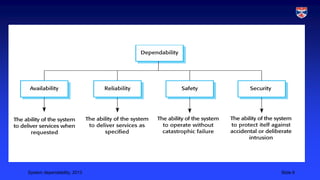
System dependability is a composite system property that reflects the degree of trust users have in a system. It is determined by availability, reliability, safety, and security. Dependability is subjective as it depends on user expectations - a system deemed dependable by one user may be seen as unreliable by another if it does not meet their expectations. Formal specifications of dependability do not always capture real user experiences.