Embed presentation


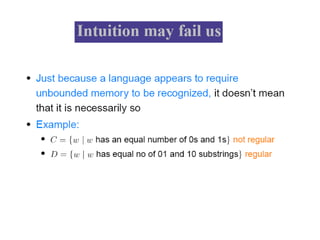



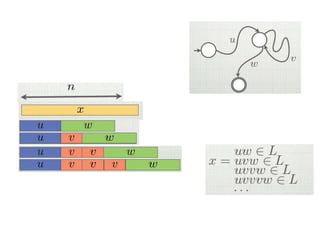
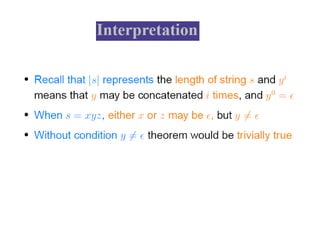




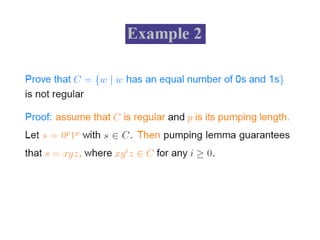
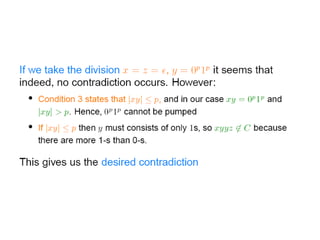

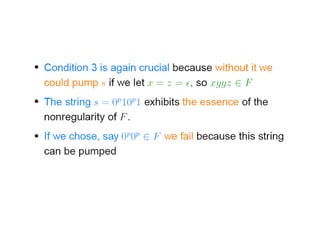


This document discusses the properties of regular languages including closure properties like union, intersection, concatenation and complementation as well as star and reversal operations. It also covers decision properties such as membership, emptiness, finiteness, infiniteness and equivalence that can be tested for regular languages.

















