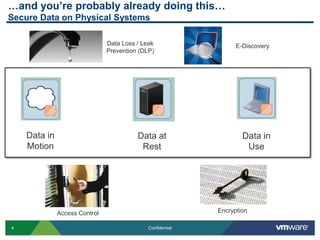
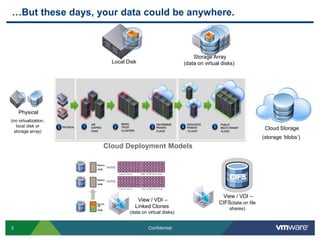
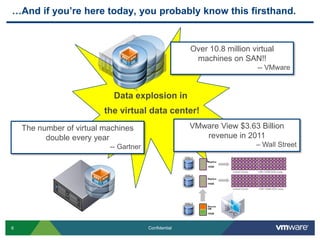
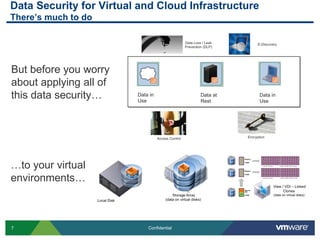
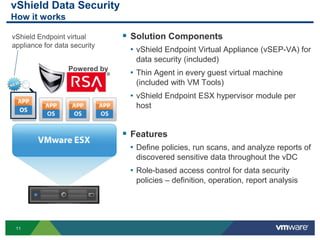
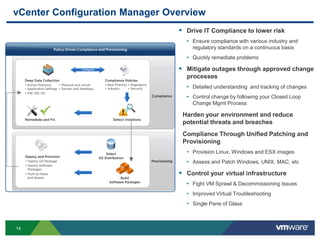
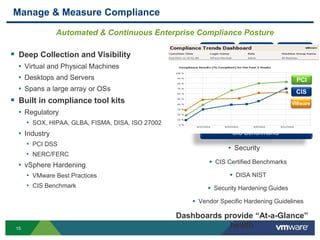
The document provides an overview of VMware's vShield Data Security (VSDS) designed to protect sensitive data in virtual and cloud environments. It outlines the challenges of data security in such environments and highlights VSDS features including policy definition, continuous scanning for sensitive data, and compliance analysis. Additionally, it mentions the vCenter Configuration Manager as a tool for maintaining IT compliance and managing virtual infrastructures.