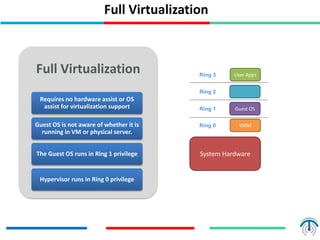
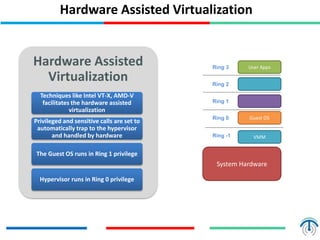
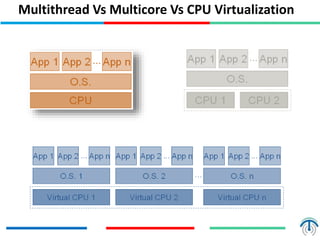
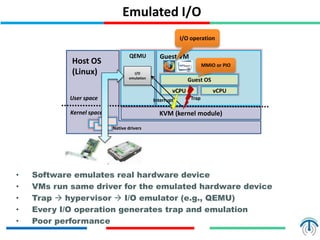
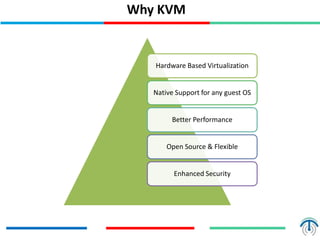
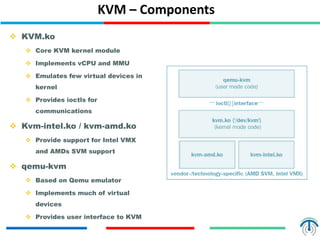
Server virtualization concepts allow partitioning of physical servers into multiple virtual servers using virtualization software and hardware techniques. This improves resource utilization by running multiple virtual machines on a single physical server. Server virtualization provides benefits like reduced costs, higher efficiency, lower power consumption, and improved availability compared to running each application on its own physical server. Key components of server virtualization include virtual machines, hypervisors, CPU virtualization using techniques like Intel VT-x or AMD-V, memory virtualization, and I/O virtualization through methods like emulated, paravirtualized or direct I/O. KVM and QEMU are popular open source virtualization solutions, with KVM providing kernel-level virtualization support and Q