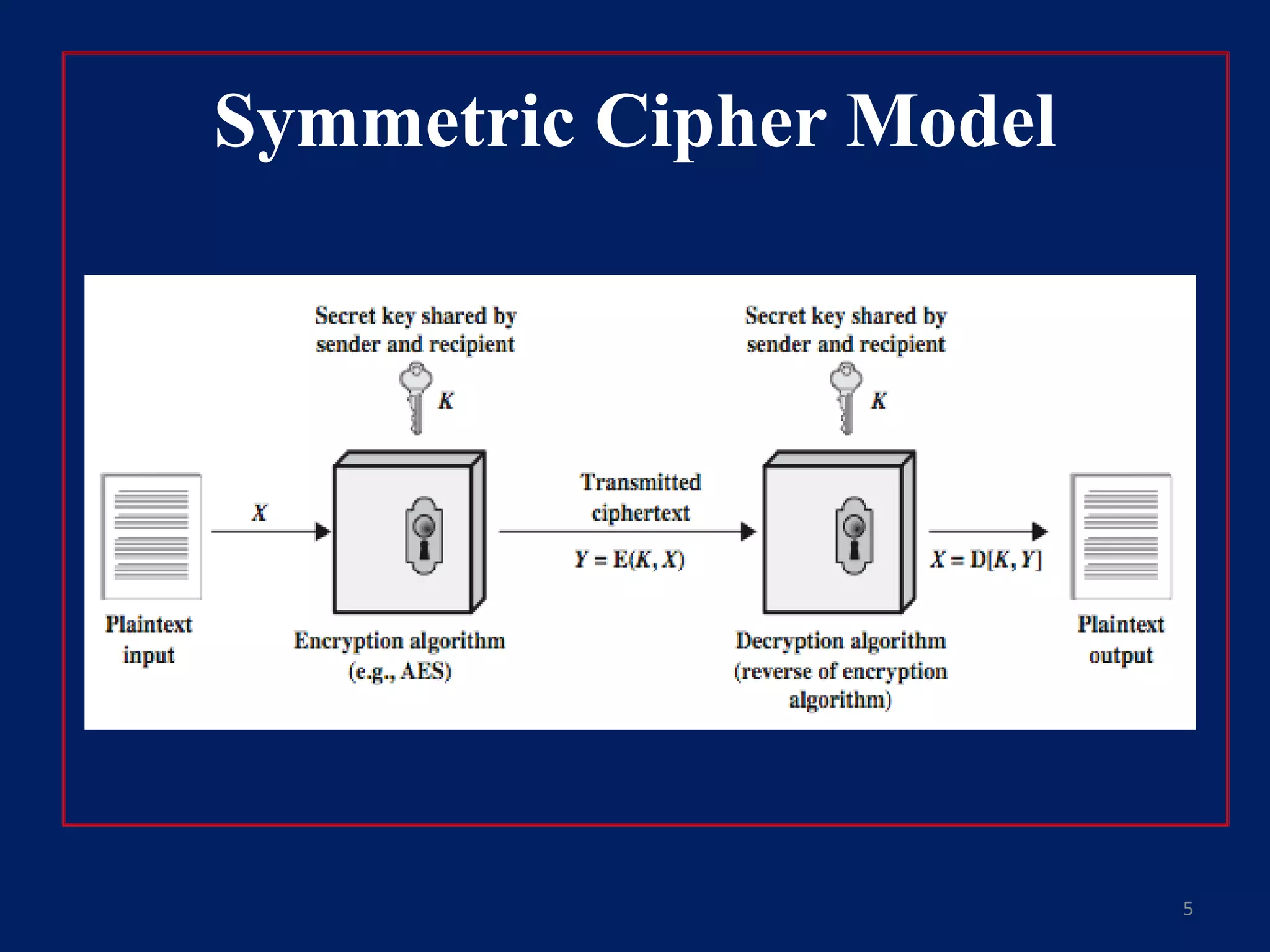
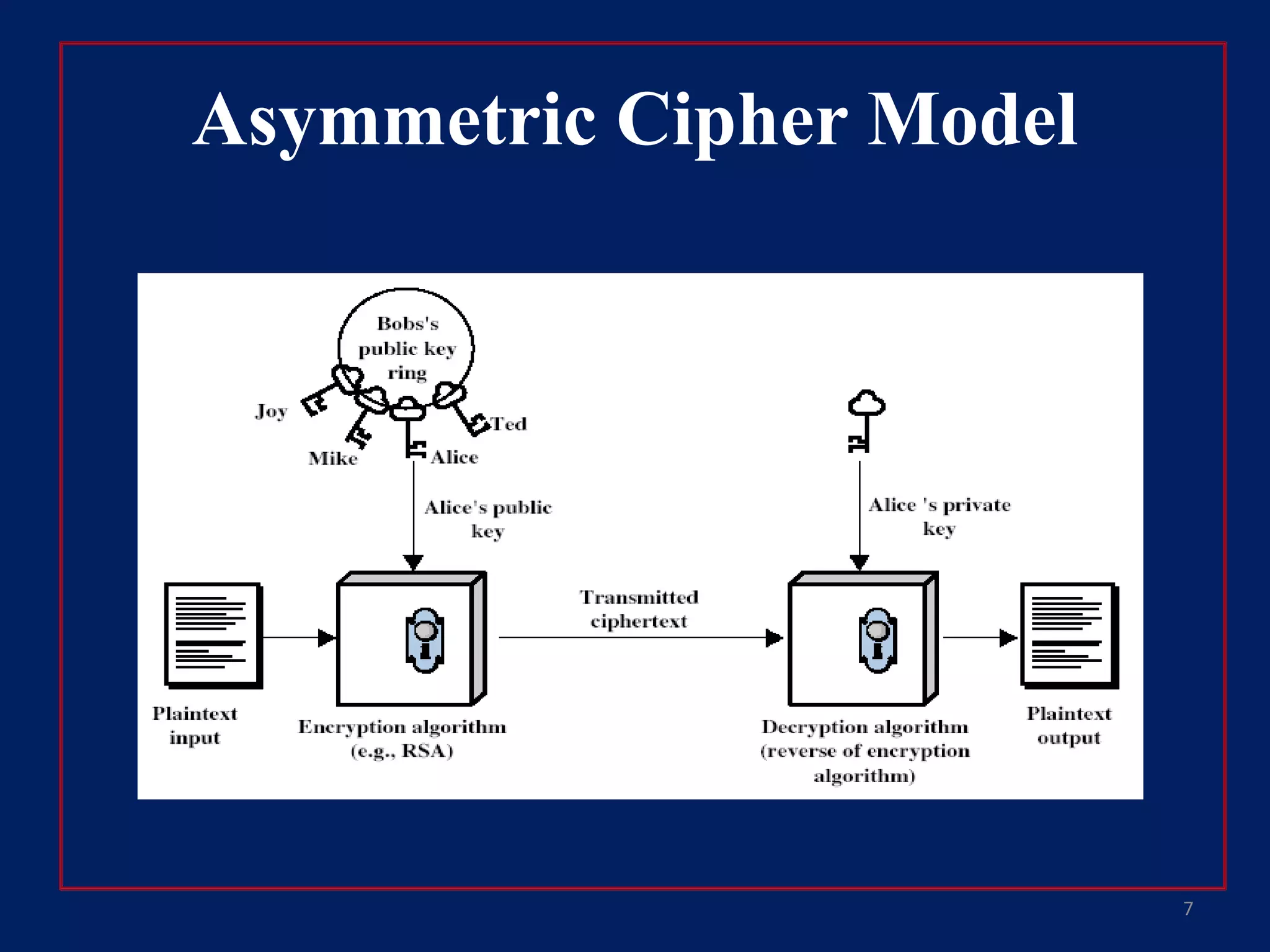
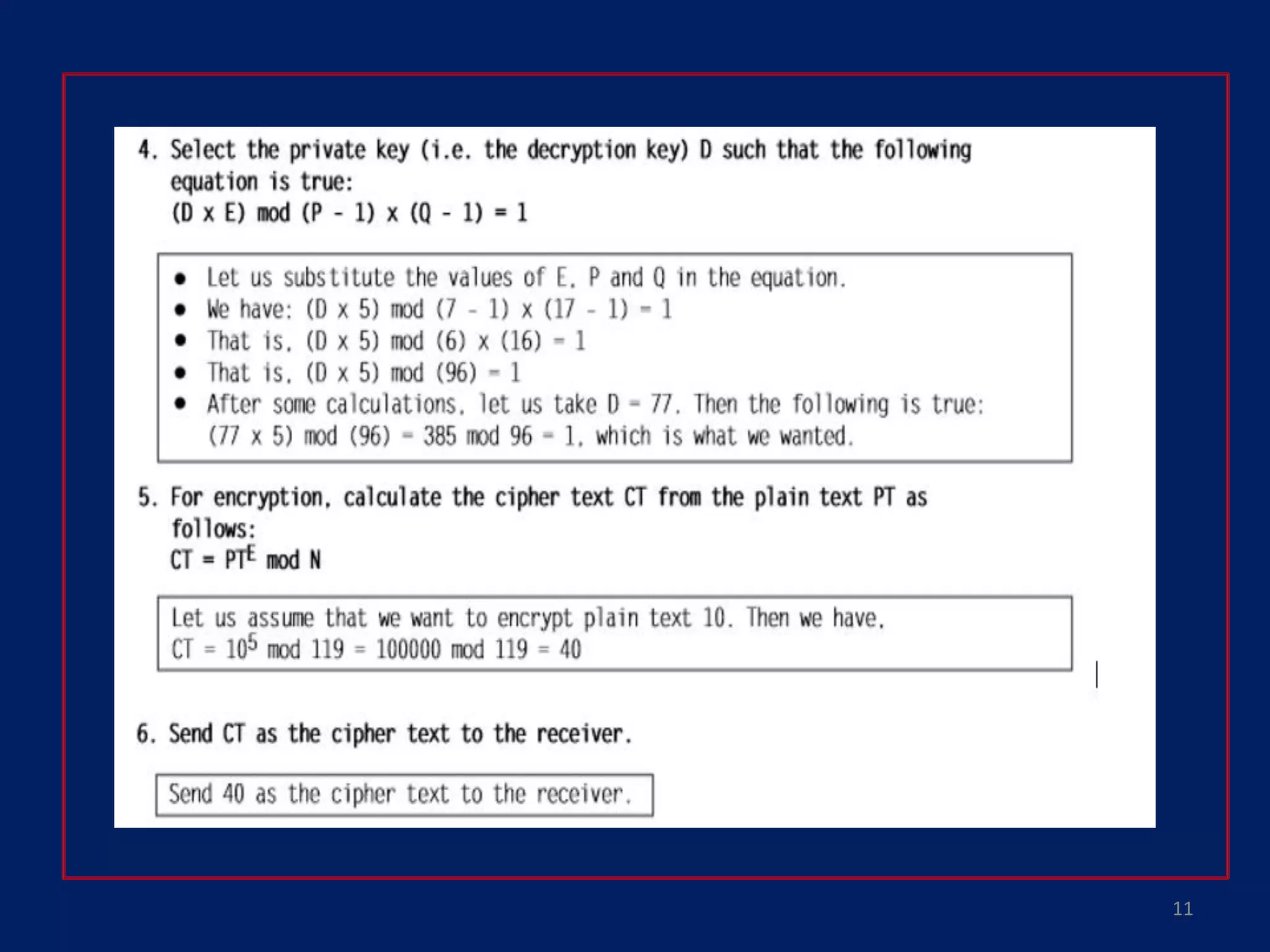
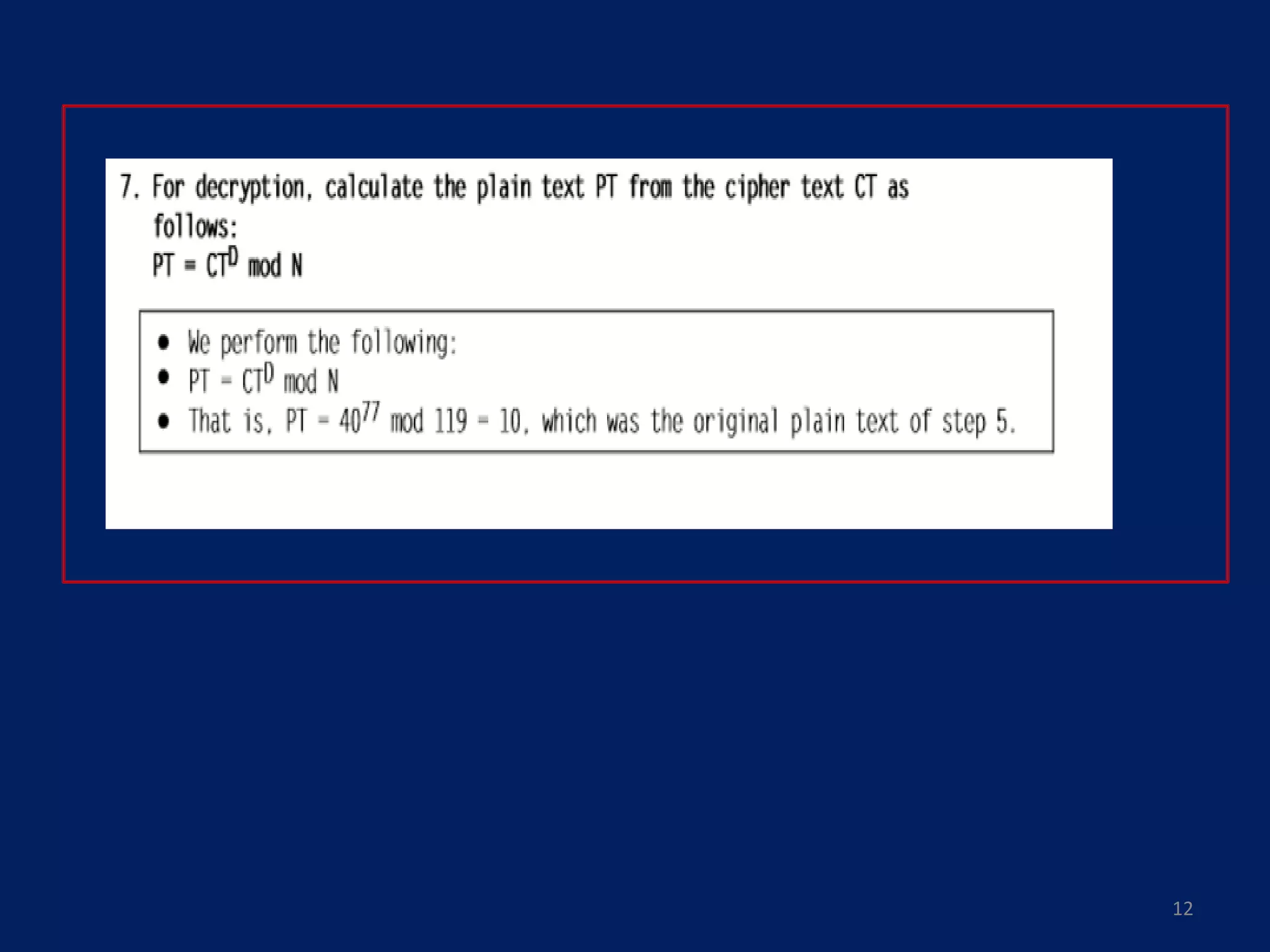
This document provides an overview of symmetric encryption, asymmetric encryption, and the RSA algorithm. It discusses how symmetric encryption uses a shared key for encryption and decryption, while asymmetric encryption uses public and private key pairs. It then explains that RSA is an asymmetric encryption algorithm that is widely used today. Specifically, RSA is based on the difficulty of factoring large prime numbers, where a public key is used to encrypt messages and a private key is used to decrypt them.