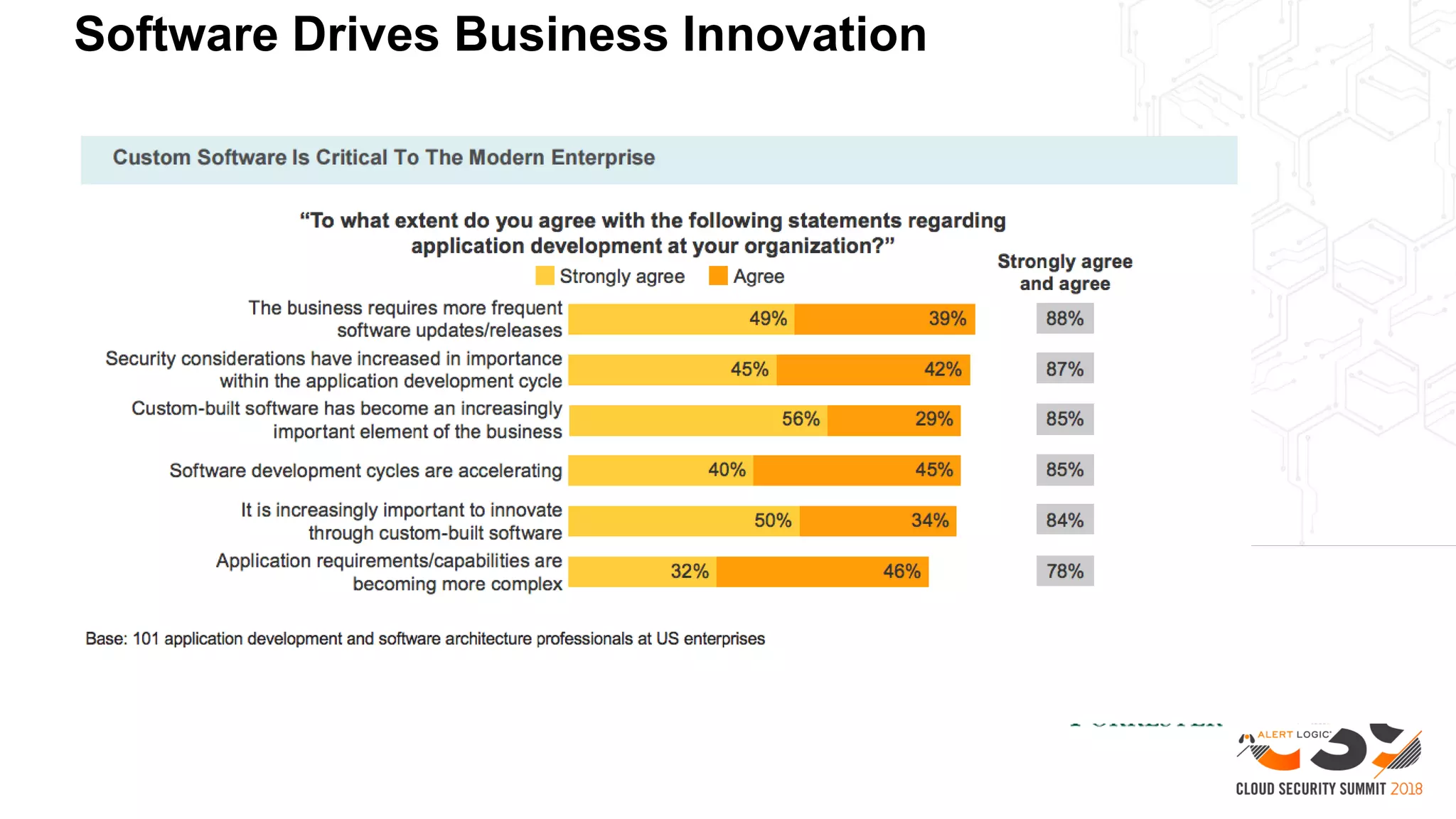
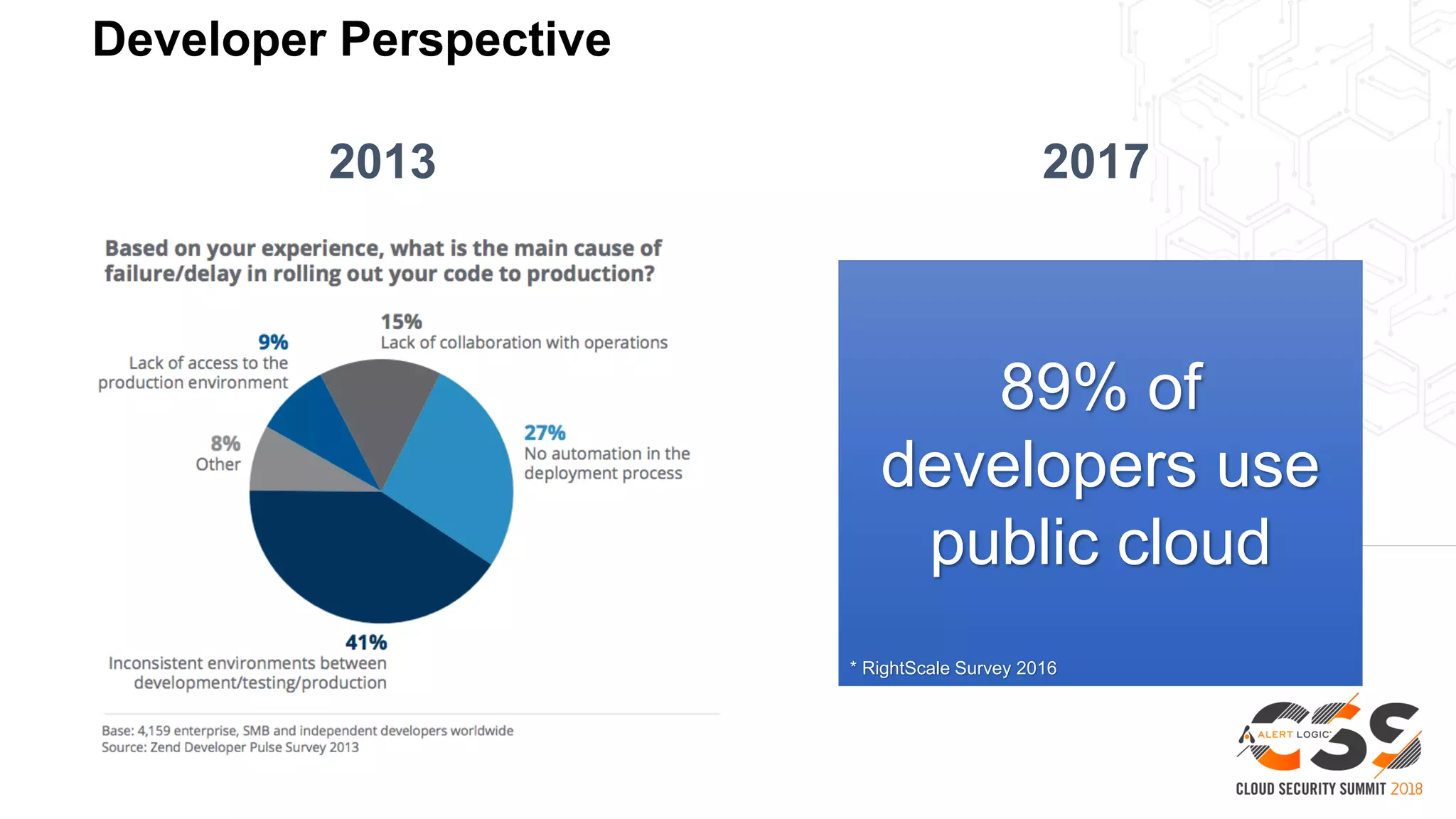
