- Understanding your attack surface is critical to deploying the right security controls. The attack surface in cloud environments differs significantly from on-premises environments.
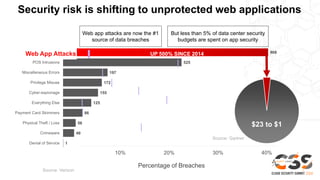
- Web application attacks are now the leading cause of data breaches. However, less than 5% of data center security budgets are spent on application security.
- Common cloud misconfigurations expose organizations to attacks. The most frequent misconfigurations relate to EC2 instances, S3 object storage, and IAM user policies.