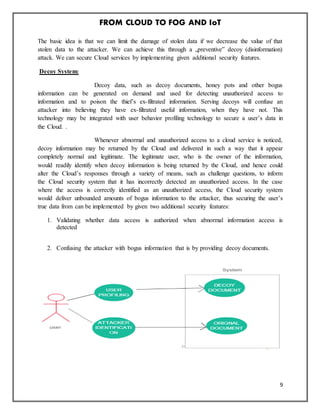
This document discusses fog computing as an extension of cloud computing that moves some computing and storage to the edge of the network. It begins with an abstract that outlines fog computing and its advantages over cloud, such as lower latency. The introduction discusses Cisco's vision for fog computing and bringing applications to billions of connected devices at the network edge. It then discusses how fog computing addresses the issues of slow response times and scalability that cloud computing faces for machine-to-machine communication. The document provides examples of how fog computing could be applied in smart traffic lights, wireless sensor networks, and the internet of things.