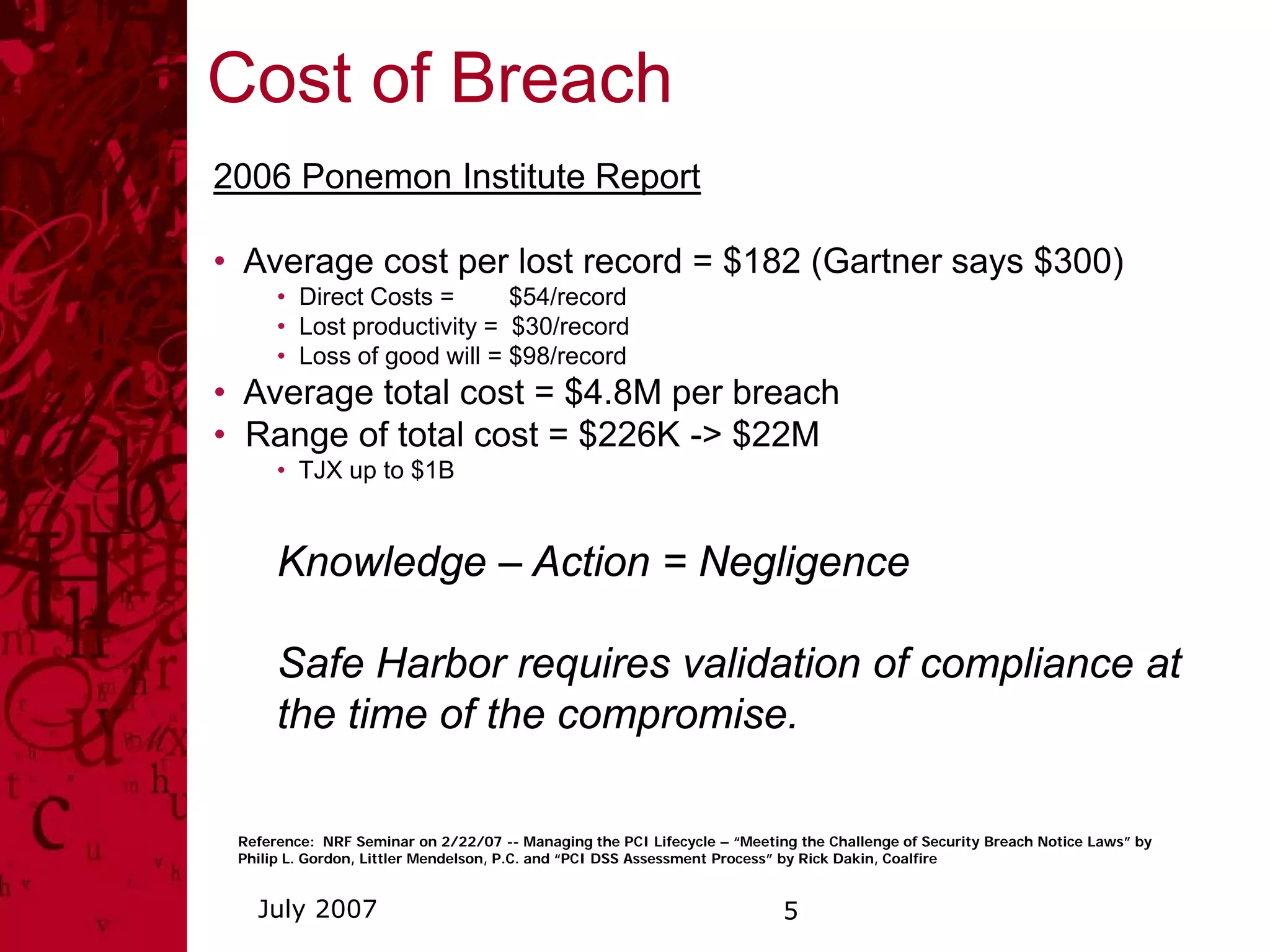
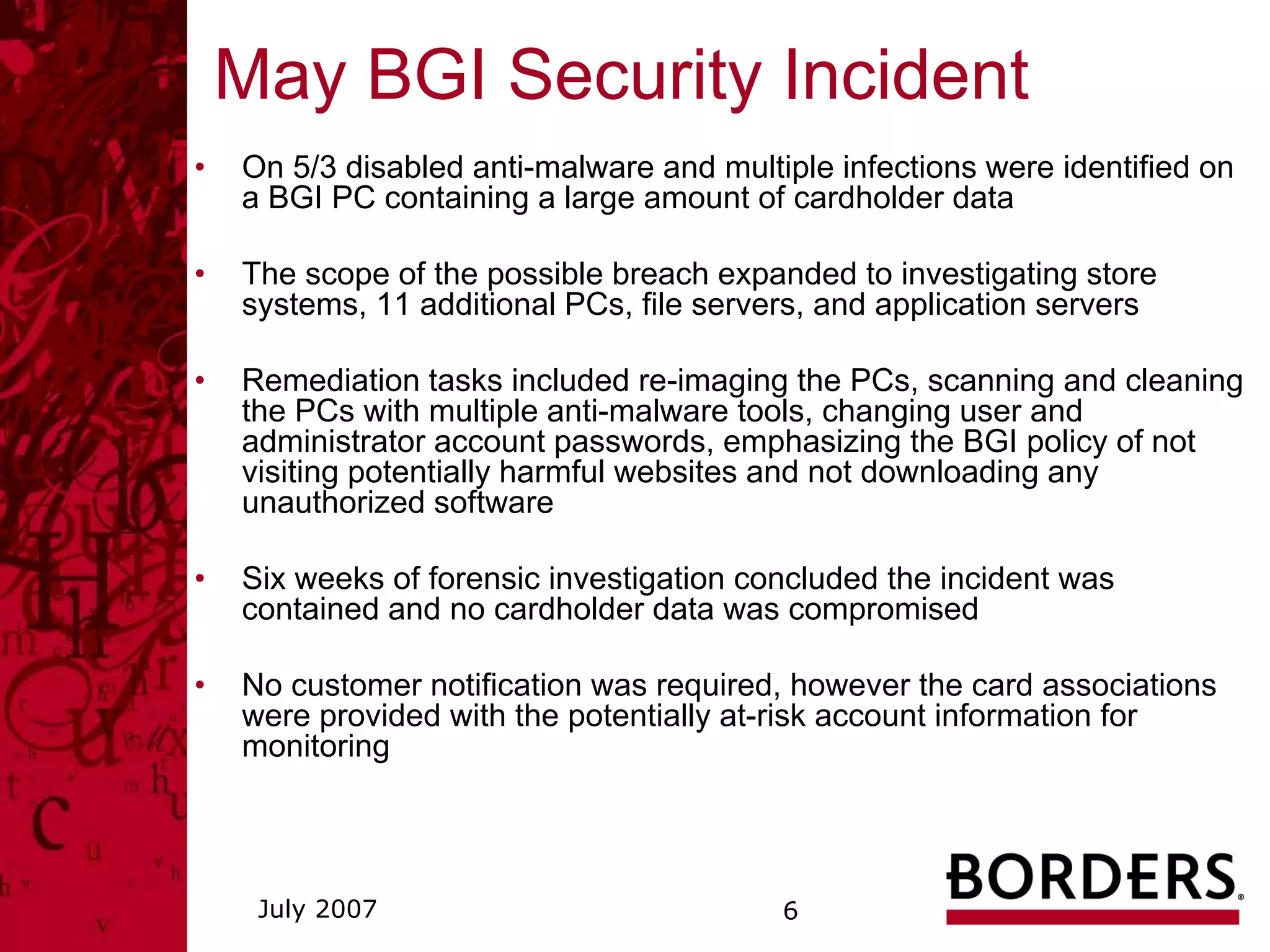
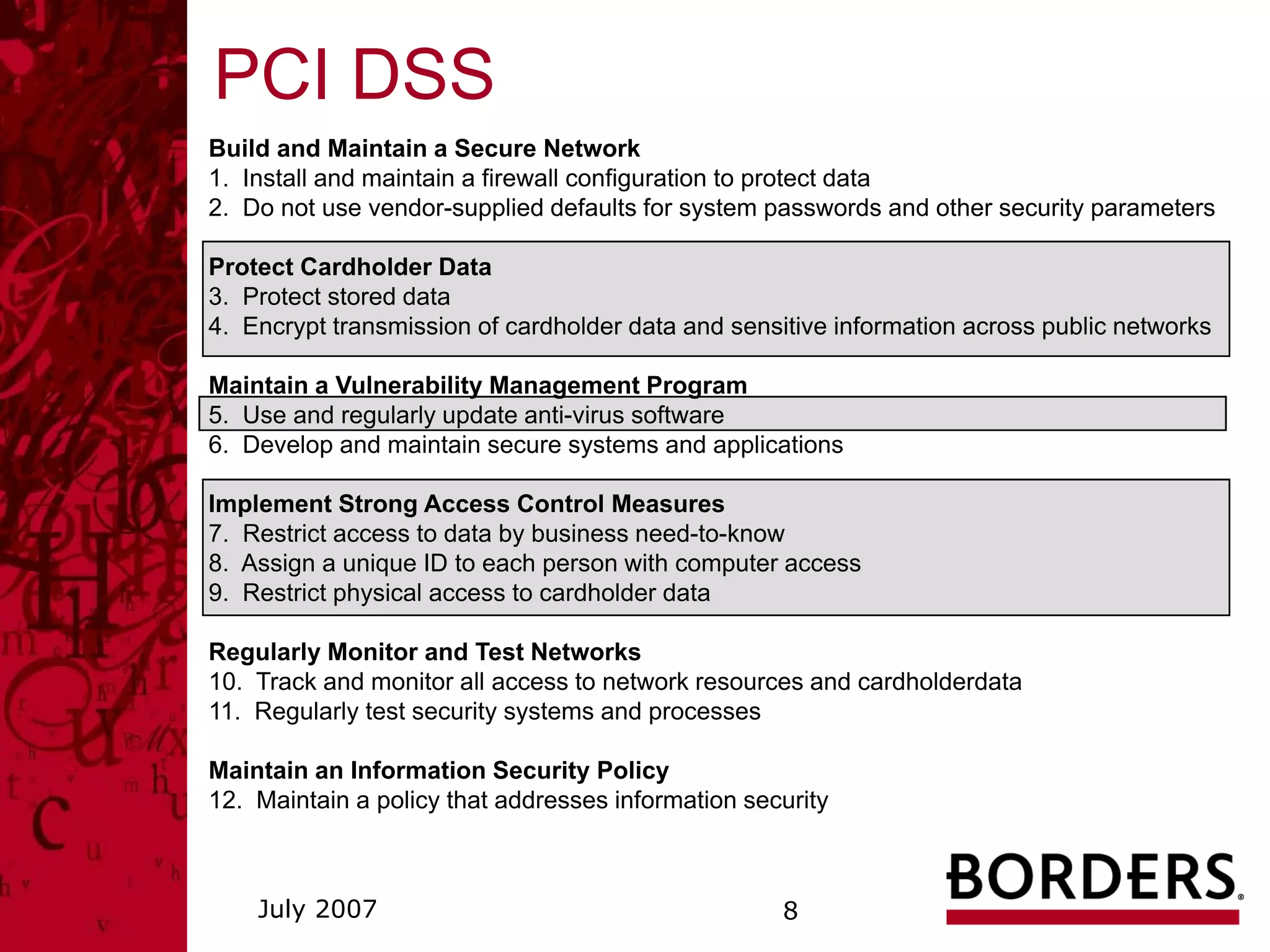
