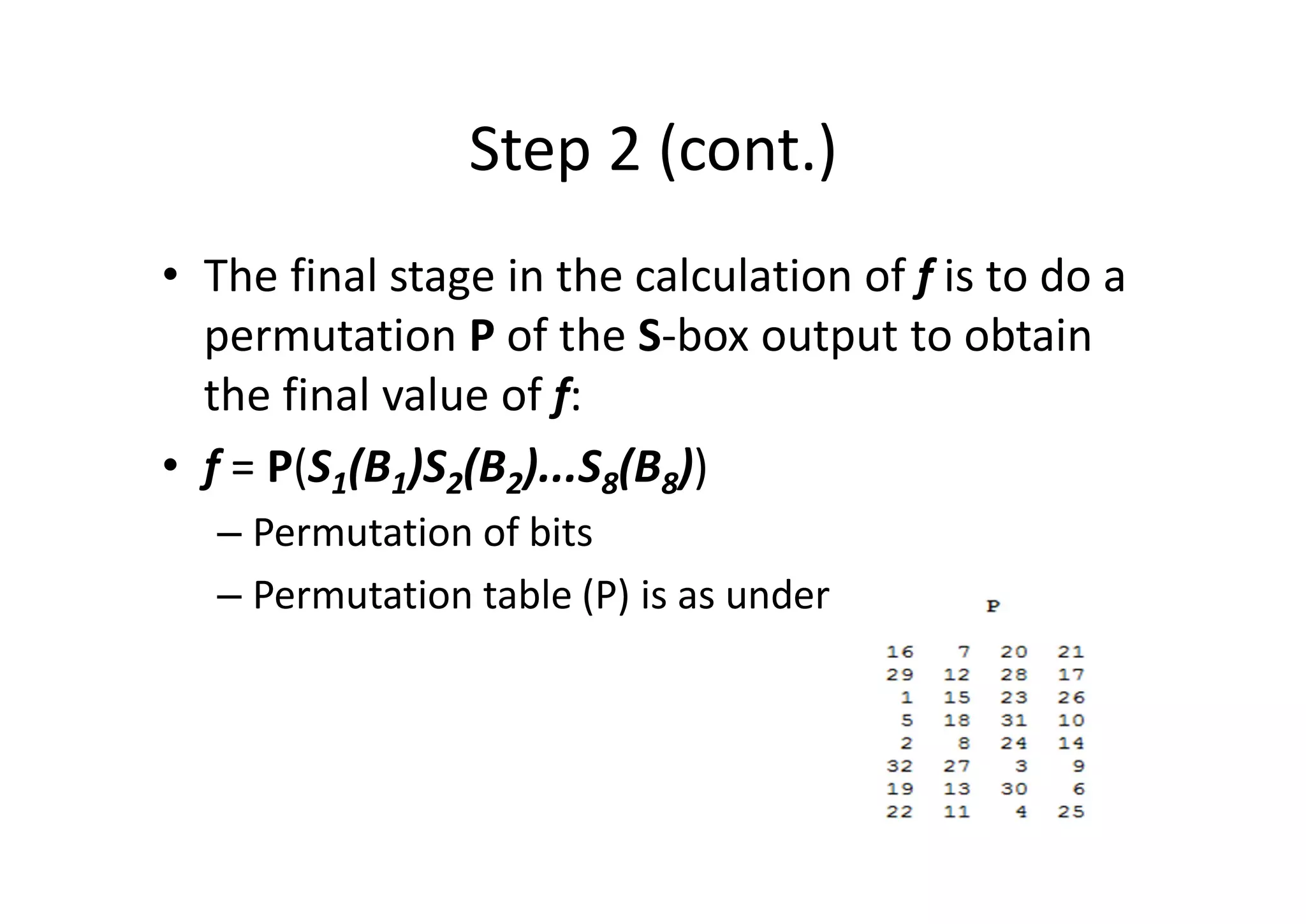
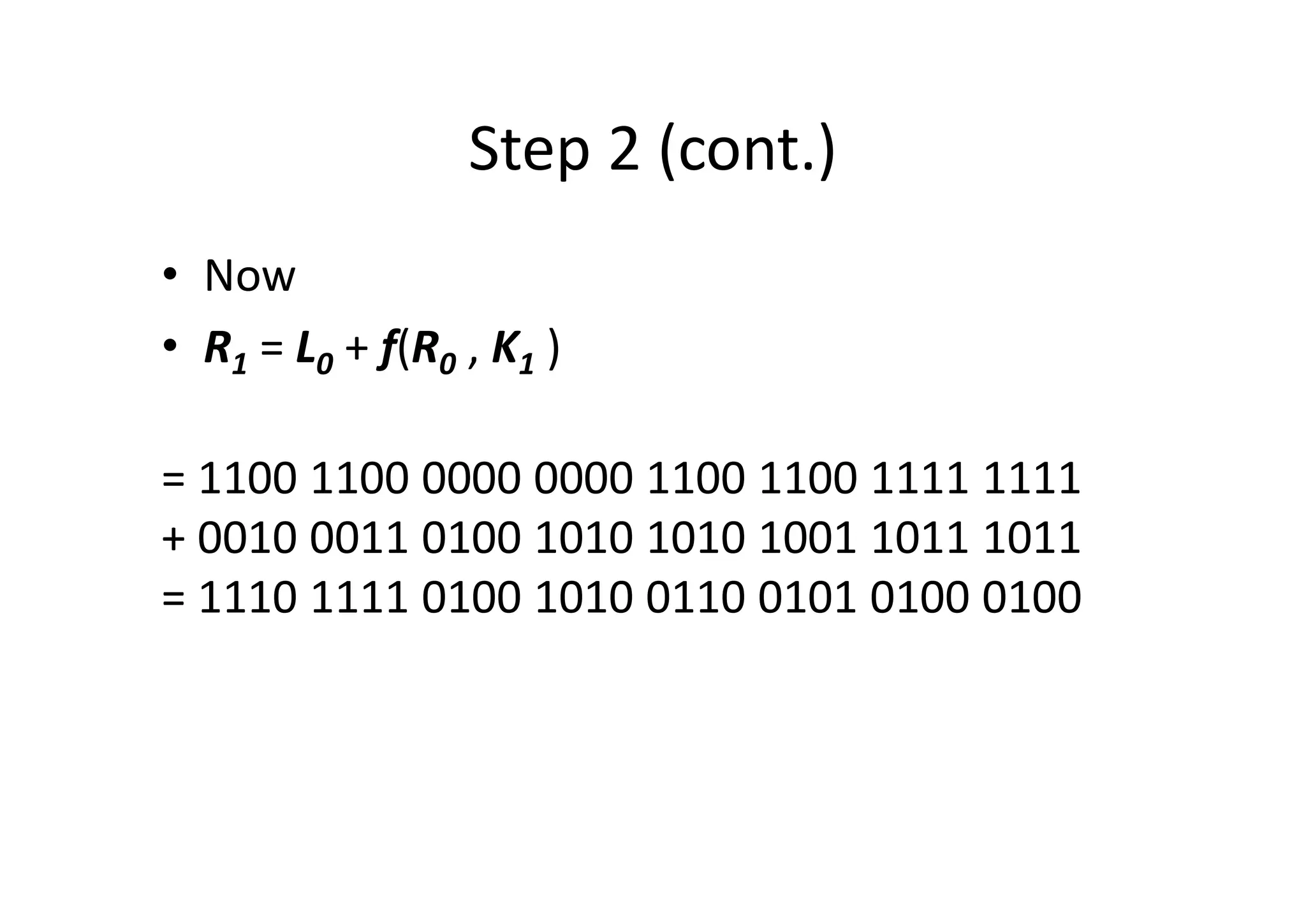
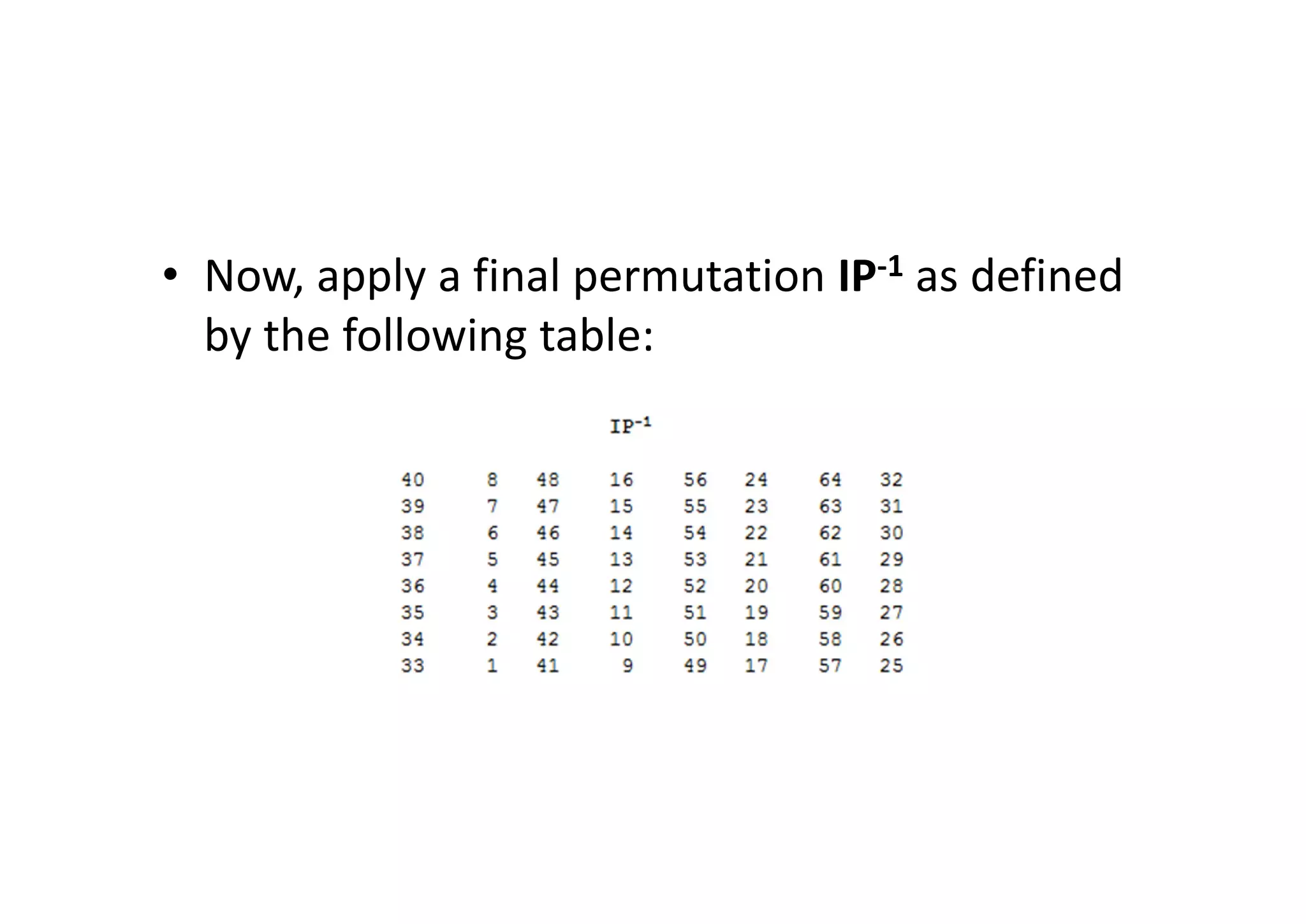
