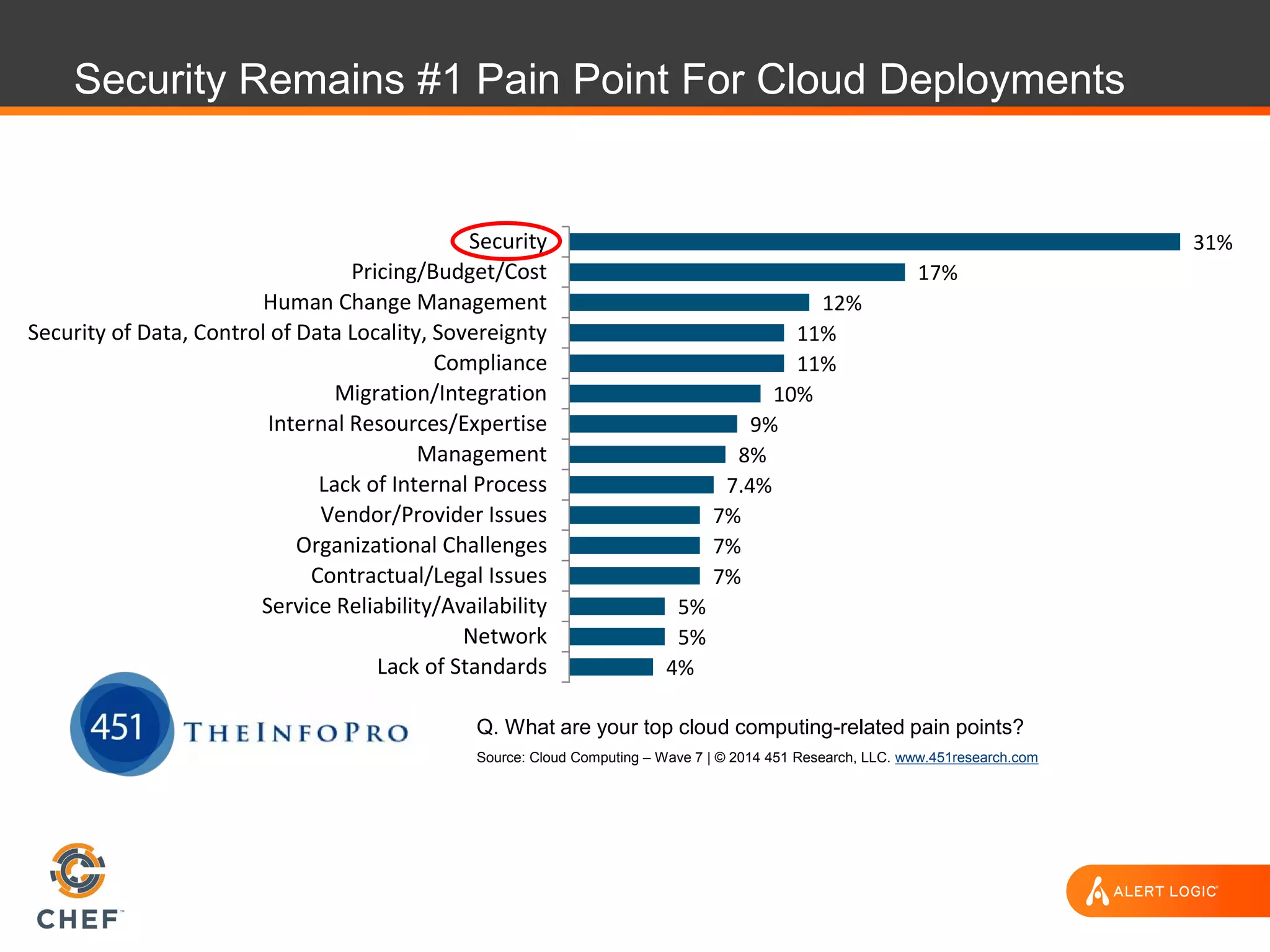
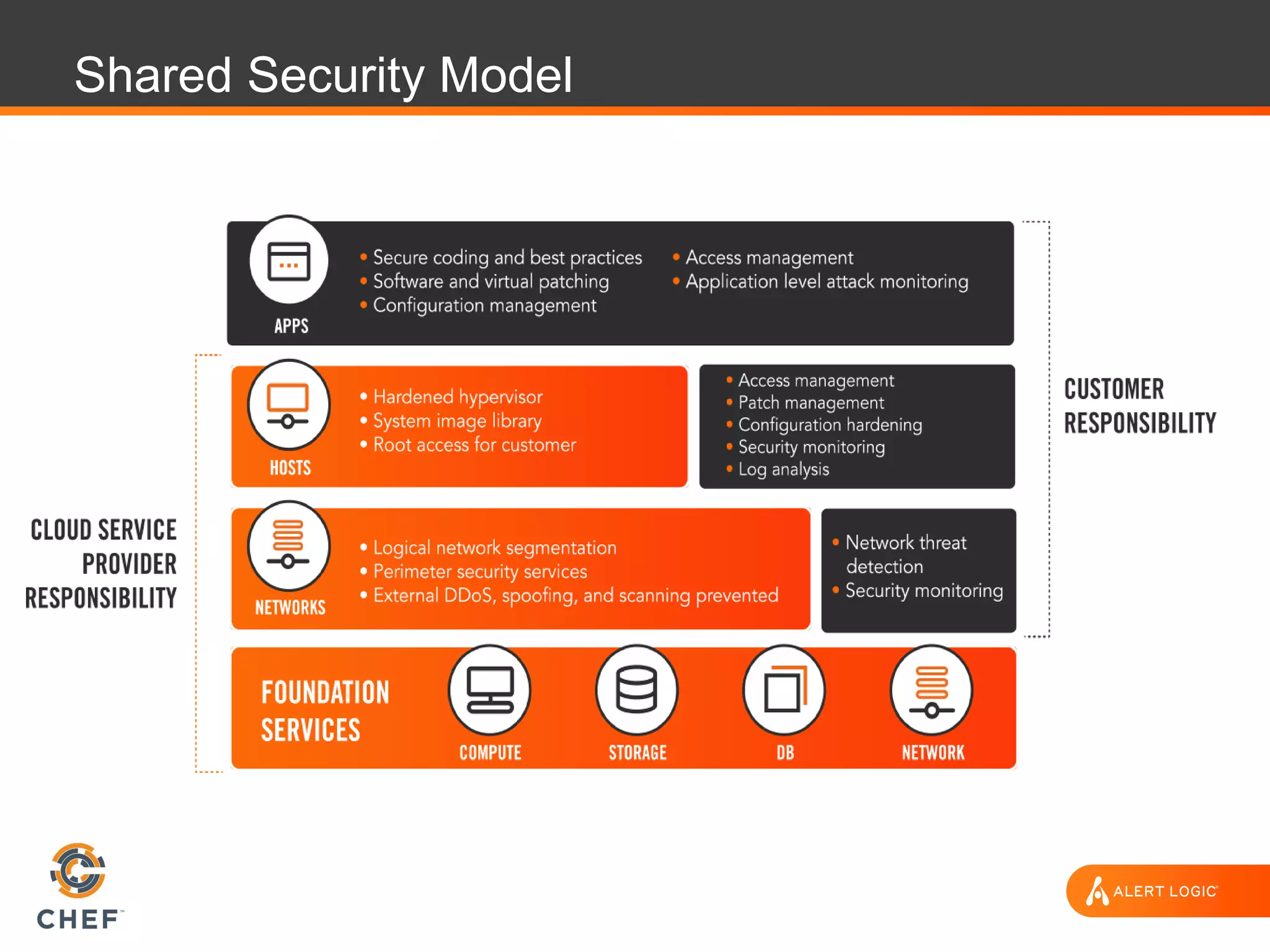
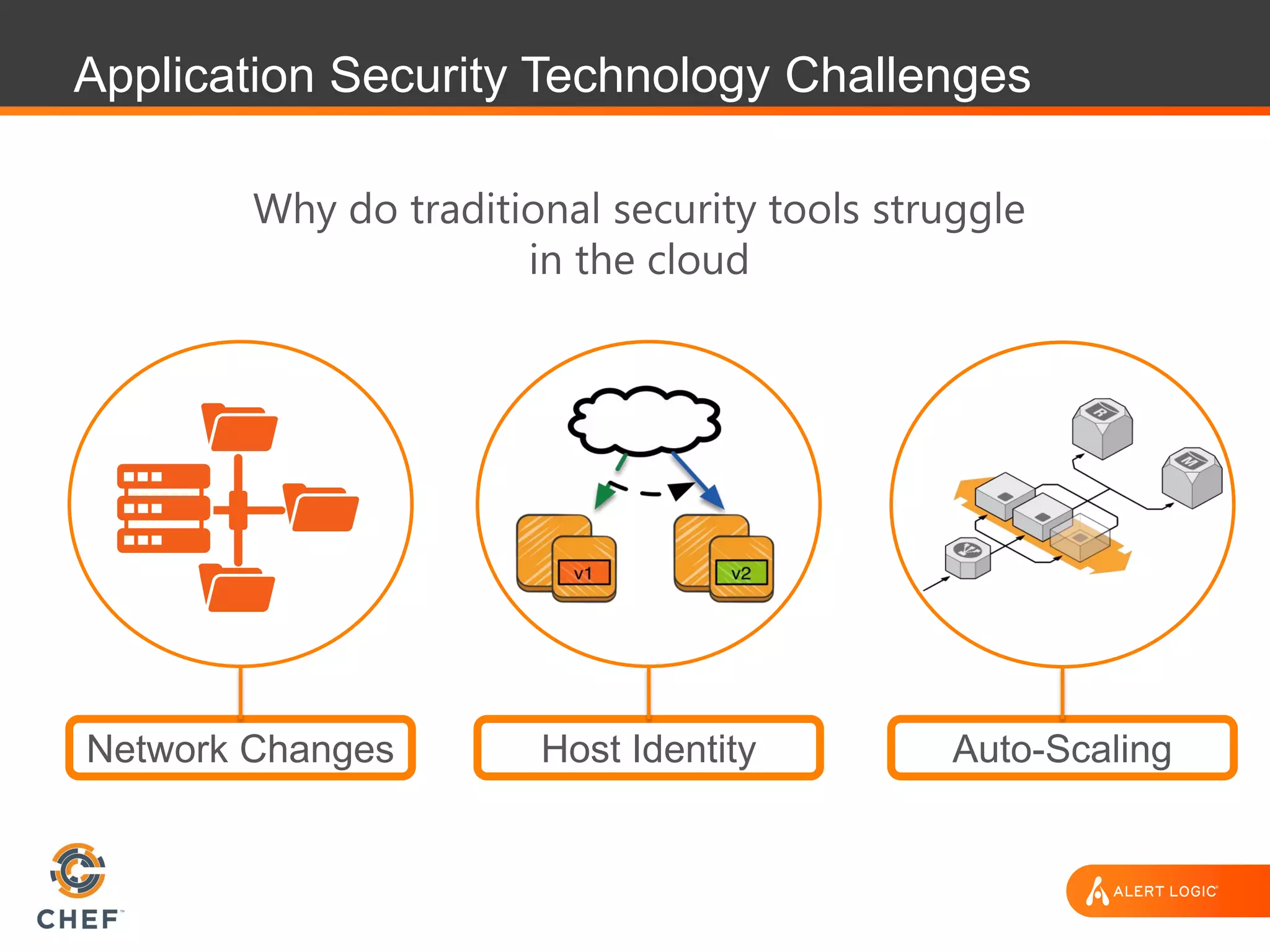
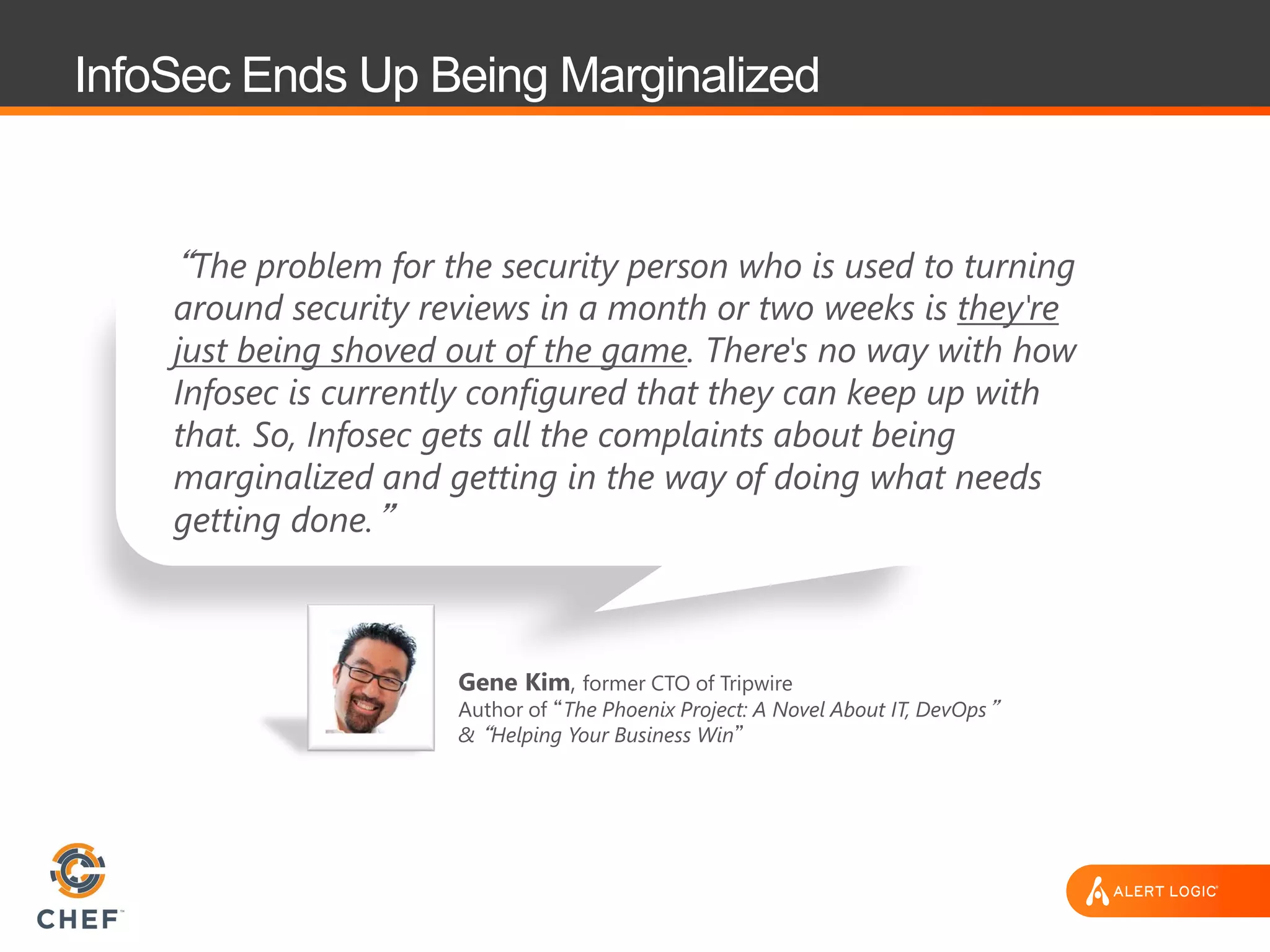
