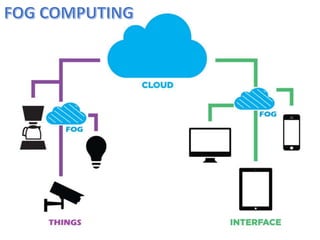
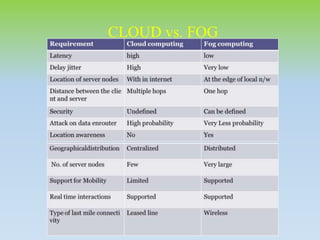
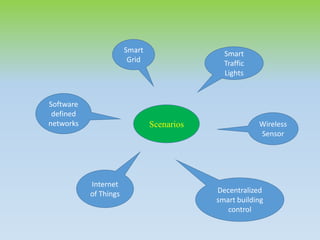
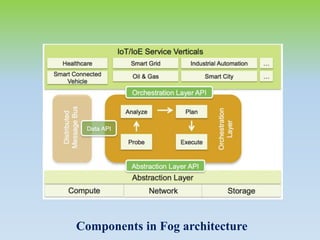
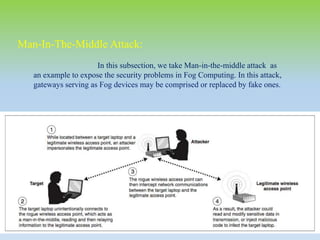
Fog computing extends cloud computing by providing decentralized resources at the network's edge, enhancing user experience through low latency and geographical distribution. Key advantages include improved data processing efficiency and security, while challenges include concerns over complexity and reliability. Future developments will focus on integrating fog computing in various applications like smart grids and connected vehicles, addressing security, privacy, and service migration issues.