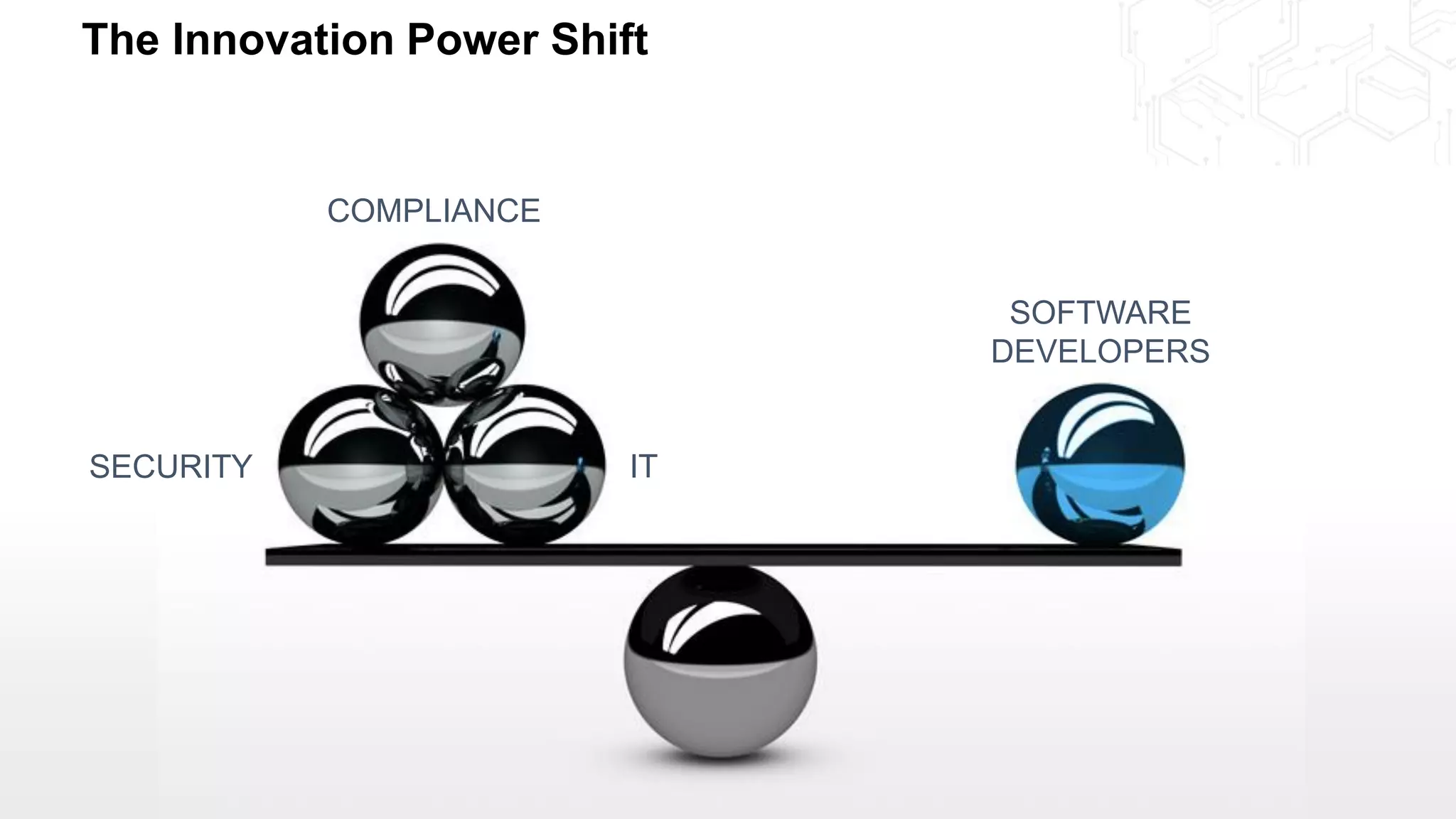
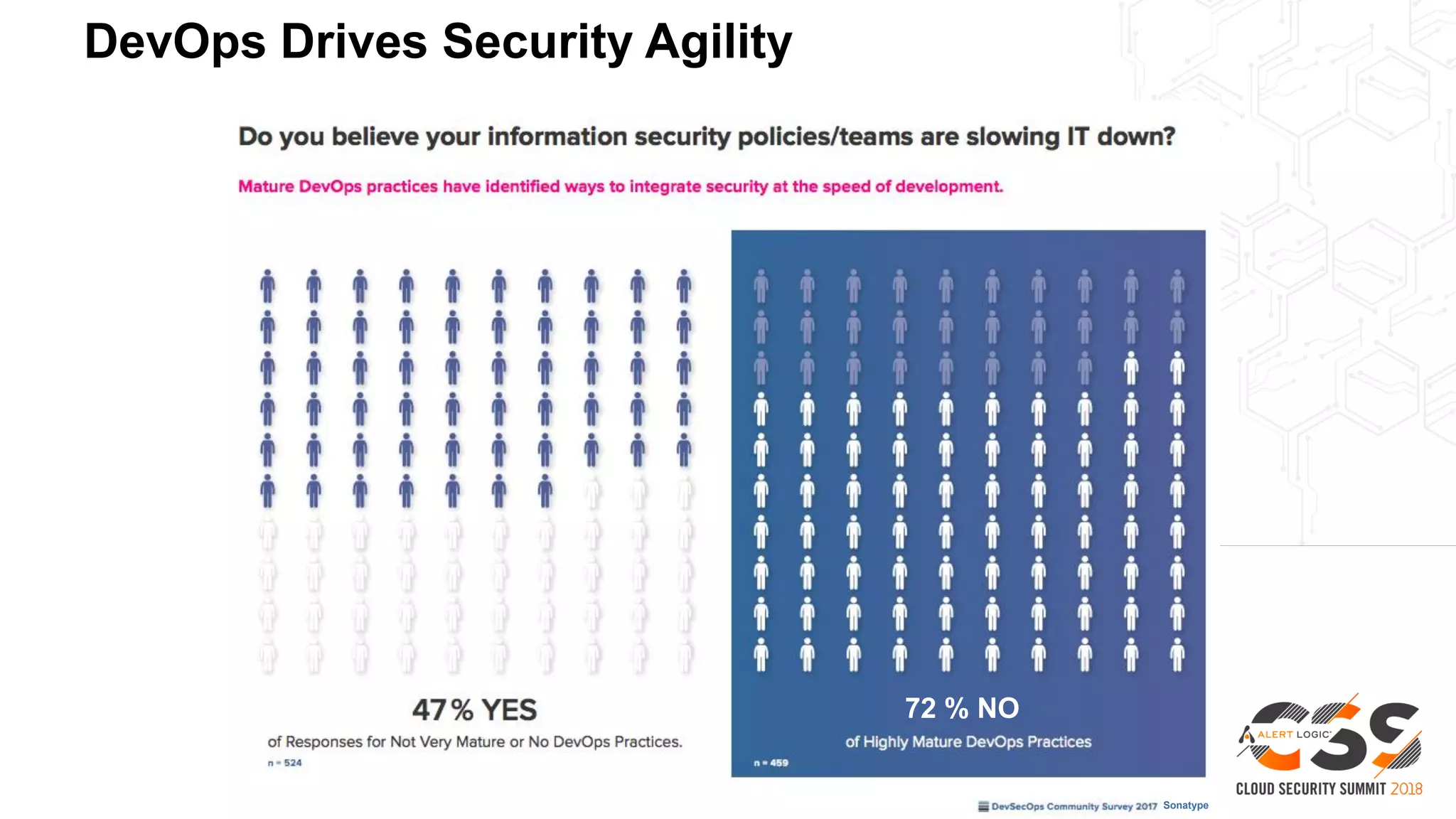
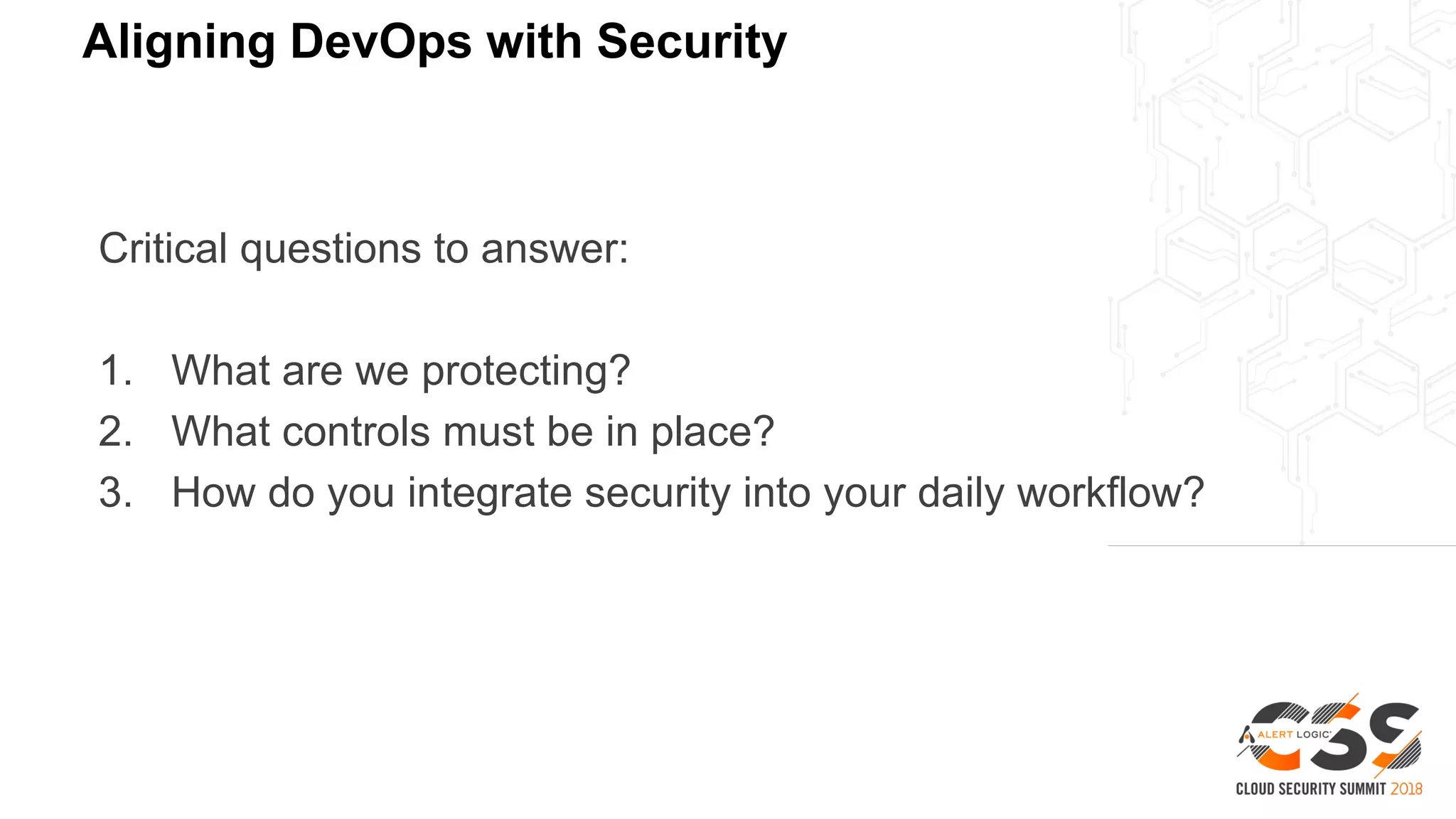
