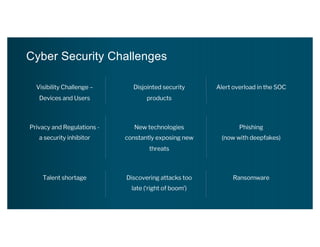
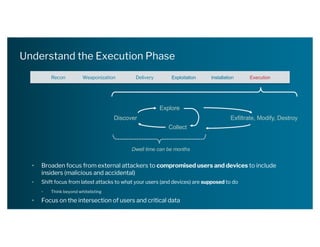
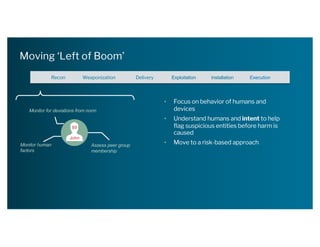
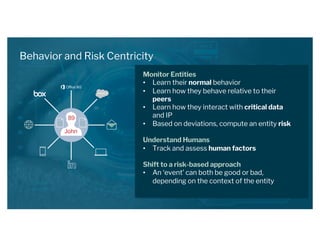
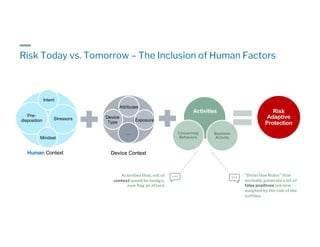
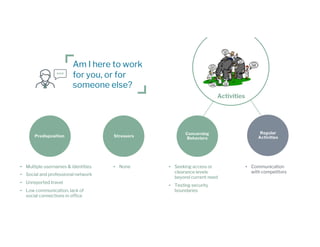
The document discusses the urgent need for a paradigm shift in cybersecurity to escape the persistent cat-and-mouse game between defense and attack. It emphasizes the importance of integrating security platforms, focusing on human behavior, and adapting to new attack surfaces driven by digital transformation. The document also highlights the challenges posed by insider threats, alert overload, and evolving technologies, advocating for a risk-based approach to enhance security effectiveness.