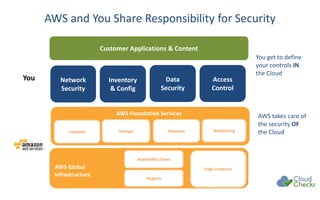
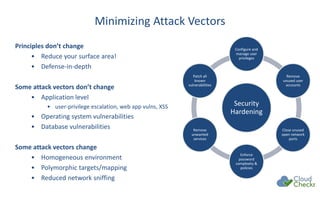
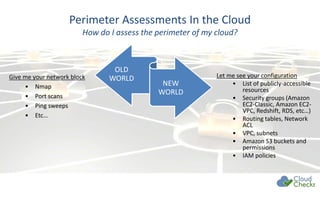
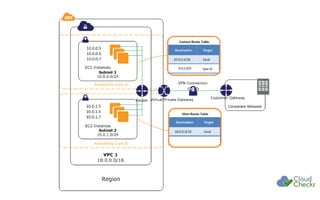
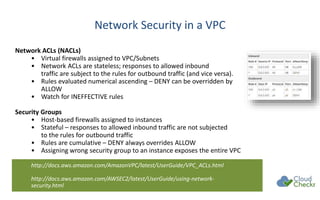
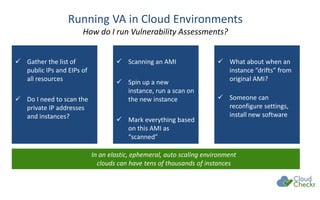
The document discusses strategies for securing cloud environments, particularly within AWS, emphasizing a shift from traditional perimeter security to managing cloud workloads. It highlights the importance of adapting security practices for ephemeral infrastructure, IAM access, and conducting continuous vulnerability assessments and patching. The document also introduces cloud management tools like CloudCheckr for monitoring security, availability, and cost in AWS deployments.








![SQS (Simple Queuing Service)
Where does SQS live?
• Within a region, not within a VPC
• Uses a URL such as:
https://sqs.us-east-1.amazonaws.com/123456789012/MySQS
Security based on policy documents:
{
"Version": "2008-10-17",
"Id": "arn:aws:sqs:us-east-1:123456789012:MySQS/SQSDefaultPolicy",
"Statement": [
{
"Sid": "Sid1415217272568",
"Effect": "Allow", "Principal": { "AWS": "*" },
"Action": [
"SQS:ReceiveMessage", "SQS:SendMessage"
],
"Resource": "arn:aws:sqs:us-east-1:123456789012:MySQS"
},](https://image.slidesharecdn.com/hackproofyourawscloudcloudcheckr040416-160408204604/85/Hack-proof-your-aws-cloud-cloudcheckr_040416-17-320.jpg)