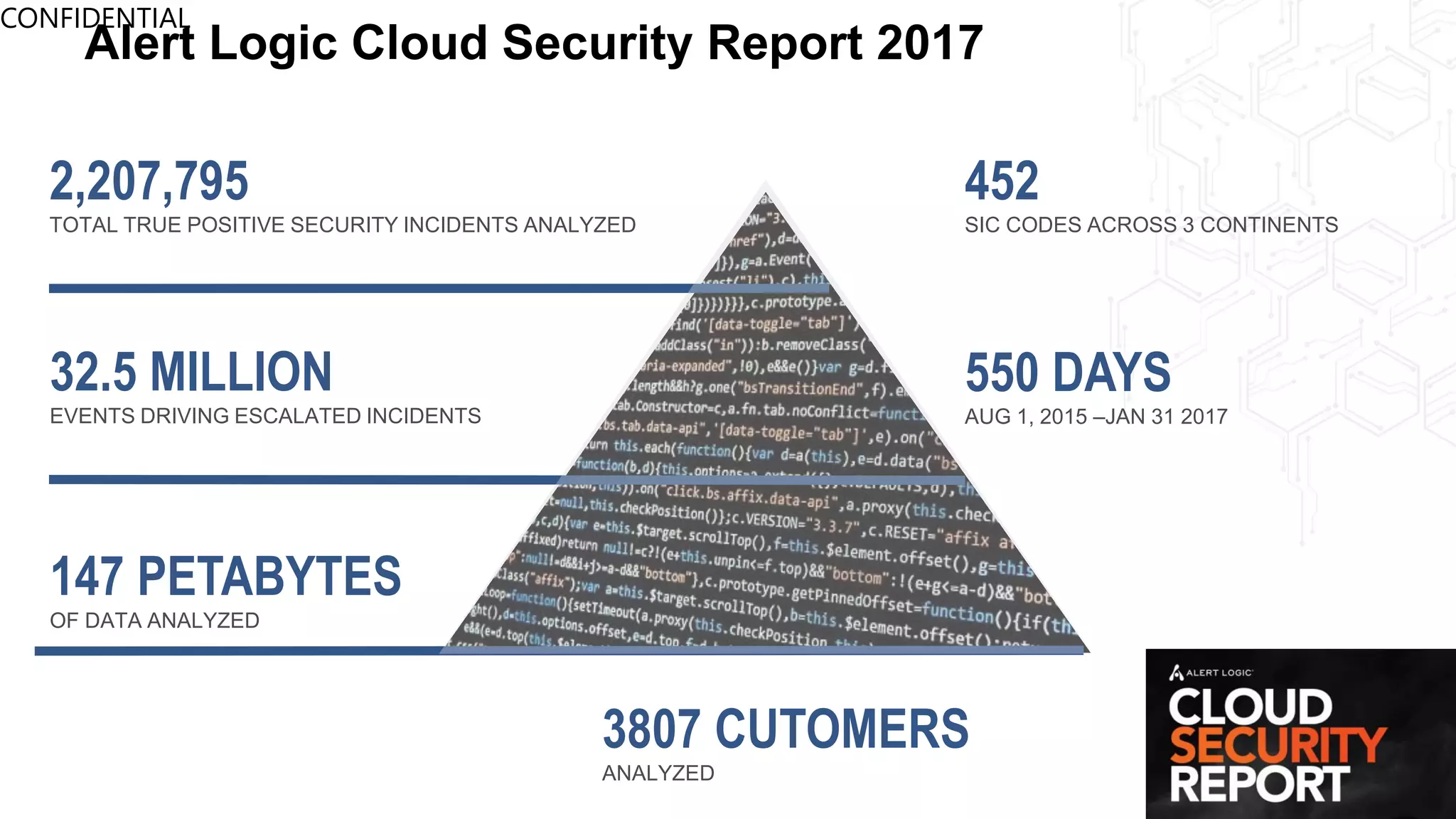
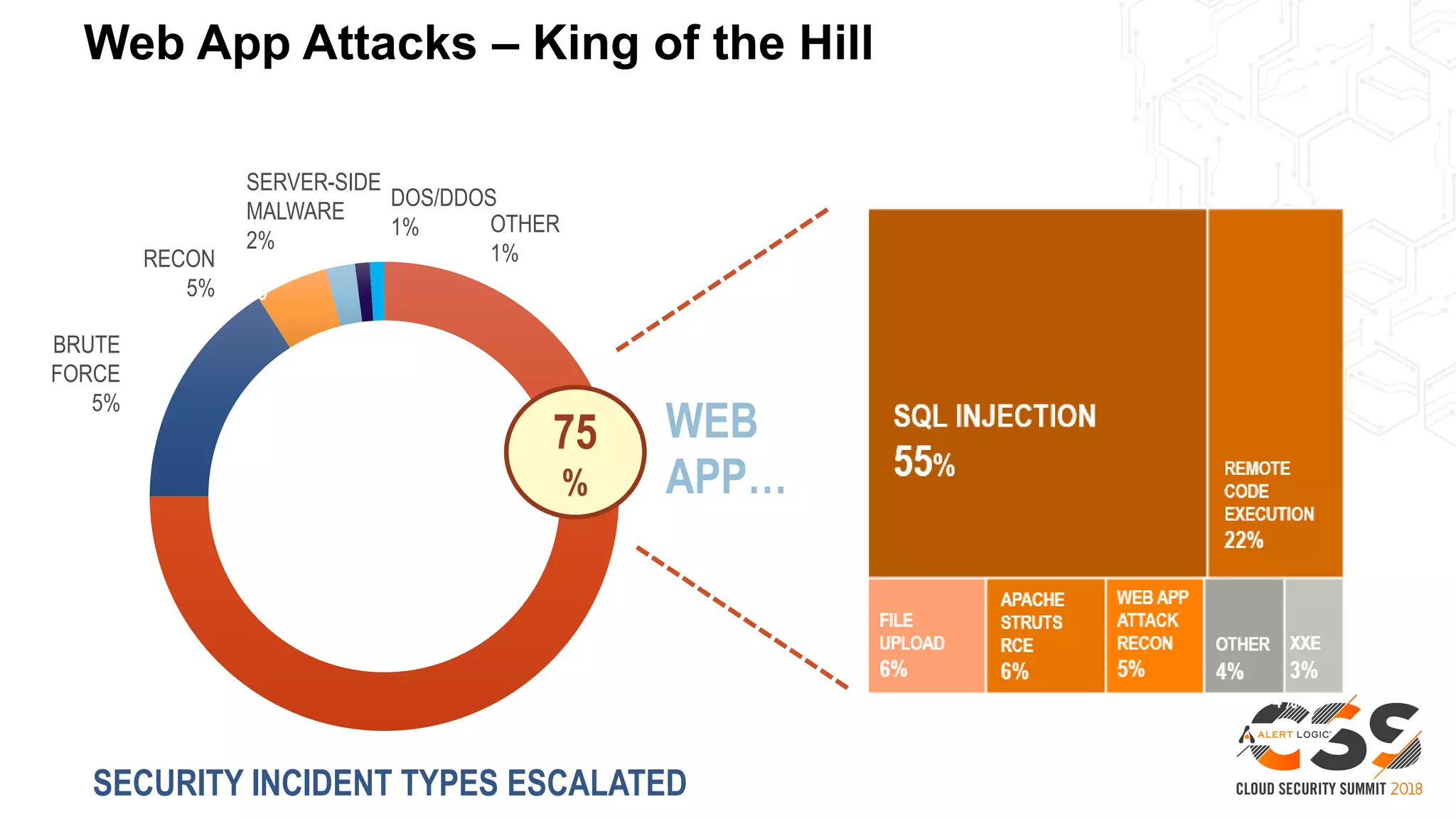
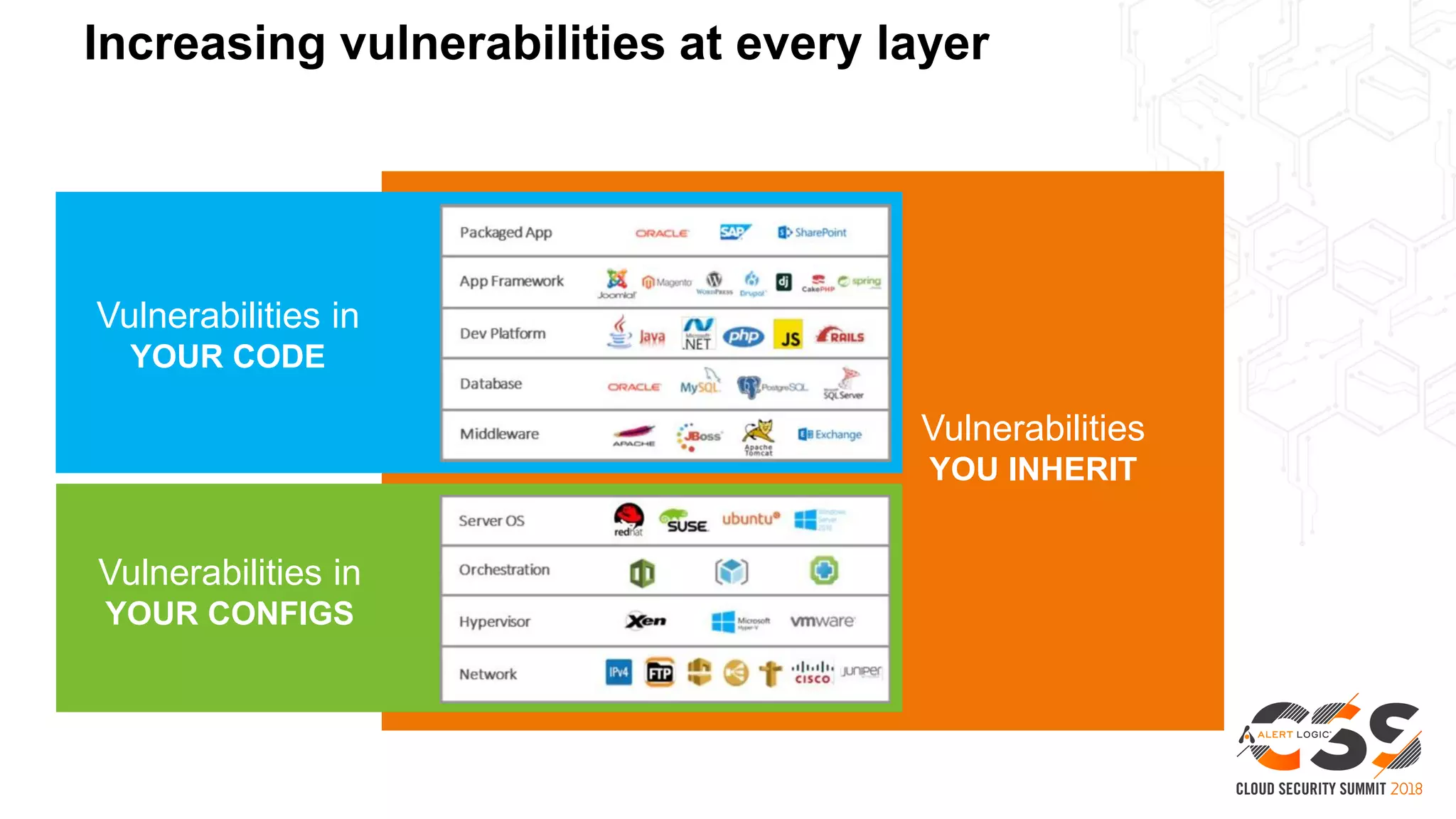
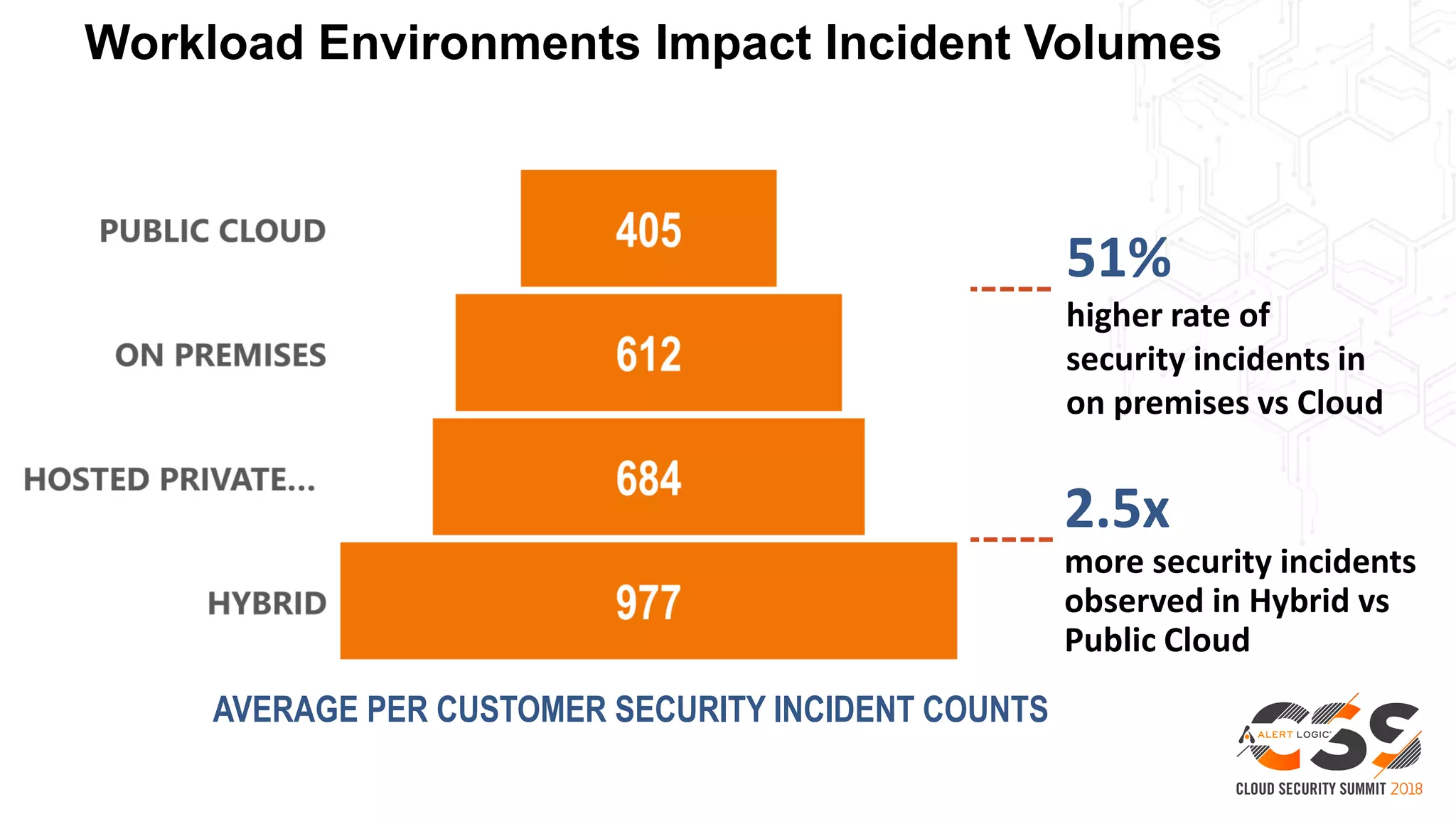
