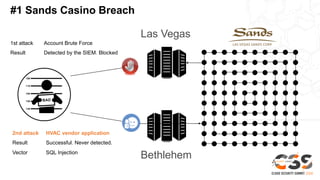
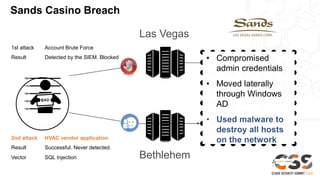
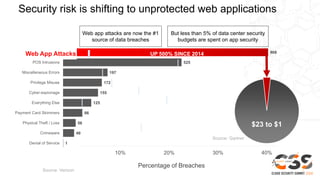
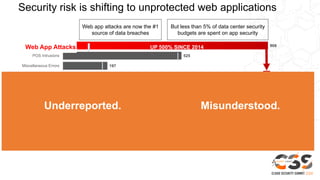
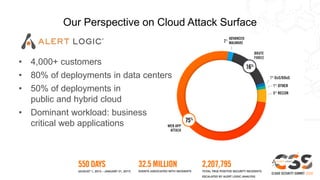
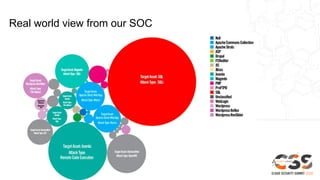
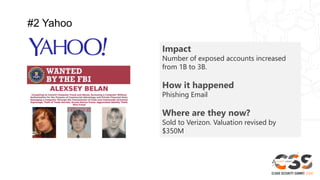
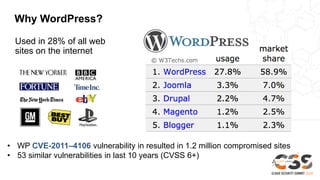
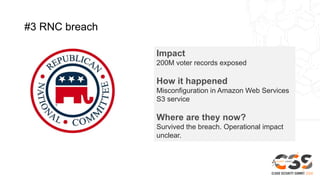
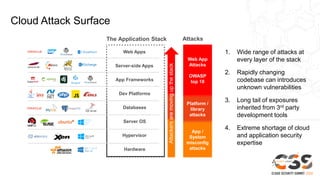
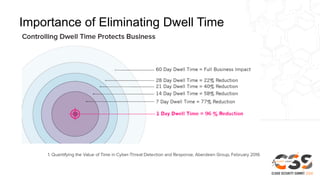
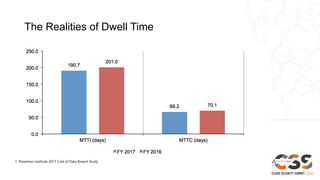
The document discusses reducing attack surfaces in cloud environments. It notes that understanding your attack surface is critical for deploying proper security controls as attack surfaces differ between cloud and on-premises environments. It also states that web application attacks are now the leading cause of data breaches but less than 5% of security budgets are spent on application security. Common cloud misconfigurations are also discussed as a major risk factor.