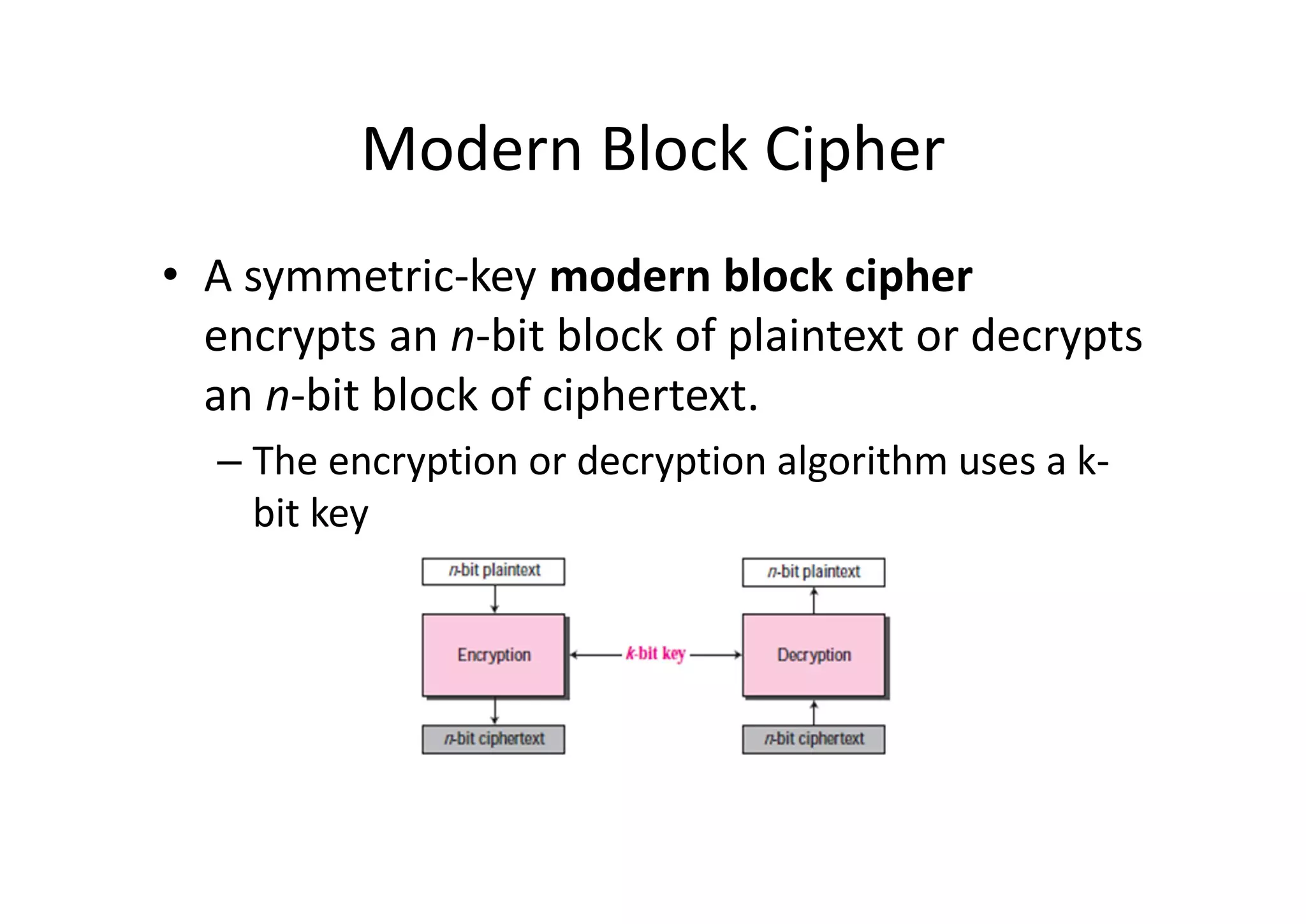
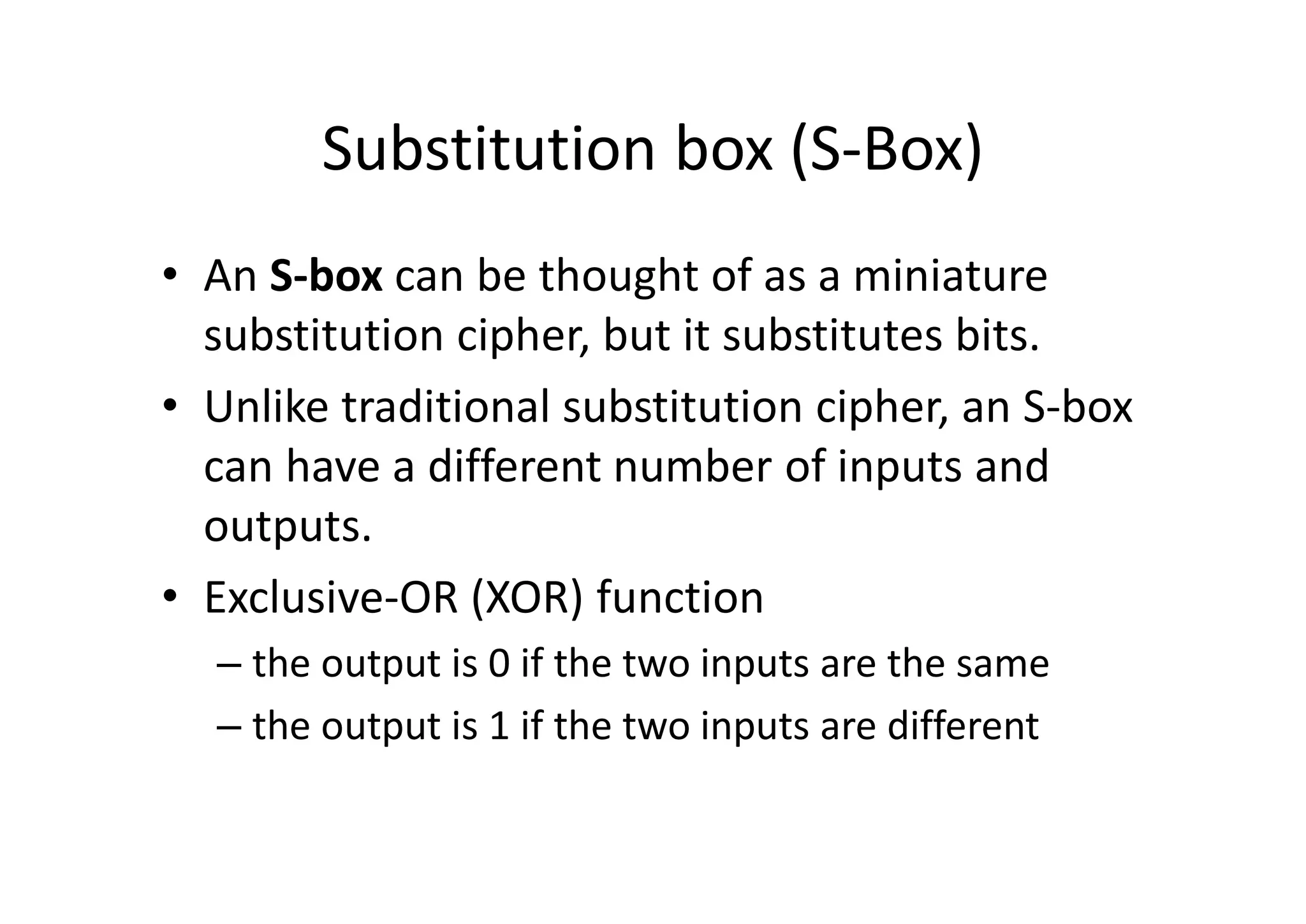
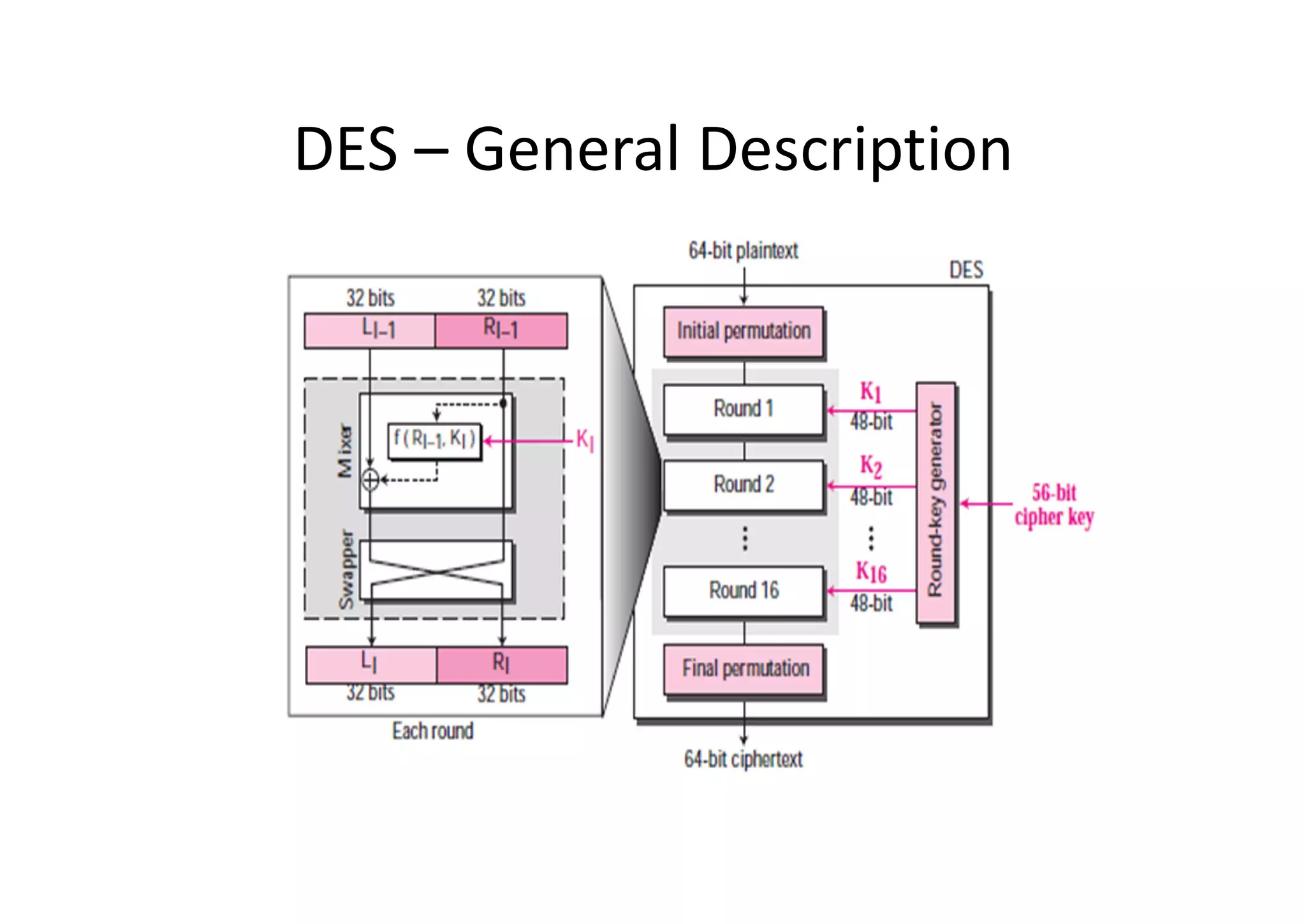
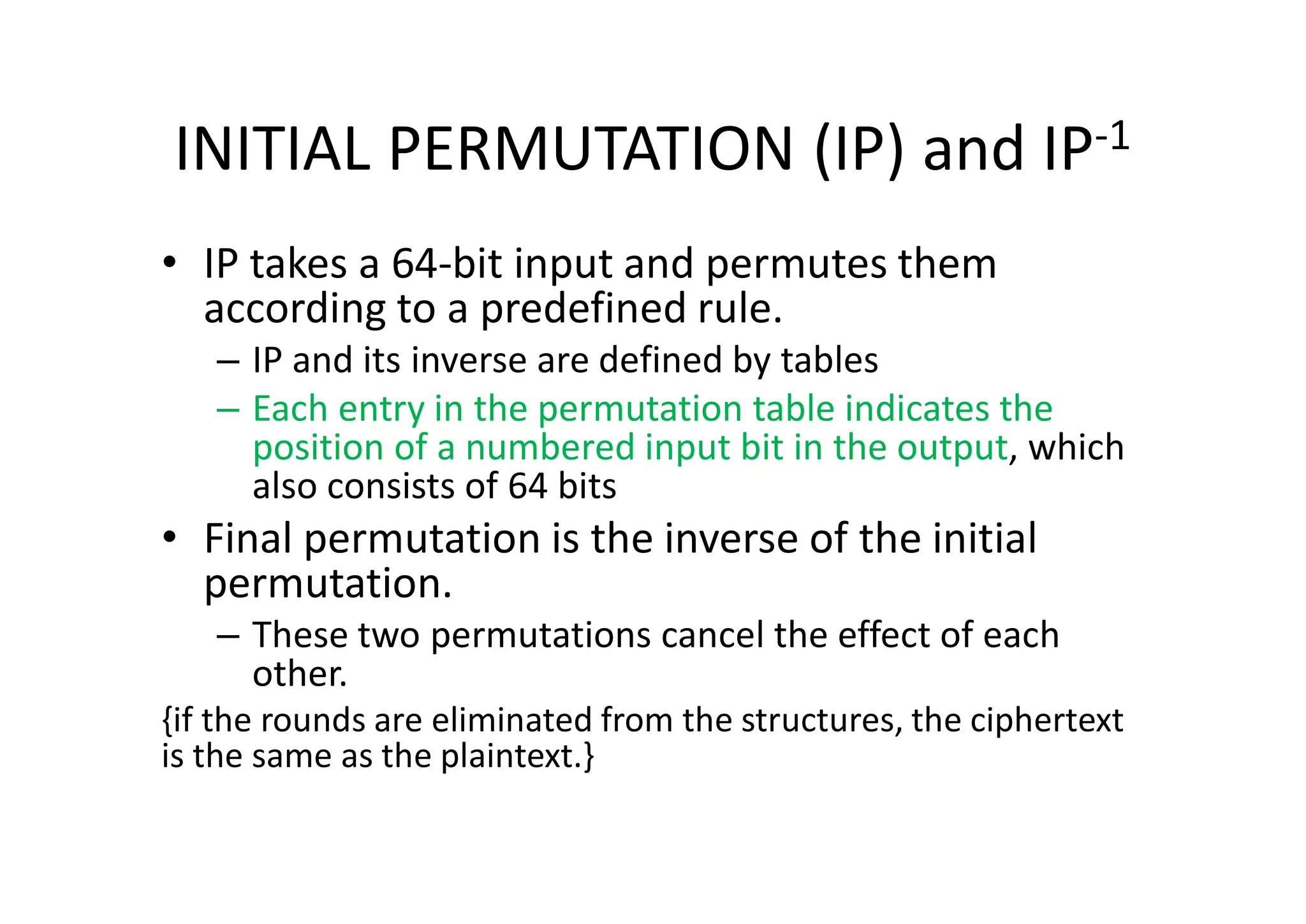