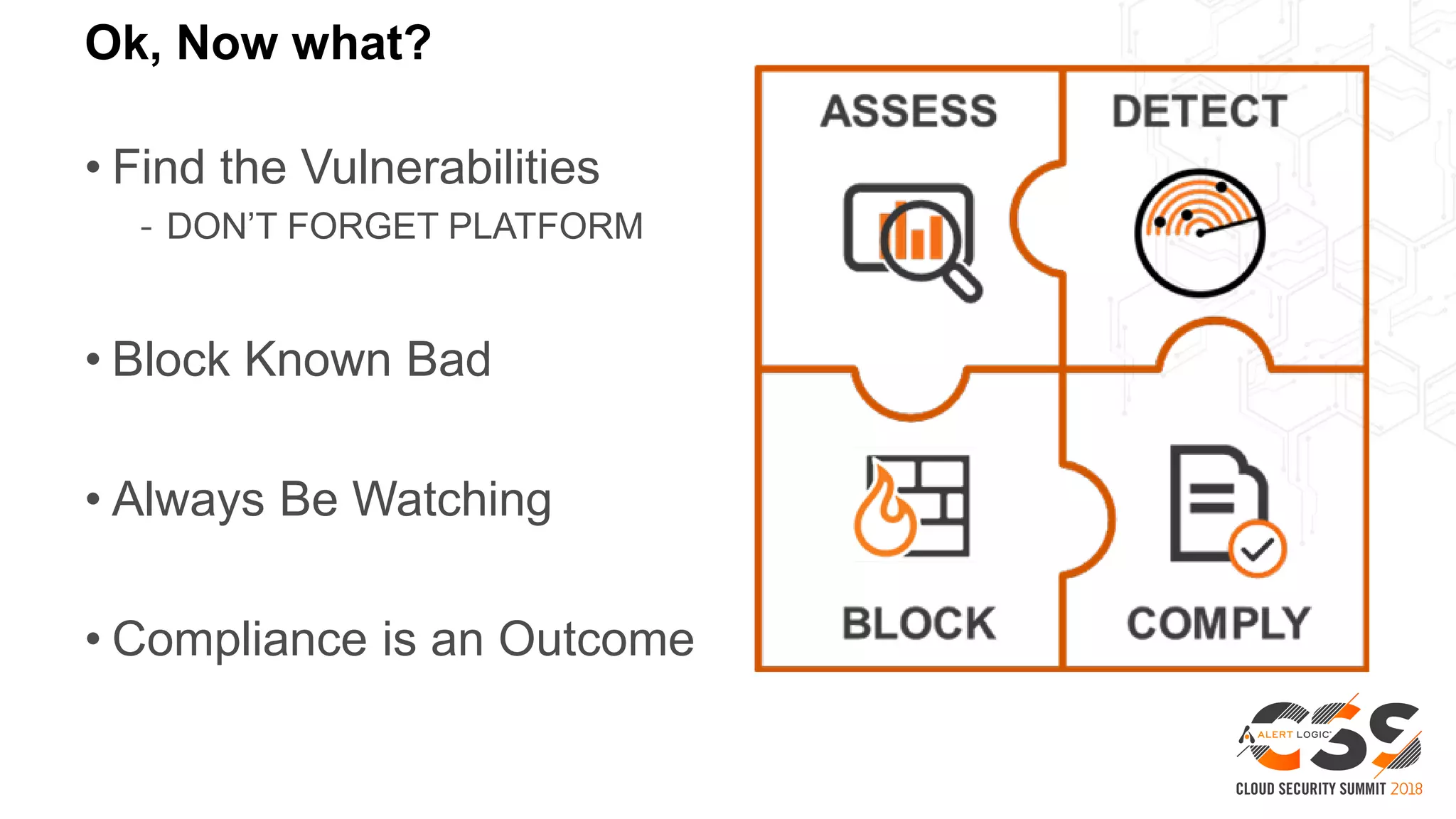
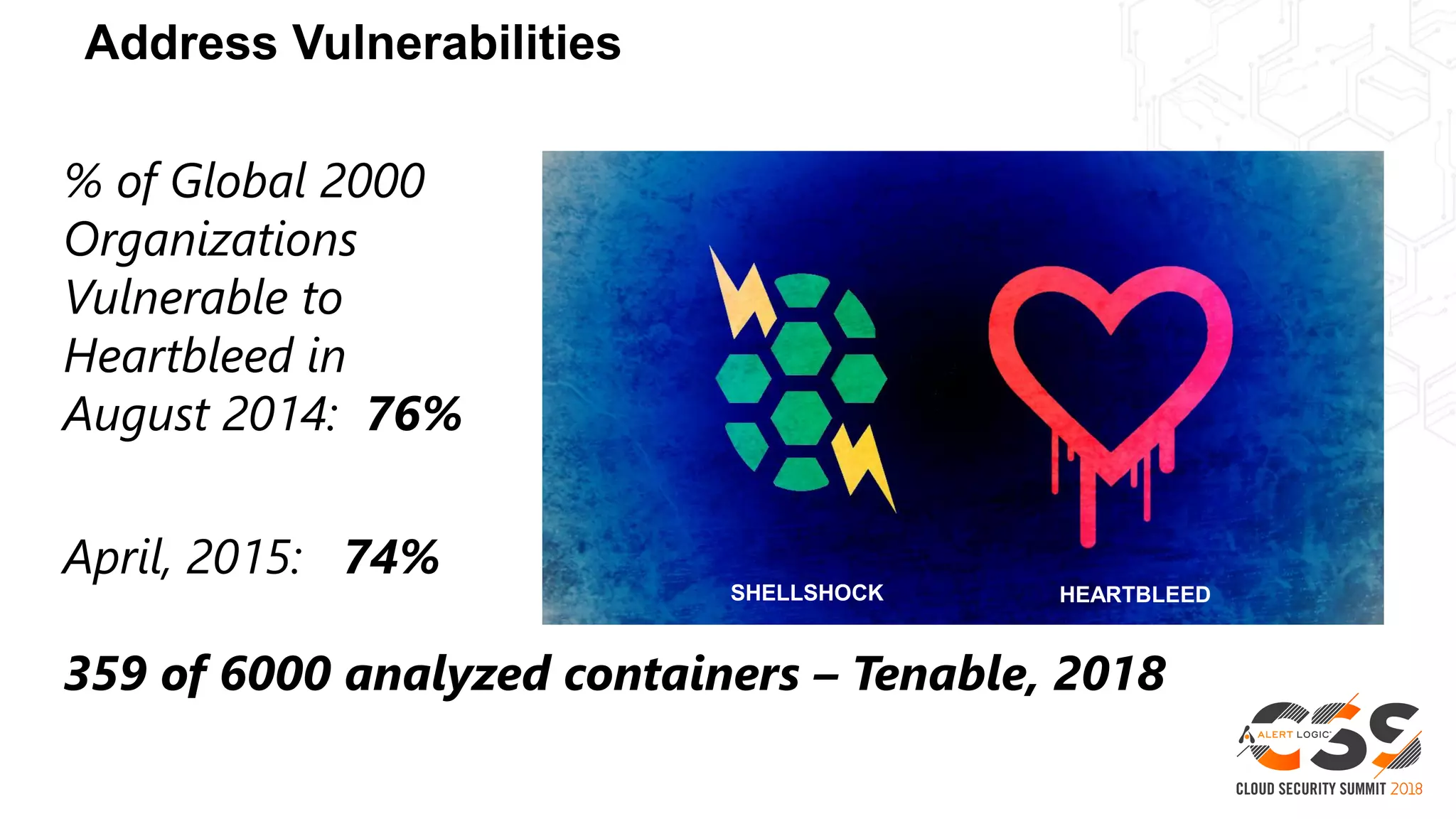
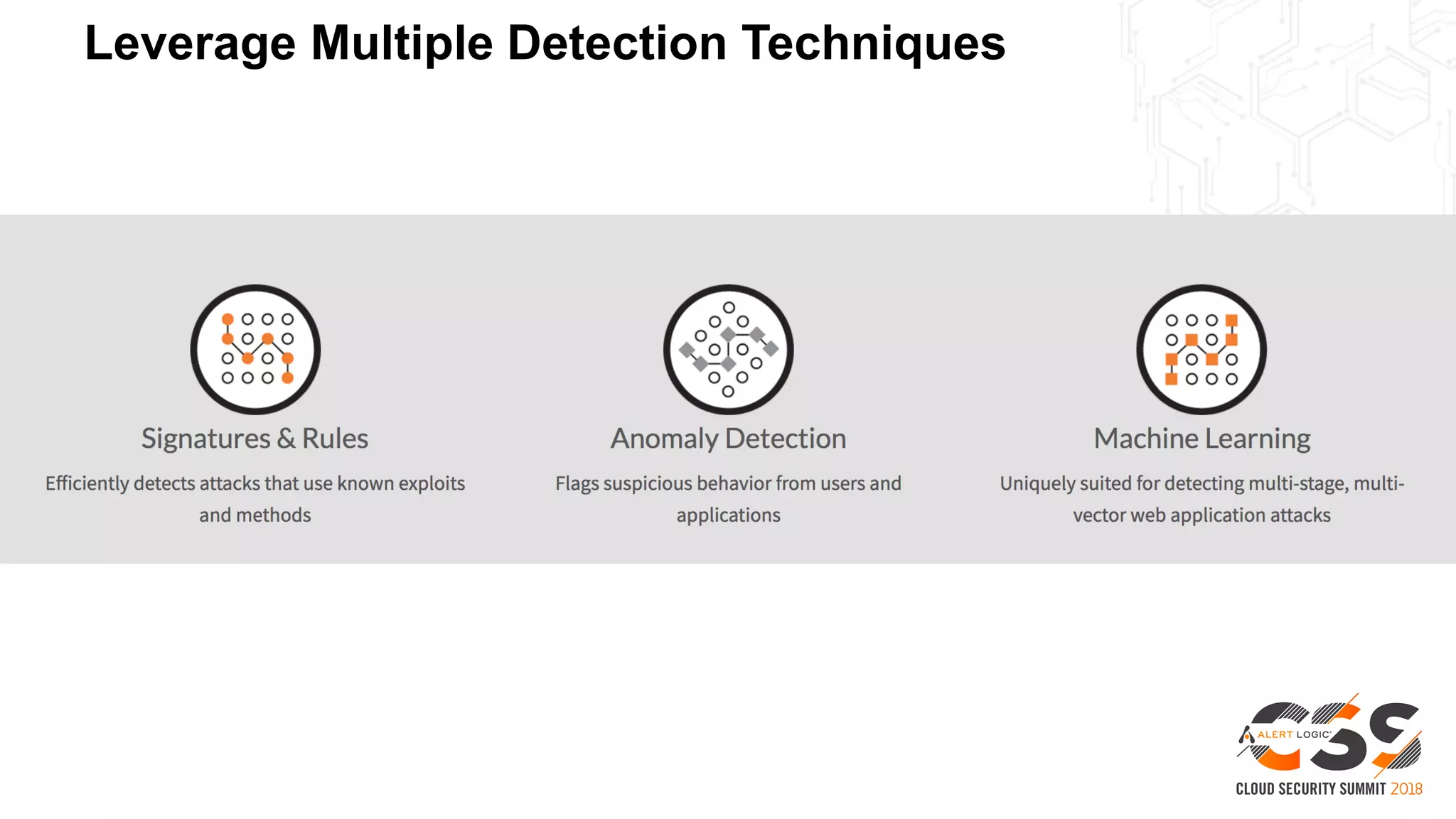
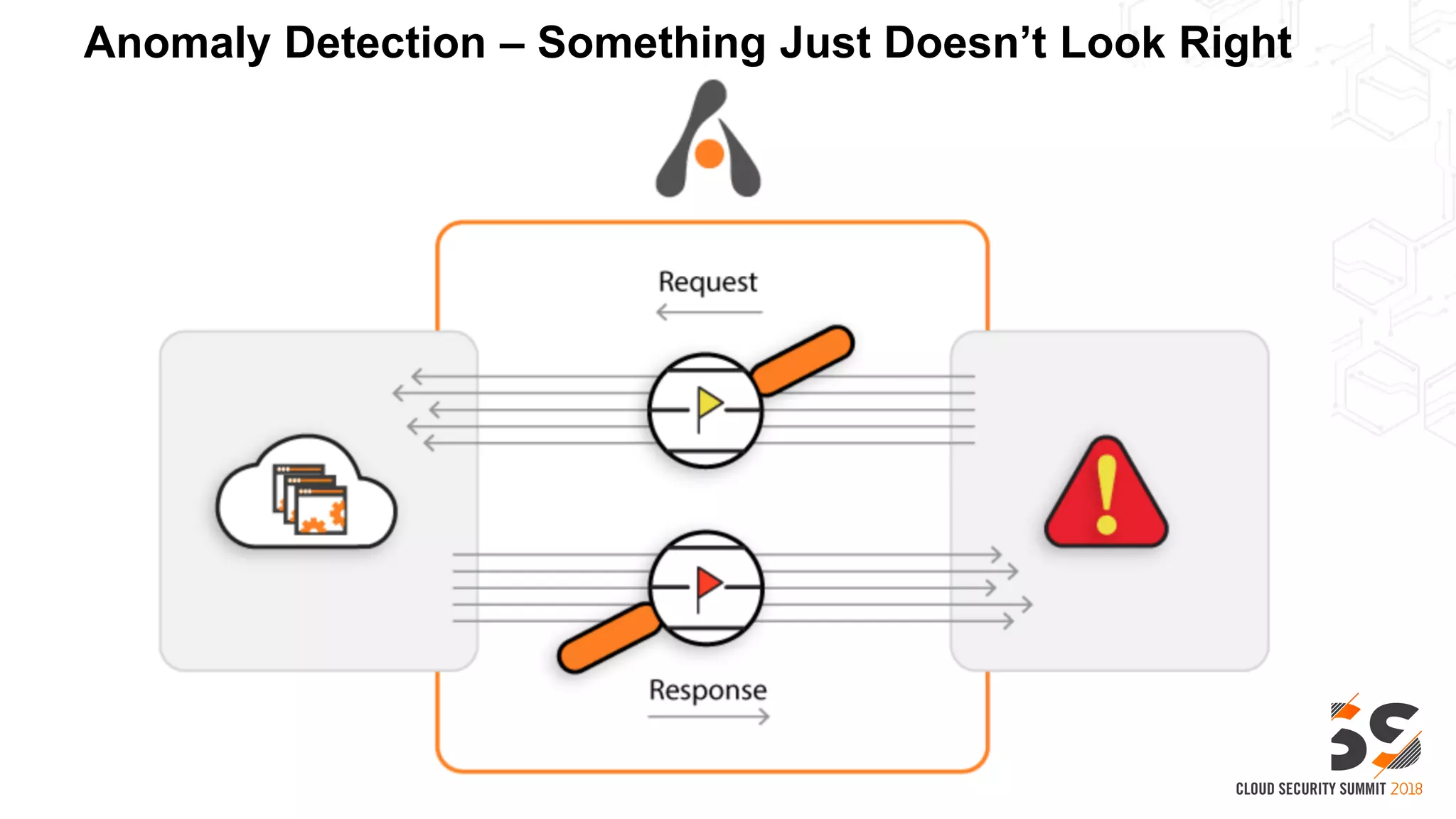
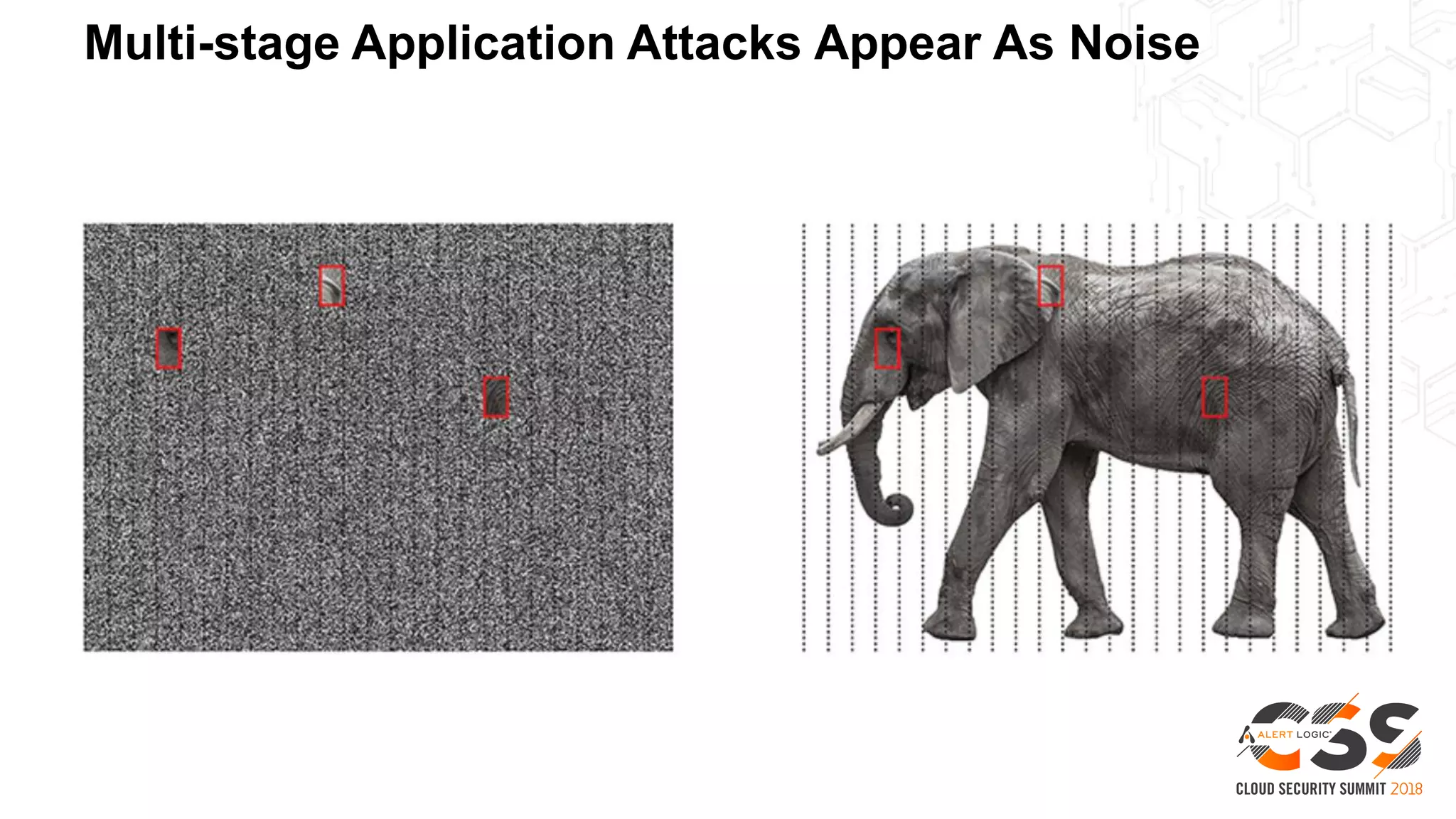
