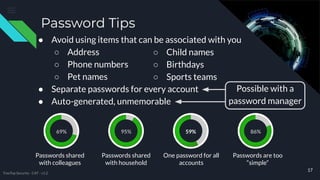
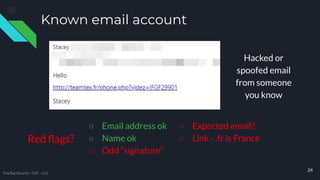
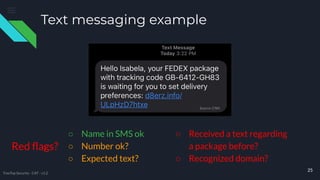
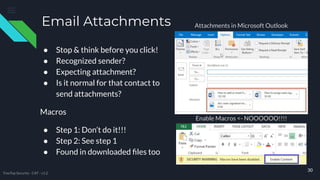
The document provides comprehensive cybersecurity awareness tips aimed at protecting personal and business data, highlighting the importance of security training, regular backups, and software updates. It also offers practical advice on password management, recognizing phishing and phone scams, and ensuring internet safety. The content emphasizes that everyone, from employees to seniors, can play a crucial role in reducing cybersecurity risks.