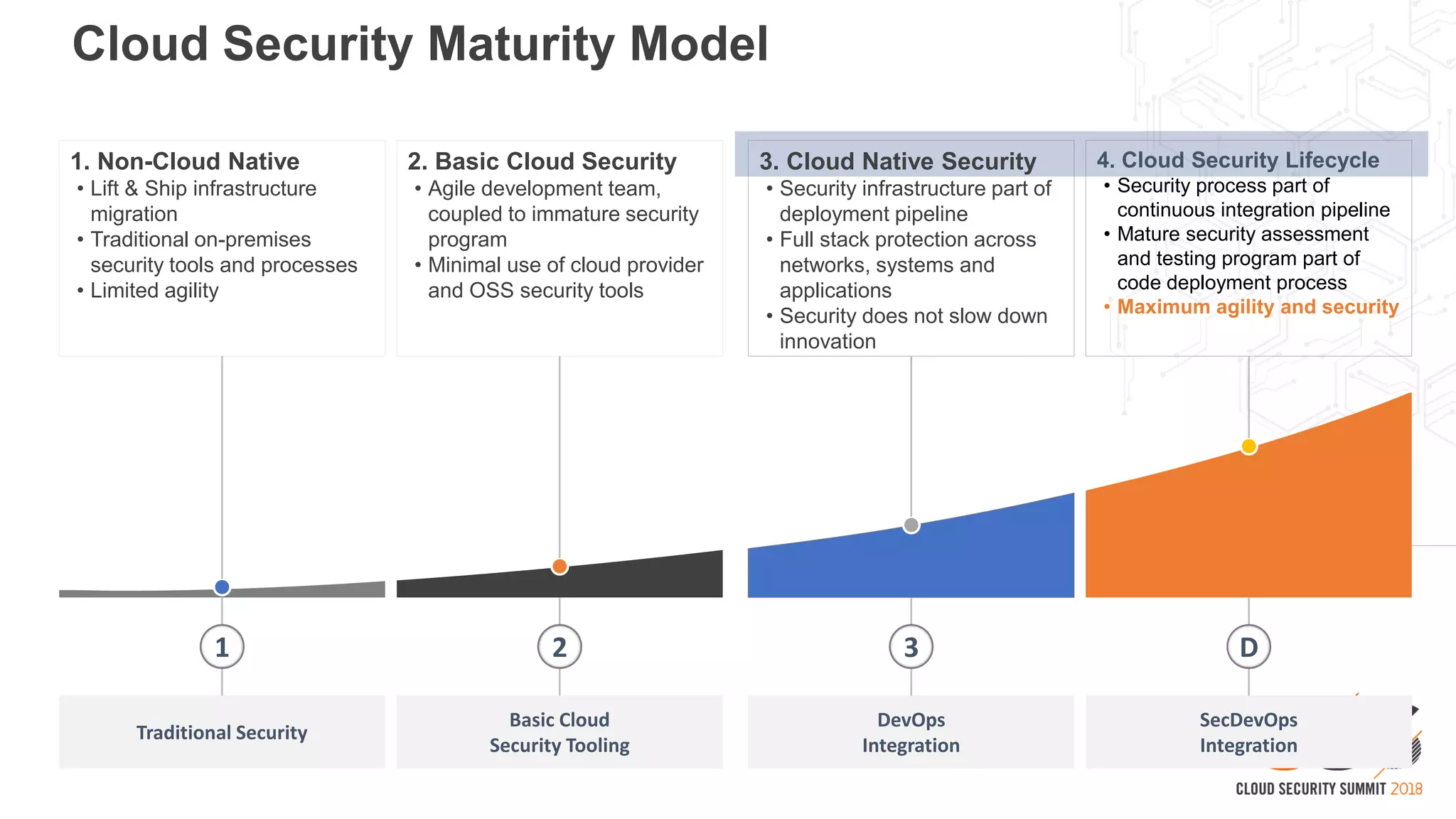
1. As developers have become the driving force behind cloud adoption, there is a need to realign security practices with DevOps workflows and priorities.