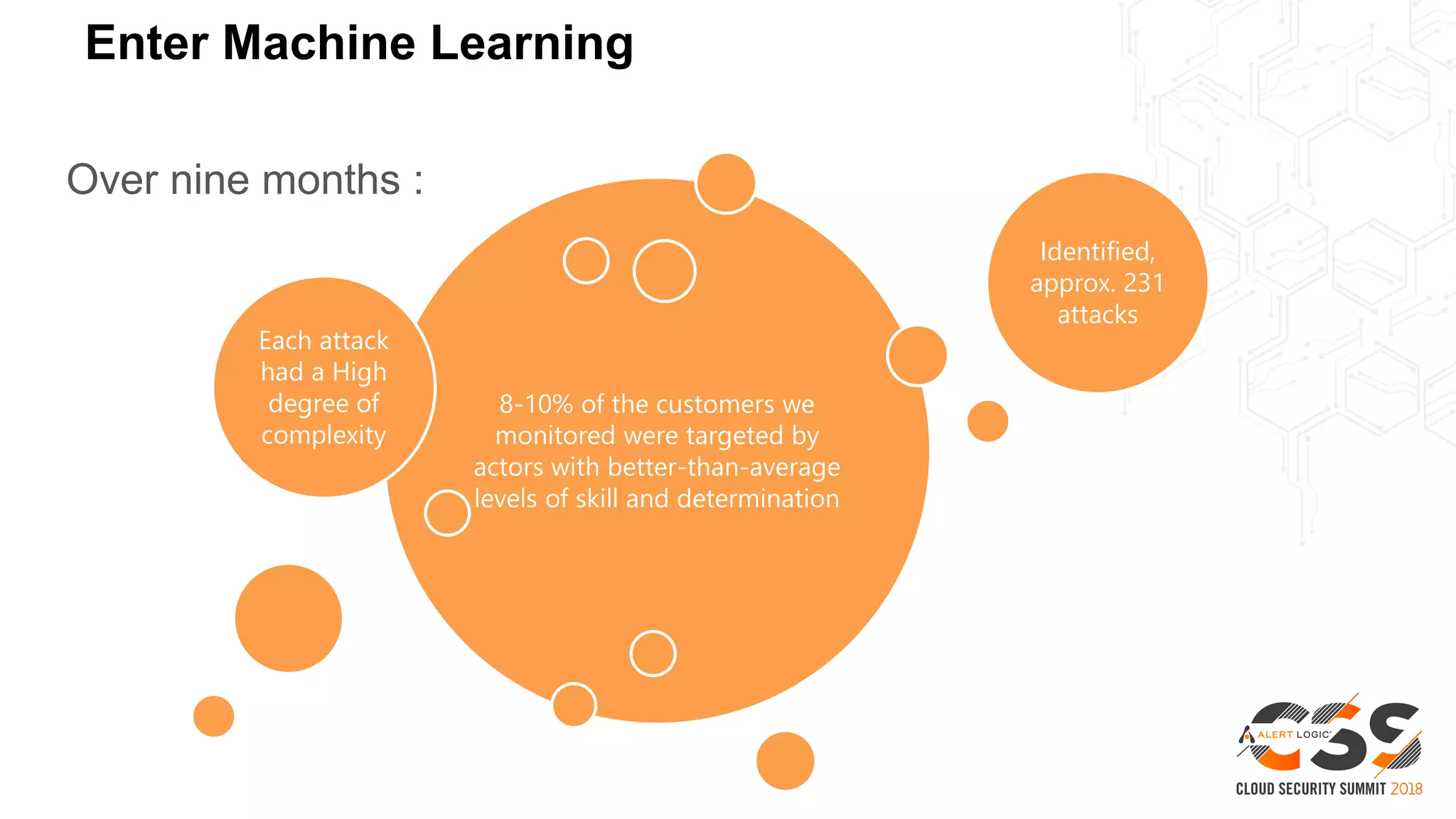
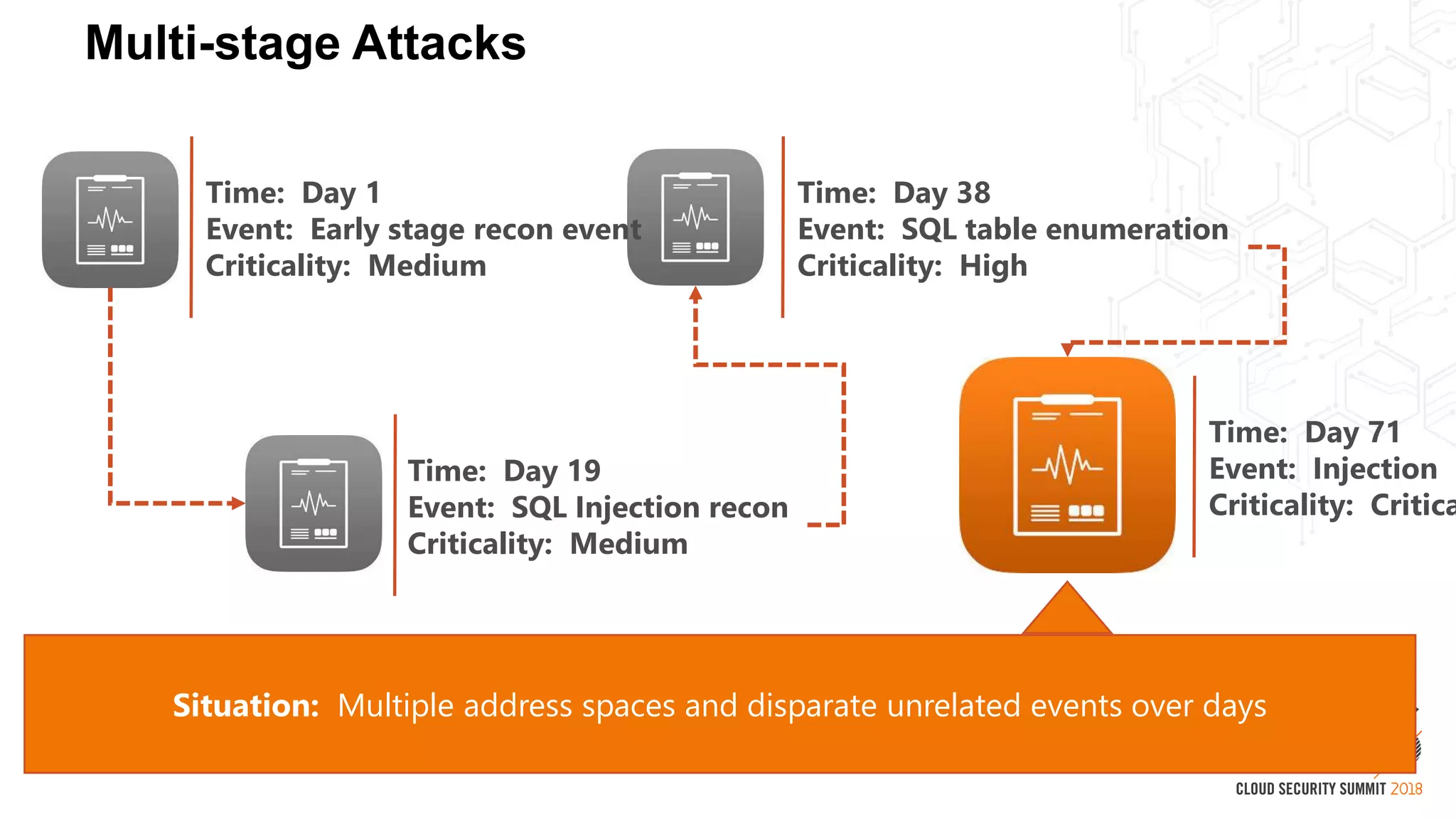
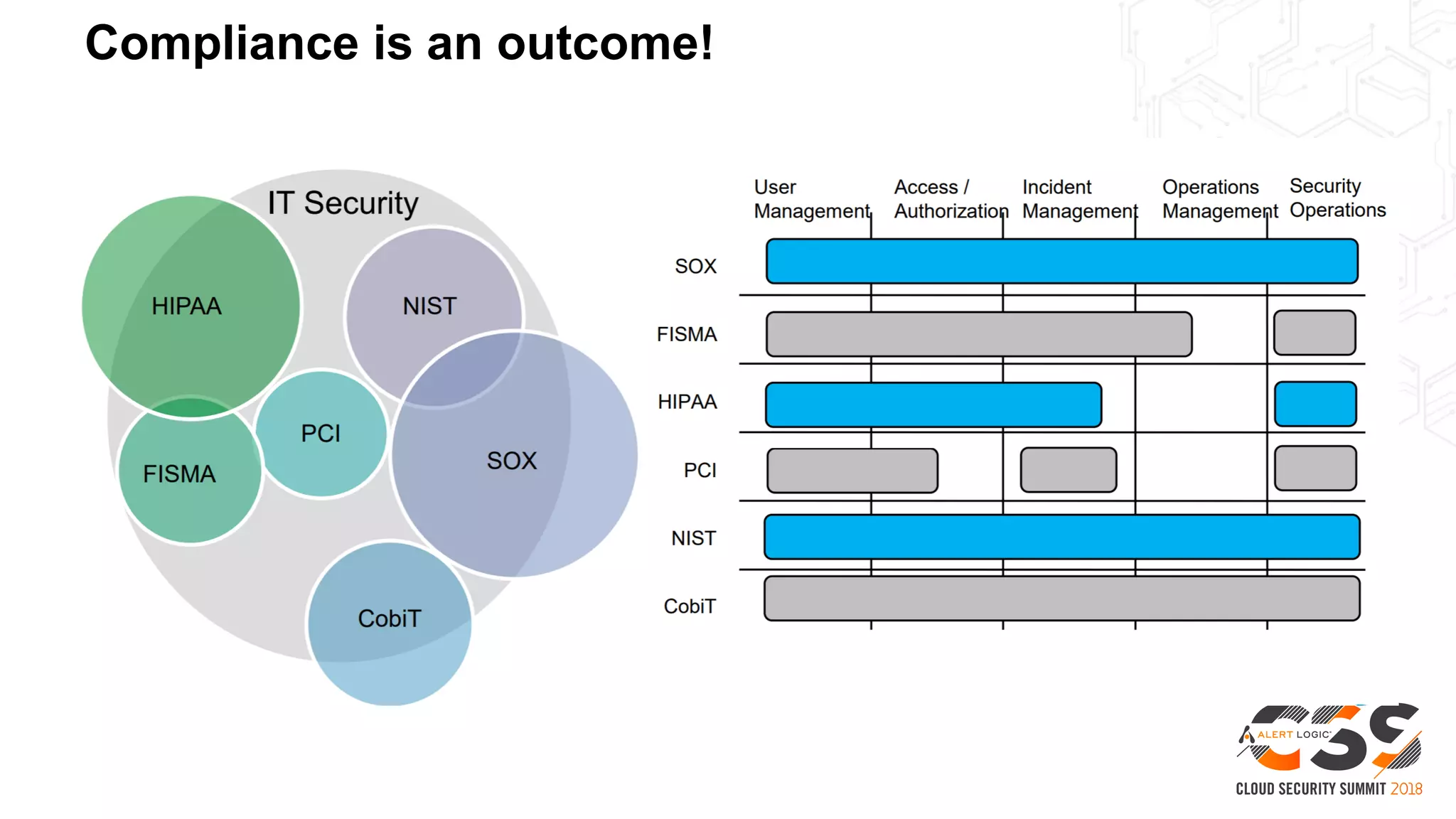
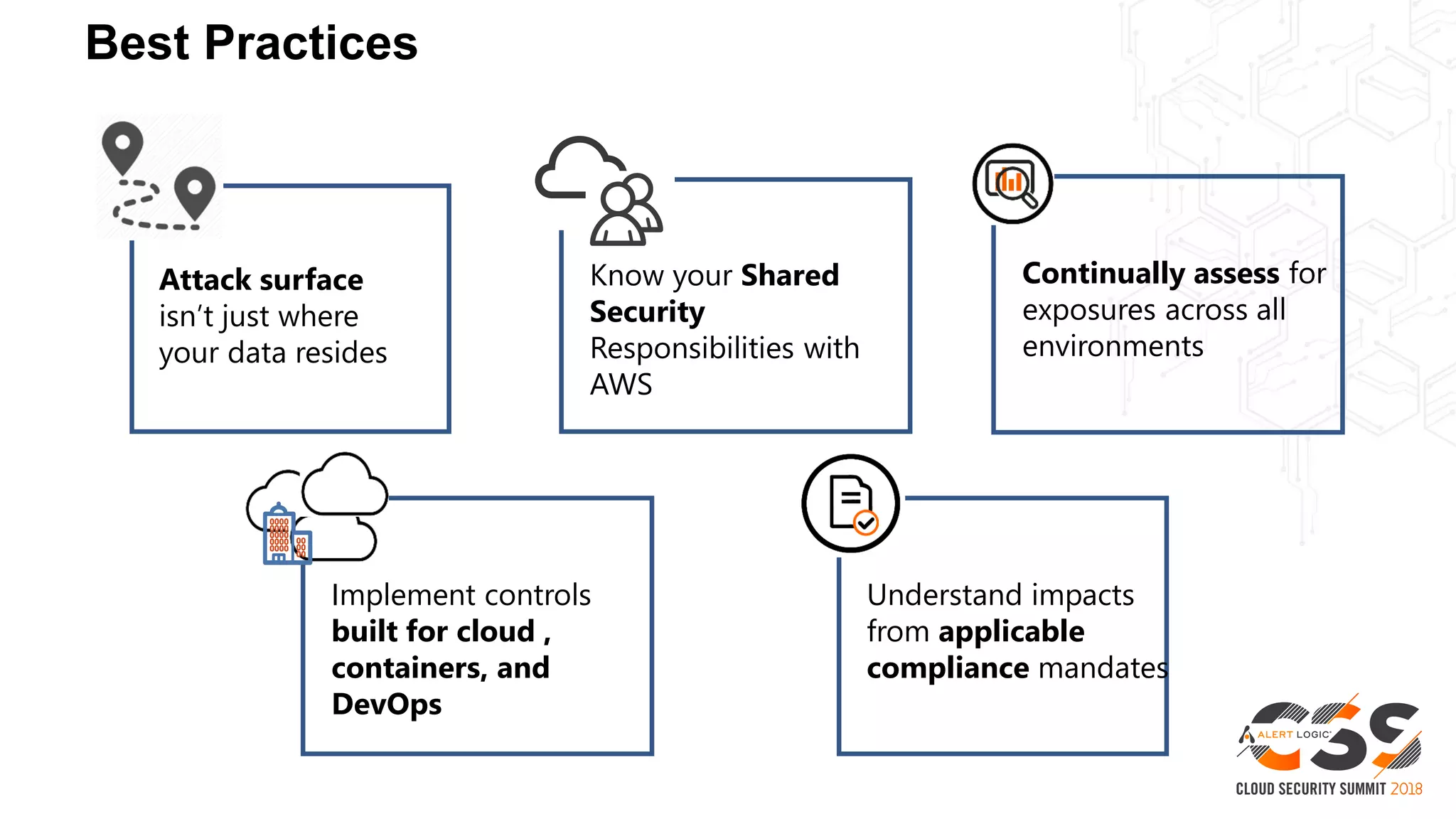
