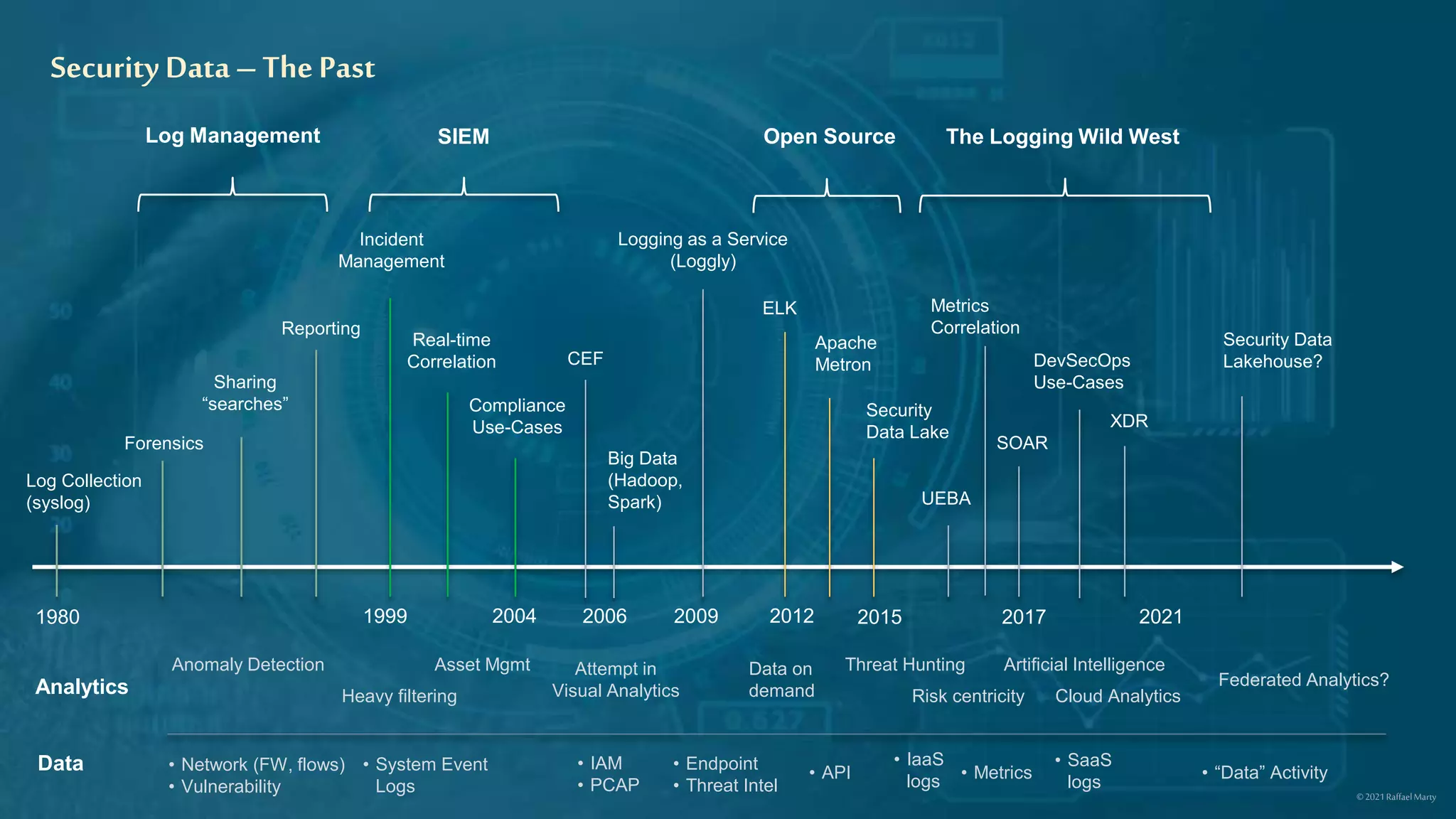
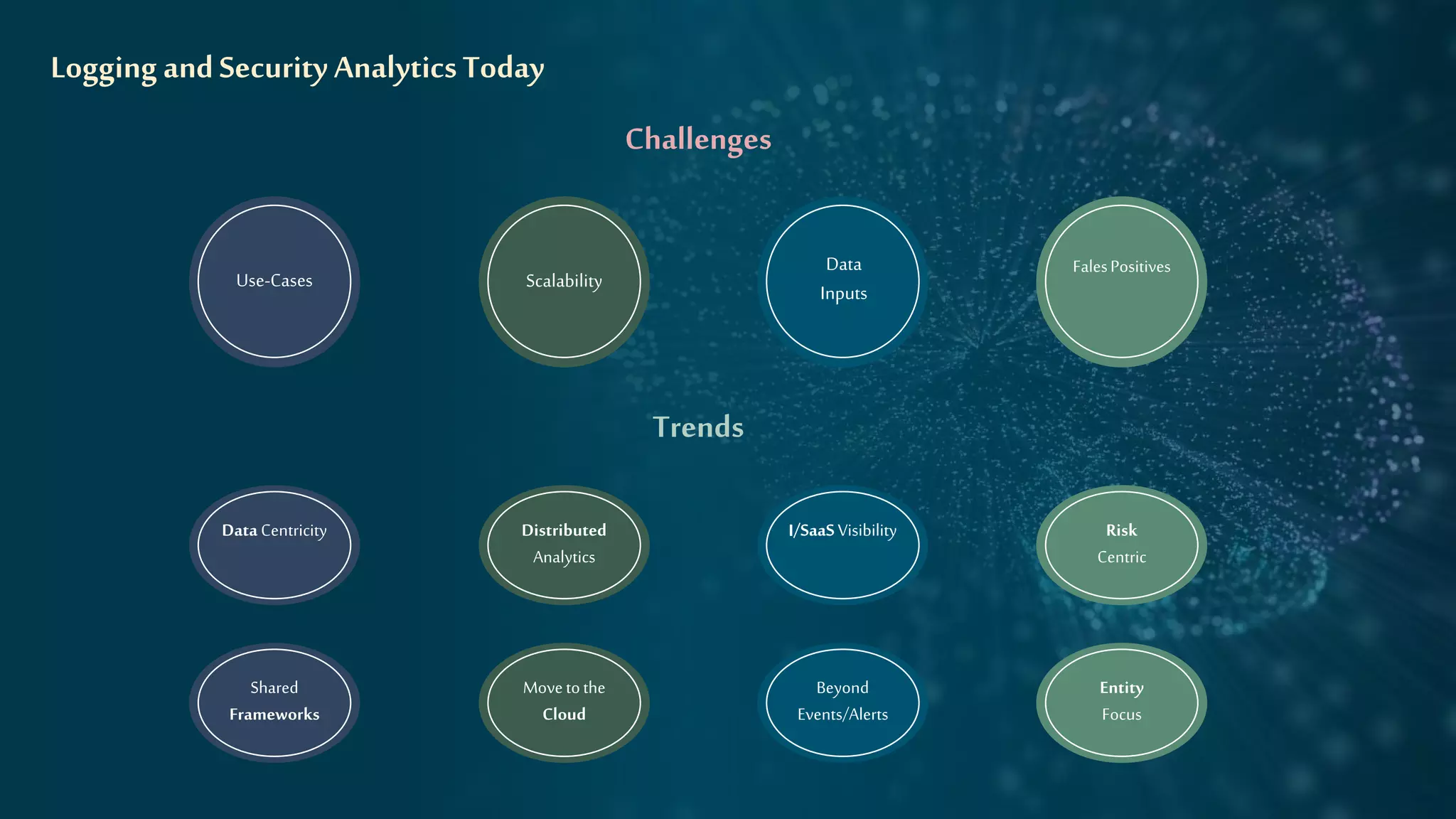
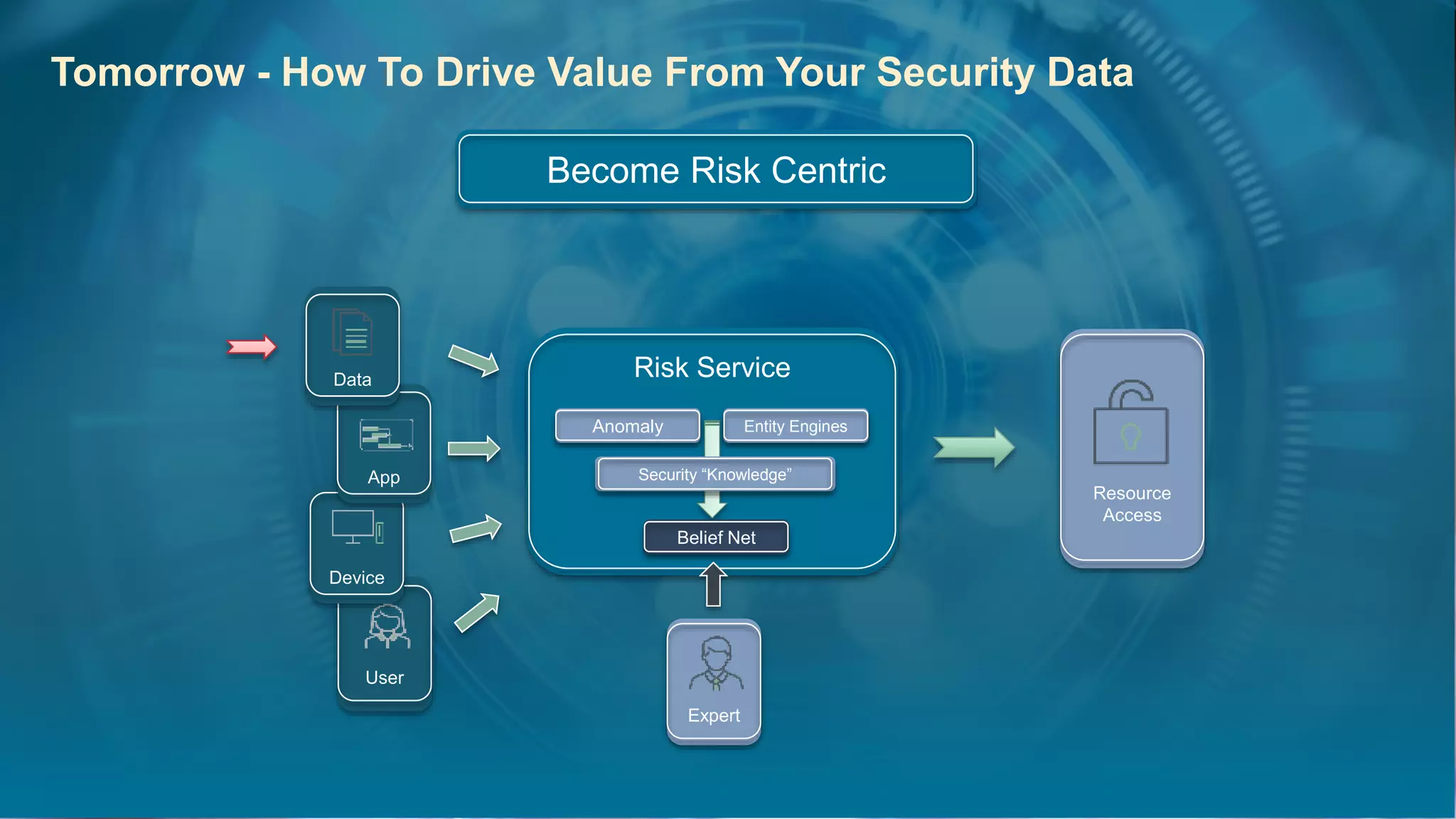