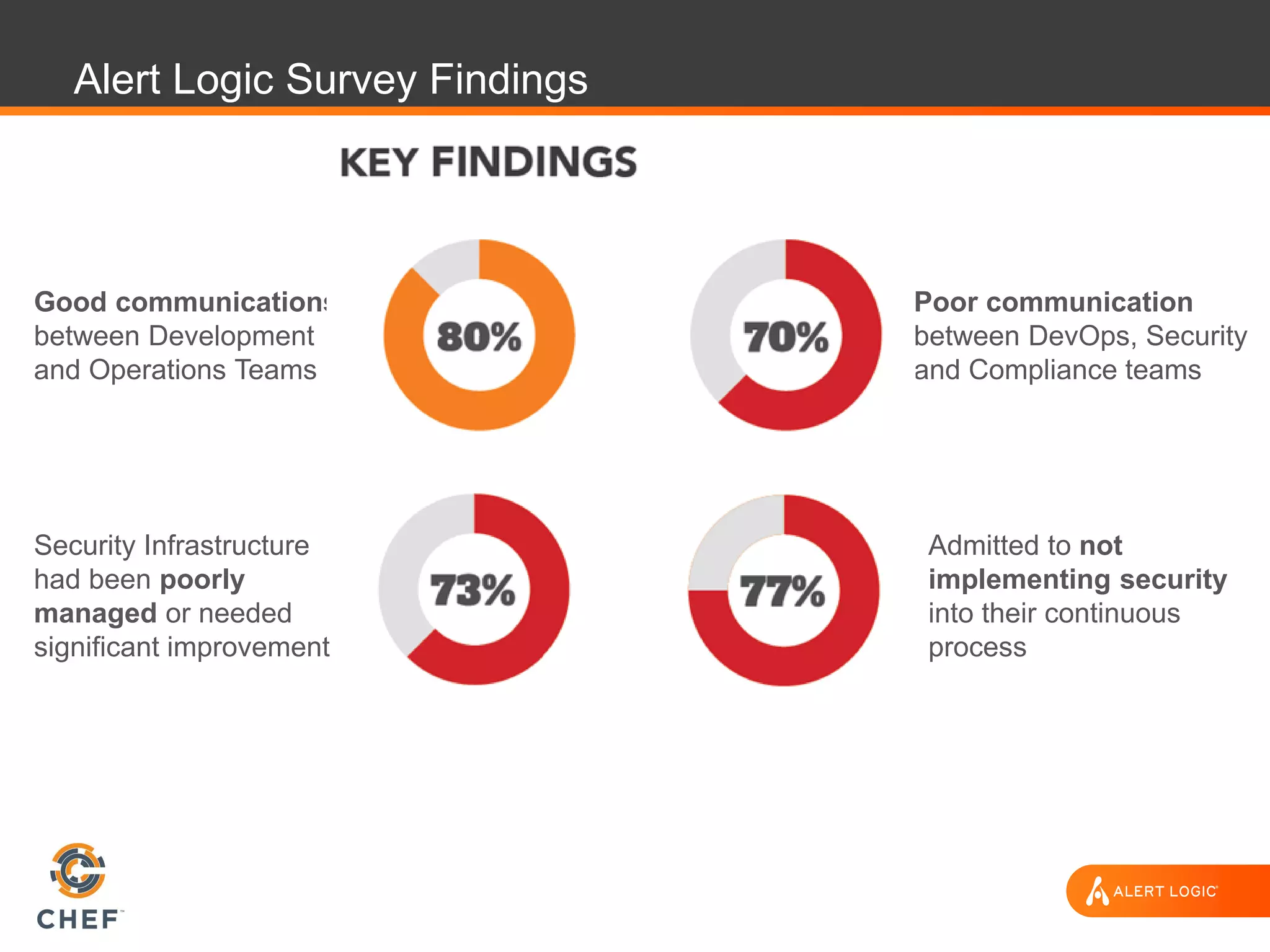
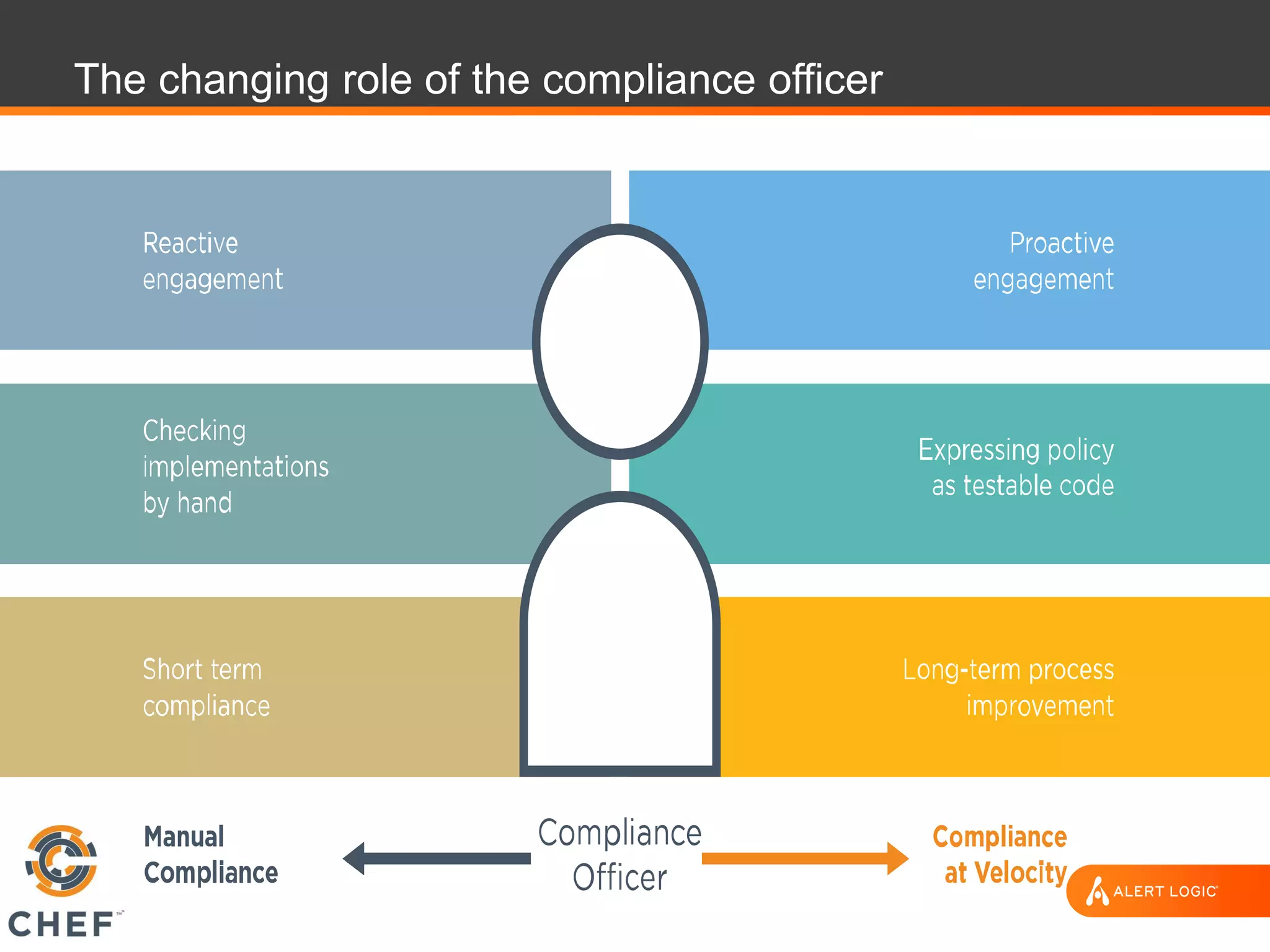
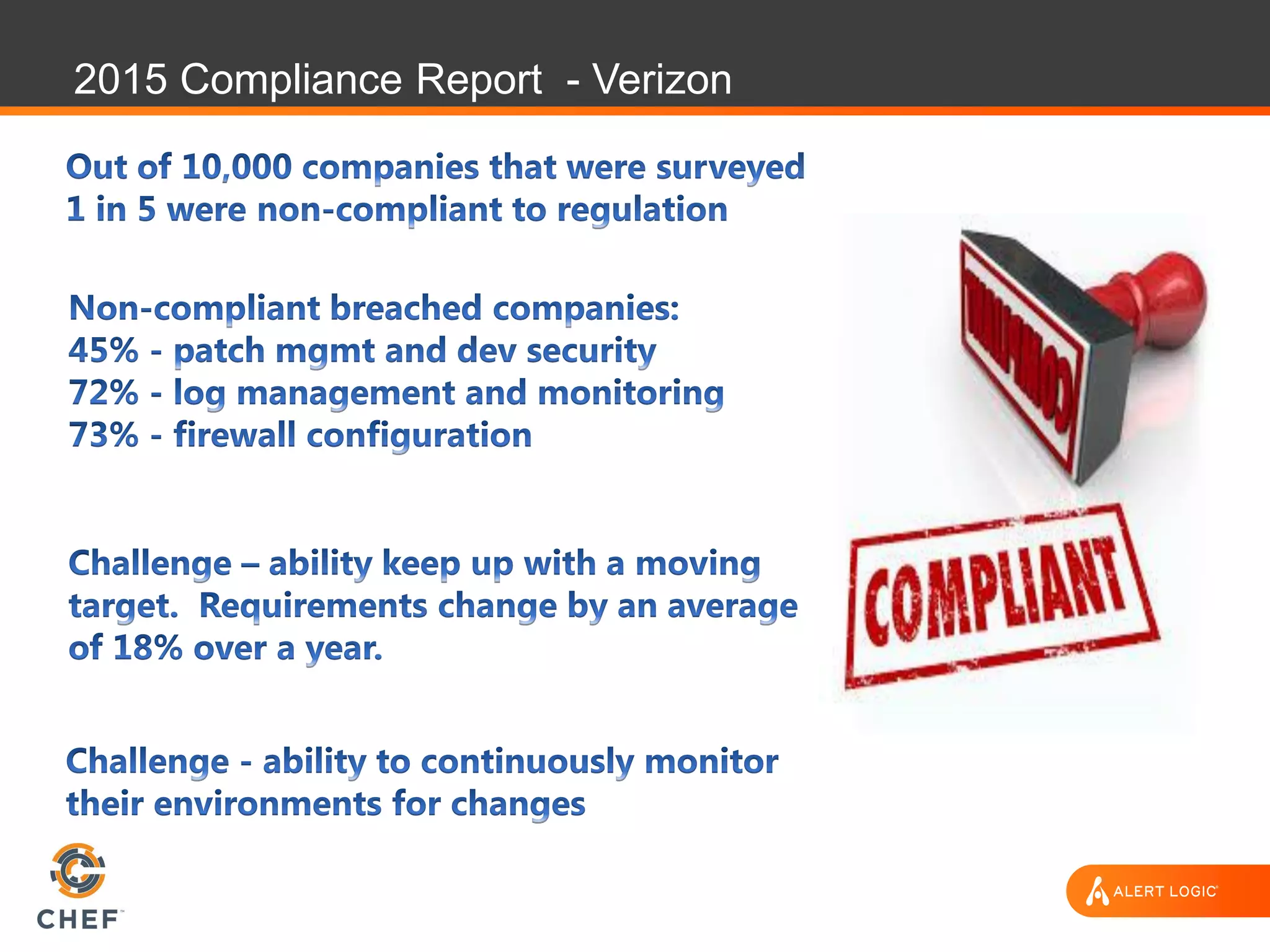
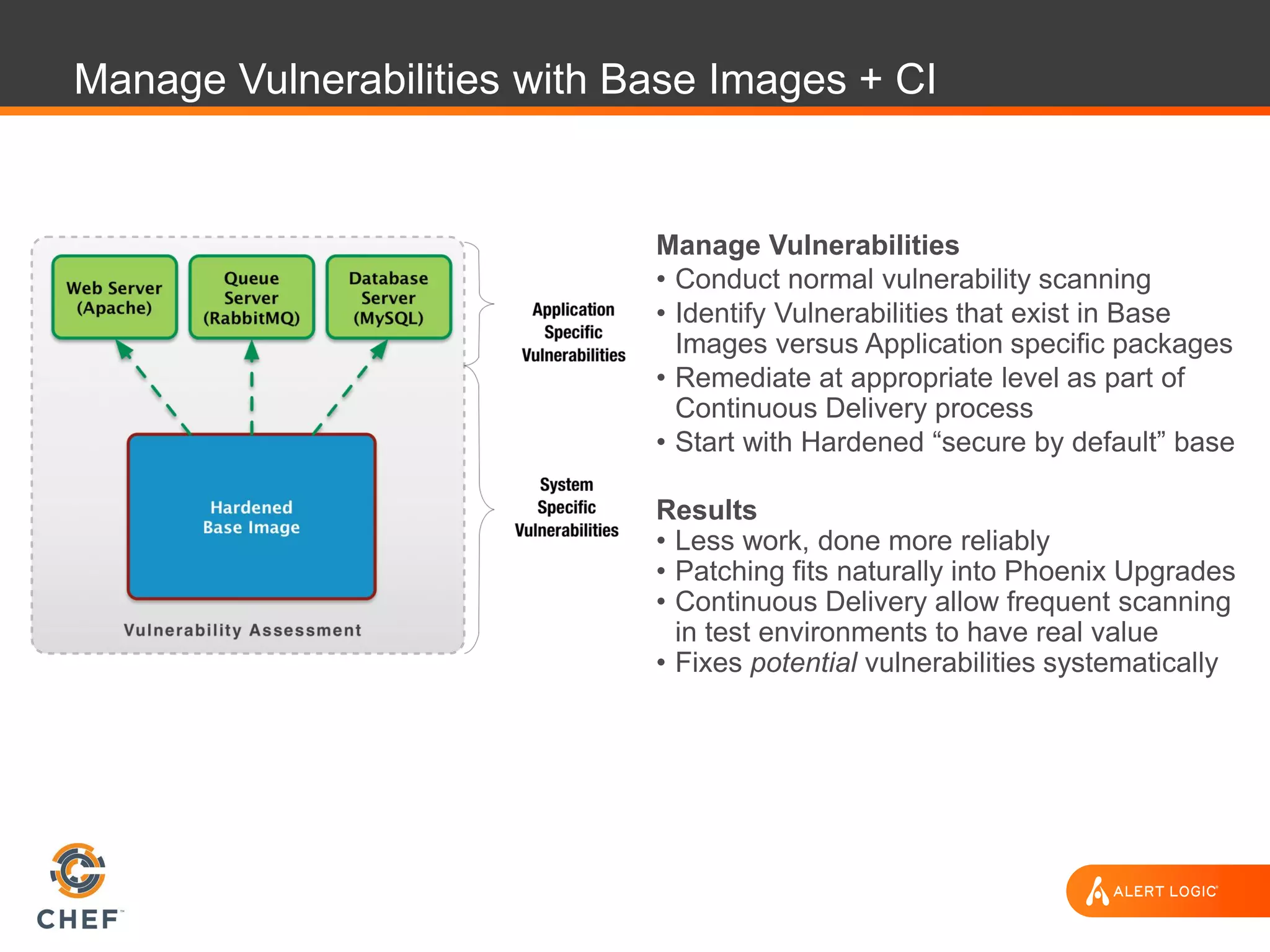
