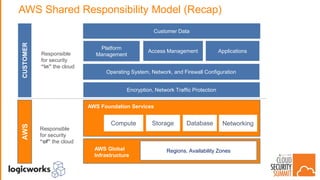
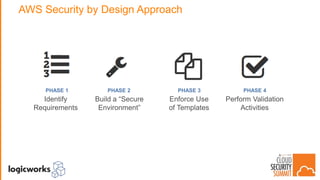
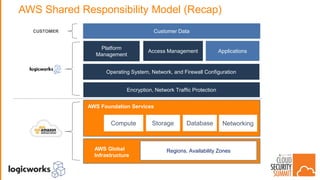
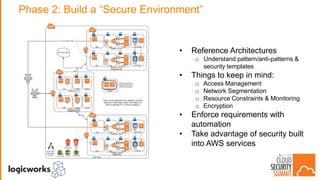
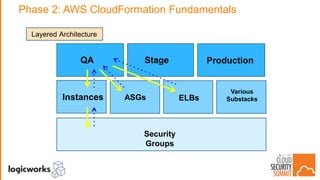
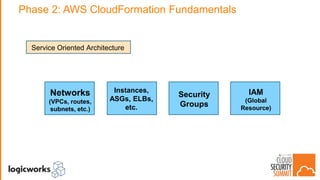
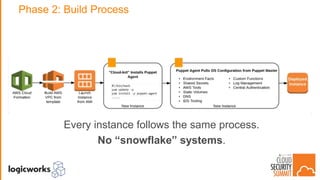
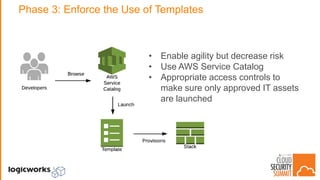
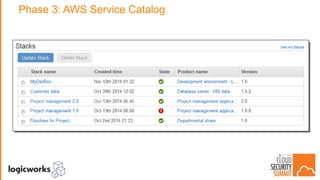
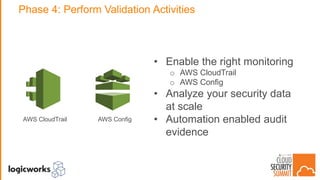
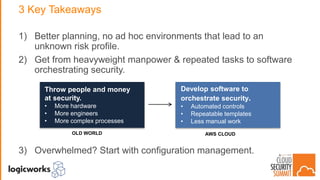
The document outlines best practices for building secure solutions in AWS, emphasizing the shared responsibility model and the importance of establishing a secure environment through requirements identification, architecture planning, and automation. It presents a phased approach for implementing security by leveraging AWS services and configuration management to achieve consistency and compliance. Key takeaways highlight the need for better planning, reducing manual security tasks through automation, and focusing on configuration management to enhance security efficiency.