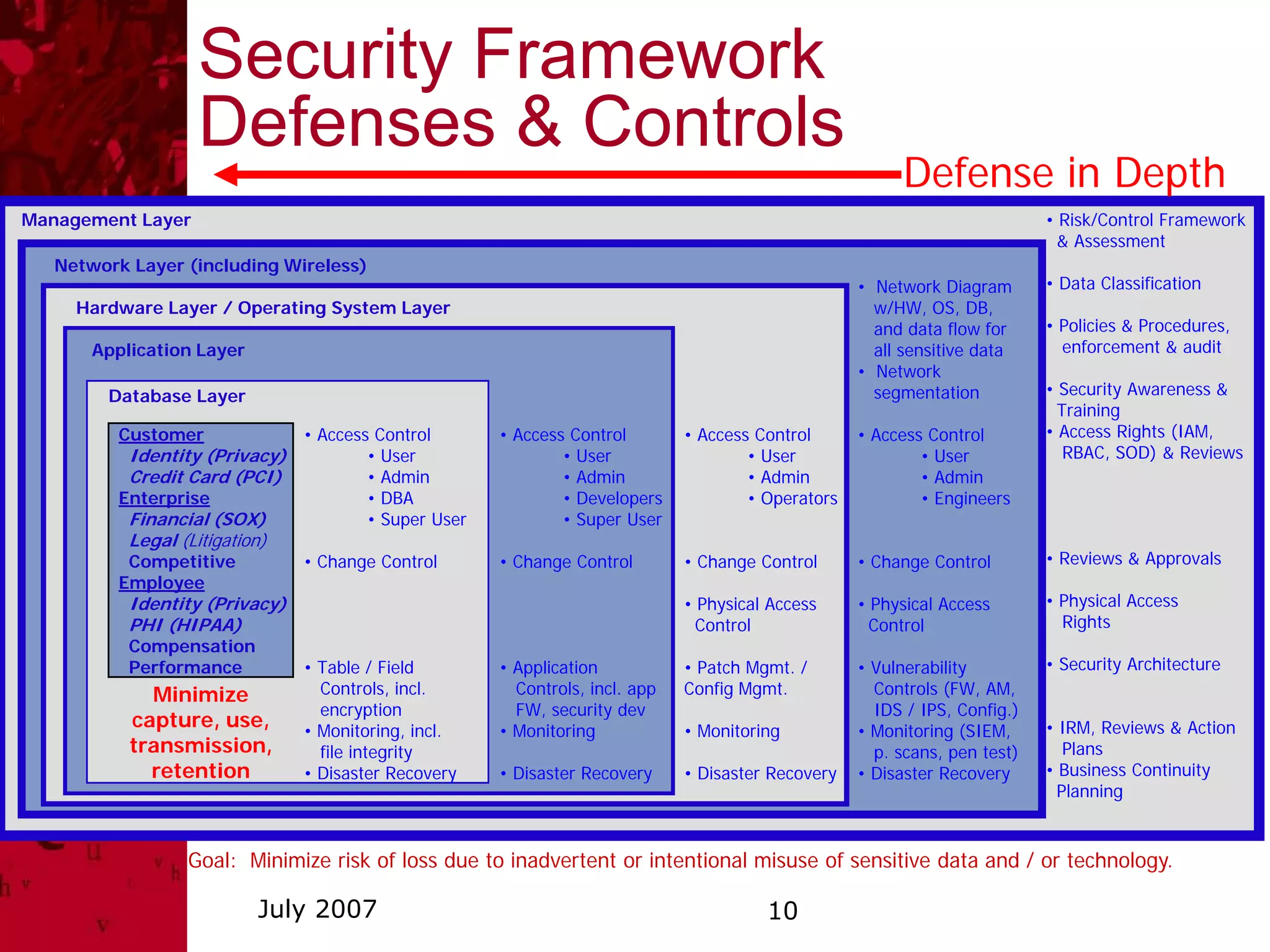
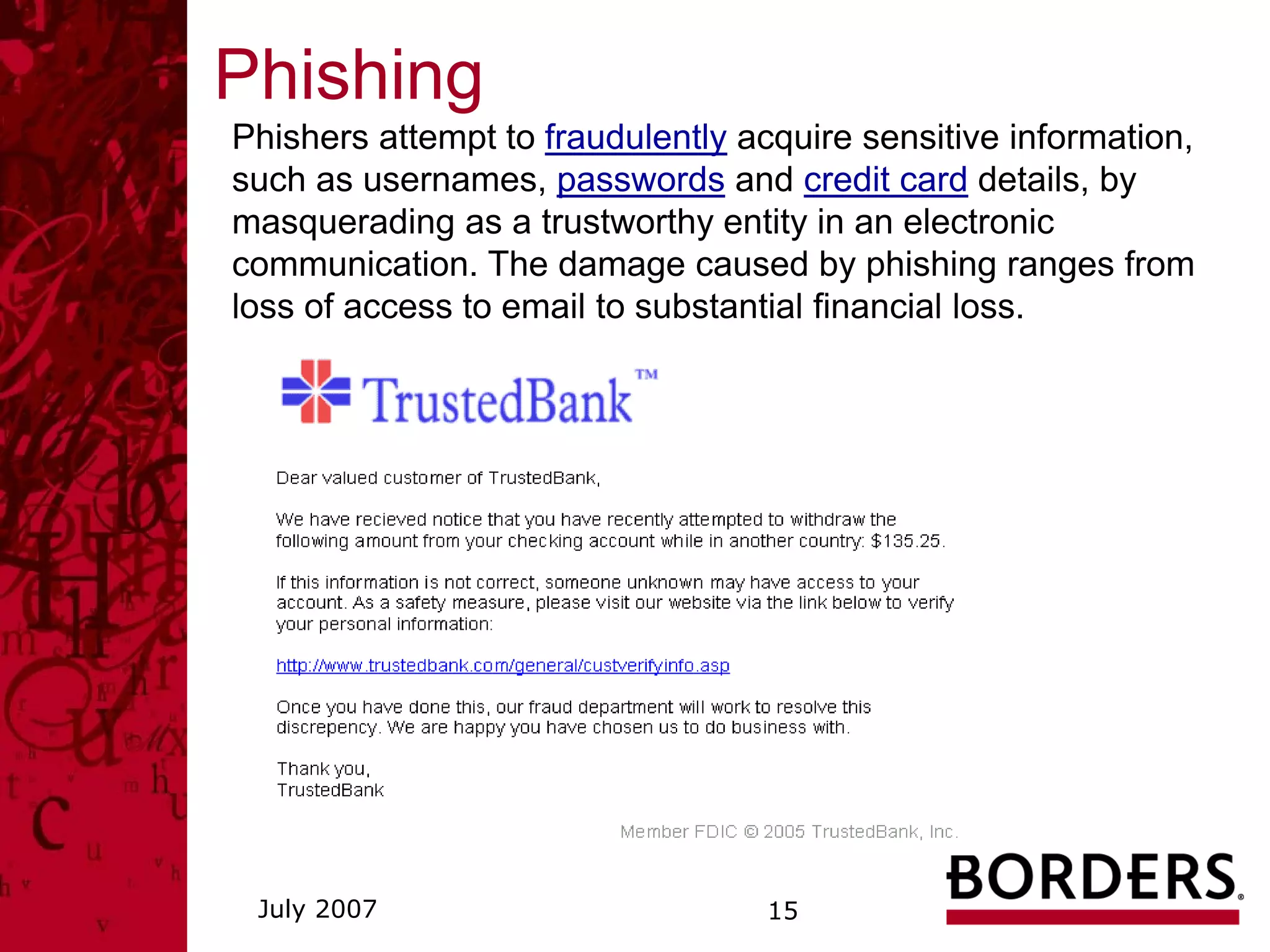
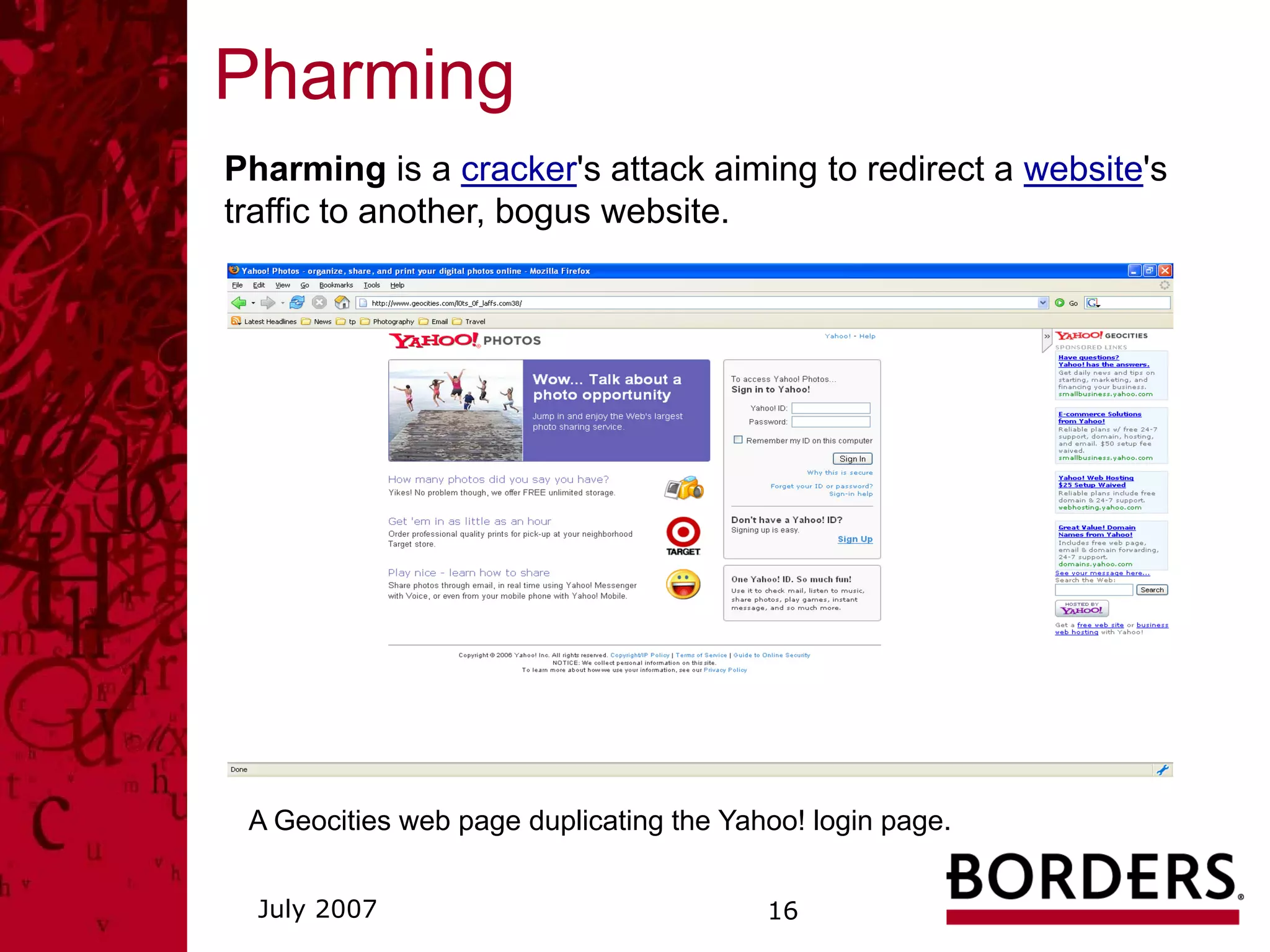
This document summarizes a security awareness training presentation that covered topics such as why security training is important, 21st century security threats, PCI compliance, security objectives and challenges, data classification, and security responsibilities. It provided examples of security incidents, the costs of data breaches, PCI DSS requirements, and outlined the company's security framework including defenses, controls, and challenges around excessive data retention, vulnerable infrastructure, lack of documentation and logging.