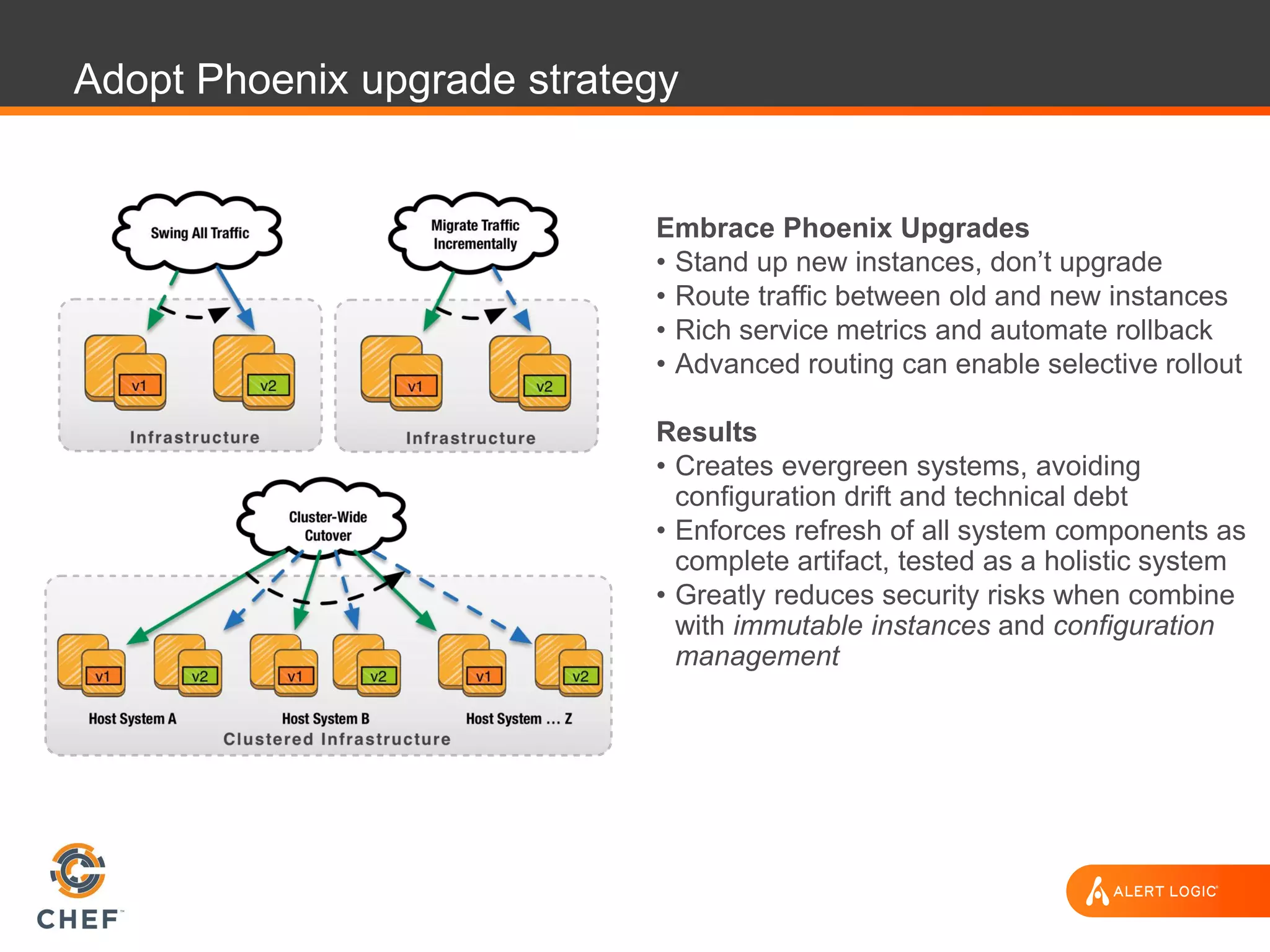
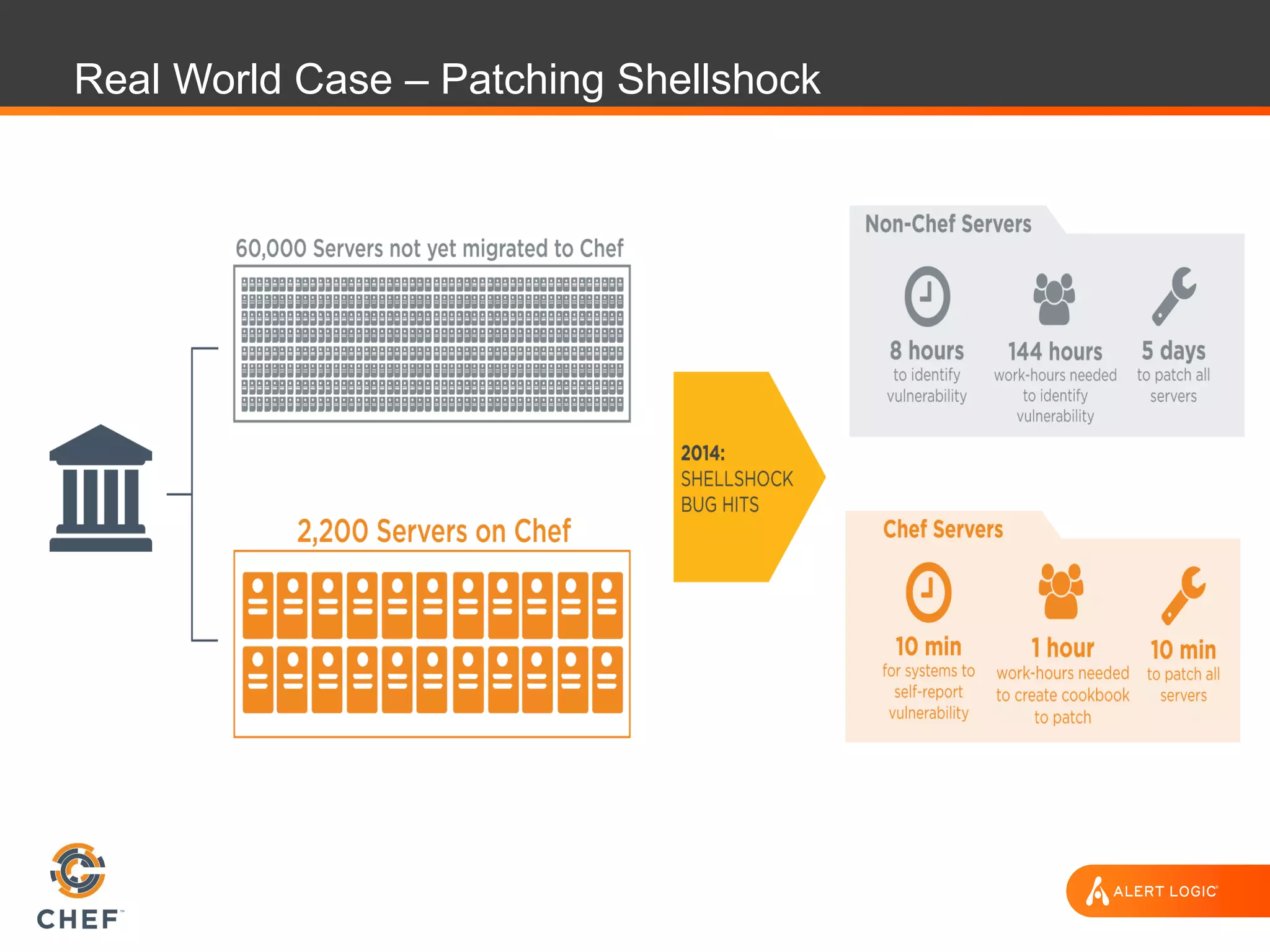
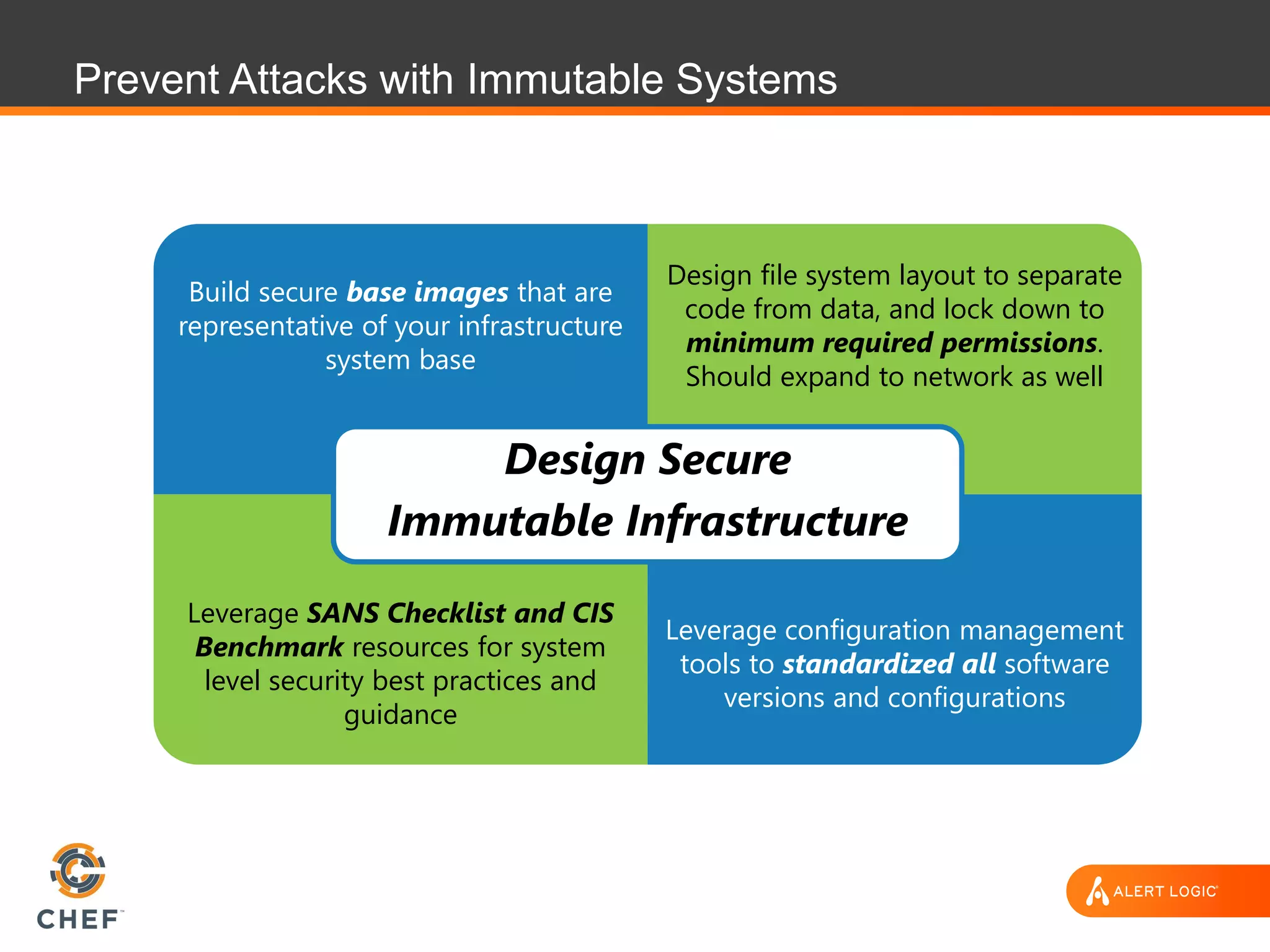
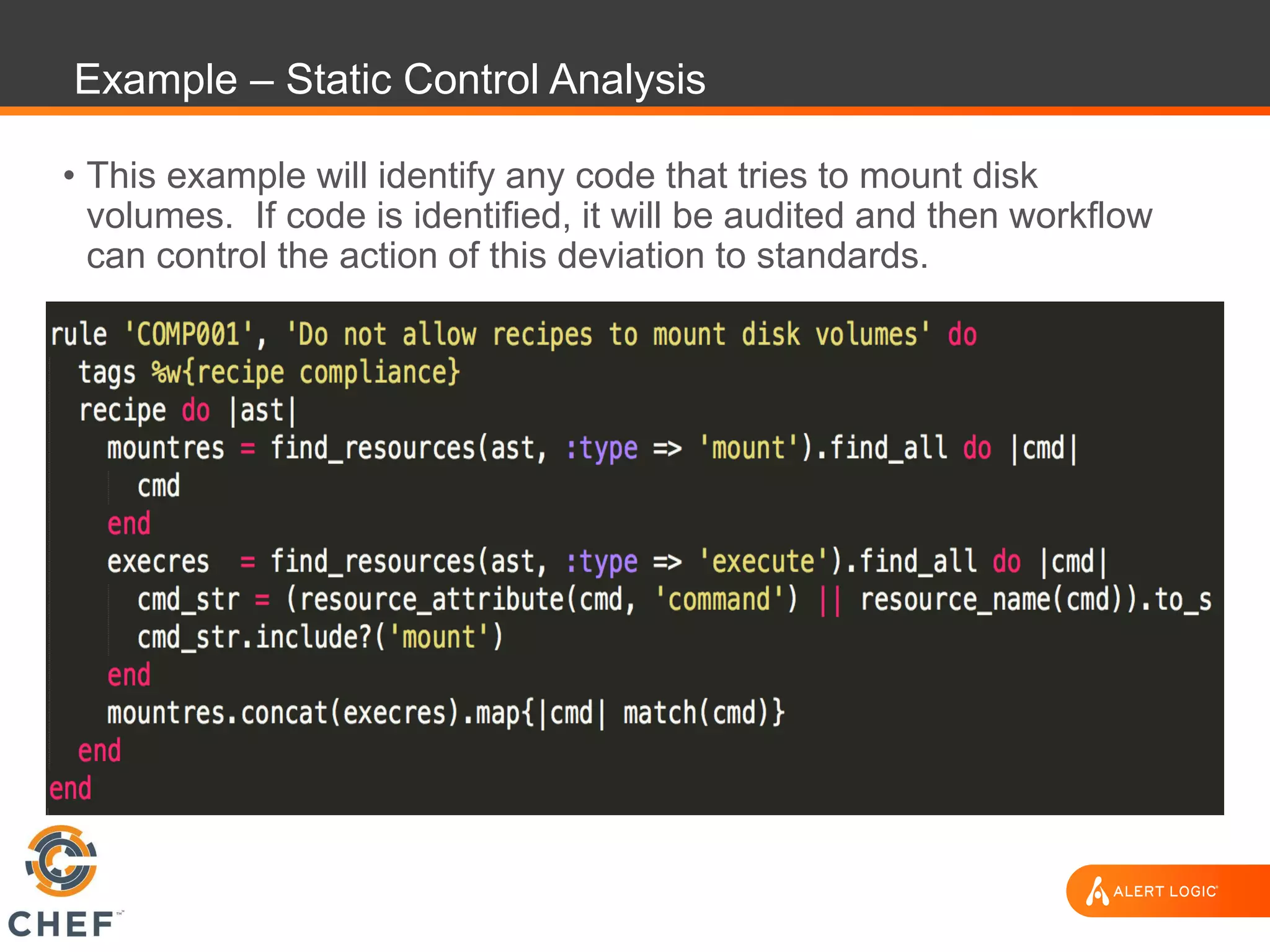
