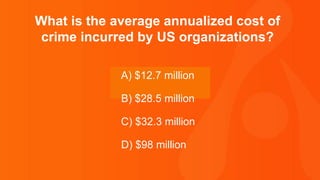
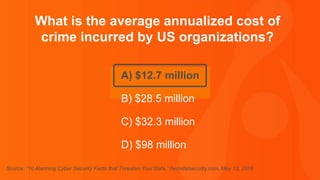
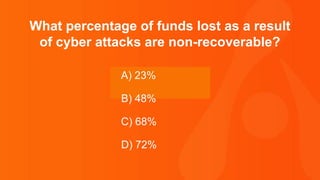
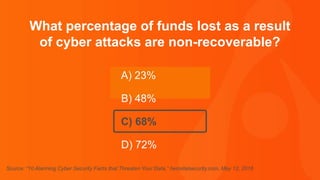
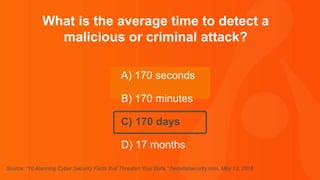
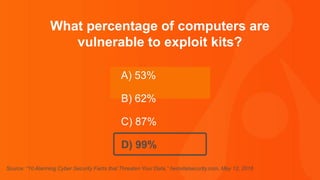
The document contains a series of questions and statements about cybersecurity statistics. Some key facts presented include that 400,000 Facebook accounts are compromised by hackers every day; the September 2016 Yahoo breach affected 500 million user accounts; and the average time to detect a malicious attack is 170 minutes. The document is a collection of cybersecurity trivia intended to highlight important statistics about threats, breaches, and vulnerabilities.