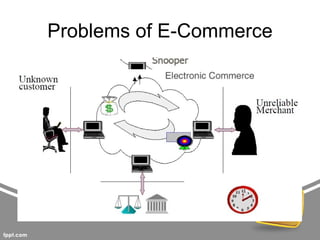
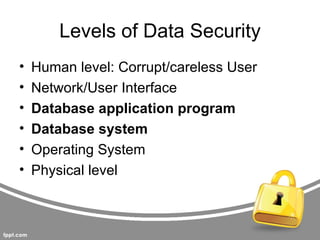
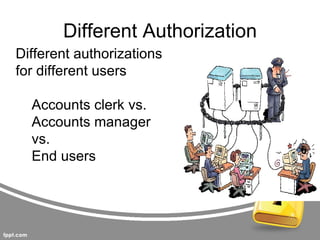
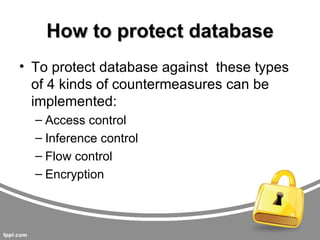
This document summarizes threats to databases in e-commerce. It discusses risks to customers like stolen credentials, dishonest merchants, and inappropriate use of transaction details. Merchants also face risks like disputed charges and insufficient customer funds. The main issue is implementing a secure payment scheme. It then outlines security levels from human to physical. Database threats include privilege abuse, database rootkits, and weak authentication. Different authorization levels are needed for different users. The document concludes protection requires access control, inference control, flow control, and encryption.