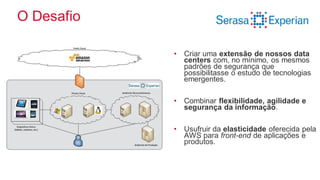
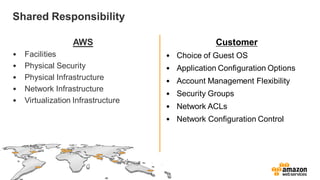
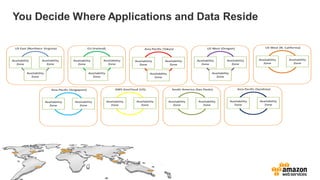
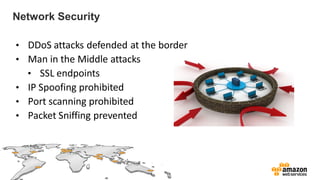
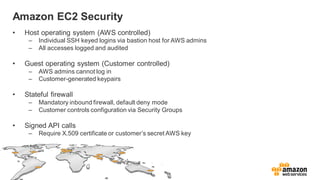
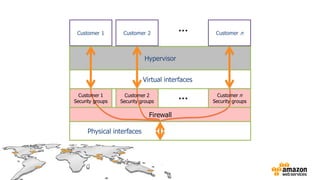
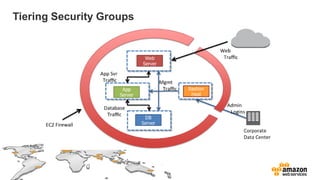
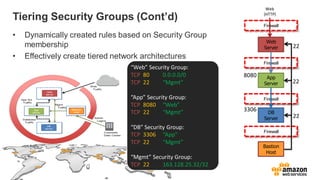
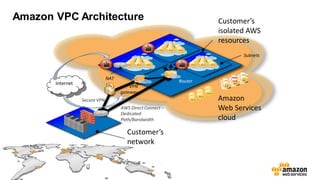
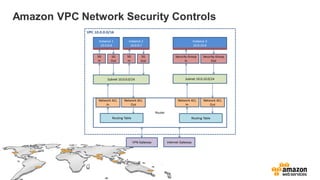
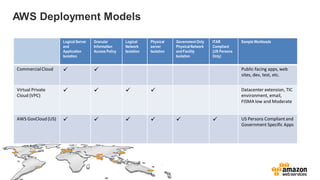
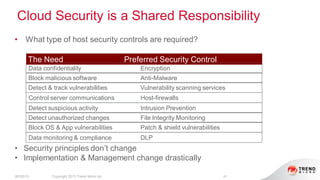
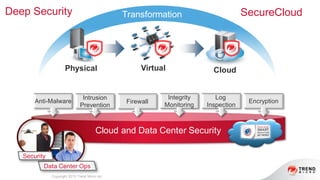
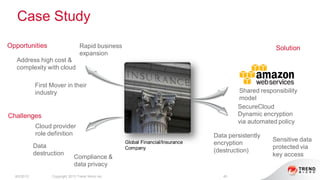
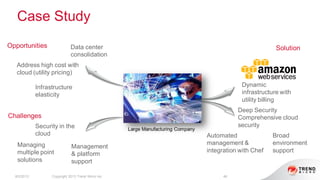
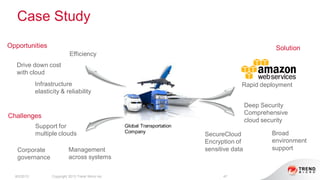
The document provides an overview of AWS security presented by Max Ramsay. It discusses AWS security capabilities that are available to all customers regardless of business type. It focuses on case studies of how Serasa Experian and Trend Micro use AWS, highlighting benefits like agility, flexibility and cost reduction. The document also covers shared security responsibilities on AWS, compliance controls, network security features, and resources for learning more about AWS security best practices.