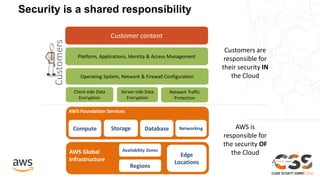
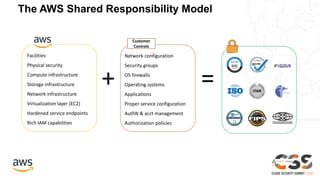
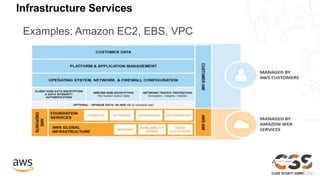
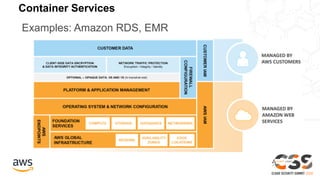
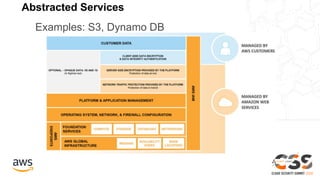
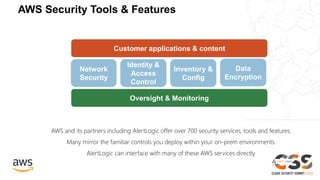
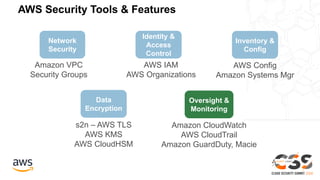
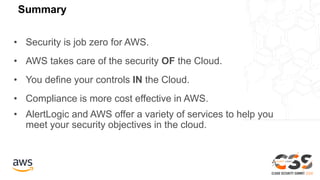
The document outlines the AWS Shared Responsibility Model, emphasizing that security is a top priority for AWS, which manages the security of the cloud while customers control their own security elements. It highlights various AWS security services and recommendations for customers to enhance their security posture. The document also provides resources for further information on AWS security best practices and compliance.