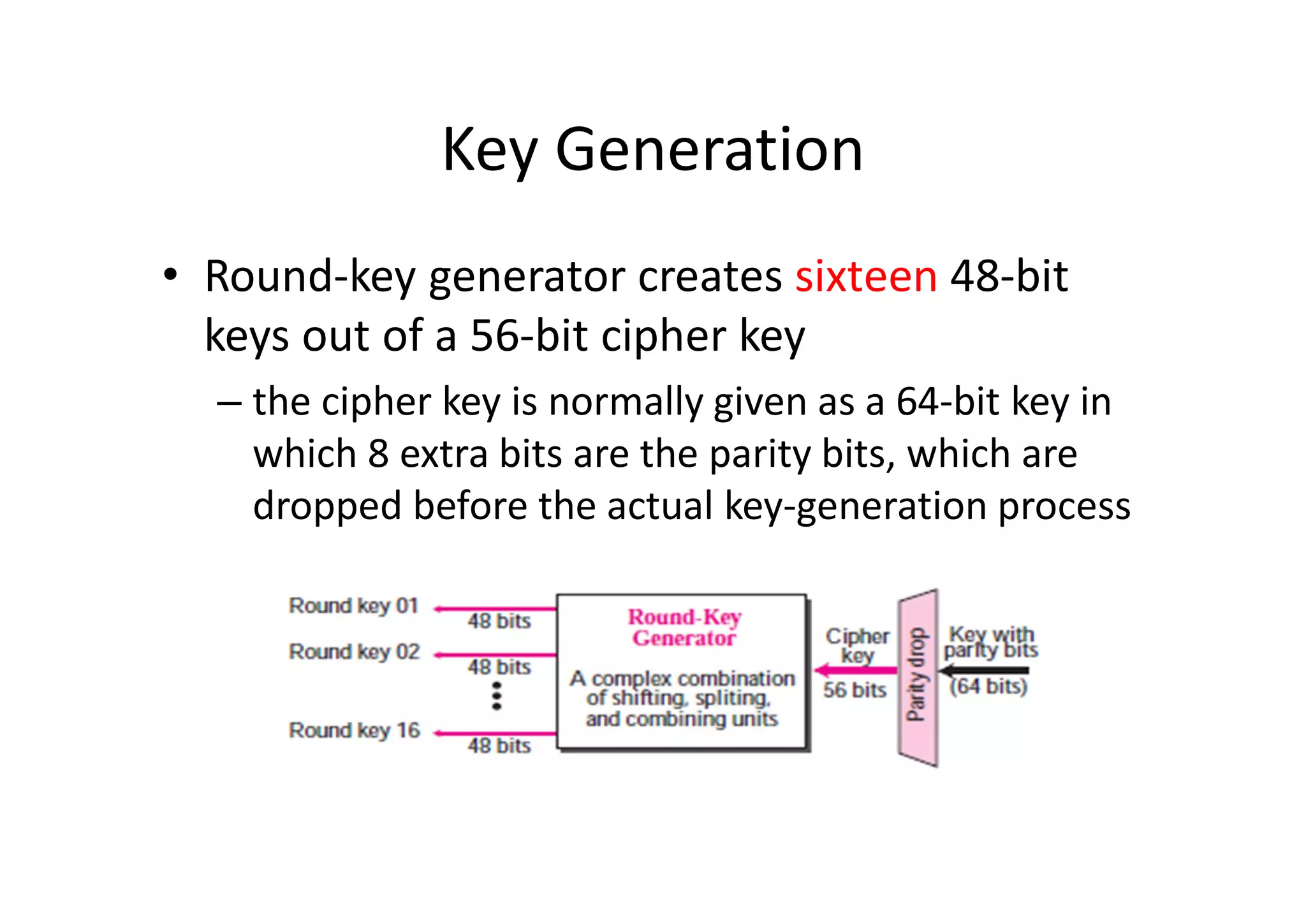
This document discusses block ciphers and the Data Encryption Standard (DES) algorithm. It begins with an overview of stream ciphers and block ciphers, then describes the components of modern block ciphers including substitution boxes (S-boxes), permutation boxes (P-boxes), and operations like XOR. It then explains DES in detail, including the initial permutation, 16 rounds of encryption using 48-bit round keys, and the final permutation. DES encrypts 64-bit blocks using a 56-bit key. The document also covers key generation for DES and the steps to encrypt a plaintext block.

























![Step 2 (cont.) – [S-Boxes]](https://image.slidesharecdn.com/3-blockciphersanddes-230120080831-9bebbcc8/75/3-Block-Ciphers-and-DES-pdf-39-2048.jpg)