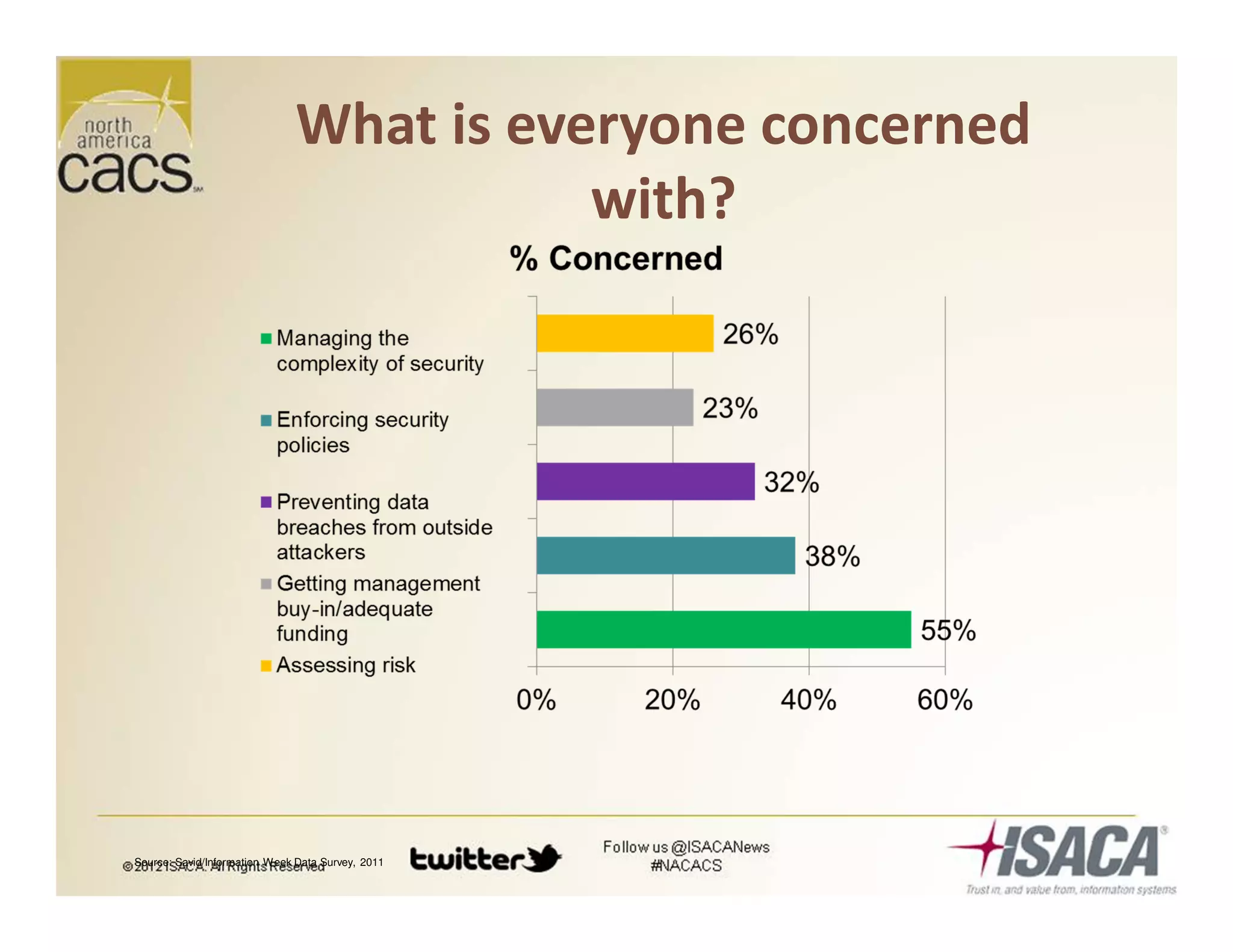
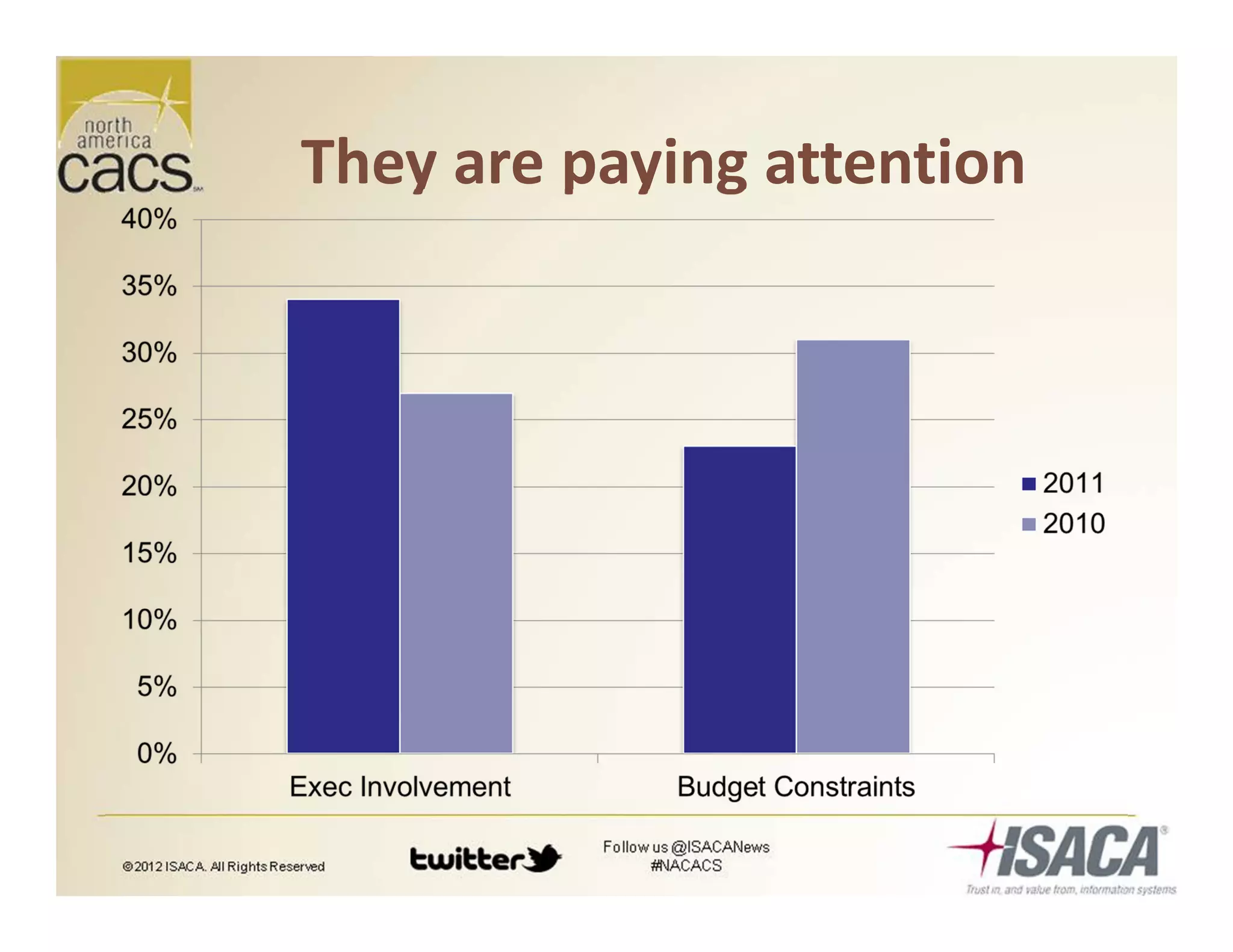
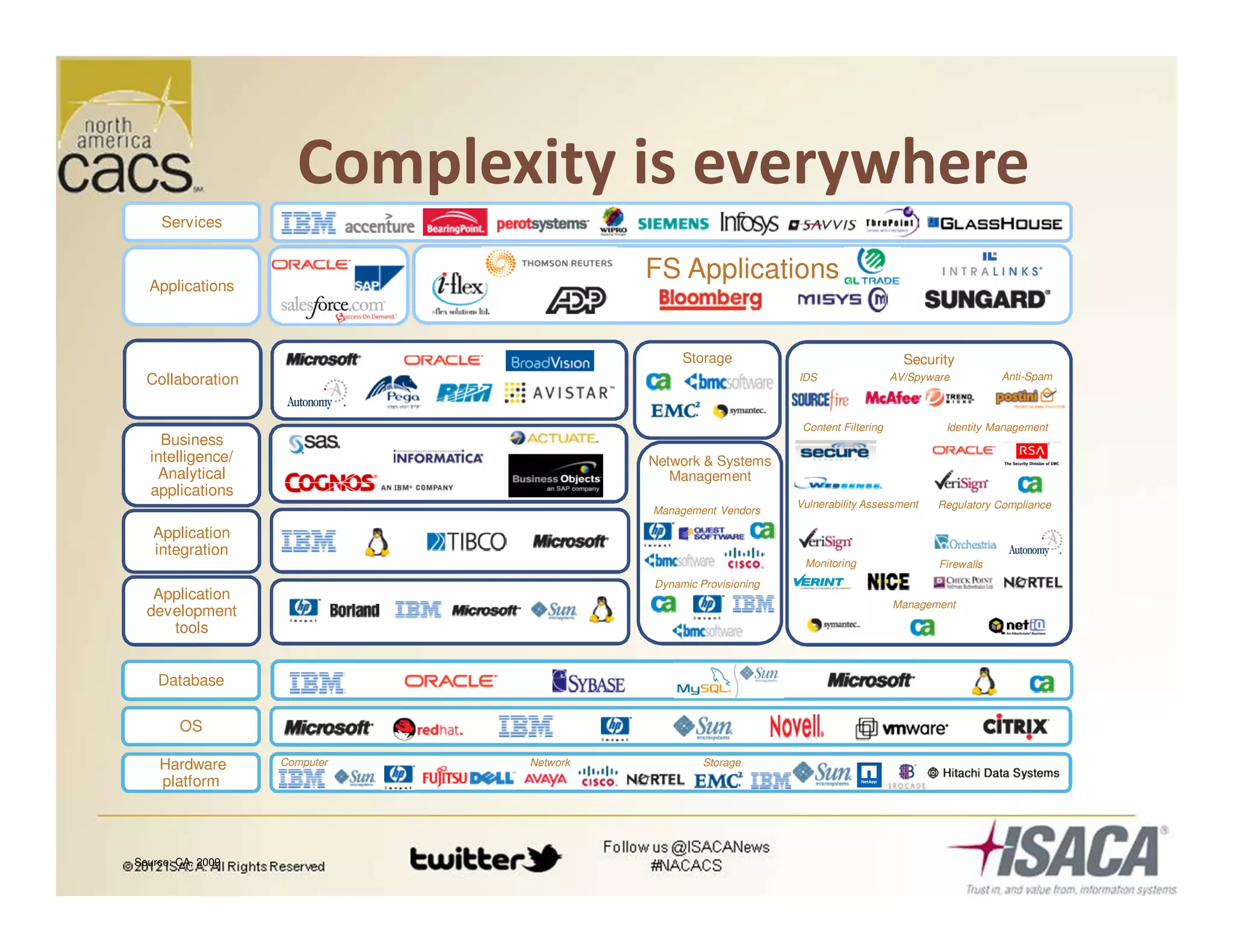