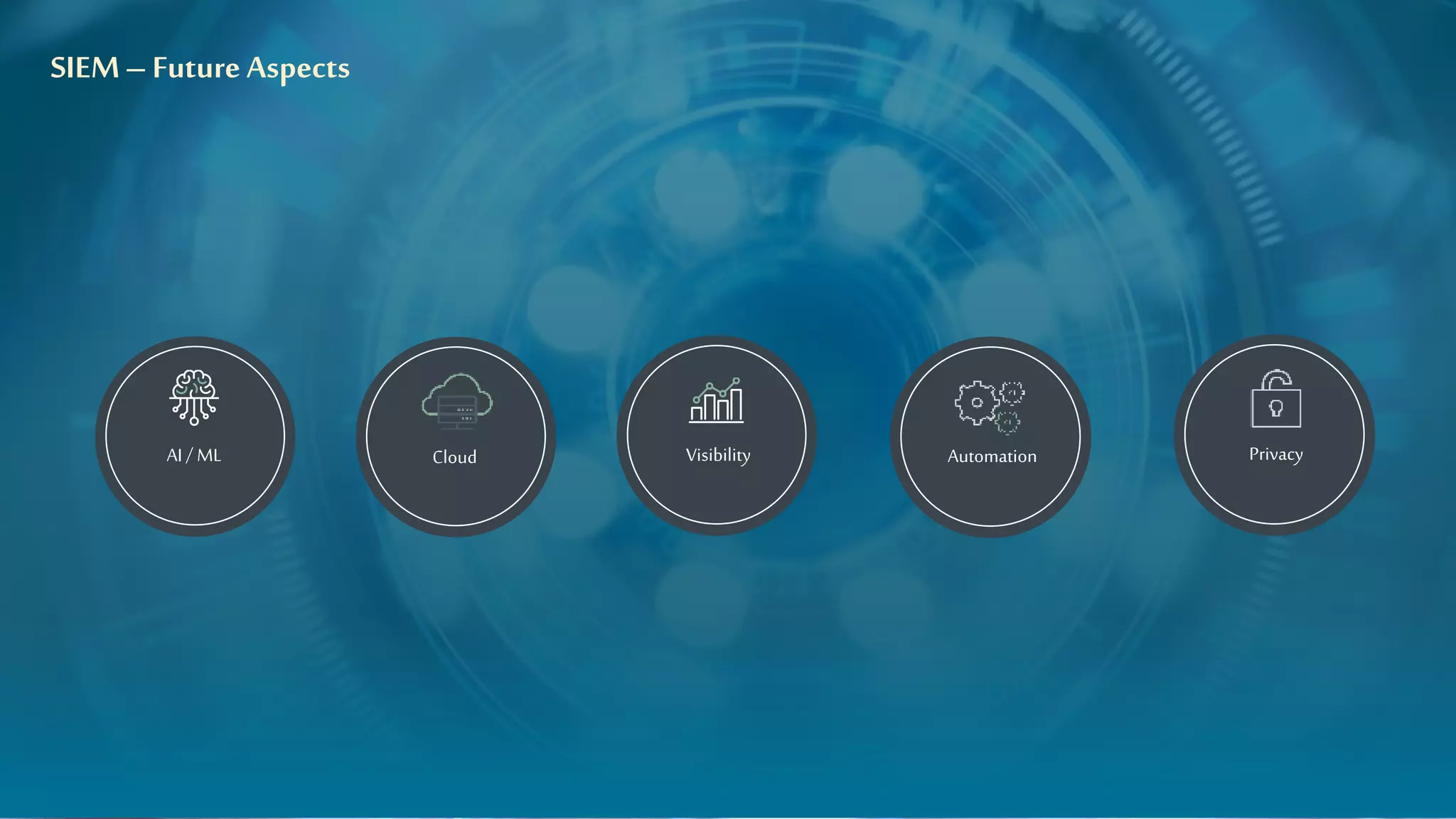
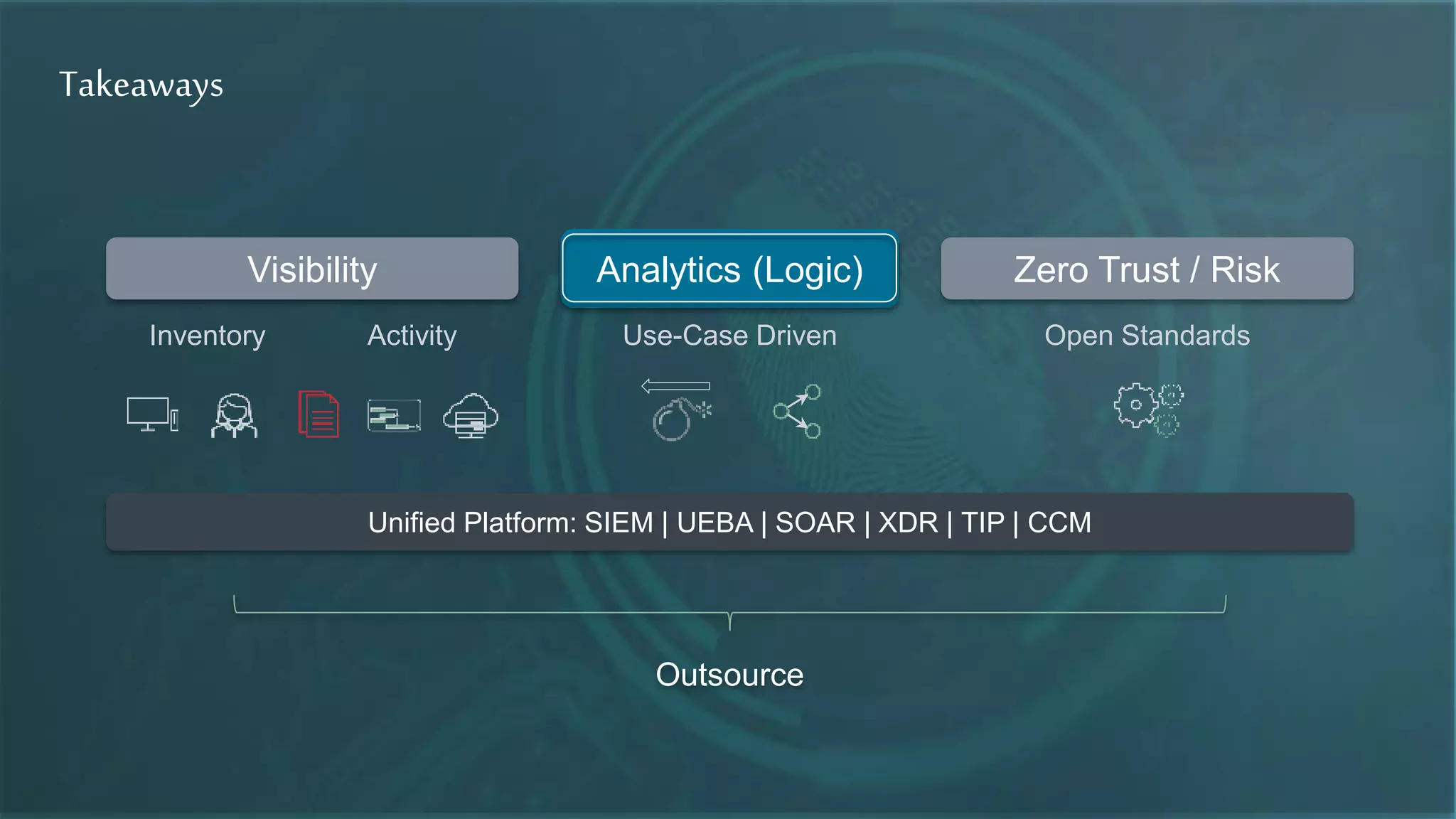
The document discusses strategies for leveraging security data to drive value, emphasizing the importance of analytics, incident management, and compliance. It highlights the evolution of logging technologies and the need for risk-centric approaches in the context of cloud and distributed analytics. Key concepts include the integration of AI/ML for anomaly detection and the future direction of security data management.