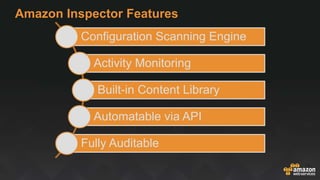
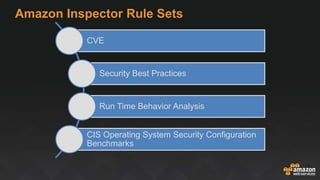
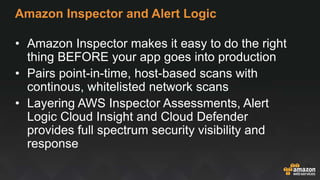
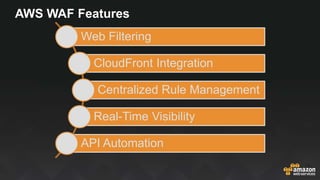
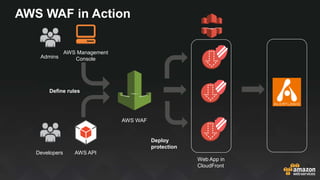
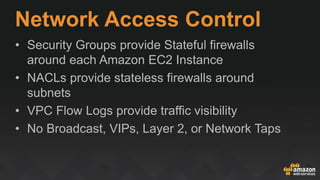
The document provides an overview of AWS security services, including network security primitives such as security groups and network access control lists (NACLs). It emphasizes the importance of continuous monitoring and vulnerability management through tools like Amazon Inspector and AWS WAF. Additionally, it discusses AWS Config rules for configuration changes and compliance, highlighting integration with remediation tasks and other platforms like Jira.




![The easy (Vulnerabilities) matter
"[With] any large network, I will tell you that
persistence and focus will get you in, we'll achieve that
exploitation without the zero days," he says. "There's
so many more vectors that are easier, less risky and
quite often more productive that going down that
route." This includes, of course, known vulnerabilities
for which a patch is available but the owner hasn't
installed it.
- Rob Joyce NSA TAO @ Enigma 2016](https://image.slidesharecdn.com/patryansecurity-presentation-al-cssawspr-final2-160613201416/85/ALSummit-Alert-Logic-AWS-AWS-Security-Services-6-320.jpg)