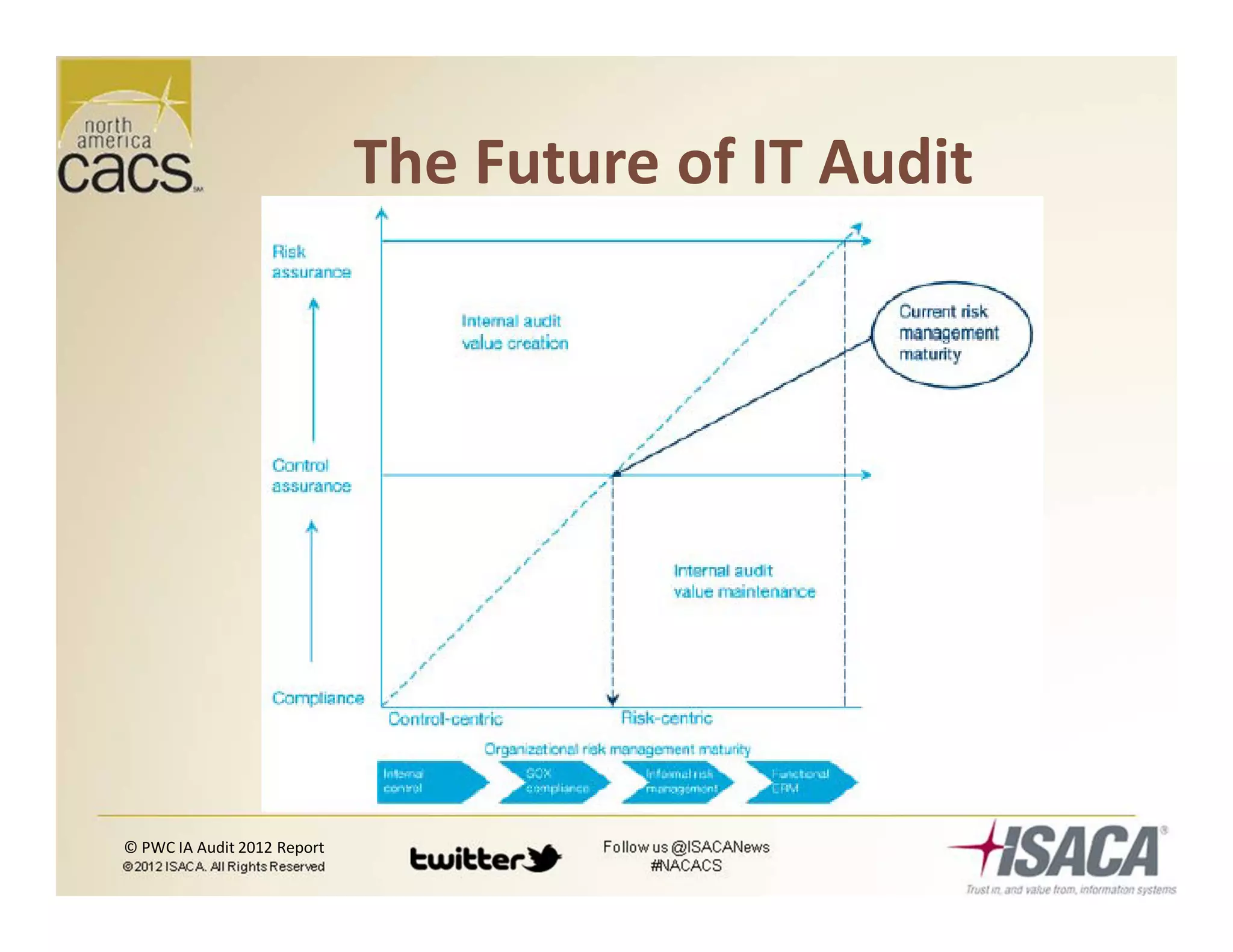
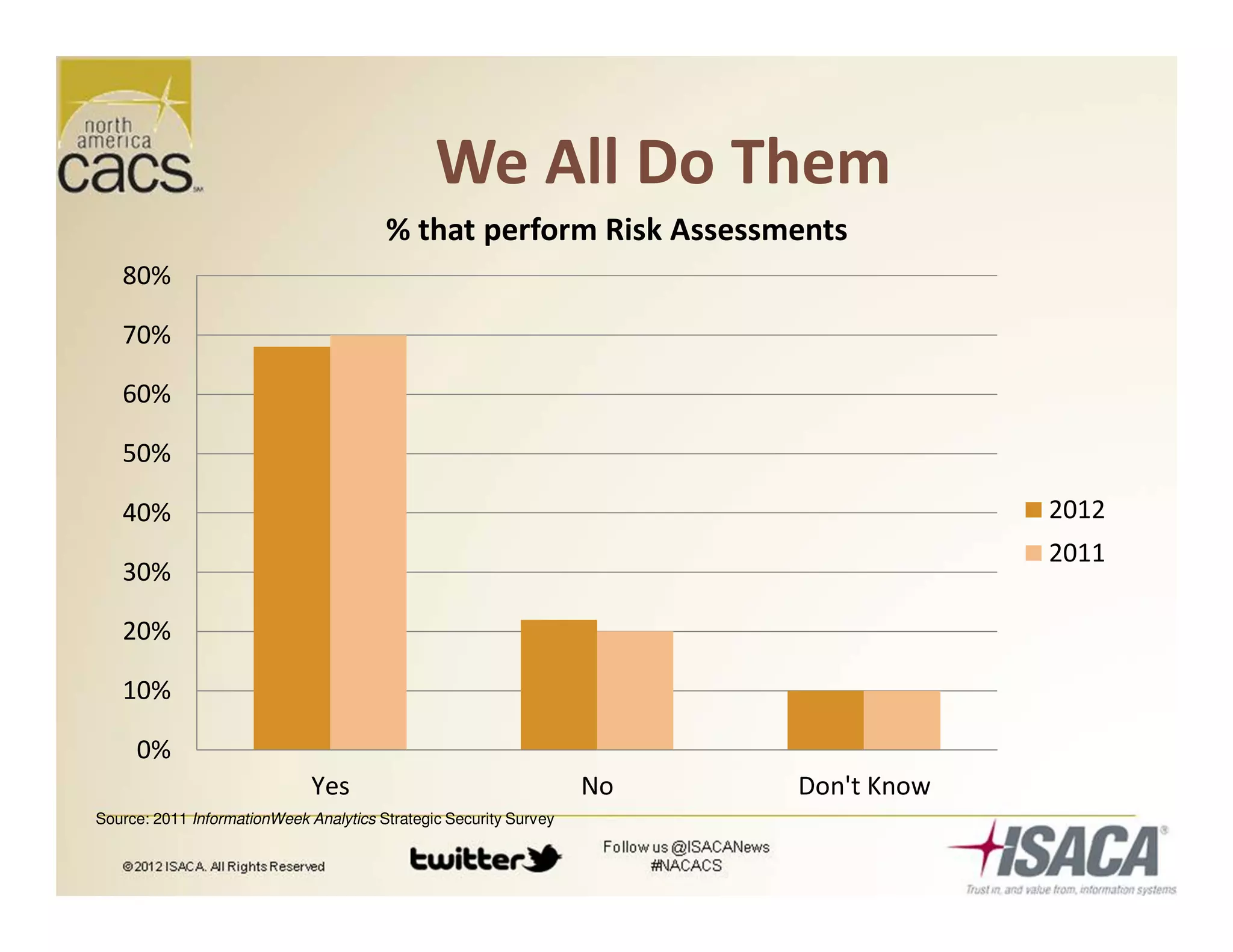
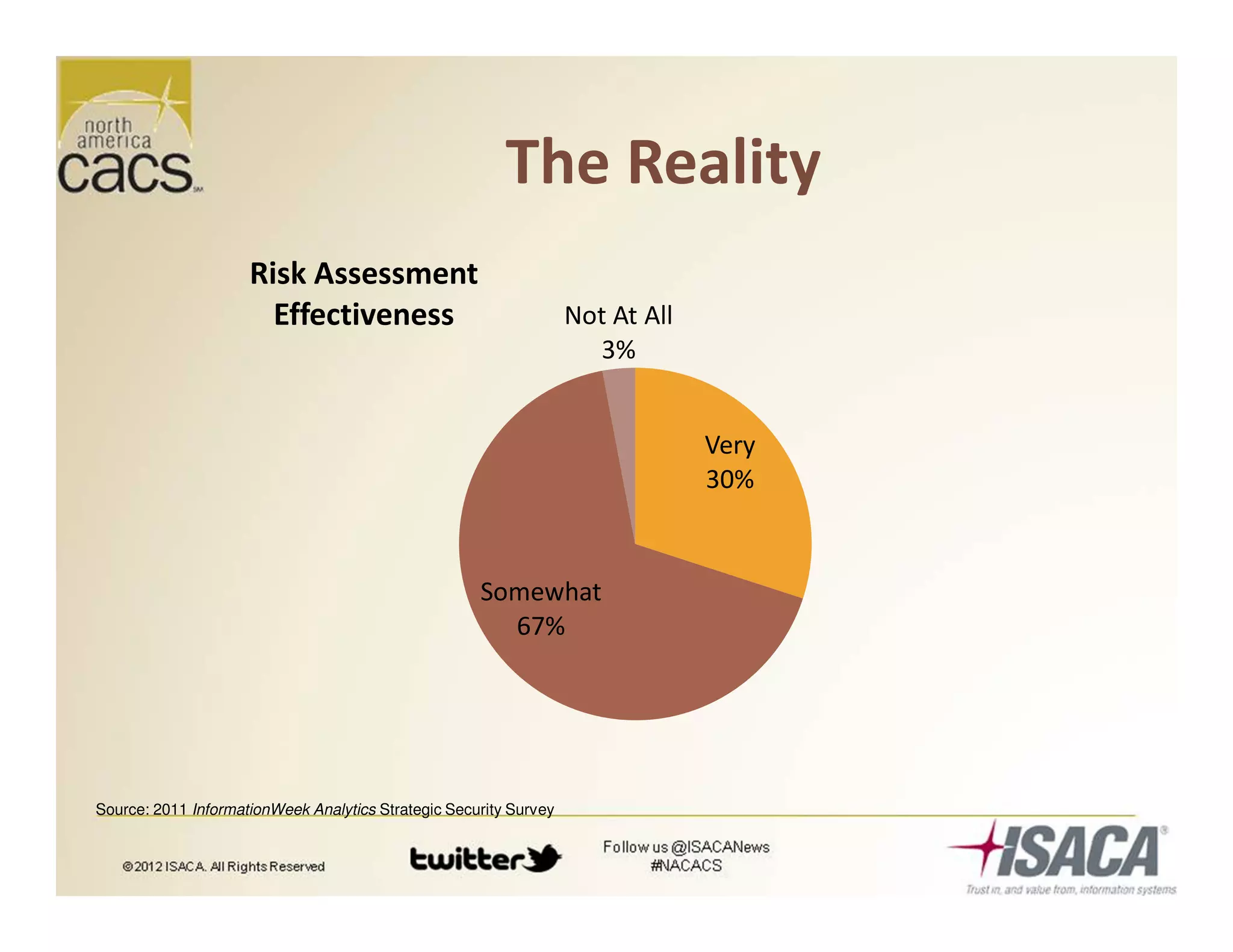