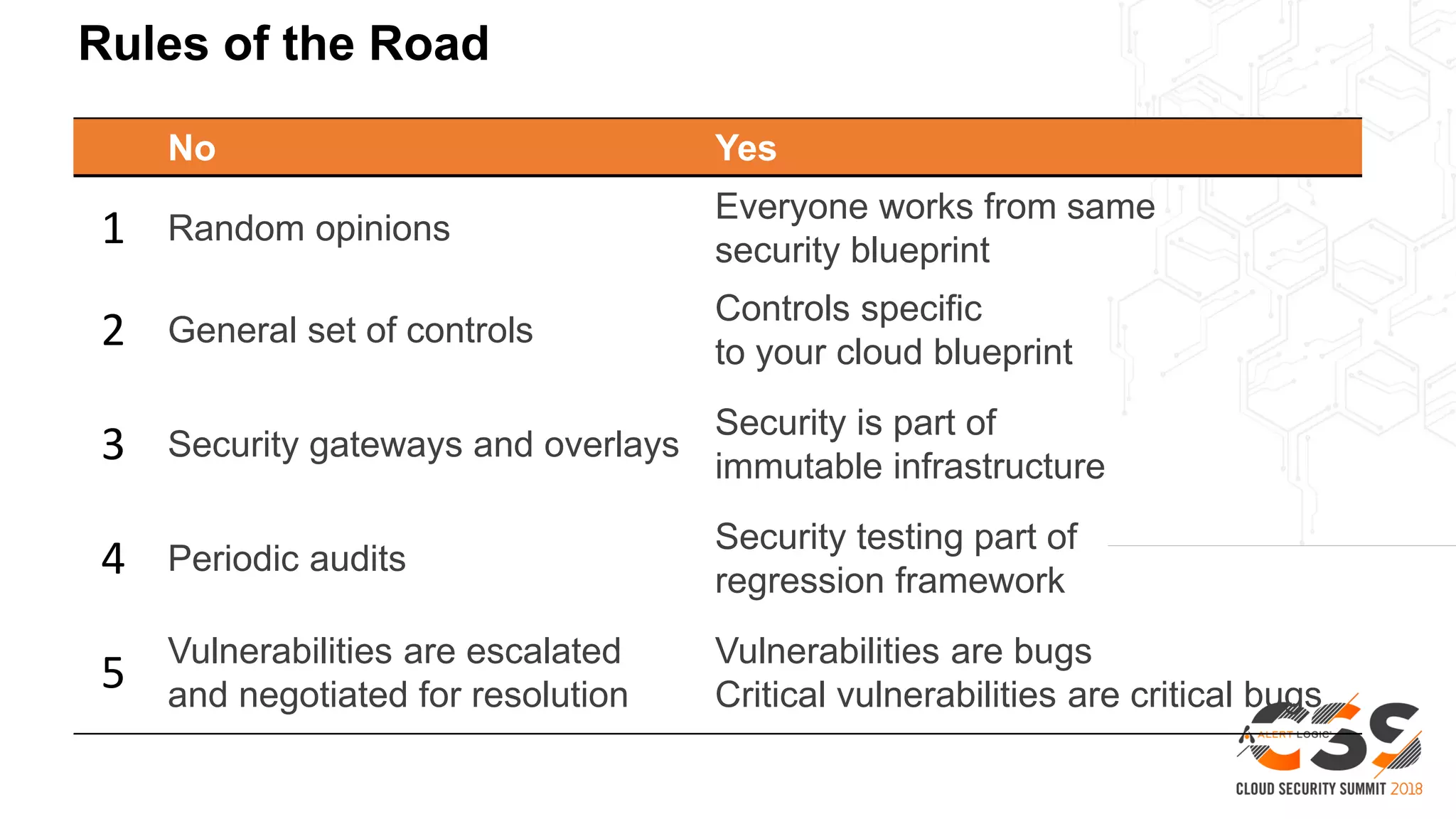
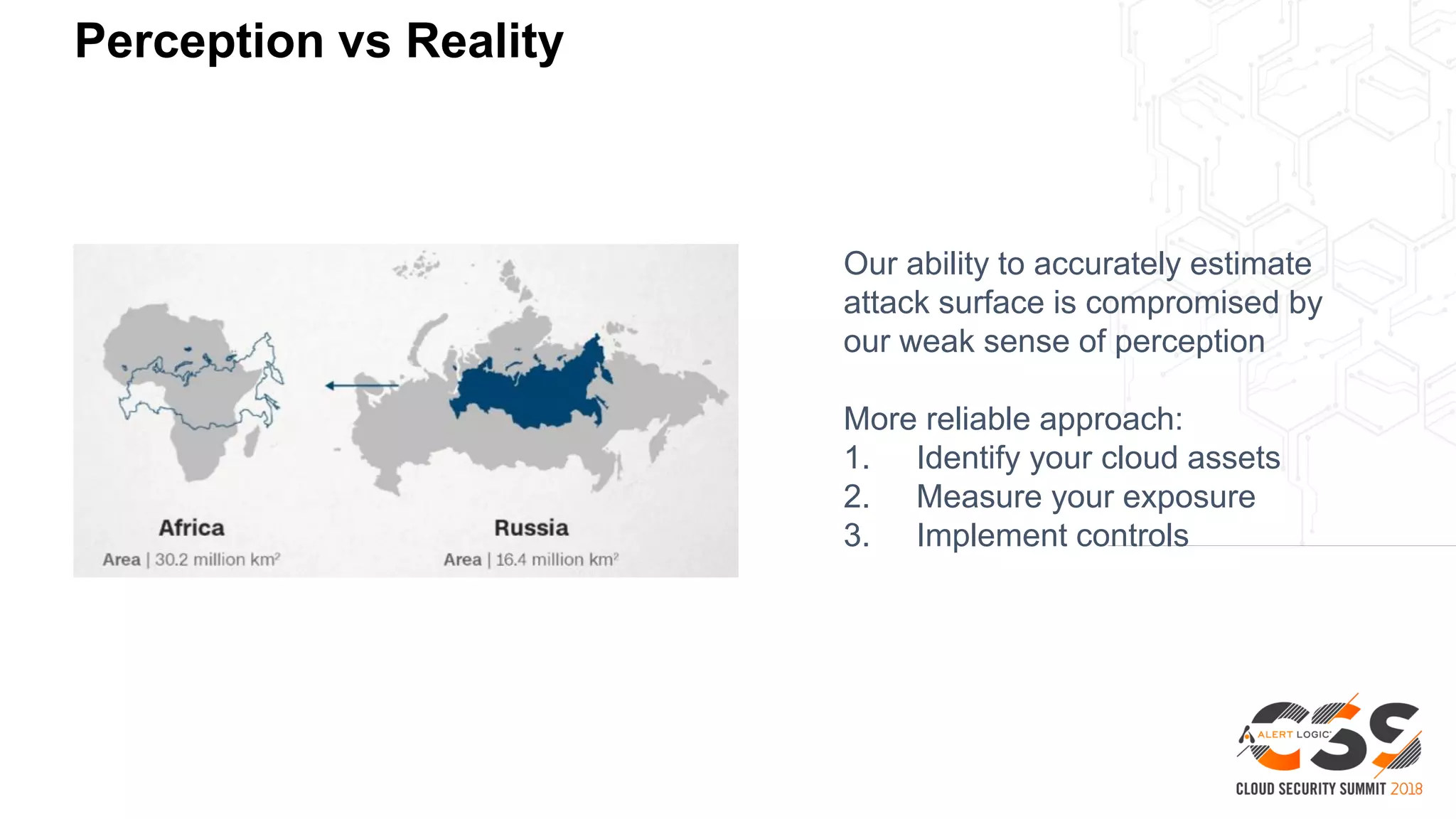
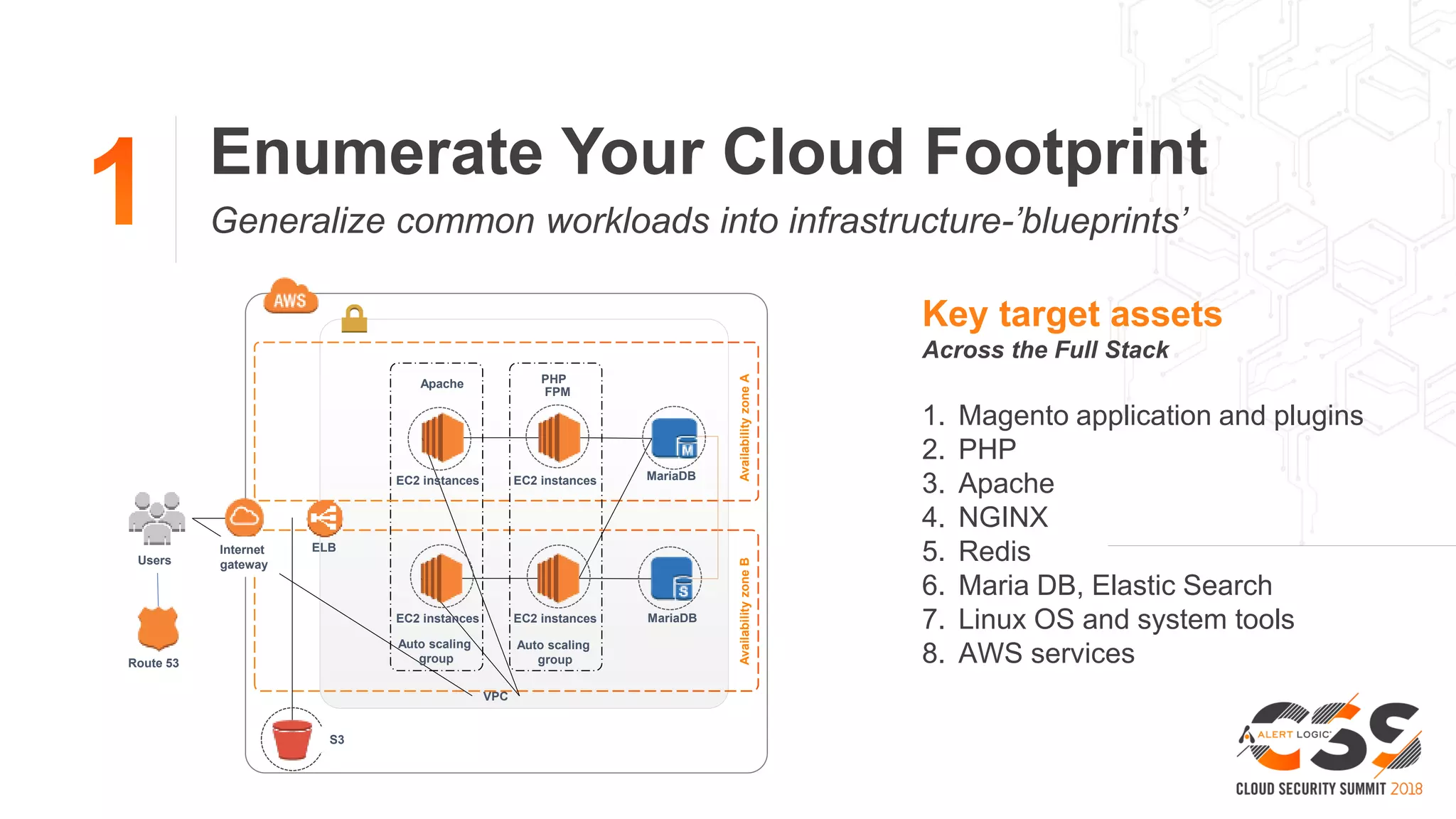
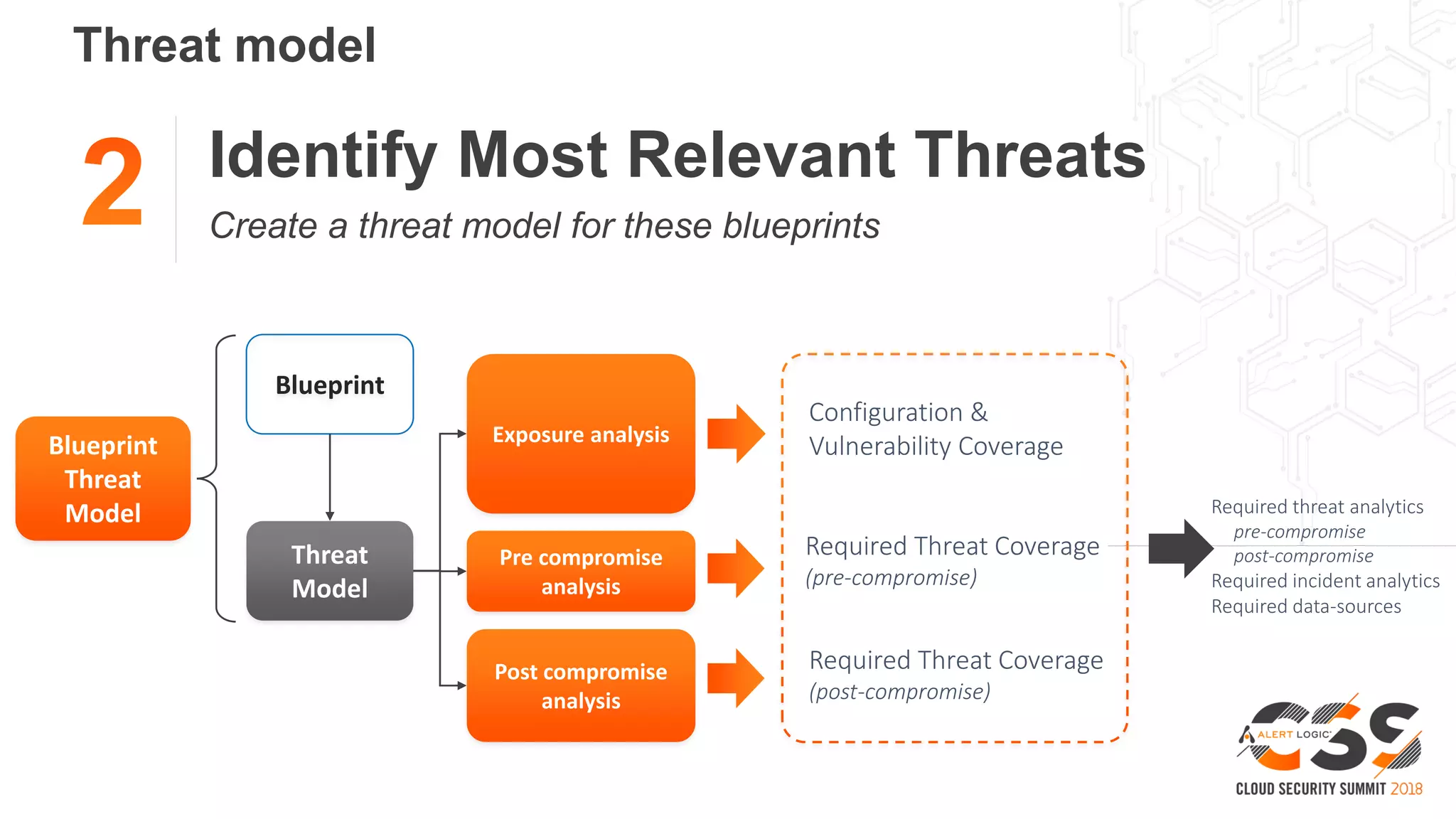