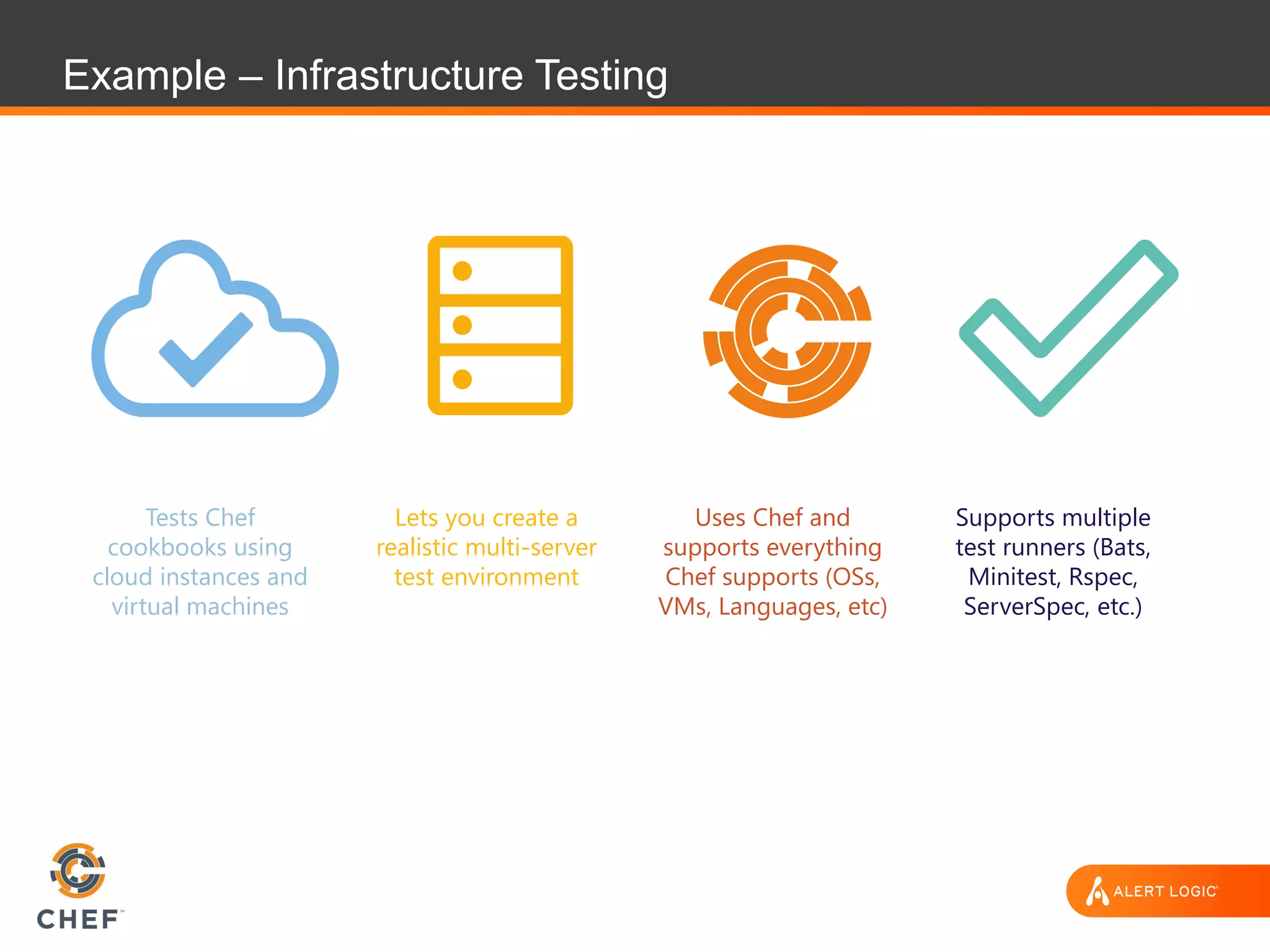
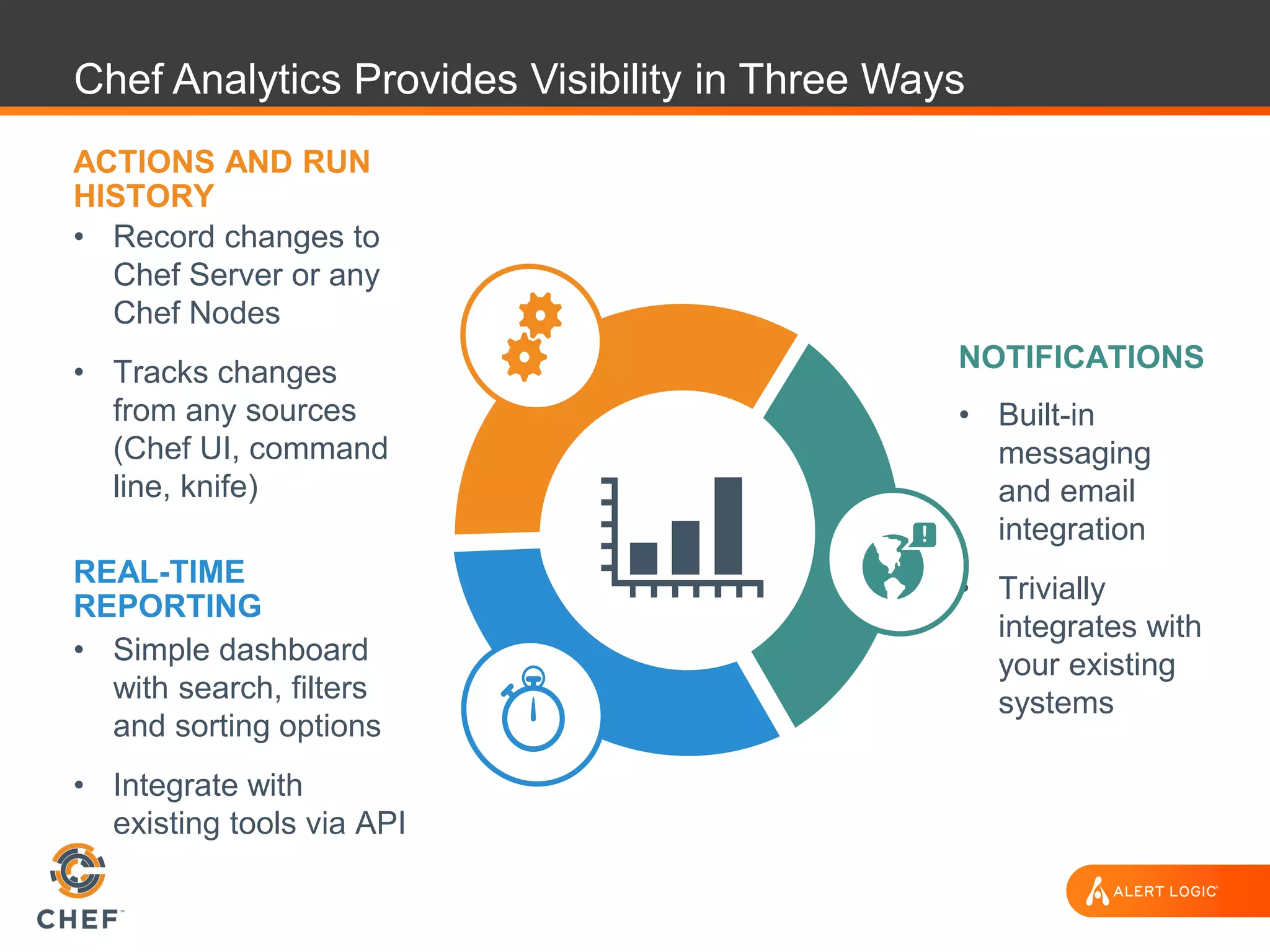
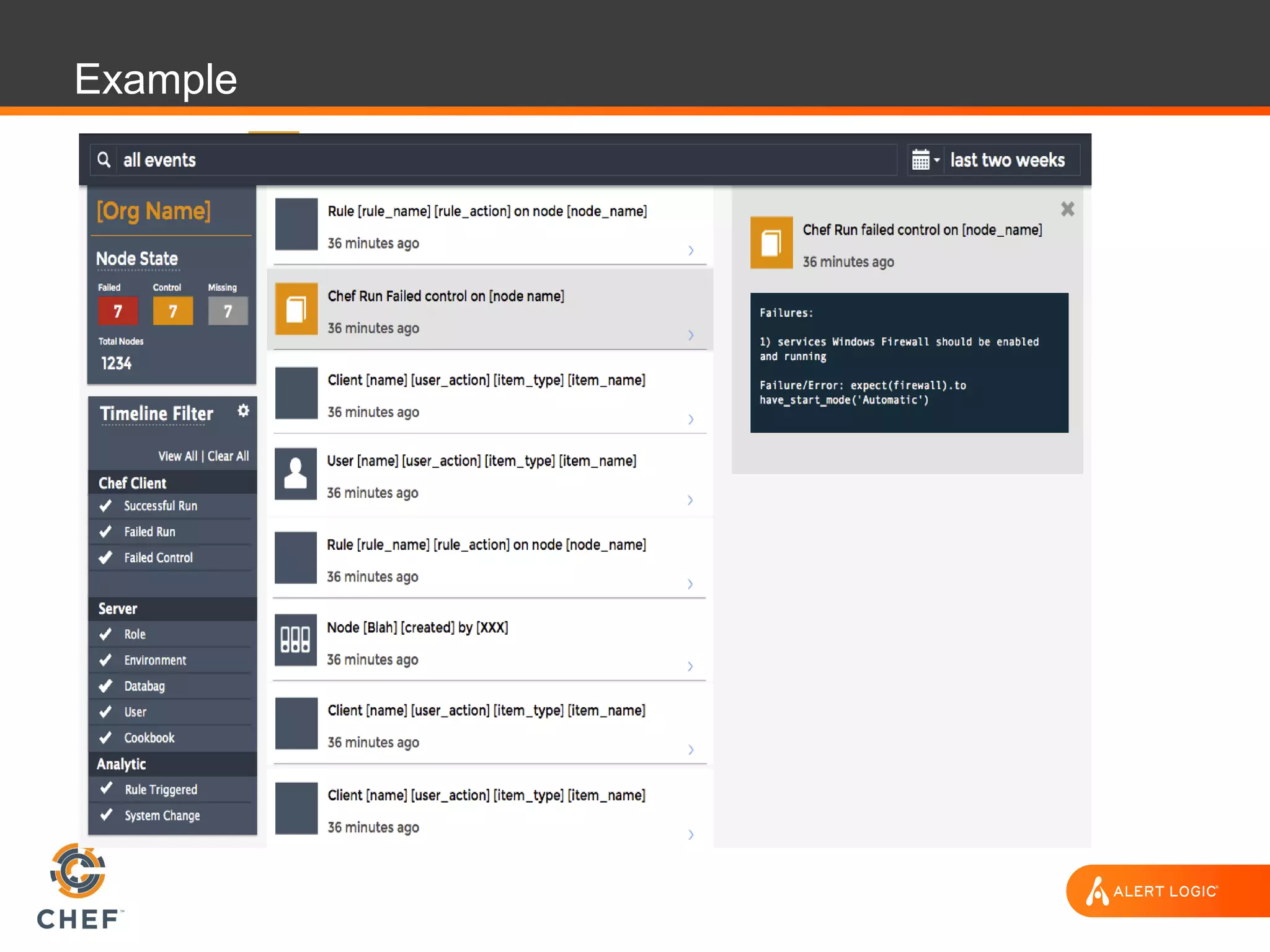
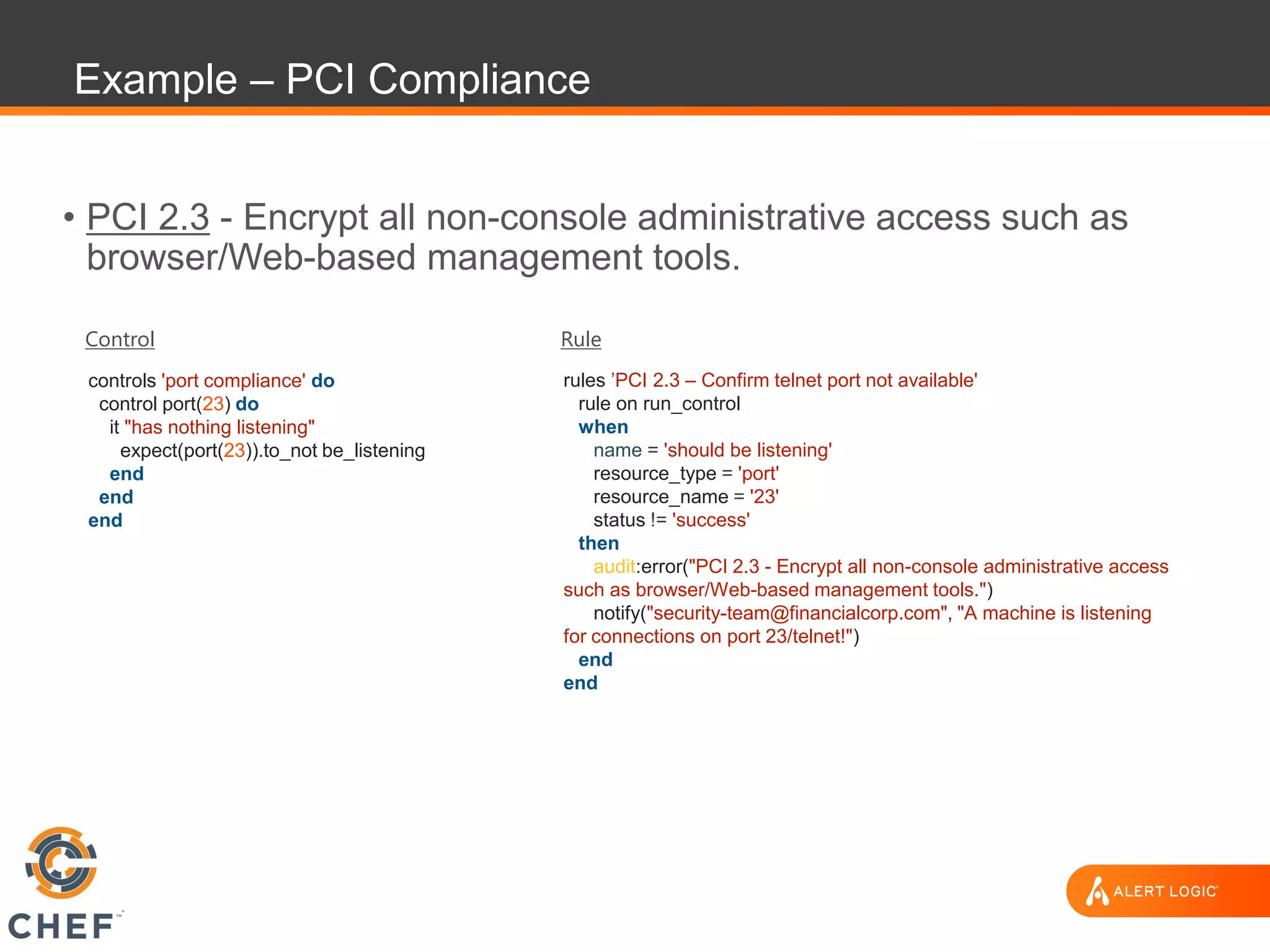