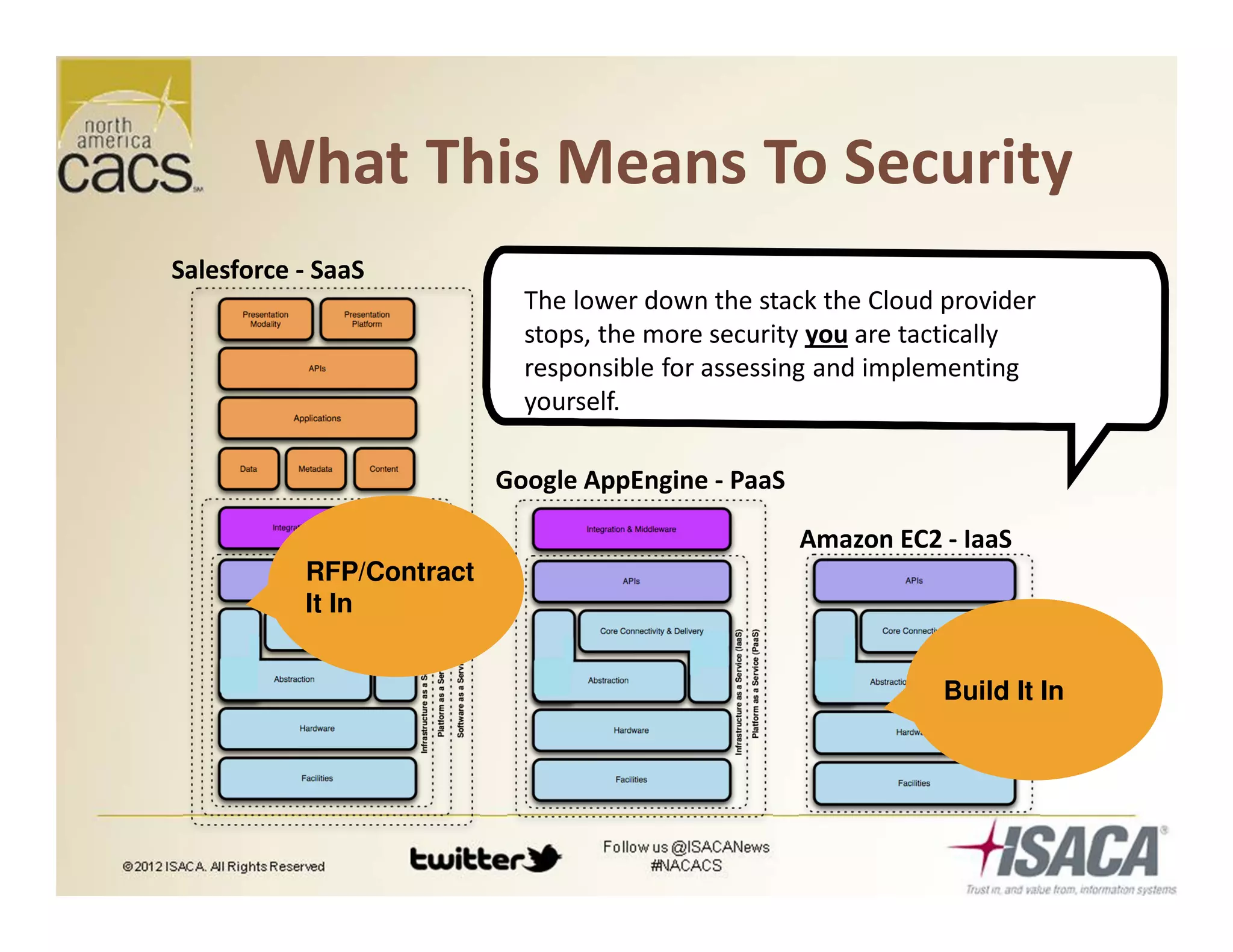
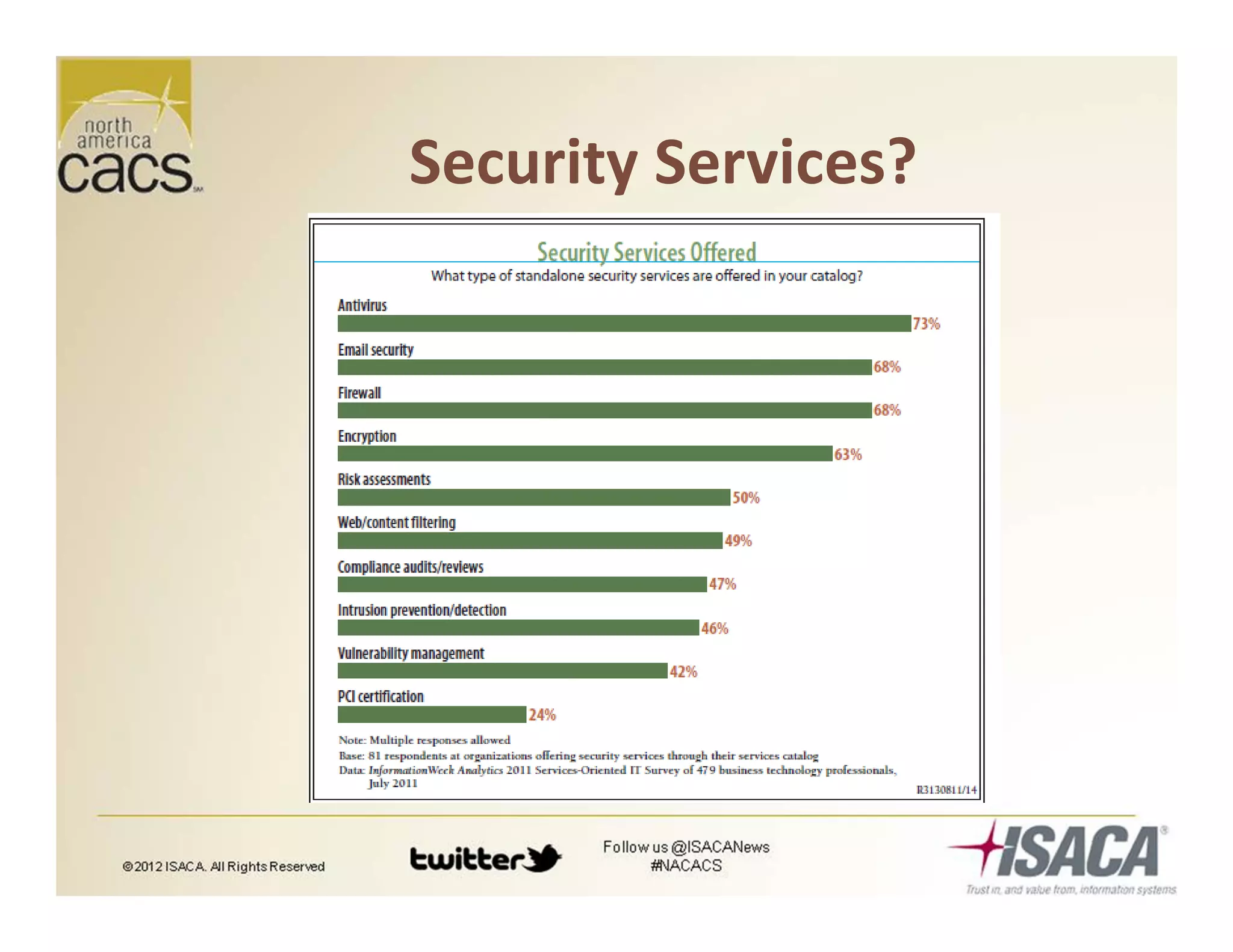
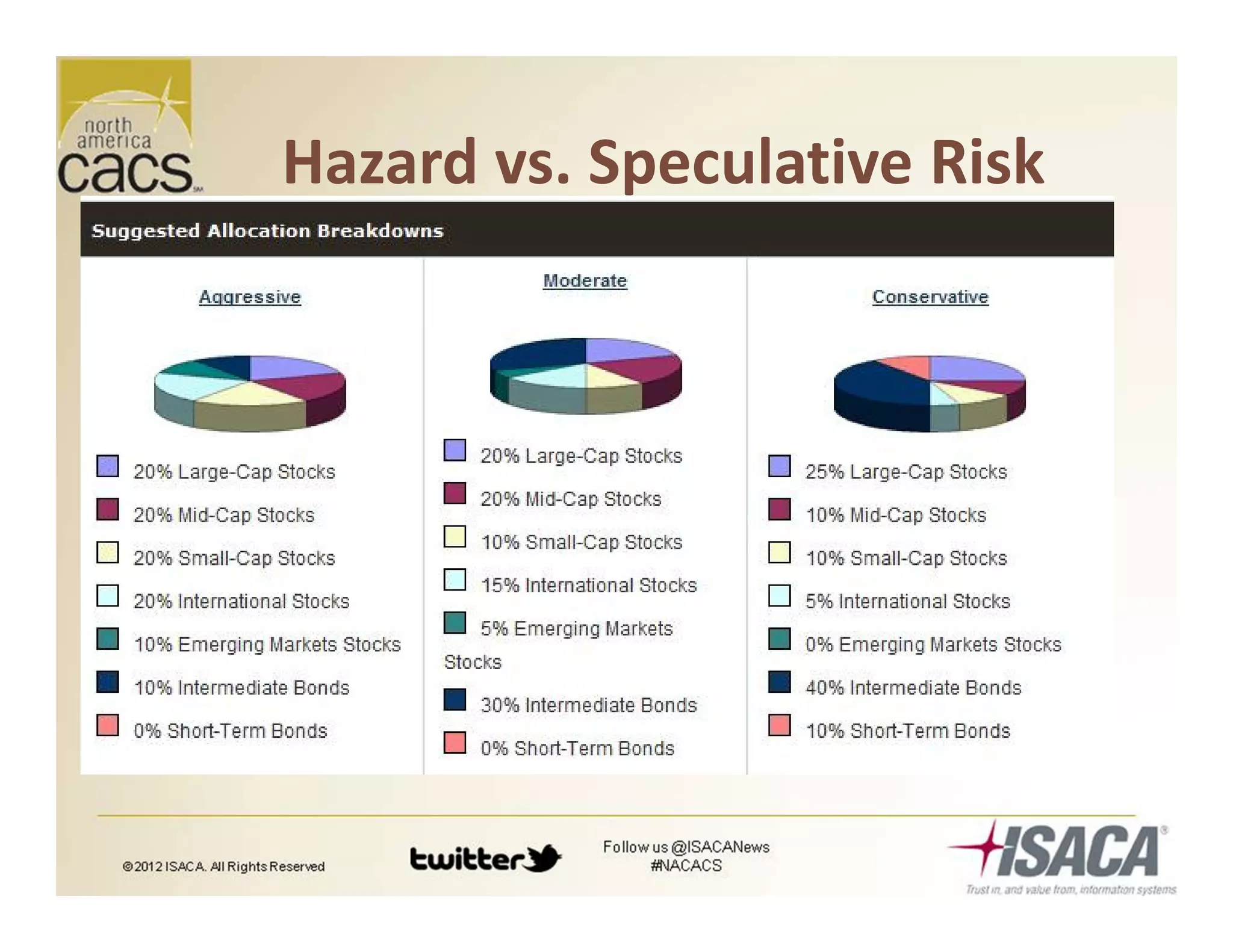
