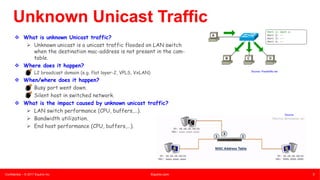
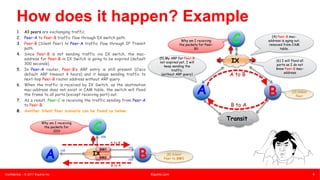
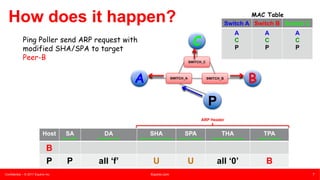
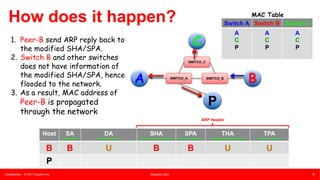
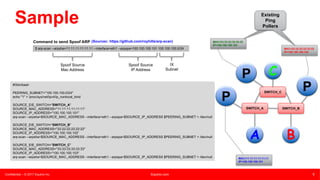
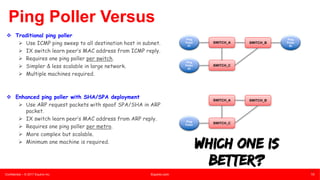
This document summarizes an presentation about unknown unicast traffic and ping pollers. It defines unknown unicast traffic as traffic flooded on a LAN switch when the destination MAC address is not in the CAM table. It occurs in layer 2 broadcast domains. Ping pollers are lightweight machines that send periodic "keep-alive" traffic to refresh MAC addresses in switches and prevent unknown unicast flooding. A traditional ping poller uses ICMP ping sweeps while an enhanced version uses ARP requests with spoofed source MAC and IP addresses, allowing it to be more scalable with just one machine needed per metro area.