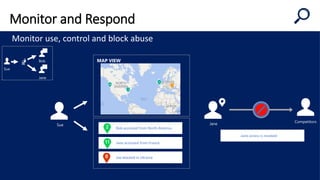
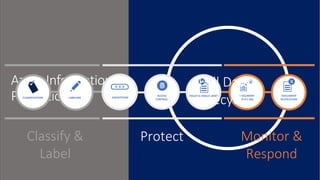
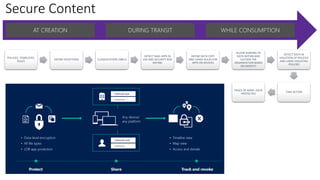
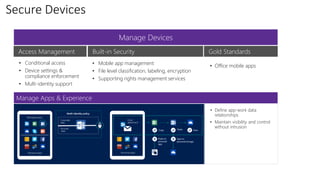
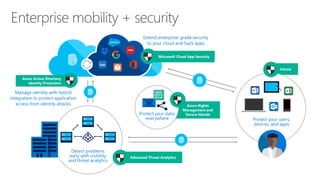
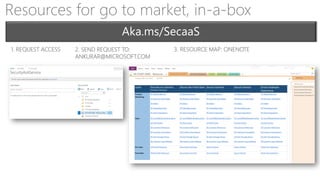
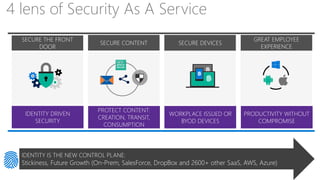
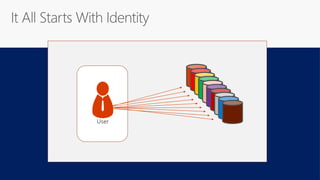
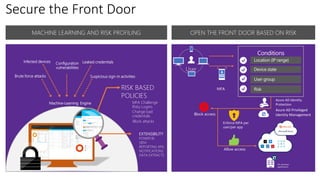
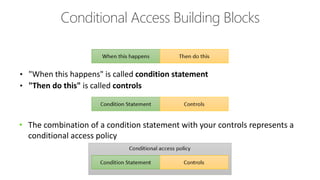
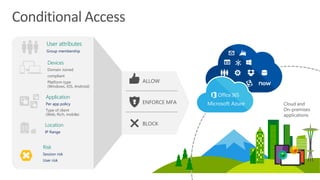
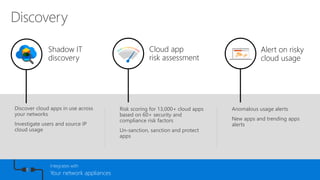
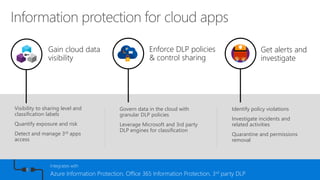
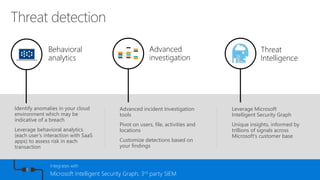
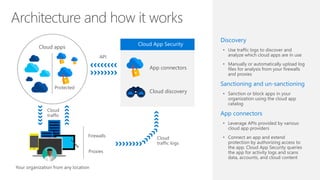
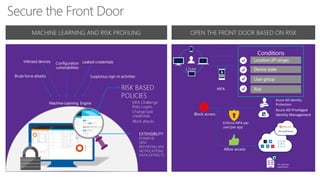
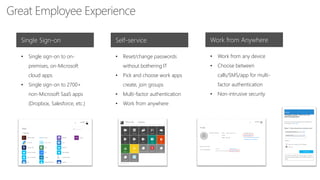
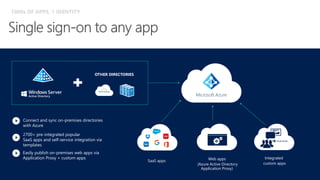
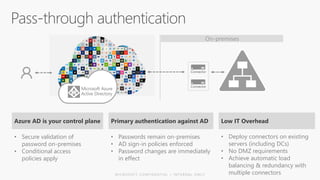
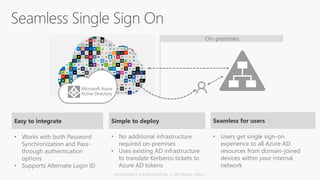
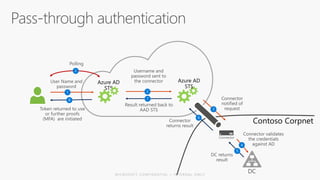
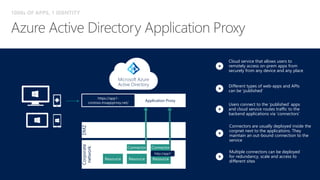
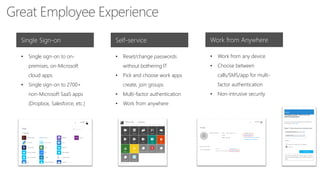
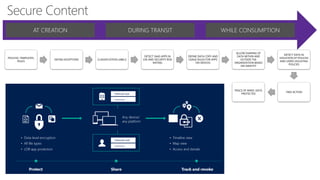
This document discusses security as a service and how it can provide identity-driven security through Azure Active Directory. It describes how Azure AD can secure devices, content, and the "front door" through risk-based conditional access policies leveraging machine learning. This allows blocking of risky logins while providing a great employee experience through single sign-on access to applications on any device with optional multi-factor authentication.

























![aEZQAR]ibr{qU@M]
BXNoHp9nMDAtnBfr
fC;jx+Tg@XL2,Jzu
()&(*7812(*:
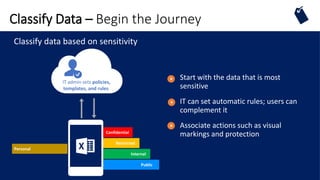
Use rights +
Secret cola formula
Water
Sugar
Brown #16
PROTECT
Usage rights and symmetric
key stored in file as “license”
Each file is protected by
a unique AES symmetric
License protected
by customer-owned RSA
key
Water
Sugar
Brown #16
UNPROTECT
How Protection Works](https://image.slidesharecdn.com/secaasppt-170510111029/85/Security-As-A-Service-48-320.jpg)
![Use rights
+
Azure RMS never sees
the file content, only
the license
How Protection Works
Apps protected with
RMS enforce rights
SDK
Apps use the SDK to
communicate with the
RMS service/servers
File content is never sent to
the RMS server/service
aEZQAR]ibr{qU@M]B
XNoHp9nMDAtnBfrfC
;jx+Tg@XL2,Jzu
()&(*7812(*:
Use rights
+
LOCAL PROCESSING ON PCS/DEVICES](https://image.slidesharecdn.com/secaasppt-170510111029/85/Security-As-A-Service-49-320.jpg)