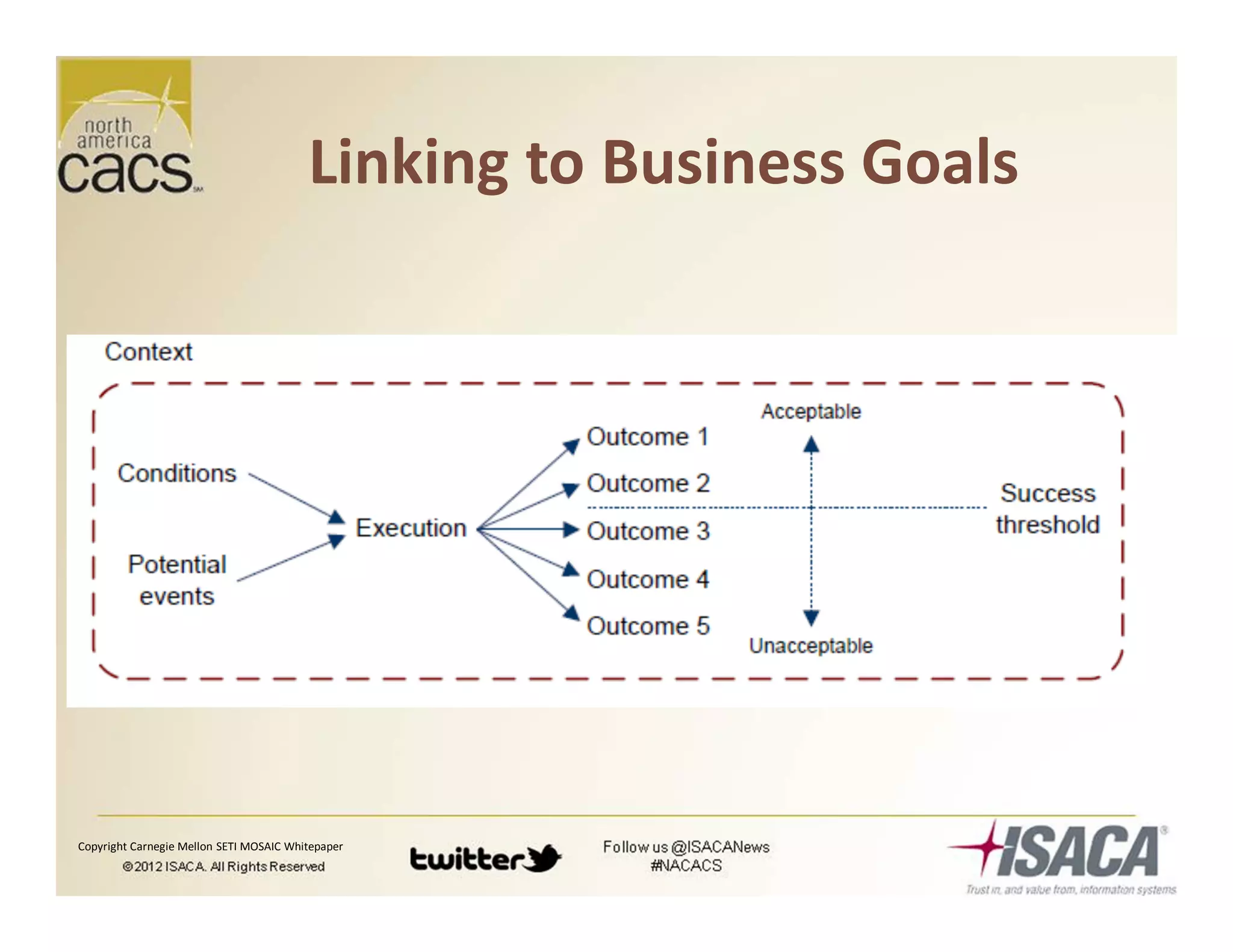
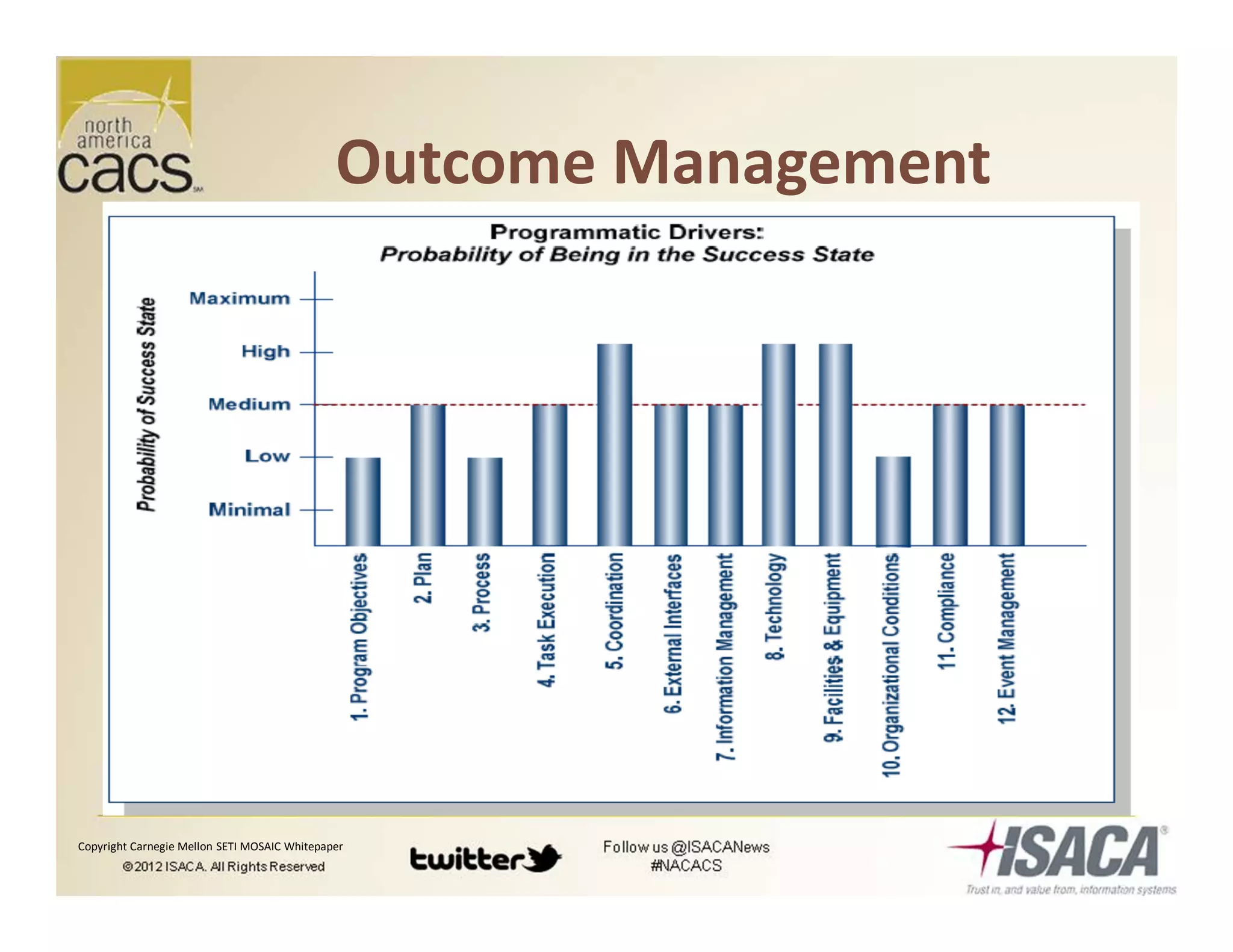
The document discusses trends in security services, specifically focusing on Security as a Service (SECaaS) and the challenges faced by IT audits in a rapidly changing environment. It emphasizes the need for a shift in the fundamental value proposition of IT audits, advocating for a more flexible and customer-focused approach. Key recommendations include enhancing communication, customizing deliverables, and ensuring metrics and transparency to improve security service adoption.