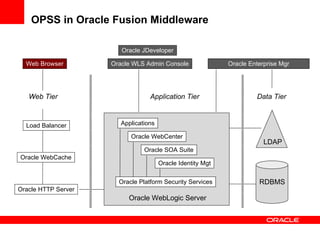
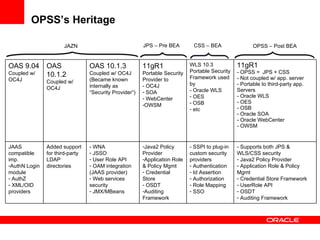
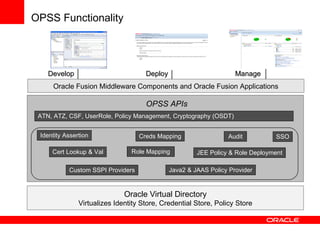
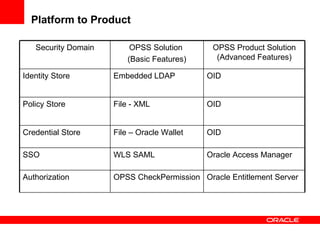
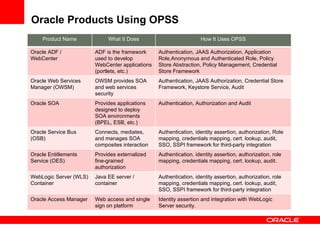
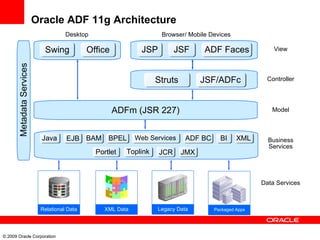
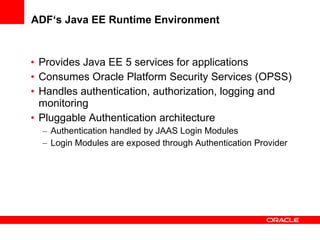
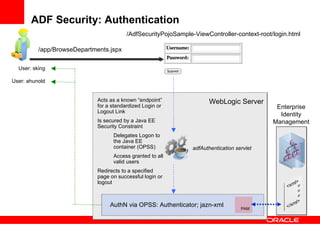
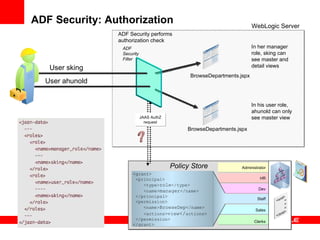
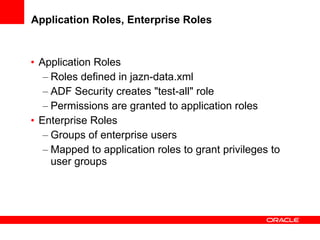
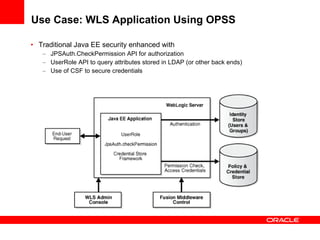
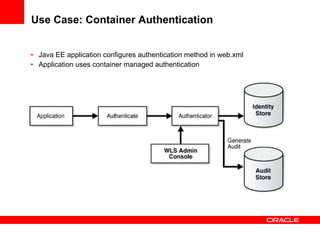
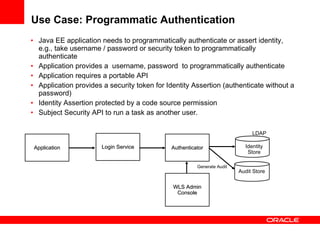
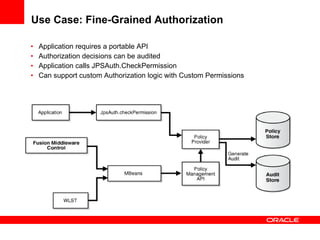
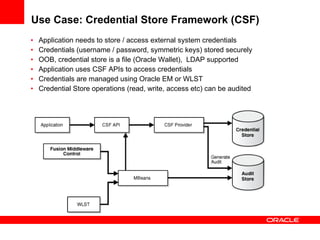
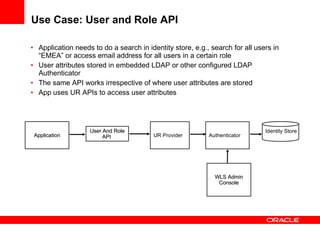
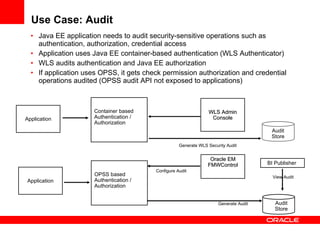
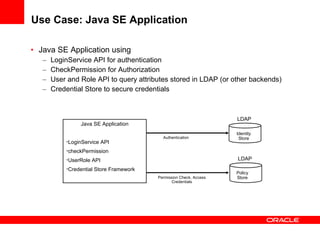
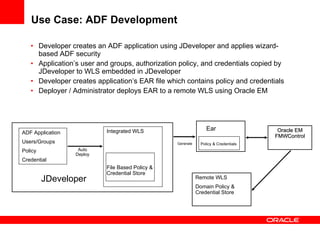
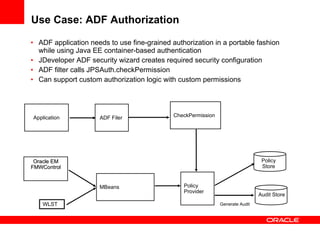
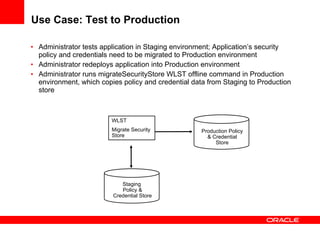
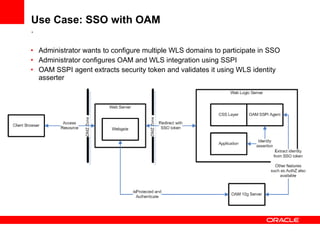
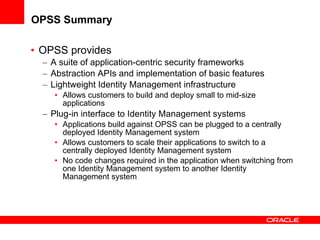
The document provides an overview of Oracle Platform Security Services (OPSS) and how it can be used to provide security for Java applications. OPSS provides standards-based security services and abstracts security implementation details away from developers. It supports features like authentication, authorization, role-based access control, and integration with identity management systems. The document also describes several use cases where OPSS can be leveraged for applications developed using Java EE, Java SE, Oracle ADF, and other Oracle products.
![Security As A Service Marc Chanliau, Identity Management Technical Evangelist [email_address]](https://image.slidesharecdn.com/oraclecodecamp09-091005110719-phpapp01/85/Security-As-A-Service-1-320.jpg)