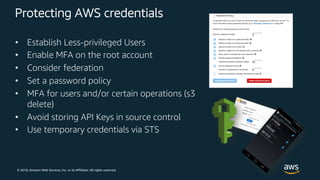
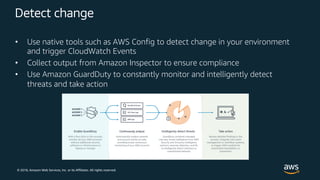
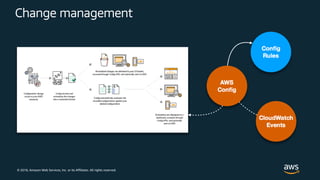
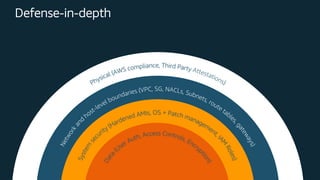
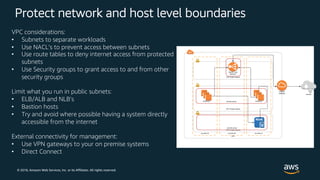
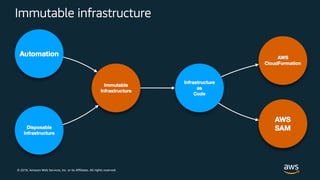
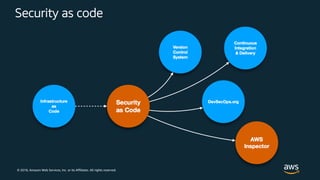
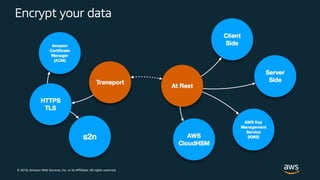
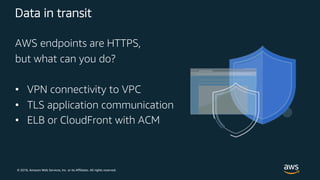
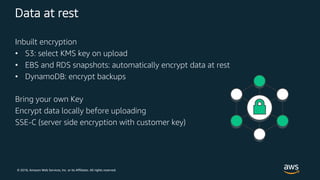
The document outlines key security principles and best practices for securing customer data in AWS, emphasizing the importance of implementing a strong identity foundation, enabling traceability, and protecting data in transit and at rest. It also highlights the need for detective controls, incident response plans, and automation of security measures, alongside the use of AWS services like IAM, CloudTrail, and others to manage access and monitor for threats. The document serves as a guideline for achieving a secure architecture while maintaining compliance and minimizing risk.