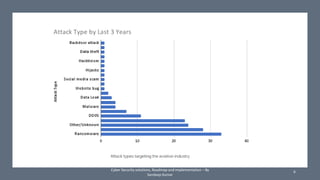
The document discusses the increasing cyber threats to the aviation industry, highlighting various types of attackers such as state-sponsored groups and cybercriminals. It outlines the critical systems at risk and the industry's need for an effective cybersecurity strategy amidst digital transformation efforts. Challenges include a lack of trained personnel and awareness, along with infrastructure and information privacy concerns.