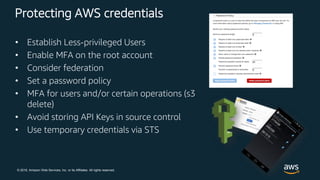
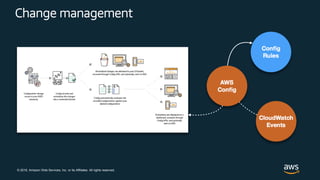
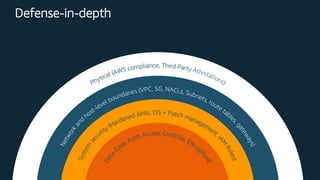
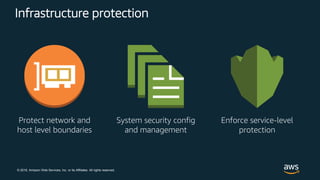
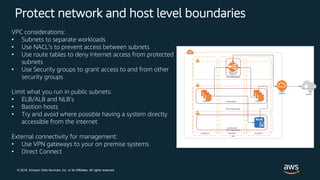
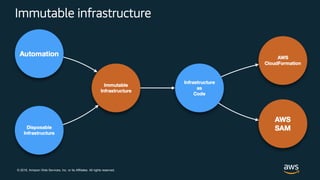
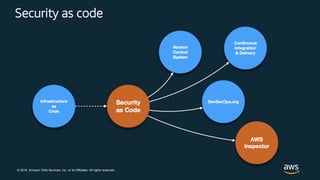
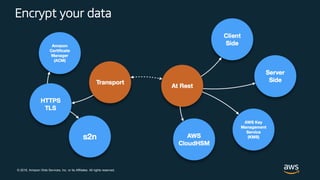
This document discusses best practices for securing customer data on AWS from day one, including implementing strong identity and access management, enabling traceability, applying security at all layers, automating security best practices, protecting data in transit and at rest, and preparing for security events. It provides guidance on setting up authentication and authorization controls with IAM, implementing detective controls with logging and monitoring tools, applying defense-in-depth with network and host security configurations, automating security configurations with tools like CloudFormation, encrypting data at rest and in transit, and planning incident response procedures.