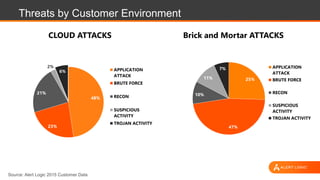
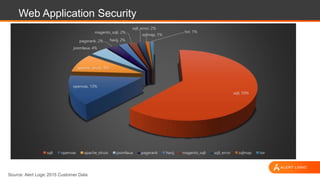
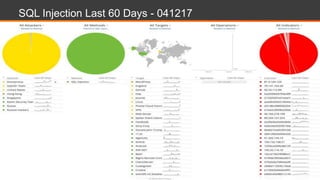
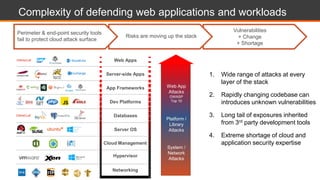
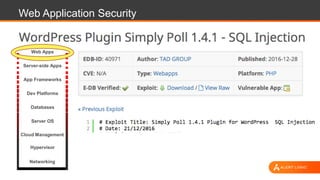
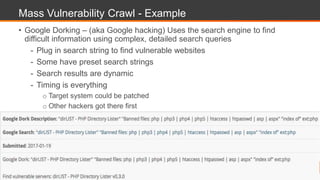
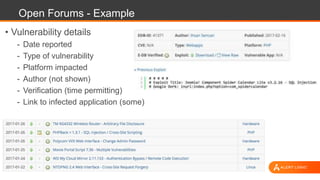
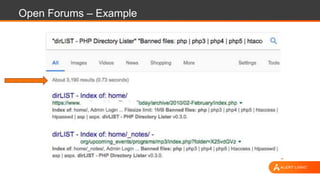
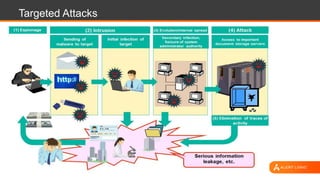
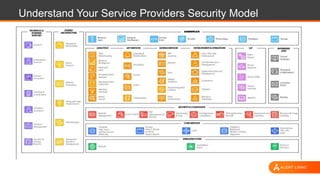
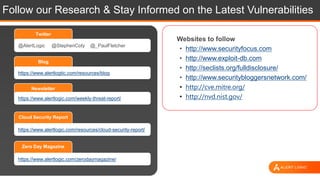
The document discusses web application security, highlighting the various types of attacks and vulnerabilities faced by web applications, particularly due to complexities and a shortage of expertise in cloud and application security. It lists several common attacks, emphasizes the importance of secure coding practices and access management, and suggests remediation strategies like regular patch management and monitoring for malicious activity. Additionally, it provides resources for staying informed about the latest threats and vulnerabilities.