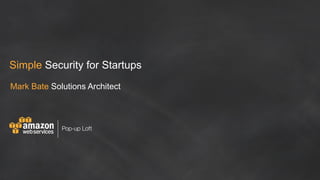
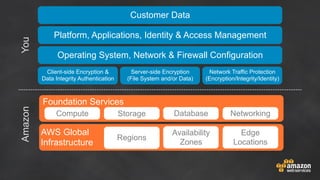
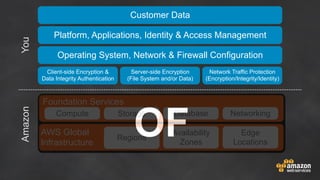
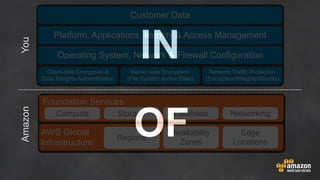
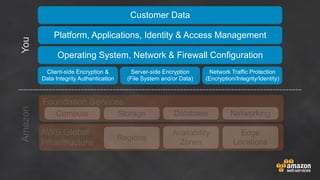
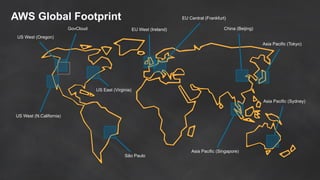
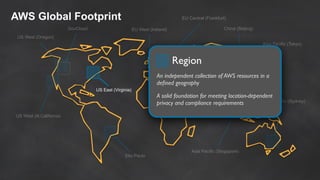
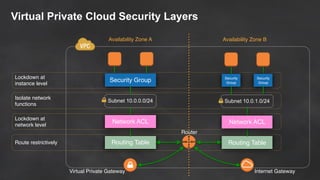
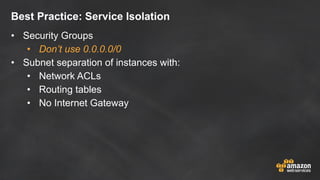
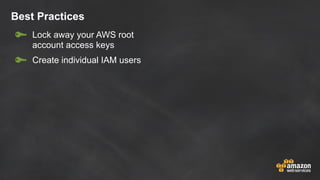
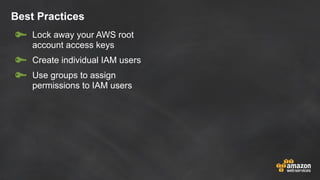
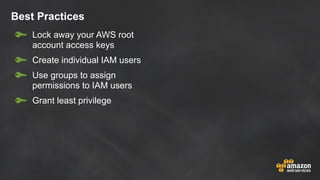
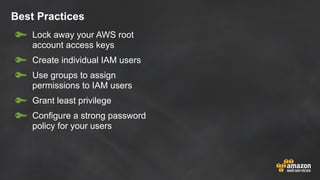
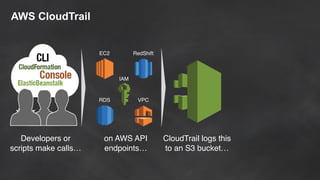
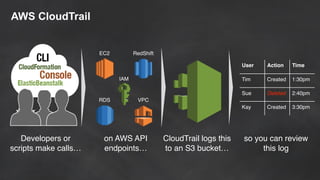
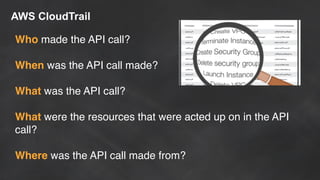
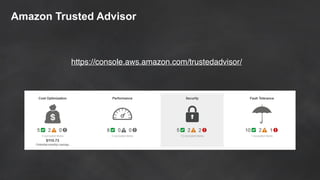
The document discusses simple security best practices for startups using AWS. It recommends locking away root credentials, creating individual IAM users with least privilege, and using roles, MFA, and rotating credentials. It also discusses encrypting data at rest using services like S3, EBS, RDS, and Redshift, and encrypting data in transit using SSL. Logging and auditing can be done with CloudTrail. The Well-Architected Framework and Trusted Advisor provide guidance on security, reliability, performance efficiency and cost optimization.