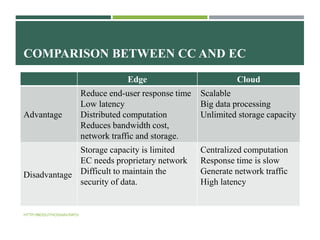
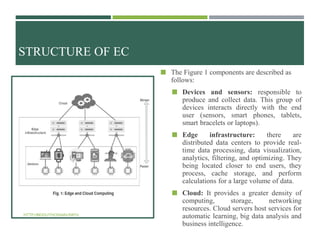
The document provides an overview of edge computing, emphasizing its importance in addressing the limitations of cloud computing, such as low latency and real-time processing. It discusses various applications of edge computing, its structure, challenges, and technologies involved, while comparing it to cloud computing. Future research is suggested to focus on enhancing security, optimizing resource utilization, and improving real-time data processing methods.