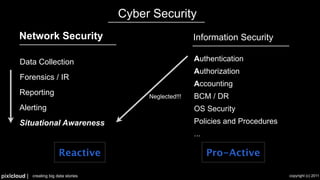
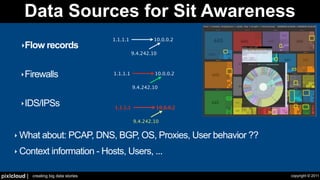
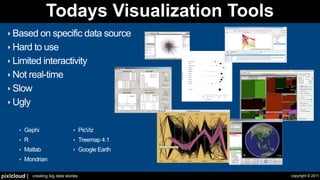
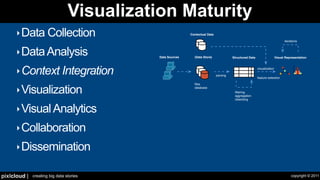
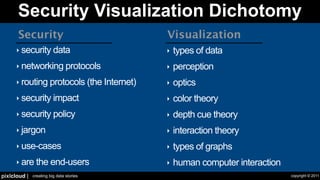
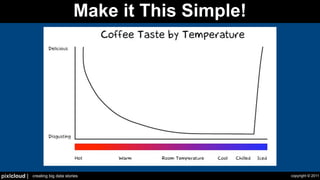
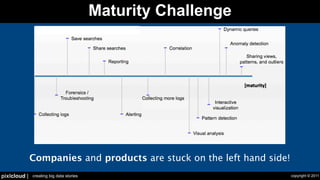
The document discusses situational awareness in network security, emphasizing the importance of visualizing data to enhance understanding and response to threats. It highlights the challenges companies face in data collection and visualization, suggesting the need for advanced tools that leverage human cognitive capabilities. The author calls for interactive and user-focused solutions to improve security insights and decision-making.