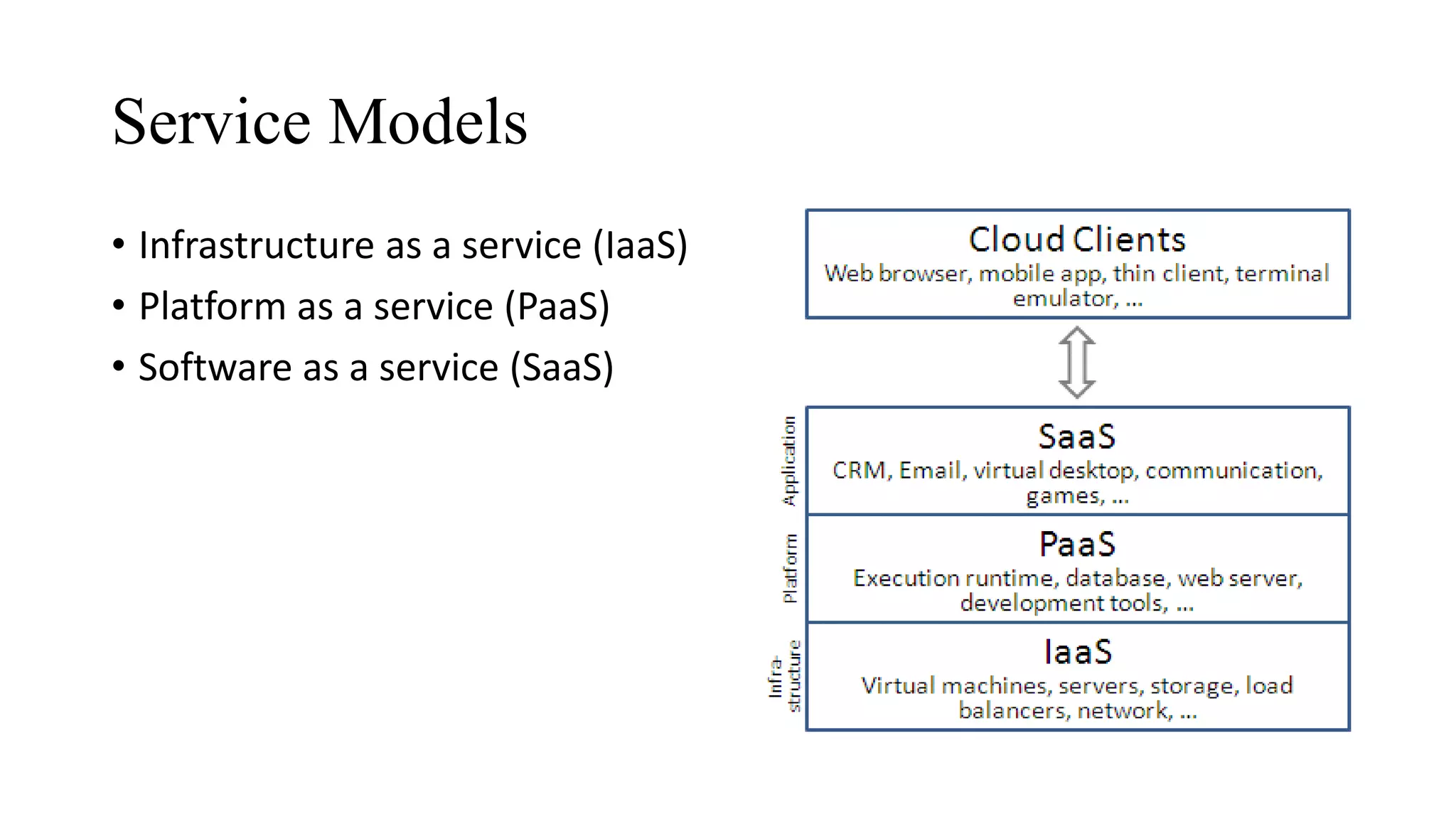
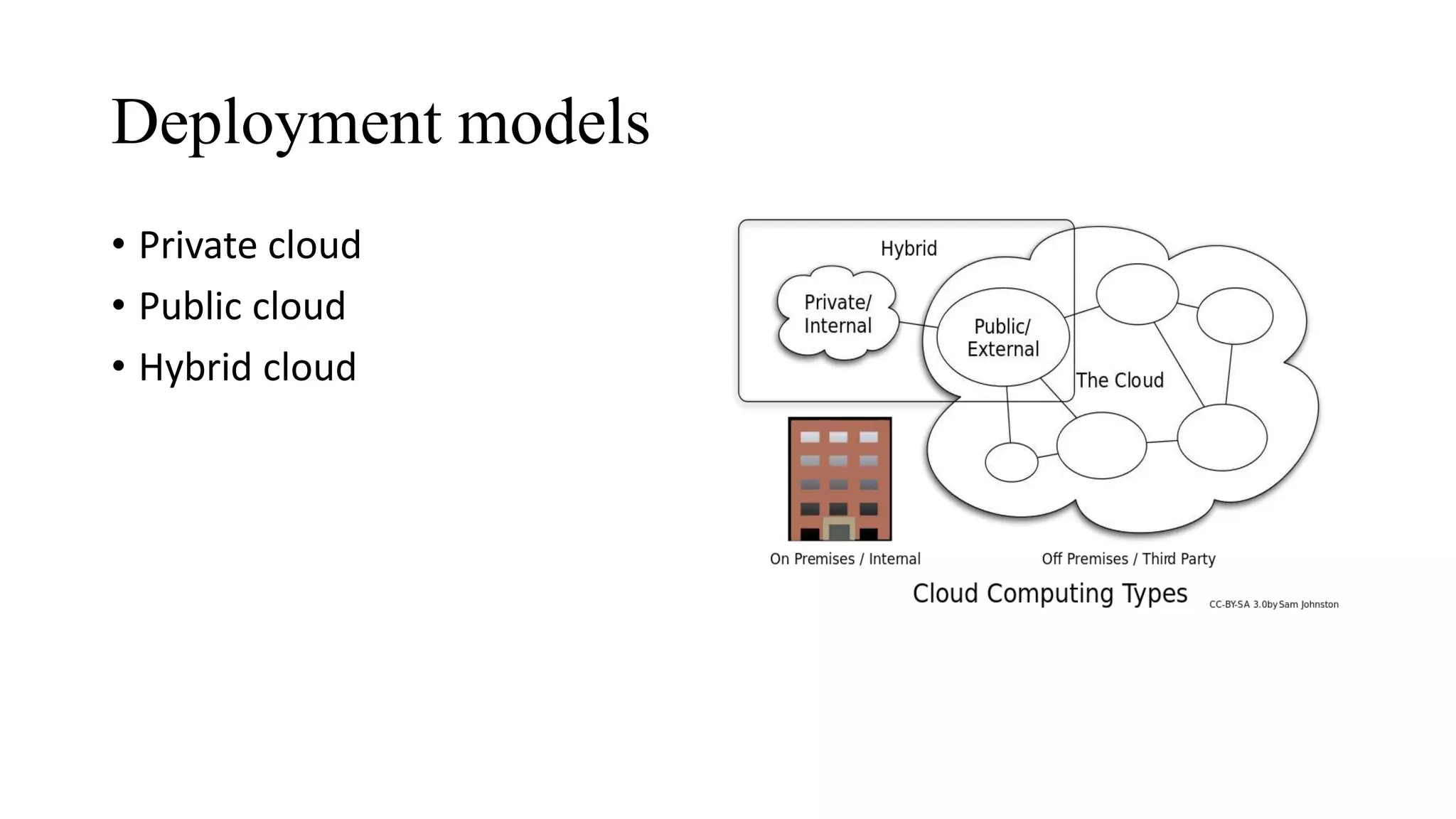
The document outlines the fundamentals of cloud computing and its related service and deployment models, highlighting its advantages like high performance and scalability. It emphasizes the importance of cloud security, discussing various threats such as loss of governance, responsibility ambiguity, and data protection. The document also details necessary security measures, including effective governance, independent audits, role management, and ensuring data confidentiality and integrity.