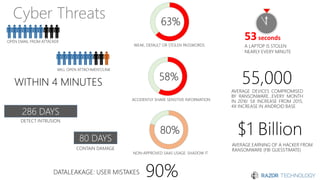
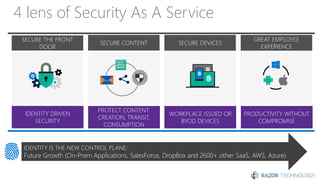
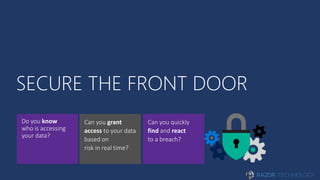
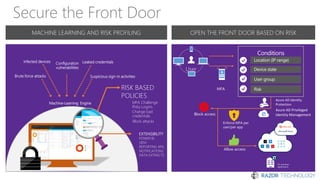
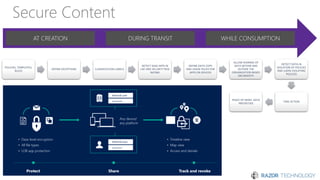
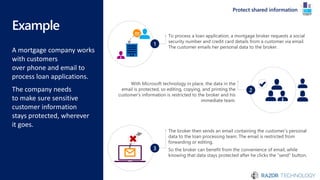
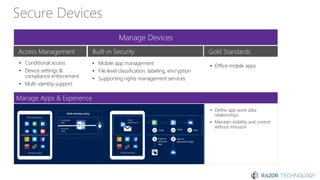
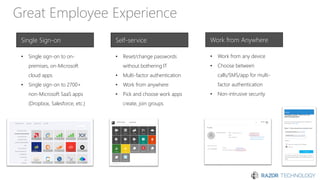
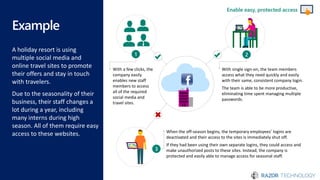
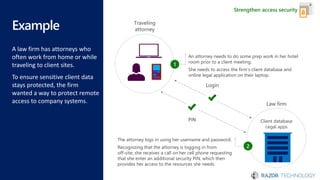
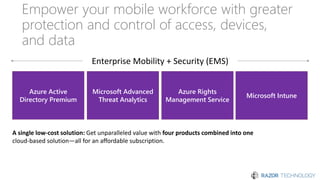
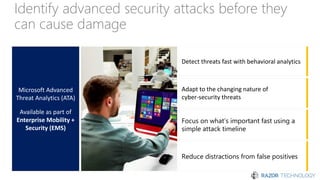
The document discusses the concept of 'Security as a Service' and its benefits for protecting content, devices, and identity-driven security. It highlights solutions offered by Microsoft, including Enterprise Mobility + Security (EMS), which helps businesses manage mobile productivity and safeguard sensitive data across various applications and devices. Key features include multi-factor authentication, mobile device management, and the ability to protect information regardless of location, ultimately providing peace of mind for companies against cyber threats.