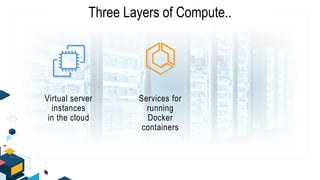
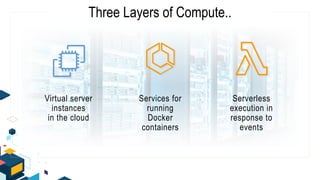
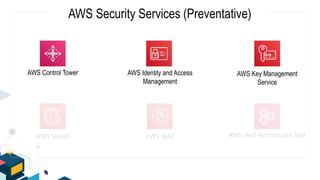
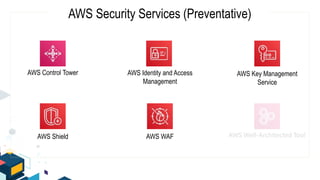
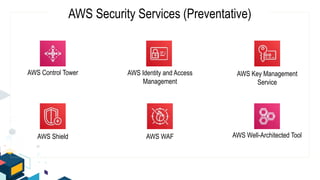
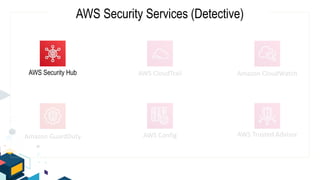
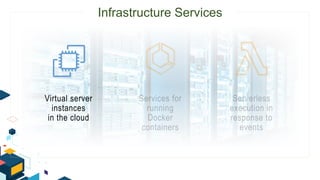
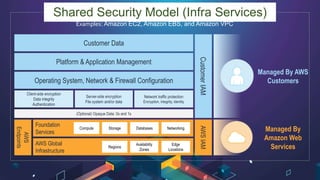
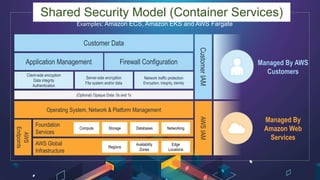
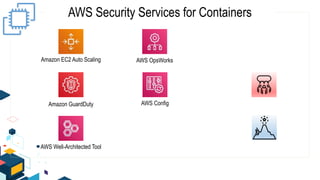
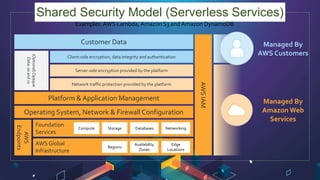
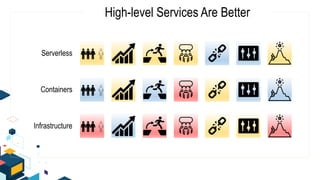
This document discusses AWS security best practices for the three layers of compute: virtual server instances, container services like ECS and EKS, and serverless services like Lambda. It outlines shared security responsibilities between AWS and customers for each layer and recommends AWS security services to use for infrastructure, containers, and serverless. These include IAM, GuardDuty, Config, and WAF as well as ensuring proper access controls, encryption, monitoring, and backups at the application layer.