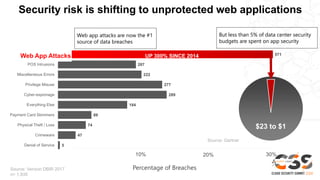
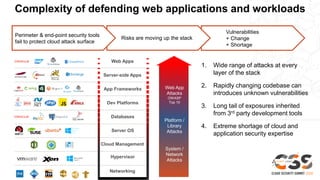
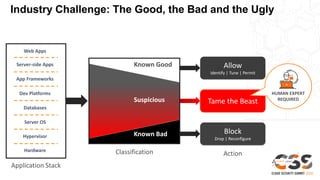
Web application attacks are now the number one source of data breaches, accounting for over 30% of all breaches. However, less than 5% of security budgets are spent on application security. The risks are shifting to unprotected web applications and workloads due to a wide range of attacks at every layer of the stack, rapidly changing codebases that can introduce vulnerabilities, and a shortage of cloud and application security expertise. Perimeter and endpoint security tools fail to protect cloud attack surfaces, so a new approach is needed that can identify, tune, and permit known good traffic while blocking known bad and suspicious traffic across the entire application stack.