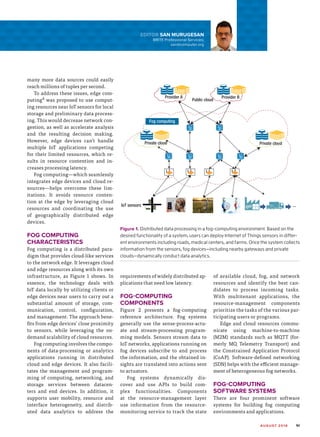
Fog computing is a distributed computing paradigm that performs storage and processing of data close to IoT devices to help address issues of latency, bandwidth, and scalability. It extends cloud computing and services to the edge of the network by leveraging edge devices such as routers, switches, and access points. Fog computing helps overcome limitations of cloud and edge computing alone by avoiding resource contention at the edge through use of geographically distributed edge devices and cloud resources. It supports real-time analytics through dynamic task placement across edge and cloud resources to minimize latency. Challenges to realizing fog computing's potential include enabling real-time analytics, developing programming models for dynamic environments, and addressing security, reliability, and power consumption issues in distributed fog