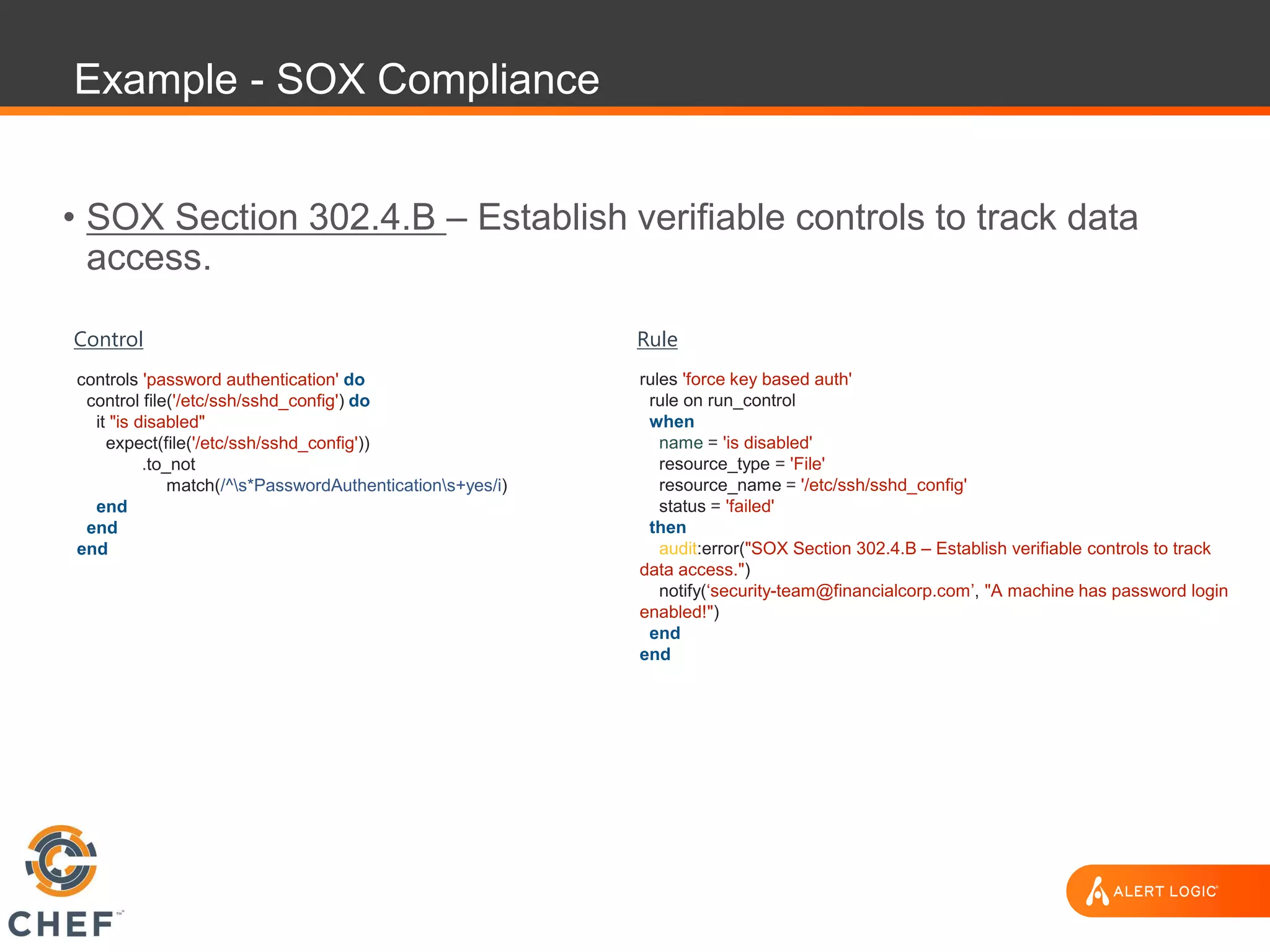
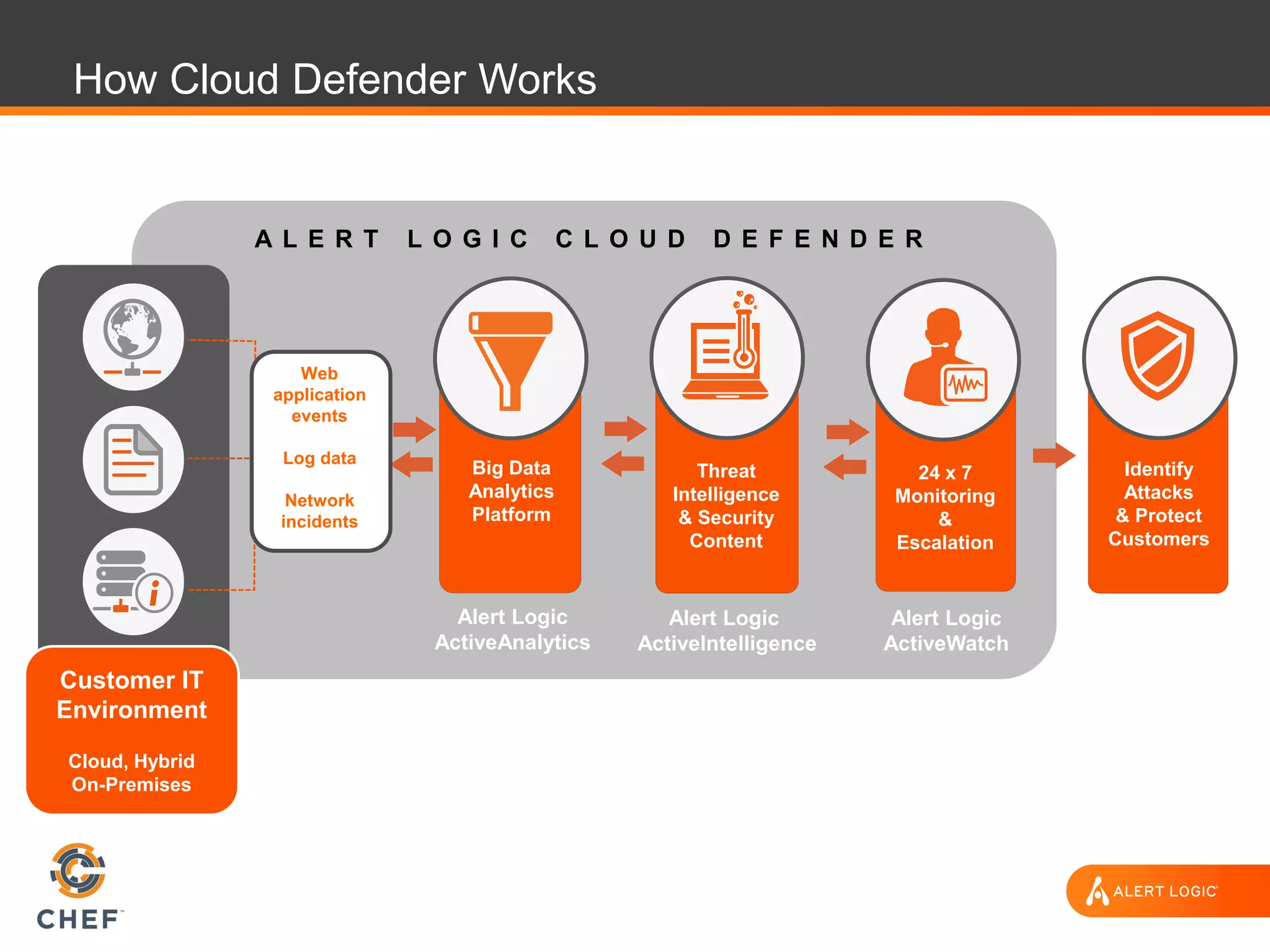
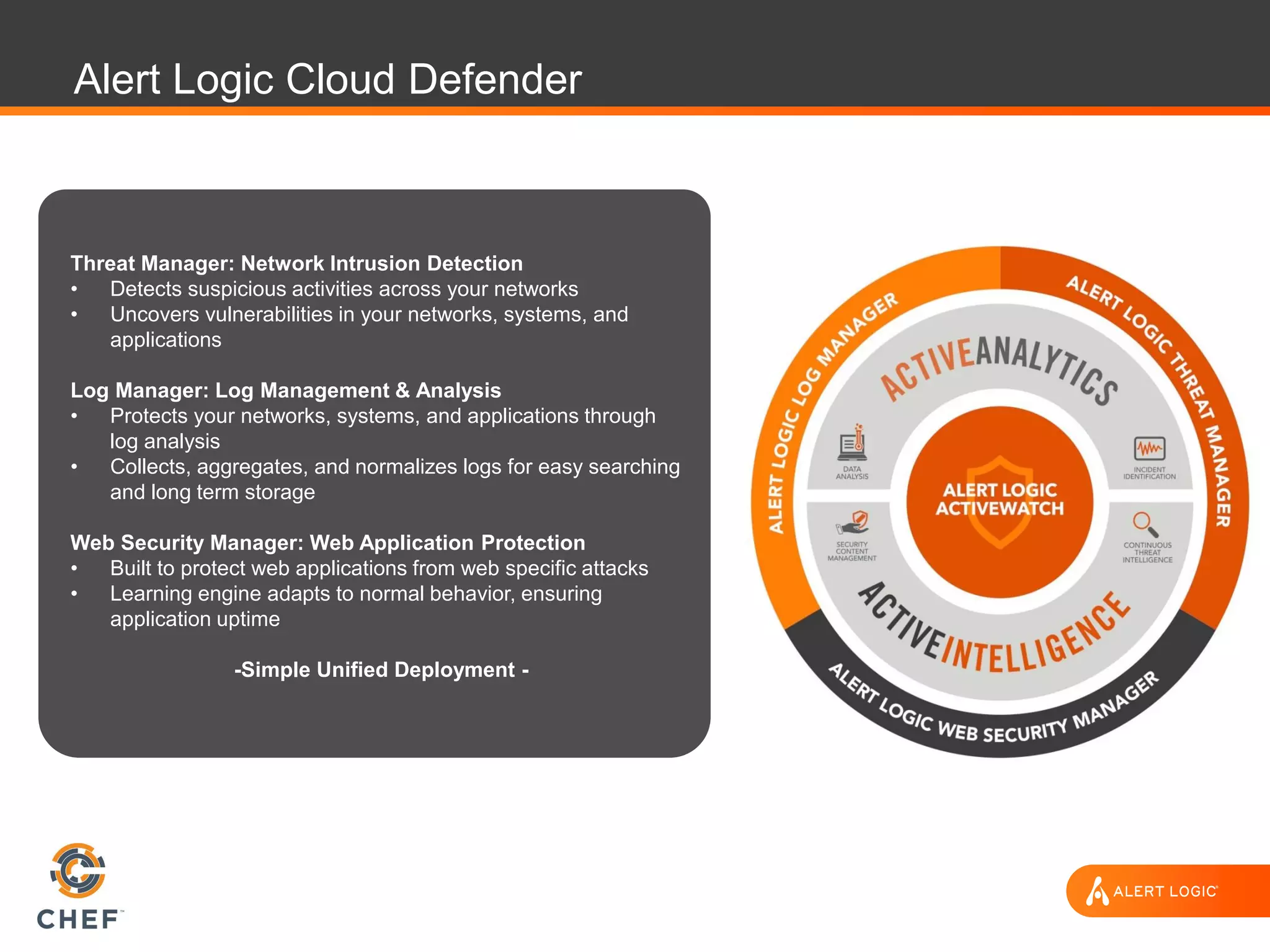
The document discusses the challenges of integrating security within DevOps practices, emphasizing the need for automation and a collaborative approach to overcome traditional security barriers. It highlights the importance of vulnerability management, continuous monitoring, and the implementation of secure, immutable systems to enhance cloud security. Additionally, it outlines strategies for effectively embedding security into development pipelines and improving communication between development, operations, and security teams.