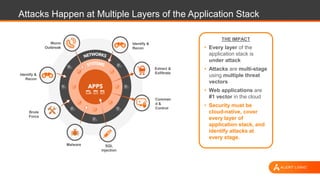
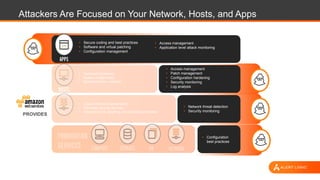
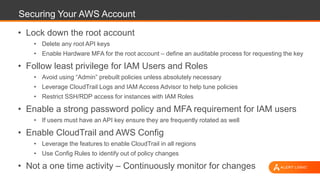
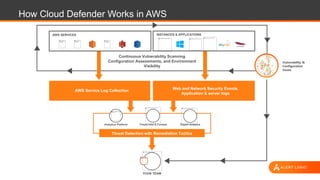
The document outlines strategies for securing AWS environments against multi-layered attacks, emphasizing the importance of cloud-native security practices. It recommends measures such as securing AWS accounts, continuous monitoring, and implementing network and log visibility tools. Additionally, it highlights the need for strong access management, secure coding practices, and proactive identification of vulnerabilities.