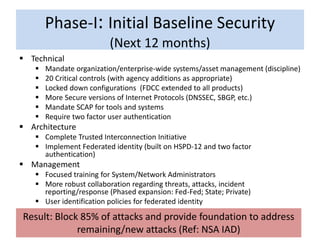
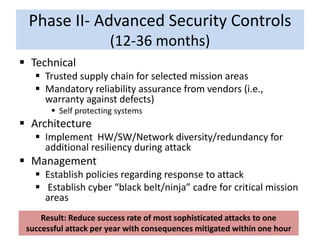
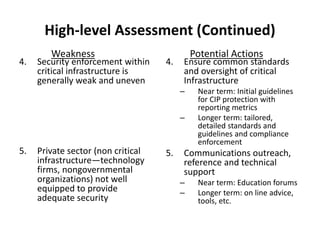
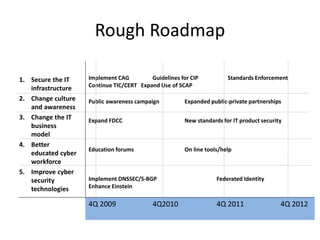
This document provides recommendations to the Department of Homeland Security on cybersecurity priorities and a roadmap. It outlines a phased approach over several years to improve the overall cybersecurity posture. Phase I focuses on establishing a baseline of security across government systems through mandates and best practices. Phase II enhances security controls and expands training and collaboration. The roadmap calls for securing infrastructure, changing culture, improving the IT business model, developing the workforce, and advancing technologies over time to reduce vulnerabilities and attacks on critical systems.