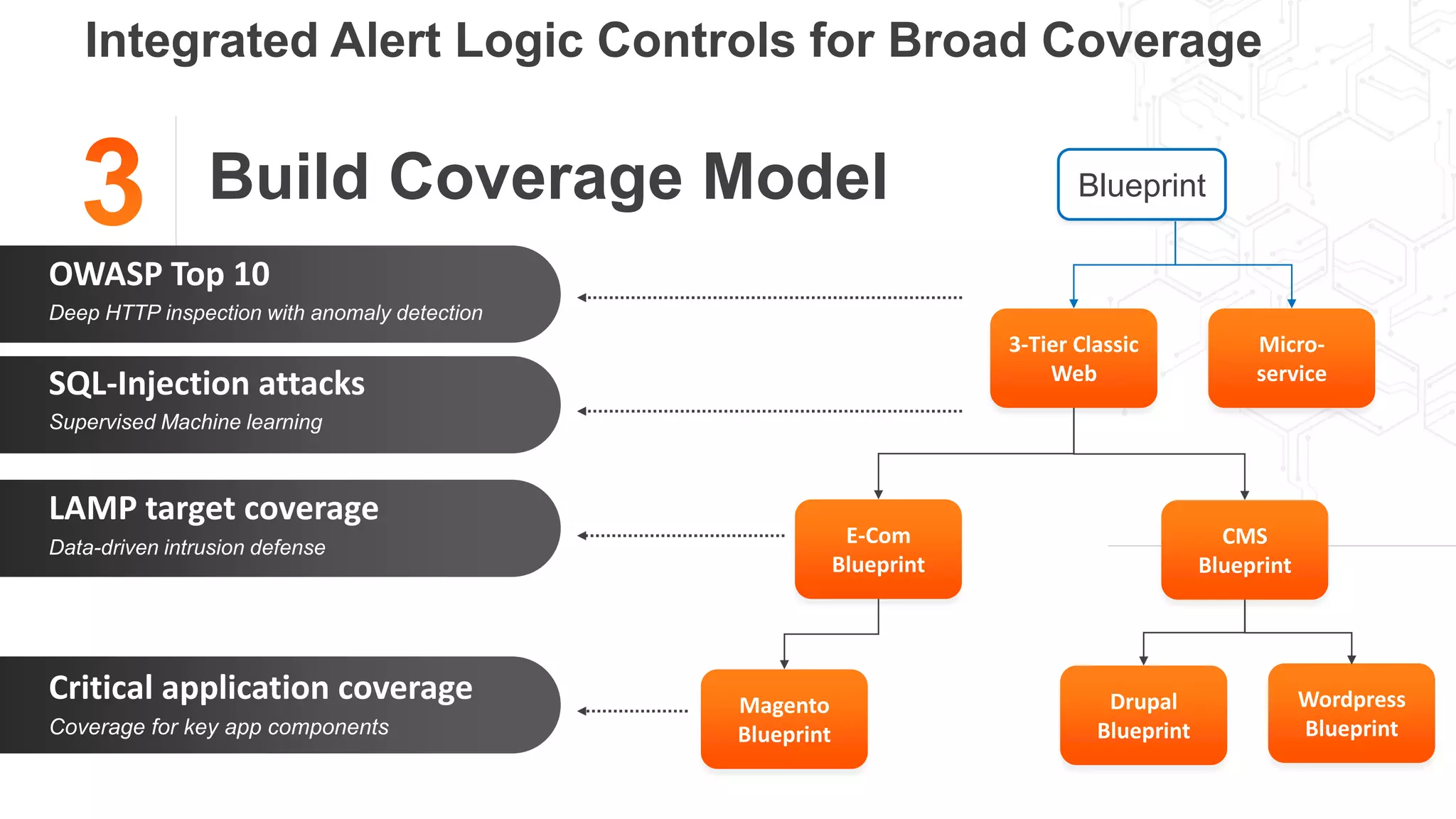
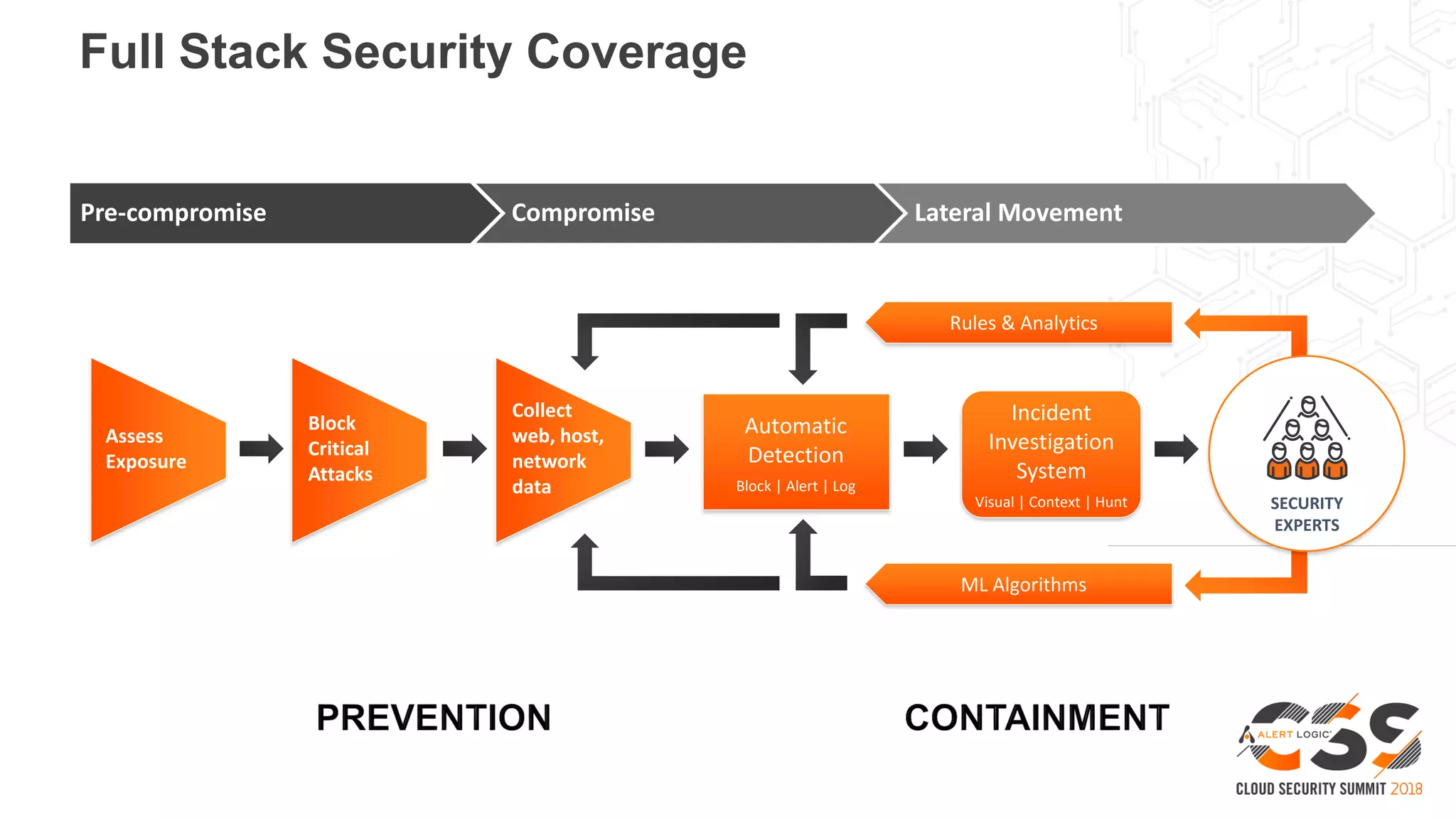
2. A blueprint approach to cloud security involves enumerating cloud assets, threat modeling for common workloads, and integrating controls across the full technology stack.
3. With a blueprint model and automated security tools integrated into the development pipeline, security can provide coverage throughout the software development lifecycle without slowing innovation or agility.