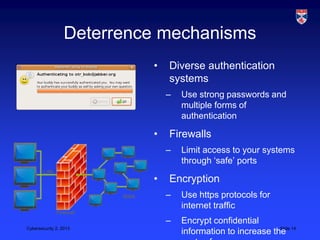
The document discusses cybersecurity and why a technological approach alone is not sufficient. It argues that cybersecurity is a socio-technical problem, as technology cannot guarantee reliability and human and organizational factors like insider threats, procedures, carelessness, and social engineering present vulnerabilities. A holistic approach is needed across personal, organizational, national, and international levels that includes deterrence, awareness, realistic procedures, monitoring, and cooperation.