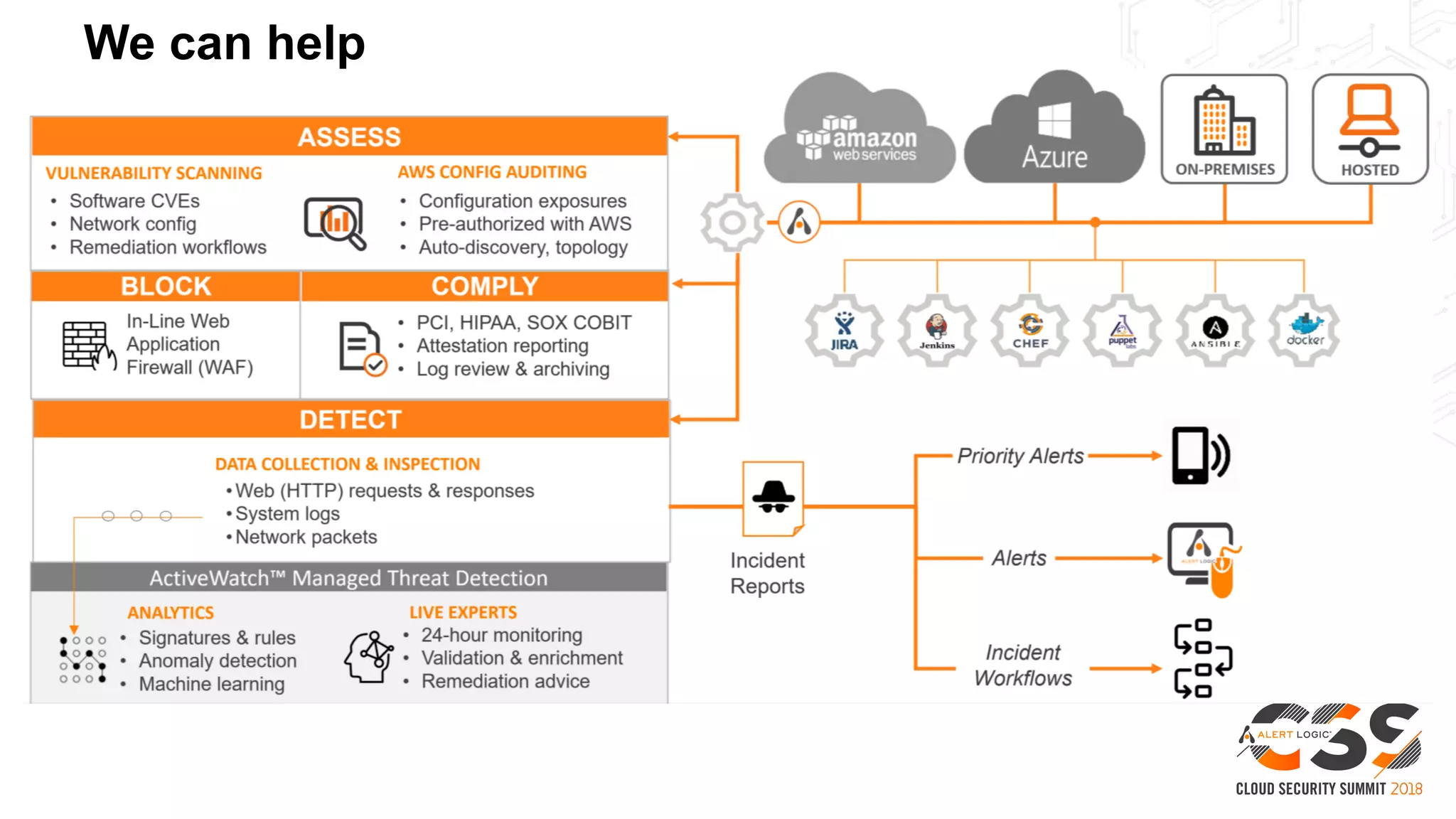
This document discusses security in the cloud and provides recommendations. It summarizes that while the cloud provides tools to enhance security, customers are still responsible for 95% of security failures due to human error. It then outlines some key findings: 1) customers must secure their entire attack surface, 2) vulnerabilities can emerge from an organization's code, configurations, and inherited issues, and 3) hybrid environments see more security incidents than public cloud alone. The document recommends that organizations find and fix vulnerabilities across their platforms, block known bad traffic, remain vigilant through monitoring, and achieve compliance as an outcome rather than a box-checking exercise. It positions Alert Logic as a partner that can help with these recommendations through anomaly detection, leveraging multiple detection